entynetproject / Proton
Licence: gpl-3.0
Proton Framework is a Windows post-exploitation framework similar to other Windows post-exploitation frameworks. The major difference is that the Proton Framework does most of its operations using Windows Script Host, with compatibility in the core to support a default installation of Windows 2000 with no service packs all the way through Windows 10.
Stars: ✭ 142
Programming Languages
python
139335 projects - #7 most used programming language
Labels
Projects that are alternatives of or similar to Proton
Mouse
Mouse Framework is an iOS and macOS post-exploitation framework that gives you a command line session with extra functionality between you and a target machine using only a simple Mouse payload. Mouse gives you the power and convenience of uploading and downloading files, tab completion, taking pictures, location tracking, shell command execution, escalating privileges, password retrieval, and much more.
Stars: ✭ 186 (+30.99%)
Mutual labels: remote-control, kali-linux, hacking, hacking-tool, payload, backdoor, post-exploitation, metasploit, exploitation-framework
Ghost
Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely access an Android device. Ghost Framework gives you the power and convenience of remote Android device administration.
Stars: ✭ 992 (+598.59%)
Mutual labels: kali-linux, hacking, backdoor, rat, post-exploitation, exploitation-framework
Ghost
Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely access an Android device.
Stars: ✭ 1,934 (+1261.97%)
Mutual labels: backdoor, rat, post-exploitation, kali-linux, exploitation-framework
Xeexe Topantivirusevasion
Undetectable & Xor encrypting with custom KEY (FUD Metasploit Rat) bypass Top Antivirus like BitDefender,Malwarebytes,Avast,ESET-NOD32,AVG,... & Automatically Add ICON and MANIFEST to excitable
Stars: ✭ 387 (+172.54%)
Mutual labels: hacking, hacking-tool, backdoor, rat, metasploit
Entropy
Entropy Toolkit is a set of tools to provide Netwave and GoAhead IP webcams attacks. Entropy Toolkit is a powerful toolkit for webcams penetration testing.
Stars: ✭ 126 (-11.27%)
Mutual labels: kali-linux, hacking, hacking-tool, payload, metasploit
Thoron
Thoron Framework is a Linux post-exploitation framework that exploits Linux TCP vulnerability to provide a shell-like connection. Thoron Framework has the ability to create simple payloads to provide Linux TCP attack.
Stars: ✭ 87 (-38.73%)
Mutual labels: remote-control, kali-linux, backdoor, rat, post-exploitation
Ratel
RAT-el is an open source penetration test tool that allows you to take control of a windows machine. It works on the client-server model, the server sends commands and the client executes the commands and sends the result back to the server. The client is completely undetectable by anti-virus software.
Stars: ✭ 121 (-14.79%)
Mutual labels: remote-control, hacking, payload, rat
trolo
trolo - an easy to use script for generating Payloads that bypasses antivirus
Stars: ✭ 45 (-68.31%)
Mutual labels: rat, payload, hacking-tool, metasploit
Chaos
🔥 CHAOS is a Remote Administration Tool that allow generate binaries to control remote operating systems.
Stars: ✭ 1,168 (+722.54%)
Mutual labels: remote-control, hacking, hacking-tool, payload
Phpsploit
Full-featured C2 framework which silently persists on webserver with a single-line PHP backdoor
Stars: ✭ 1,188 (+736.62%)
Mutual labels: hacking, backdoor, post-exploitation, privilege-escalation
Ethical Hacking Tools
Complete Listing and Usage of Tools used for Ethical Hacking
Stars: ✭ 272 (+91.55%)
Mutual labels: kali-linux, hacking, hacking-tool, metasploit
Paradoxiarat
ParadoxiaRat : Native Windows Remote access Tool.
Stars: ✭ 395 (+178.17%)
Mutual labels: hacking, hacking-tool, backdoor, rat
Thefatrat
Thefatrat a massive exploiting tool : Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack and etc . This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most AV softw…
Stars: ✭ 5,944 (+4085.92%)
Mutual labels: kali-linux, hacking, backdoor, rat
Powershell Rat
Python based backdoor that uses Gmail to exfiltrate data through attachment. This RAT will help during red team engagements to backdoor any Windows machines. It tracks the user activity using screen capture and sends it to an attacker as an e-mail attachment.
Stars: ✭ 636 (+347.89%)
Mutual labels: hacking, hacking-tool, backdoor, rat
Dr0p1t Framework
A framework that create an advanced stealthy dropper that bypass most AVs and have a lot of tricks
Stars: ✭ 1,132 (+697.18%)
Mutual labels: kali-linux, hacking, hacking-tool, backdoor
Torat
ToRat is a Remote Administation tool written in Go using Tor as a transport mechanism and RPC for communication
Stars: ✭ 415 (+192.25%)
Mutual labels: payload, rat, post-exploitation, privilege-escalation
Pupy
Pupy is an opensource, cross-platform (Windows, Linux, OSX, Android) remote administration and post-exploitation tool mainly written in python
Stars: ✭ 6,737 (+4644.37%)
Mutual labels: payload, backdoor, rat, post-exploitation
One Lin3r
Gives you one-liners that aids in penetration testing operations, privilege escalation and more
Stars: ✭ 1,259 (+786.62%)
Mutual labels: kali-linux, hacking, hacking-tool, metasploit
Reconnoitre
A security tool for multithreaded information gathering and service enumeration whilst building directory structures to store results, along with writing out recommendations for further testing.
Stars: ✭ 1,824 (+1184.51%)
Mutual labels: kali-linux, hacking, hacking-tool
Skyrat
SkyRAT - Powershell Remote Administration Tool
Stars: ✭ 21 (-85.21%)
Mutual labels: remote-control, hacking-tool, rat
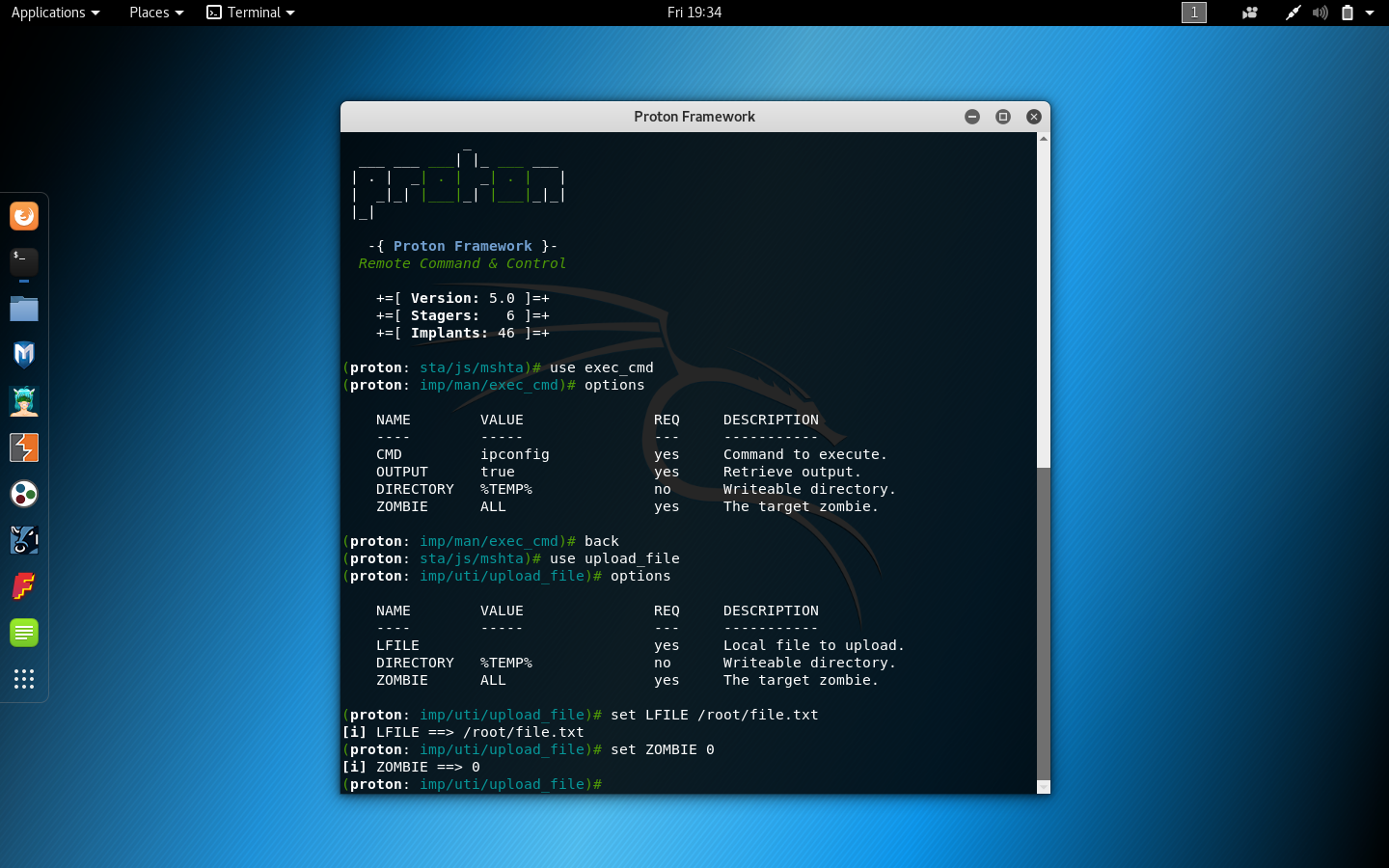
Proton Framework
About Proton Framework
Proton Framework is a Windows post-exploitation framework similar to
other Windows post-exploitation frameworks. The major difference is that
the Proton Framework does most of its operations using Windows Script Host,
with compatibility in the core to support a default installation of
Windows 2000 with no service packs all the way through Windows 10.
Getting started
Proton installation
cd proton
chmod +x install.sh
./install.sh
Proton uninstallation
cd proton
chmod +x uninstall.sh
./uninstall.sh
Proton Framework execution
To run Proton Framework you should
execute the following command.
proton
Why Proton Framework
- Simple and clear UX/UI.
Proton Framework has a simpleand clear UX/UI.
It is easy to understand and it will be easier
for you to master the Proton Framework.
- A lot of different stagers.
There are a lot of different stagers in Proton
Framework such as mshta, disk and wmic stagers.
- A lot of different implants.
There are a lot of different implants in Proton
Framework such as exec_cmd and upload_file implants.
Proton Framework disclaimer
Usage of the Proton Framework for attacking targets without prior mutual consent is illegal.
It is the end user's responsibility to obey all applicable local, state, federal, and international laws.
Developers assume no liability and are not responsible for any misuse or damage caused by this program.
Proton Framework license
---------------------------------------------------
Proton Framework
---------------------------------------------------
Copyright (C) <2019-2020> <Entynetproject>
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].