marco-lancini / Goscan
Labels
Projects that are alternatives of or similar to Goscan
GoScan is an interactive network scanner client, featuring auto-completion, which provides abstraction and automation over nmap.
Although it started as a small side-project I developed in order to learn @golang, GoScan can now be used to perform host discovery, port scanning, and service enumeration not only in situations where being stealthy is not a priority and time is limited (think at CTFs, OSCP, exams, etc.), but also (with a few tweaks in its configuration) during professional engagements.
GoScan is also particularly suited for unstable environments (think unreliable network connectivity, lack of "screen", etc.), given that it fires scans and maintain their state in an SQLite database. Scans run in the background (detached from the main thread), so even if connection to the box running GoScan is lost, results can be uploaded asynchronously (more on this below). That is, data can be imported into GoScan at different stages of the process, without the need to restart the entire process from scratch if something goes wrong.
In addition, the Service Enumeration phase integrates a collection of other tools (e.g., EyeWitness, Hydra, nikto, etc.), each one tailored to target a specific service.
Installation
Binary installation (Recommended)
Binaries are available from the Release page.
# Linux (64bit)
$ wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_amd64.zip
$ unzip goscan_2.4_linux_amd64.zip
# Linux (32bit)
$ wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_386.zip
$ unzip goscan_2.4_linux_386.zip
# After that, place the executable in your PATH
$ chmod +x goscan
$ sudo mv ./goscan /usr/local/bin/goscan
Build from source
# Clone and spin up the project
$ git clone https://github.com/marco-lancini/goscan.git
$ cd goscan/
$ docker-compose up --build
$ docker-compose run cli /bin/bash
# Initialize DEP
[email protected]:/go/src/github.com/marco-lancini/goscan $ make init
[email protected]:/go/src/github.com/marco-lancini/goscan $ make setup
# Build
[email protected]:/go/src/github.com/marco-lancini/goscan $ make build
# To create a multi-platform binary, use the cross command via make
[email protected]:/go/src/github.com/marco-lancini/goscan $ make cross
Usage
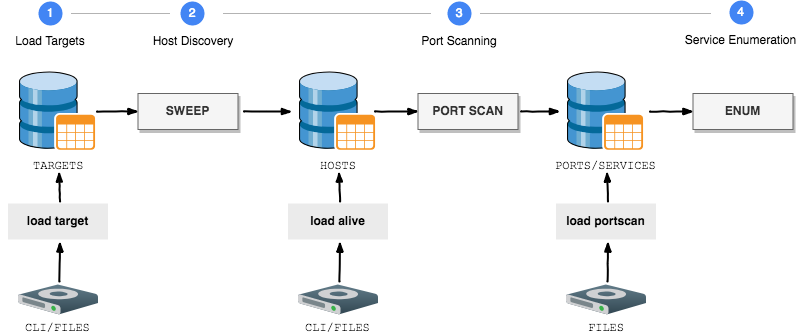
GoScan supports all the main steps of network enumeration:
| Step | Commands |
|---|---|
| 1. Load targets |
|
| 2. Host Discovery |
|
| 3. Port Scanning |
|
| 4. Service Enumeration |
|
| 5. Special Scans |
|
| Utils |
|
External Integrations
The Service Enumeration phase currently supports the following integrations:
| WHAT | INTEGRATION |
|---|---|
| ARP |
|
| DNS |
|
| FINGER |
|
| FTP |
|
| HTTP |
|
| RDP |
|
| SMB |
|
| SMTP |
|
| SNMP |
|
| SSH |
|
| SQL |
|
| VNC |
|
License
GoScan is released under a MIT License. See the LICENSE file for full details.