Nalen98 / Angryghidra
Licence: mit
Use angr in Ghidra
Stars: ✭ 241
Programming Languages
java
68154 projects - #9 most used programming language
Labels
Projects that are alternatives of or similar to Angryghidra
Medusa
An open source interactive disassembler
Stars: ✭ 946 (+292.53%)
Mutual labels: symbolic-execution
Alive2
Automatic verification of LLVM optimizations
Stars: ✭ 199 (-17.43%)
Mutual labels: symbolic-execution
Ponce
IDA 2016 plugin contest winner! Symbolic Execution just one-click away!
Stars: ✭ 1,066 (+342.32%)
Mutual labels: symbolic-execution
Sys
Sys: A Static/Symbolic Tool for Finding Good Bugs in Good (Browser) Code
Stars: ✭ 149 (-38.17%)
Mutual labels: symbolic-execution
Angora
Angora is a mutation-based fuzzer. The main goal of Angora is to increase branch coverage by solving path constraints without symbolic execution.
Stars: ✭ 669 (+177.59%)
Mutual labels: symbolic-execution
Idangr
Use angr in the IDA Pro debugger generating a state from the current debug session
Stars: ✭ 214 (-11.2%)
Mutual labels: symbolic-execution
Mythril
Security analysis tool for EVM bytecode. Supports smart contracts built for Ethereum, Hedera, Quorum, Vechain, Roostock, Tron and other EVM-compatible blockchains.
Stars: ✭ 1,968 (+716.6%)
Mutual labels: symbolic-execution
Etheno
Simplify Ethereum security analysis and testing
Stars: ✭ 77 (-68.05%)
Mutual labels: symbolic-execution
Pakala
Offensive vulnerability scanner for ethereum, and symbolic execution tool for the Ethereum Virtual Machine
Stars: ✭ 97 (-59.75%)
Mutual labels: symbolic-execution
Kleefl
Seeding fuzzers with symbolic execution
Stars: ✭ 172 (-28.63%)
Mutual labels: symbolic-execution
Apisan
APISan: Sanitizing API Usages through Semantic Cross-Checking
Stars: ✭ 46 (-80.91%)
Mutual labels: symbolic-execution
Symgdb
SymGDB - symbolic execution plugin for gdb
Stars: ✭ 202 (-16.18%)
Mutual labels: symbolic-execution
Wasabi Aeg
Yet another implementation of AEG (Automated Exploit Generation) using symbolic execution engine Triton.
Stars: ✭ 23 (-90.46%)
Mutual labels: symbolic-execution
Triton
Triton is a Dynamic Binary Analysis (DBA) framework. It provides internal components like a Dynamic Symbolic Execution (DSE) engine, a dynamic taint engine, AST representations of the x86, x86-64, ARM32 and AArch64 Instructions Set Architecture (ISA), SMT simplification passes, an SMT solver interface and, the last but not least, Python bindings.
Stars: ✭ 1,934 (+702.49%)
Mutual labels: symbolic-execution
Miasm
Reverse engineering framework in Python
Stars: ✭ 2,649 (+999.17%)
Mutual labels: symbolic-execution
Symbiotic
Symbiotic is a tool for finding bugs in computer programs based on instrumentation, program slicing and KLEE
Stars: ✭ 212 (-12.03%)
Mutual labels: symbolic-execution
AngryGhidra
This project was initially started as a part of Digital Security's Research Centre internship "Summer of Hack 2020".
The plugin allows you to use angr for binary analysis and symbolic execution from Ghidra interface.
Solving CTF challenge from SecurityFest 2016 "fairlight" with AngryGhidra plugin:
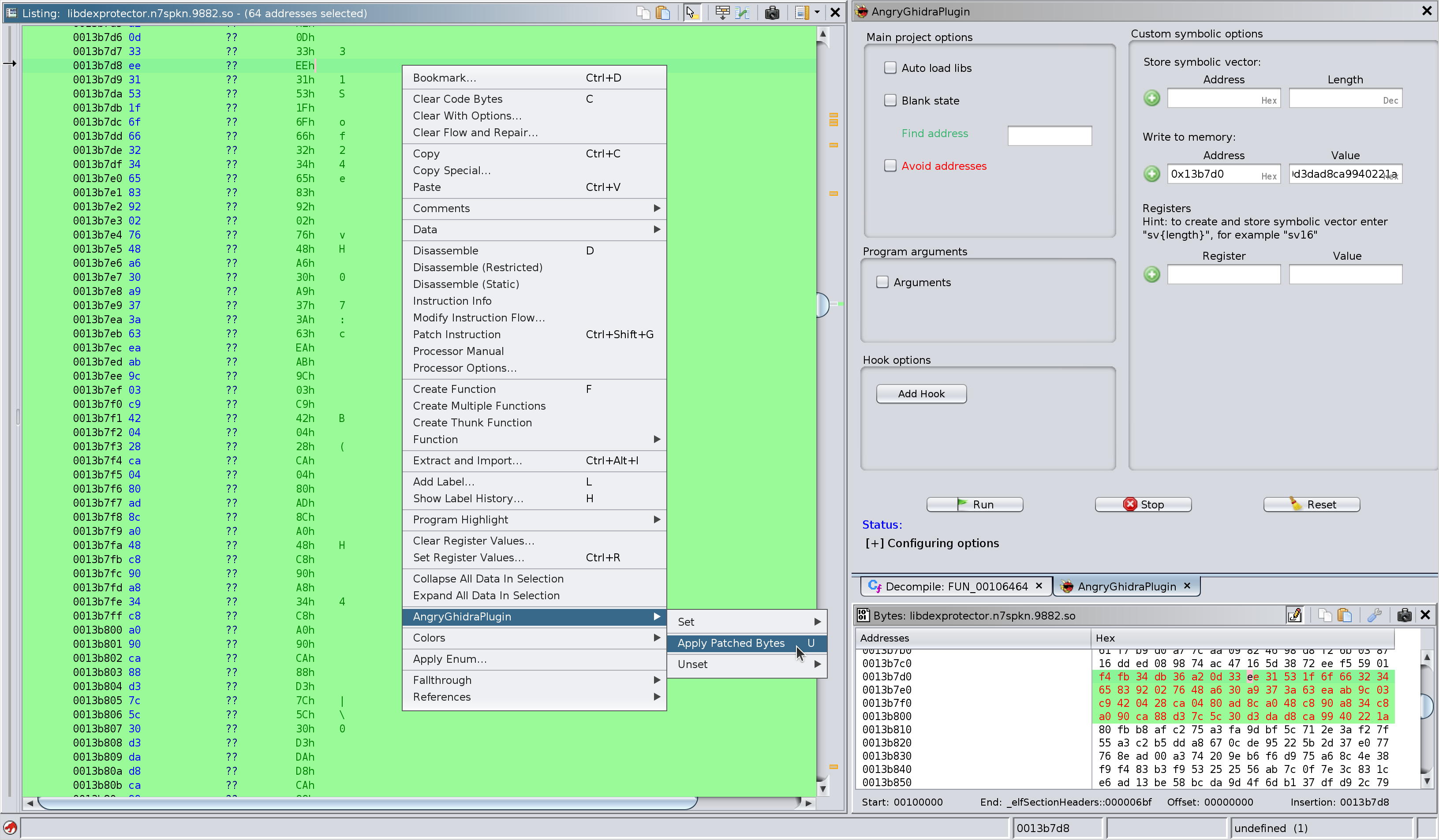
Screenshots
Apply patched bytes to write them to the memory of angr project:
Installation
-
pip3 install angrat first - Make sure that python3 directory added to the
PATH(necessarily) - Download Release version of extension and install it in Ghidra
File → Install Extensions... - Use gradle to build extension:
GHIDRA_INSTALL_DIR=${GHIDRA_HOME} gradleand use Ghidra to install it:File → Install Extensions... - Clone this repository to
\Ghidra\Extensionsdirectory.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].