yunxu1 / Dnsub
dnsub一款好用的子域名扫描工具
Stars: ✭ 106
Labels
Projects that are alternatives of or similar to Dnsub
Burpsuite Collections
BurpSuite收集:包括不限于 Burp 文章、破解版、插件(非BApp Store)、汉化等相关教程,欢迎添砖加瓦---burpsuite-pro burpsuite-extender burpsuite cracked-version hackbar hacktools fuzzing fuzz-testing burp-plugin burp-extensions bapp-store brute-force-attacks brute-force-passwords waf sqlmap jar
Stars: ✭ 1,081 (+919.81%)
Mutual labels: pentest-tool
Venom
Venom - A Multi-hop Proxy for Penetration Testers
Stars: ✭ 1,228 (+1058.49%)
Mutual labels: pentest-tool
Foolavc
foolav successor - loads DLL, executable or shellcode into memory and runs it effectively bypassing AV
Stars: ✭ 93 (-12.26%)
Mutual labels: pentest-tool
Nim Smbexec
SMBExec implementation in Nim - SMBv2 using NTLM Authentication with Pass-The-Hash technique
Stars: ✭ 59 (-44.34%)
Mutual labels: pentest-tool
Cloudflair
🔎 Find origin servers of websites behind CloudFlare by using Internet-wide scan data from Censys.
Stars: ✭ 1,176 (+1009.43%)
Mutual labels: pentest-tool
In Spectre Meltdown
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown) and CVE-2017-5715 (Spectre) allows unprivileged processes to steal secrets from privileged processes. These attacks present 3 different ways of attacking data protection measures on CPUs enabling attackers to read data they shouldn't be able to. This tool is originally based on Microsoft: https://support.microsoft.com/en-us/help/4073119/protect-against-speculative-execution-side-channel-vulnerabilities-in
Stars: ✭ 86 (-18.87%)
Mutual labels: pentest-tool
Sudo killer
A tool to identify and exploit sudo rules' misconfigurations and vulnerabilities within sudo for linux privilege escalation.
Stars: ✭ 1,073 (+912.26%)
Mutual labels: pentest-tool
Arl
ARL(Asset Reconnaissance Lighthouse)资产侦察灯塔系统旨在快速侦察与目标关联的互联网资产,构建基础资产信息库。 协助甲方安全团队或者渗透测试人员有效侦察和检索资产,发现存在的薄弱点和攻击面。
Stars: ✭ 1,357 (+1180.19%)
Mutual labels: pentest-tool
Ldap search
Python3 script to perform LDAP queries and enumerate users, groups, and computers from Windows Domains. Ldap_Search can also perform brute force/password spraying to identify valid accounts via LDAP.
Stars: ✭ 78 (-26.42%)
Mutual labels: pentest-tool
Winpwn
Automation for internal Windows Penetrationtest / AD-Security
Stars: ✭ 1,303 (+1129.25%)
Mutual labels: pentest-tool
Eyes.sh
Let's you perform domain/IP information gathering... in BASH! Wasn't it esr who said "With enough eyeballs, all your IP info are belong to us?"
Stars: ✭ 89 (-16.04%)
Mutual labels: pentest-tool
Vulmap
Vulmap 是一款 web 漏洞扫描和验证工具, 可对 webapps 进行漏洞扫描, 并且具备漏洞利用功能
Stars: ✭ 1,079 (+917.92%)
Mutual labels: pentest-tool
Erodir
A fast web directory/file enumeration tool written in Rust
Stars: ✭ 94 (-11.32%)
Mutual labels: pentest-tool
Nmap Nse Info
Browse and search through nmap's NSE scripts.
Stars: ✭ 54 (-49.06%)
Mutual labels: pentest-tool
One Lin3r
Gives you one-liners that aids in penetration testing operations, privilege escalation and more
Stars: ✭ 1,259 (+1087.74%)
Mutual labels: pentest-tool
Vailyn
A phased, evasive Path Traversal + LFI scanning & exploitation tool in Python
Stars: ✭ 103 (-2.83%)
Mutual labels: pentest-tool
Win Portfwd
Powershell script to setup windows port forwarding using native netsh client
Stars: ✭ 95 (-10.38%)
Mutual labels: pentest-tool
Eggshell
iOS/macOS/Linux Remote Administration Tool
Stars: ✭ 1,286 (+1113.21%)
Mutual labels: pentest-tool
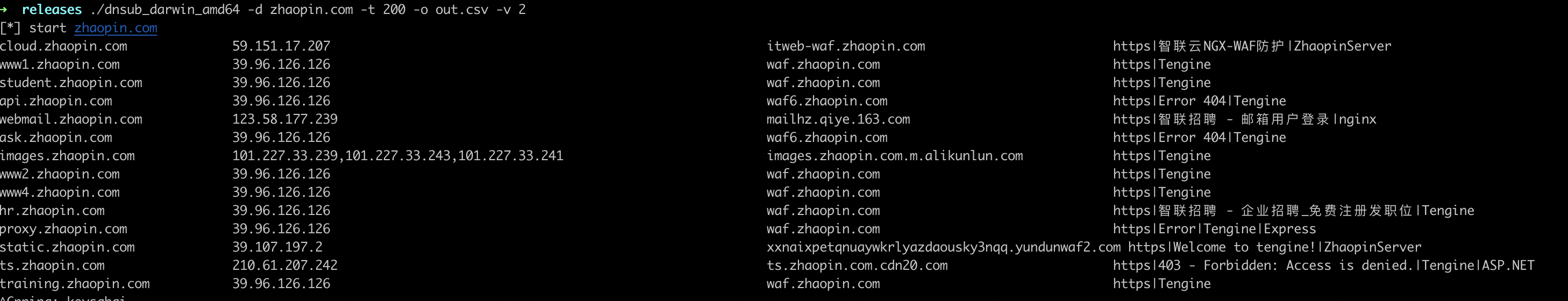
dnsub
本工具通过字典枚举的方式用于扫描探测子域名,意在帮助用户梳理子域名资产使用,dnsub使用go语言高并发扫描,并可展示 子域名、IP 、 CNAME、域名信息,处理了枚举中常见的泛解析问题,支持加载多个字典,枚举探测更多深度的子域名信息,帮助用户快速掌握域名资产,扫描速度快效率高且跨平台,希望这款工具能帮助你有更多的收获 : )
参数:
Usage of ./dnsub:
-d string
target domain (子域名目标)
-depth int
enumerating subdomain depth using a param[f2] file content (default 2) (子域名爆破深度)
-dns string
dns server address (default "9.9.9.9") (指定dns服务器)
-f string
load subdomain filepath. eg: dnsubnames.txt (default "dict/dnsubnames.txt") (子域名字典)
-f2 string
load subdomain filepath. eg: dnsub_next.txt (default "dict/dnsub_next.txt") (子域名字典,这个参数主要用于爆破2级及以后深度所使用的字典)
-o string
output result to csv,set file path.(子域名扫描结果输出到csv文件,指定路径及文件名)
-t int
thread pool numbers (default 20) (设置扫描的线程池数)
-timeout int
dns question timeout,unit is second (default 5) (dns请求超时时间,默认5秒)
-v int
show verbose level (default 1) (展示扫描信息等级,默认为1,如果大于1则会展示域名banner信息)
-debug
enable debug output log info (打印debug信息)
-h help (帮助)
简单扫描:
dnsub -d example.com
常规扫描:
dnsub -d example.com -t 200 -v 2 -o out.csv
# -d 指定目标
# -t 指定线程数
# -o 指定输出文件
# -v 2 扫描到子域名后展示banner信息
指定双字典扫描 && 设置扫描深度
本功能根据枚举深度加载不同的字典,推荐使用一些小字典多深度爆破下级域名
dnsub -d example.com -t 200 -f subnames.txt -f2 next.txt -depth 3 -o out.csv -v 2
#通过指定 -f 参数加载一个一级子域名枚举字典;
#通过指定 -f2 参数加载一个2级以上的子域名枚举字典
#通过指定 -depth 参数设置子域名枚举深度为3,即 a.b.c.example ,该参数默认值是2
如果你希望所有深度子域名枚举都使用一个字典可以指定
dnsub -f sub.txt -f2 sub.txt
版本更新记录:
- 优化泛解析识别;
- 缩短打印行;
- 优化域名访问探测,增强稳定性,忽略请求超时的域名;
- 下版本计划加入API接口查询功能.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].