pikpikcu / Pentest Tools Framework
Licence: gpl-3.0
Pentest Tools Framework is a database of exploits, Scanners and tools for penetration testing. Pentest is a powerful framework includes a lot of tools for beginners. You can explore kernel vulnerabilities, network vulnerabilities
Stars: ✭ 211
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Pentest Tools Framework
Php Antimalware Scanner
AMWScan (PHP Antimalware Scanner) is a free tool to scan php files and analyze your project to find any malicious code inside it.
Stars: ✭ 181 (-14.22%)
Mutual labels: scanner, exploit, backdoor
Pentest Tools Framework
Pentest Tools Framework is a database of exploits, Scanners and tools for penetration testing. Pentest is a powerful framework includes a lot of tools for beginners. You can explore kernel vulnerabilities, network vulnerabilities
Stars: ✭ 48 (-77.25%)
Mutual labels: scanner, exploit, backdoor
Thoron
Thoron Framework is a Linux post-exploitation framework that exploits Linux TCP vulnerability to provide a shell-like connection. Thoron Framework has the ability to create simple payloads to provide Linux TCP attack.
Stars: ✭ 87 (-58.77%)
Mutual labels: exploit, backdoor
Ladon
大型内网渗透扫描器&Cobalt Strike,Ladon8.9内置120个模块,包含信息收集/存活主机/端口扫描/服务识别/密码爆破/漏洞检测/漏洞利用。漏洞检测含MS17010/SMBGhost/Weblogic/ActiveMQ/Tomcat/Struts2,密码口令爆破(Mysql/Oracle/MSSQL)/FTP/SSH(Linux)/VNC/Windows(IPC/WMI/SMB/Netbios/LDAP/SmbHash/WmiHash/Winrm),远程执行命令(smbexec/wmiexe/psexec/atexec/sshexec/webshell),降权提权Runas、GetSystem,Poc/Exploit,支持Cobalt Strike 3.X-4.0
Stars: ✭ 2,911 (+1279.62%)
Mutual labels: scanner, exploit
Cloudfail
Utilize misconfigured DNS and old database records to find hidden IP's behind the CloudFlare network
Stars: ✭ 1,239 (+487.2%)
Mutual labels: scanner, bruteforce
Ghost
Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely access an Android device. Ghost Framework gives you the power and convenience of remote Android device administration.
Stars: ✭ 992 (+370.14%)
Mutual labels: exploit, backdoor
Blueborne Scanner
Bluetooth scanner for local devices that may be vulnerable to Blueborne exploit
Stars: ✭ 125 (-40.76%)
Mutual labels: scanner, exploit
Yotter
yotter - bash script that performs recon and then uses dirb to discover directories that might lead to information leakage
Stars: ✭ 118 (-44.08%)
Mutual labels: scanner, bruteforce
Svscanner
SVScanner - Scanner Vulnerability And MaSsive Exploit.
Stars: ✭ 143 (-32.23%)
Mutual labels: scanner, exploit
Vulmap
Vulmap 是一款 web 漏洞扫描和验证工具, 可对 webapps 进行漏洞扫描, 并且具备漏洞利用功能
Stars: ✭ 1,079 (+411.37%)
Mutual labels: scanner, exploit
Routersploit
Exploitation Framework for Embedded Devices
Stars: ✭ 9,866 (+4575.83%)
Mutual labels: scanner, bruteforce
Xattacker
X Attacker Tool ☣ Website Vulnerability Scanner & Auto Exploiter
Stars: ✭ 897 (+325.12%)
Mutual labels: scanner, exploit
V3n0m Scanner
Popular Pentesting scanner in Python3.6 for SQLi/XSS/LFI/RFI and other Vulns
Stars: ✭ 847 (+301.42%)
Mutual labels: scanner, exploit
Ddos Rootsec
DDOS Archive by RootSec (Scanners, BotNets (Mirai and QBot Premium & Normal and more), Exploits, Methods, Sniffers)
Stars: ✭ 108 (-48.82%)
Mutual labels: scanner, exploit
Mouse
Mouse Framework is an iOS and macOS post-exploitation framework that gives you a command line session with extra functionality between you and a target machine using only a simple Mouse payload. Mouse gives you the power and convenience of uploading and downloading files, tab completion, taking pictures, location tracking, shell command execution, escalating privileges, password retrieval, and much more.
Stars: ✭ 186 (-11.85%)
Mutual labels: exploit, backdoor
Pentest Tools Framework (exploits, Scanner, Password.)
Details
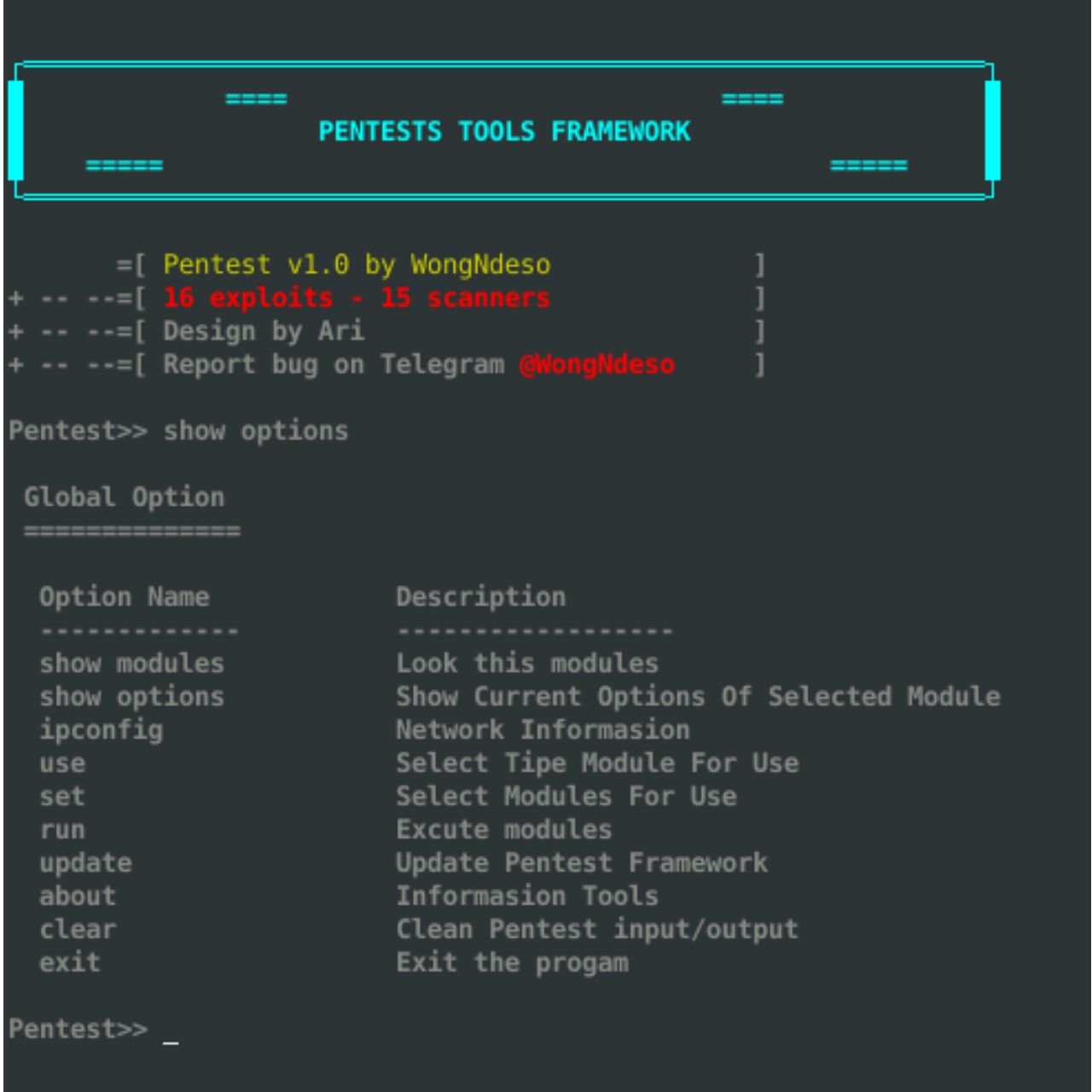 |
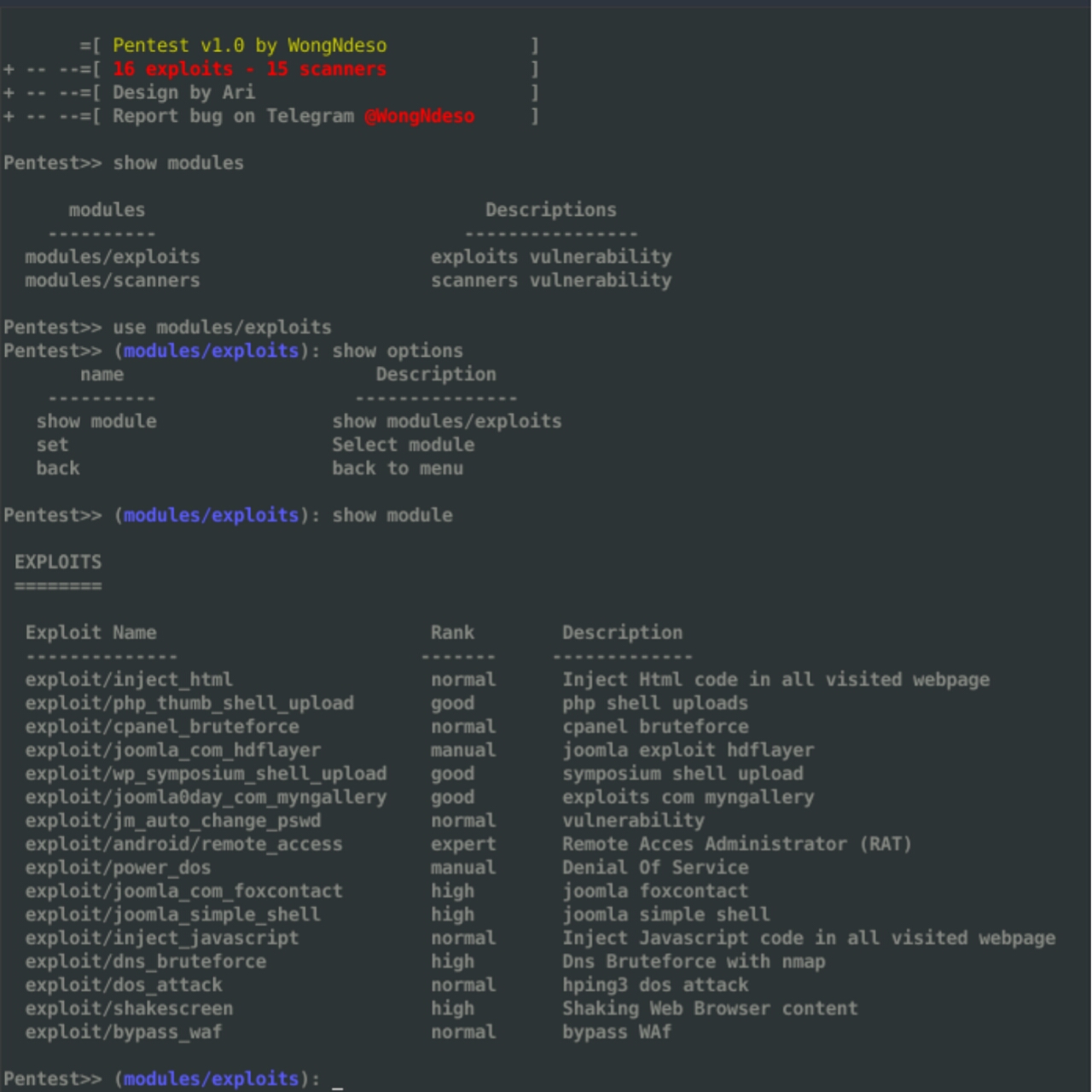 |
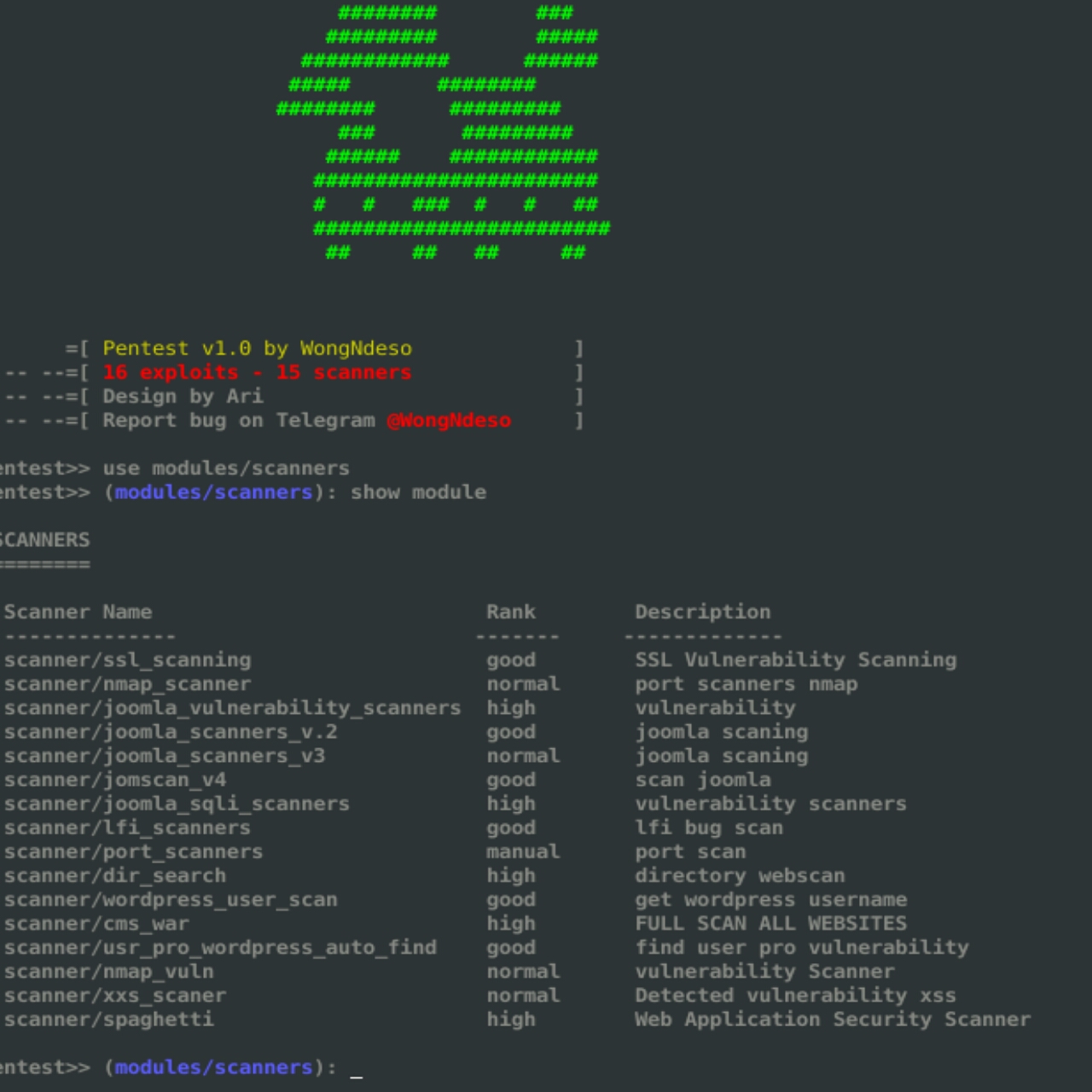 |
NEWS Modules PTF UPDATE!
PTF OPtions
-------------------------------------------------------------------------------------
| Global Option |
-------------------------------------------------------------------------------------
| Command Description |
|-----------------------------------------------------------------------------------|
| show modules | Look this modules |
| show options | Show Current Options Of Selected Module |
| ipconfig | Network Informasion |
| shell | Execution Command Shell >[ctrl+C exit shell ] |
| use | Select Tipe Module For Use |
| set | Select Modules For Use |
| run | Excute modules |
| update | Update Pentest Framework |
| banner | PTF Banner |
| about | Informasion Tools |
| credits | Credits && Thanks |
| clear | Clean Pentest input/output |
| exit | Exit the progam |
-------------------------------------------------------------------------------------
Modules

+-----------------------------------------------------------------------------------------------------------------------------------+
| EXPLOITS |
-------------------------------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
-------------------------------------------------------------------------------------------------------------------------------------
| exploit/abrt_privilege_escalation | normal | ABRT - sosreport Privilege Escalation |
| exploit/web_delivery | good | Script Web Delivery |
| exploit/apache | good | Apache exploit |
| exploit/shellshock | good | cgi-bin/vulnerable shellshock |
| exploit/davtest | good | Testing tool for webdav server |
| exploit/auto_sql | good | auto with sqlmap |
| exploit/ldap_buffer_overflow | normal | Apache module mod_rewrite LDAP protocol Buffer Overflow |
| exploit/vbulletin_rce | good | vBulletin 5.x 0day pre-quth RCE exploit |
| exploit/cmsms_showtime2_rce | normal | CMS Made Simple (CMSMS) Showtime2 File Upload RCE |
| exploit/awind_snmp_exec | good | AwindInc SNMP Service Command Injection |
| exploit/webmin_packageup_rce | excellent | Webmin Package Updates Remote Command Execution |
| exploit/samsung_knox_smdm_url | good | Samsung Galaxy KNOX Android Browser RCE |
| exploit/cisco_dcnm_upload_2019 | excellent | Cisco Data Center Network Manager Unauthenticated Remote Code Execution |
| exploit/zenworks_configuration | excellent | Novell ZENworks Configuration Management Arbitrary File Upload |
| exploit/cisco_ucs_rce | excellent | Cisco UCS Director Unauthenticated Remote Code Execution |
| exploit/sonicwall | normal | Sonicwall SRA <= v8.1.0.2-14sv remote exploit |
| exploit/bluekeep | good | cve 2019 0708 bluekeep rce |
| exploit/eternalblue | good | MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption |
| exploit/inject_html | normal | Inject Html code in all visited webpage |
| exploit/robots | normal | robots.txt Detected |
| exploit/jenkins_script_console | good | Jenkins-CI Script-Console Java Execution |
| exploit/php_thumb_shell_upload | good | php shell uploads |
| exploit/cpanel_bruteforce | normal | cpanel bruteforce |
| exploit/cms_rce | normal | CMS Made Simple 2.2.7 - (Authenticated) Remote Code Execution |
| exploit/joomla_com_hdflayer | manual | joomla exploit hdflayer |
| exploit/wp_symposium_shell_upload | good | symposium shell upload |
| exploit/joomla0day_com_myngallery | good | exploits com myngallery |
| exploit/jm_auto_change_pswd | normal | vulnerability |
| exploit/android_remote_access | expert | Remote Acces Administrator (RAT) |
| exploit/power_dos | manual | Denial Of Service |
| exploit/tp_link_dos | normal | TP_LINK DOS, 150M Wireless Lite N Router, Model No. TL-WR740N |
| exploit/joomla_com_foxcontact | high | joomla foxcontact |
| exploit/joomla_simple_shell | high | joomla simple shell |
| exploit/joomla_comfields_sqli_rce | high | Joomla Component Fields SQLi Remote Code Execution |
| exploit/inject_javascript | normal | Inject Javascript code in all visited webpage |
| exploit/dns_bruteforce | high | Dns Bruteforce with nmap |
| exploit/dos_attack | normal | hping3 dos attack |
| exploit/shakescreen | high | Shaking Web Browser content |
| exploit/bypass_waf | normal | bypass WAf |
| exploit/enumeration | high | simple enumeration |
| exploit/restrict_anonymous | normal | obtain credentials |
| exploit/openssl_heartbleed | high | dump openssl_heartbleed |
| exploit/samba | good | Samba EXploits |
| exploit/smb | good | Albitary samba exploit |
| exploit/webview_addjavascriptinterface | good | Android Browser and WebView addJavascriptInterface Code Execution |
-------------------------------------------------------------------------------------------------------------------------------------

+------------------------------------------------------------------------------------------------------------------------------------+
| SCANNERS |
--------------------------------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
--------------------------------------------------------------------------------------------------------------------------------------
| scanner/enumiax | good | protocol username enumeration |
| scanner/wordpress_user_dislosure | normal | wordpress 5.3 User Disclosure |
| scanner/botnet_scanning | normal | Bootnet Scanning, first need to find the botnet IP |
| scanner/check_ssl_certificate | normal | SSL Certificate |
| scanner/http_services | normal | Gather page titles from HTTP services |
| scanner/dnsrecon | normal | Record enumeration |
| scanner/sslscan | normal | SSL Scanner |
| scanner/ssl_cert | normal | Nmap script ssl-cert |
| scanner/dns_zone_transfer | normal | Dns Zone transfer |
| scanner/dns_bruteforce | normal | Dns Bruteforce |
| scanner/zone_walking | normal | Zone walking |
| scanner/web_services | normal | Get HTTP headers of web services |
| scanner/http_enum | normal | Find web apps from known paths |
| scanner/ddos_reflectors | normal | Scan for UDP DDOS reflectors |
| scanner/grabbing_detection | normal | Lighter banner grabbing detection |
| scanner/discovery | normal | Scan selected ports - ignore discovery |
| scanner/bluekeep | good | CVE-2019-0708 BlueKeep Microsoft Remote Desktop RCE Check |
| scanner/drupal_scan | good | drupal scanner |
| scanner/eternalblue | good | SMB RCE Detection |
| scanner/header | good | header Scanner with nmap |
| scanner/firewalk | good | firewalk |
| scanner/whois | high | whois |
| scanner/dmitry | good | Information Gathering Tool |
| scanner/admin_finder | normal | Admin finder |
| scanner/heartbleed | normal | heartbleed scanner vulnerability |
| scanner/wordpress_scan | normal | wordpress scanner |
| scanner/ssl_scanning | good | SSL Vulnerability Scanning |
| scanner/dns_bruteforce | normal | dns bruteforce |
| scanner/nmap_scanner | normal | port scanners nmap |
| scanner/https_discover | normal | https discover |
| scanner/smb_scanning | good | scan vulnerable SMB server |
| scanner/joomla_vulnerability_scanners | high | vulnerability |
| scanner/mysql_empty_password | good | mysql empty password Detected |
| scanner/joomla_scanners_v.2 | good | joomla scaning |
| scanner/joomla_scanners_v3 | normal | joomla scaning |
| scanner/jomscan_v4 | good | scan joomla |
| scanner/webdav_scan | normal | webdav scan vulnerable |
| scanner/joomla_sqli_scanners | high | vulnerability scanners |
| scanner/lfi_scanners | good | lfi bug scan |
| scanner/port_scanners | manual | port scan |
| scanner/dir_search | high | directory webscan |
| scanner/dir_bruteforce | good | directory Scanning |
| scanner/wordpress_user_scan | good | get wordpress username |
| scanner/cms_war | high | FULL SCAN ALL WEBSITES |
| scanner/usr_pro_wordpress_auto_find | norma | find user vulnerability |
| scanner/nmap_vuln | normal | vulnerability Scanner |
| scanner/xss_scaner | normal | Detected vulnerability xss |
| scanner/spaghetti | high | Web Application Security Scanner |
| scanner/dnslookup | normal | dnslookup scan |
| scanner/reverse_dns | normal | Reverse Dns Lookup |
| scanner/domain_map | normal | scanner domain map |
| scanner/dns_report | normal | dns report |
| scanner/find_shared_dns | normal | find shared dns |
| scanner/golismero | normal | scan vulnerability with golismero |
| scanner/dns_propagation | low | dns propagation |
| scanner/find_records | normal | find records |
| scanner/cloud_flare | normal | cloud flare |
| scanner/extract_links | normal | links extract |
| scanner/web_robot | normal | web robots scanner |
| scanner/enumeration | normal | http-enumeration |
| scanner/ip_locator | good | ip Detected LOcator |
--------------------------------------------------------------------------------------------------------------------------------------

+----------------------------------------------------------------------------------------------------------+
| POST |
------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
------------------------------------------------------------------------------------------------------------
| post/enumeration | normal | http-enumeration |
| post/vbulletin | high | exploits |
| post/wordpress_user_scan | good | scanners |
| post/dir_search | high | scanners |
| post/cms_war | high | scanners |
| post/usr_pro_wordpress_auto_find | normal | scanners |
| post/android_remote_access | good | exploits |
| post/samba | good | exploits |
------------------------------------------------------------------------------------------------------------

+----------------------------------------------------------------------------------------------------------+
| PASSWORD |
------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
------------------------------------------------------------------------------------------------------------
| password/base64_decode | good | base64 decode |
| password/md5_decrypt | good | md5 decrypt |
| password/sha1_decrypt | good | sha1 decrypt |
| password/sha256_decrypt | good | sha256 decrypt |
| password/sha384_decrypt | good | sha384 decrypt |
| password/sha512_decrypt | good | sha512 decrypt |
| password/ssh_bruteforce | good | ssh password bruteforce |
------------------------------------------------------------------------------------------------------------

+------------------------------------------------------------------------------------------------------------------------------------+
| LISTENERS MODULES |
--------------------------------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
--------------------------------------------------------------------------------------------------------------------------------------
| android_meterpreter_reverse_tcp | good | Android Meterpreter, Android Reverse TCP Stager |
| android_meterpreter_reverse_https | good | Android Meterpreter, Android Reverse HTTPS Stager |
| java_jsp_shell_reverse_tcp | good | Java JSP Command Shell, Reverse TCP Inline |
| linux_x64_meterpreter_reverse_https | good | linux/x64/meterpreter_reverse_https |
| linux_x64_meterpreter_reverse_tcp | good | Linux Meterpreter, Reverse TCP Inline |
| linux_x64_shell_reverse_tcp | good | Linux Command Shell, Reverse TCP Stager |
| osx_x64_meterpreter_reverse_https | good | OSX Meterpreter, Reverse HTTPS Inline |
| osx_x64_meterpreter_reverse_tcp | good | OSX Meterpreter, Reverse TCP Inline |
| php_meterpreter_reverse_tcp | good | PHP Meterpreter, PHP Reverse TCP Stager |
| python_meterpreter_reverse_https | good | Python Meterpreter Shell, Reverse HTTPS Inline |
| python_meterpreter_reverse_tcp | good | python/meterpreter_reverse_tcp |
| windows_x64_meterpreter_reverse_https | good | Windows Meterpreter Shell, Reverse HTTPS Inline (x64) |
| windows_x64_meterpreter_reverse_tcp | good | Windows Meterpreter Shell, Reverse TCP Inline x64 |
| cmd_windows_reverse_powershell | good | Windows Command Shell, Reverse TCP (via Powershell) |
+------------------------------------------------------------------------------------------------------------------------------------+
About Pentest Tools Framework
INFO: Pentest Tools Framework is a database of exploits, Scanners
and tools for penetration testing. Pentest is a powerful
framework includes a lot of tools for beginners. You can explore
kernel vulnerabilities, network vulnerabilities.
How to install PTF(Pentest Tools Framework)
[email protected]~# cd Pentest-Tools-Framework
[email protected]~# pip install -r requirements.txt
[email protected]~# python install.py
[email protected]~# PTF
INFO: After running install.py you should
select your backbox/kali linux /parrot Os , all computer OS,
About Pentest Tools Framework modules
Exploits
INFO: A computer program, piece of code,
or sequence of commands that exploit vulnerabilities
in software and are used to carry out an attack on a
computer system. The purpose of the attack can be as a
seizure of control over the system, and the violation
of its functioning!
Scanners
INFO: The program that scans the specified Internet resource,
archive or website. Also network scanners can scan open ports or
your local network and IPs!
Why Pentest Tools Framework?
Pentest Tools Framework is a free software
INFO: This is a good platform
to start exploring vulnerabilities!
Simple UX/UI interface for beginners
INFO: Pentest Tools Framework has simple UX/UI for beginners!
It is easy to understand and it will be easier
for you to master the Pentest Tools Framework.
A lot of tools for beginners
INFO: Pentest Tools Framework has еру following modules
exploits - scanners - password
This is enough for beginners.
Donate!
(I love coffee and am very addicted to coffee:v)

Credits & Thanks
[Nmap Security Scanners]

|
[Metasploit-framework]

|
[exploit-db]

|
[offensive-security]

|
END
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].






