tegal1337 / 0l4bs
Licence: gpl-3.0
Cross-site scripting labs for web application security enthusiasts
Stars: ✭ 119
Projects that are alternatives of or similar to 0l4bs
Findom Xss
A fast DOM based XSS vulnerability scanner with simplicity.
Stars: ✭ 310 (+160.5%)
Mutual labels: xss, bugbounty
Android Reports And Resources
A big list of Android Hackerone disclosed reports and other resources.
Stars: ✭ 590 (+395.8%)
Mutual labels: xss, bugbounty
Bxss
bXSS is a utility which can be used by bug hunters and organizations to identify Blind Cross-Site Scripting.
Stars: ✭ 331 (+178.15%)
Mutual labels: xss, bugbounty
Gxss
A tool to check a bunch of URLs that contain reflecting params.
Stars: ✭ 115 (-3.36%)
Mutual labels: xss, bugbounty
Eagle
Multithreaded Plugin based vulnerability scanner for mass detection of web-based applications vulnerabilities
Stars: ✭ 85 (-28.57%)
Mutual labels: xss, bugbounty
Xspear
Powerfull XSS Scanning and Parameter analysis tool&gem
Stars: ✭ 583 (+389.92%)
Mutual labels: xss, bugbounty
vaf
Vaf is a cross-platform very advanced and fast web fuzzer written in nim
Stars: ✭ 294 (+147.06%)
Mutual labels: xss, bugbounty
Tiny Xss Payloads
A collection of tiny XSS Payloads that can be used in different contexts. https://tinyxss.terjanq.me
Stars: ✭ 975 (+719.33%)
Mutual labels: xss, bugbounty
Blackwidow
A Python based web application scanner to gather OSINT and fuzz for OWASP vulnerabilities on a target website.
Stars: ✭ 887 (+645.38%)
Mutual labels: xss, bugbounty
PastebinMarkdownXSS
XSS in pastebin.com and reddit.com via unsanitized markdown output
Stars: ✭ 84 (-29.41%)
Mutual labels: xss, bugbounty
Ezxss
ezXSS is an easy way for penetration testers and bug bounty hunters to test (blind) Cross Site Scripting.
Stars: ✭ 1,022 (+758.82%)
Mutual labels: xss, bugbounty
XSS-Payload-without-Anything
XSS Payload without Anything.
Stars: ✭ 74 (-37.82%)
Mutual labels: xss, bugbounty
xssfinder
Toolset for detecting reflected xss in websites
Stars: ✭ 105 (-11.76%)
Mutual labels: xss, bugbounty
Hackerone Reports
Top disclosed reports from HackerOne
Stars: ✭ 458 (+284.87%)
Mutual labels: xss, bugbounty
Xss Payload List
🎯 Cross Site Scripting ( XSS ) Vulnerability Payload List
Stars: ✭ 2,617 (+2099.16%)
Mutual labels: xss, bugbounty
Dalfox
🌘🦊 DalFox(Finder Of XSS) / Parameter Analysis and XSS Scanning tool based on golang
Stars: ✭ 791 (+564.71%)
Mutual labels: xss, bugbounty
Reconftw
reconFTW is a tool designed to perform automated recon on a target domain by running the best set of tools to perform scanning and finding out vulnerabilities
Stars: ✭ 974 (+718.49%)
Mutual labels: xss, bugbounty
0l4bs

Cross-site scripting labs for web application security enthusiasts
List of Chall :
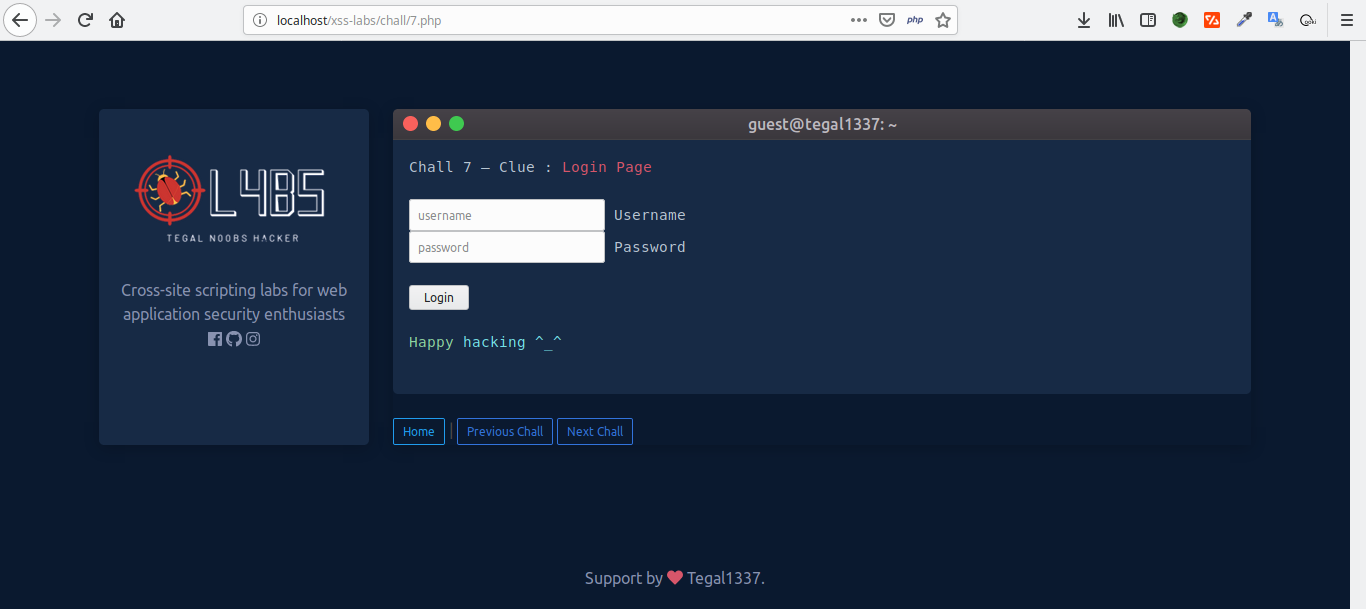
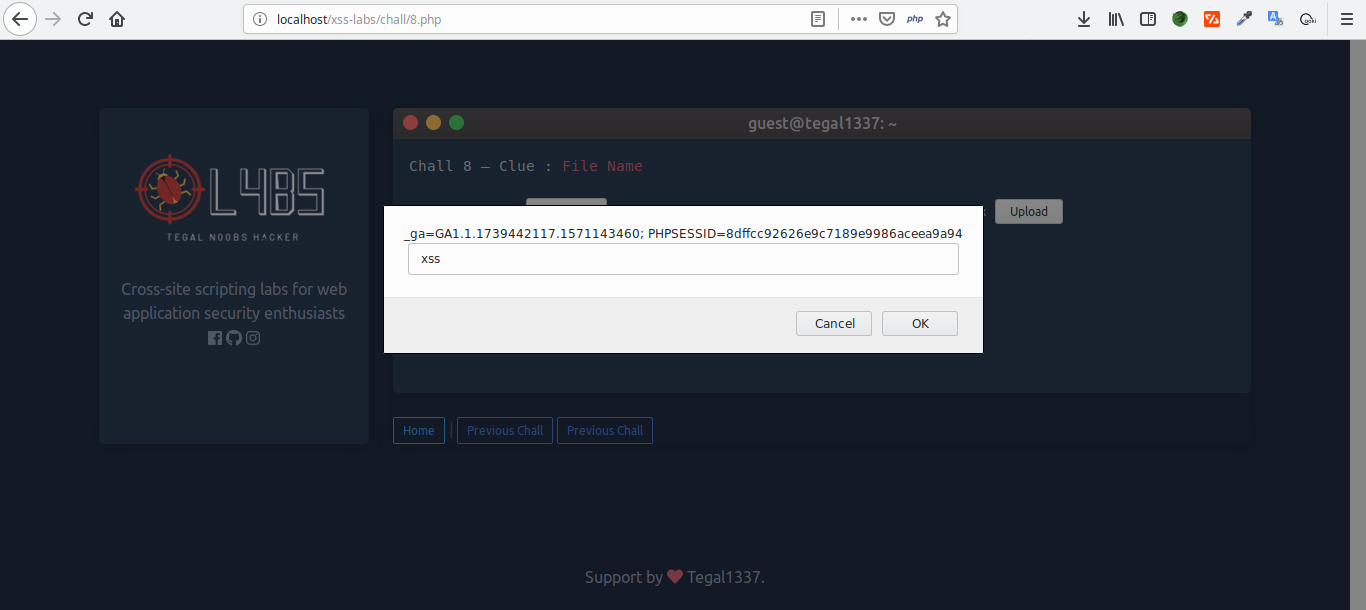
~ Chall 1 | URL ~ Chall 2 | Form ~ Chall 3 | User-Agent ~ Chall 4 | Referrer ~ Chall 5 | Cookie ~ Chall 6 | LocalStorage ~ Chall 7 | Login Page ~ Chall 8 | File Upload ~ Chall 9 | Base64 Encoding ~ Chall 10 | Removes Alert ~ Chall 11 | Removes Script ~ Chall 12 | Preg_replace ~ Chall 13 | HTML Entities ~ Chall 14 | Regex Filter #1 ~ Chall 15 | Regex Filter #2 ~ Chall 16 | Regex Filter #3 ~ Chall 17 | HTML Entities + URL Encode ~ Chall 18 | HTML Entities #2 (Special Character) ~ Chall 19 | HTML Entities #3 (Input Value) ~ Chall 20 | HTML Entities #4 (Input Value + Capitalizes)
Screenshot :
Instalation :
- Run your web server (XAMPP / LAMPP)
- Clone the repository and put the files in the /htdocs/xss-labs
- You can akses http://localhost:8080/xss-labs
- Happy Hacking ^_^
Run this image
To run this image you need docker installed. Just run the command:
docker run --name web-ctf -d -it -p 80:80 hightechsec/xsslabs
Deploy Manually Docker image
- Clone this repo (
git clone https://github.com/tegal1337/0l4bs) - Then run
docker build -t "xsslabs" .and wait untill it's done - If the build is clear, run this command
docker run --name web-ctf -d -it -p 80:80 xsslabs
Write Up / Articles
0l4bs XSS Labs (https://blog.tegalsec.org/2020/10/0l4bs-cross-site-scripting-labs-for-web.html)
跨站脚本攻击实验室:0l4bs (https://zhuanlan.zhihu.com/p/108023848)
0l4bs XSS实验 (https://icssec.club/2020/02/25/0l4bs-XSS/)
Kitploit (https://www.kitploit.com/2020/02/0l4bs-cross-site-scripting-labs-for-web.html?m=0)
Support our organization by giving donations
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].