TophantTechnology / Arl
ARL(Asset Reconnaissance Lighthouse)资产侦察灯塔系统旨在快速侦察与目标关联的互联网资产,构建基础资产信息库。 协助甲方安全团队或者渗透测试人员有效侦察和检索资产,发现存在的薄弱点和攻击面。
Stars: ✭ 1,357
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Arl
Awesome Bbht
A bash script that will automatically install a list of bug hunting tools that I find interesting for recon, exploitation, etc. (minus burp) For Ubuntu/Debain.
Stars: ✭ 190 (-86%)
Mutual labels: security-tools, recon, bugbounty
vaf
Vaf is a cross-platform very advanced and fast web fuzzer written in nim
Stars: ✭ 294 (-78.33%)
Mutual labels: recon, bugbounty, pentest-tool
Deksterecon
Web Application recon automation
Stars: ✭ 109 (-91.97%)
Mutual labels: security-tools, recon, bugbounty
Recon My Way
This repository created for personal use and added tools from my latest blog post.
Stars: ✭ 271 (-80.03%)
Mutual labels: security-tools, recon, bugbounty
Oneforall
OneForAll是一款功能强大的子域收集工具
Stars: ✭ 4,202 (+209.65%)
Mutual labels: pentest-tool, recon, bugbounty
Hosthunter
HostHunter a recon tool for discovering hostnames using OSINT techniques.
Stars: ✭ 427 (-68.53%)
Mutual labels: security-tools, recon, bugbounty
Rengine
reNgine is an automated reconnaissance framework for web applications with a focus on highly configurable streamlined recon process via Engines, recon data correlation and organization, continuous monitoring, backed by a database, and simple yet intuitive User Interface. reNgine makes it easy for penetration testers to gather reconnaissance with…
Stars: ✭ 3,439 (+153.43%)
Mutual labels: security-tools, recon, bugbounty
Recon Pipeline
An automated target reconnaissance pipeline.
Stars: ✭ 278 (-79.51%)
Mutual labels: security-tools, recon, bugbounty
Osmedeus
Fully automated offensive security framework for reconnaissance and vulnerability scanning
Stars: ✭ 3,391 (+149.89%)
Mutual labels: security-tools, pentest-tool, bugbounty
Watchdog
Watchdog - A Comprehensive Security Scanning and a Vulnerability Management Tool.
Stars: ✭ 345 (-74.58%)
Mutual labels: security-tools, pentest-tool, bugbounty
Bigbountyrecon
BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of initial reconnaissance on the target organisation.
Stars: ✭ 541 (-60.13%)
Mutual labels: pentest-tool, recon, bugbounty
Bypass Firewalls By Dns History
Firewall bypass script based on DNS history records. This script will search for DNS A history records and check if the server replies for that domain. Handy for bugbounty hunters.
Stars: ✭ 739 (-45.54%)
Mutual labels: security-tools, bugbounty
Interlace
Easily turn single threaded command line applications into a fast, multi-threaded application with CIDR and glob support.
Stars: ✭ 760 (-43.99%)
Mutual labels: security-tools, bugbounty
Vhostscan
A virtual host scanner that performs reverse lookups, can be used with pivot tools, detect catch-all scenarios, work around wildcards, aliases and dynamic default pages.
Stars: ✭ 767 (-43.48%)
Mutual labels: security-tools, bugbounty
Dumpsterfire
"Security Incidents In A Box!" A modular, menu-driven, cross-platform tool for building customized, time-delayed, distributed security events. Easily create custom event chains for Blue- & Red Team drills and sensor / alert mapping. Red Teams can create decoy incidents, distractions, and lures to support and scale their operations. Build event sequences ("narratives") to simulate realistic scenarios and generate corresponding network and filesystem artifacts.
Stars: ✭ 775 (-42.89%)
Mutual labels: security-tools, pentest-tool
Exploitpack
Exploit Pack -The next generation exploit framework
Stars: ✭ 728 (-46.35%)
Mutual labels: security-tools, pentest-tool
Evillimiter
Tool that monitors, analyzes and limits the bandwidth of devices on the local network without administrative access.
Stars: ✭ 764 (-43.7%)
Mutual labels: security-tools, pentest-tool
Urlhunter
a recon tool that allows searching on URLs that are exposed via shortener services
Stars: ✭ 934 (-31.17%)
Mutual labels: recon, bugbounty
Gitgot
Semi-automated, feedback-driven tool to rapidly search through troves of public data on GitHub for sensitive secrets.
Stars: ✭ 964 (-28.96%)
Mutual labels: security-tools, recon
ARL(Asset Reconnaissance Lighthouse)资产侦察灯塔系统
资产灯塔,不仅仅是域名收集
简介
旨在快速侦察与目标关联的互联网资产,构建基础资产信息库。 协助甲方安全团队或者渗透测试人员有效侦察和检索资产,发现存在的薄弱点和攻击面。
在开始使用之前,请务必阅读并同意免责声明中的条款,否则请勿下载安装使用本系统。
系统要求
目前暂不支持Windows。Linux和MAC建议采用Docker运行,系统配置最低2核4G。
由于自动资产发现过程中会有大量的的发包,建议采用云服务器可以带来更好的体验。
Docker 启动
拉取镜像
docker pull tophant/arl
docker-compose 启动
git clone https://github.com/TophantTechnology/ARL
cd ARL/docker/
docker-compose up -d
详细说明可以参考: Docker 环境安装 ARL
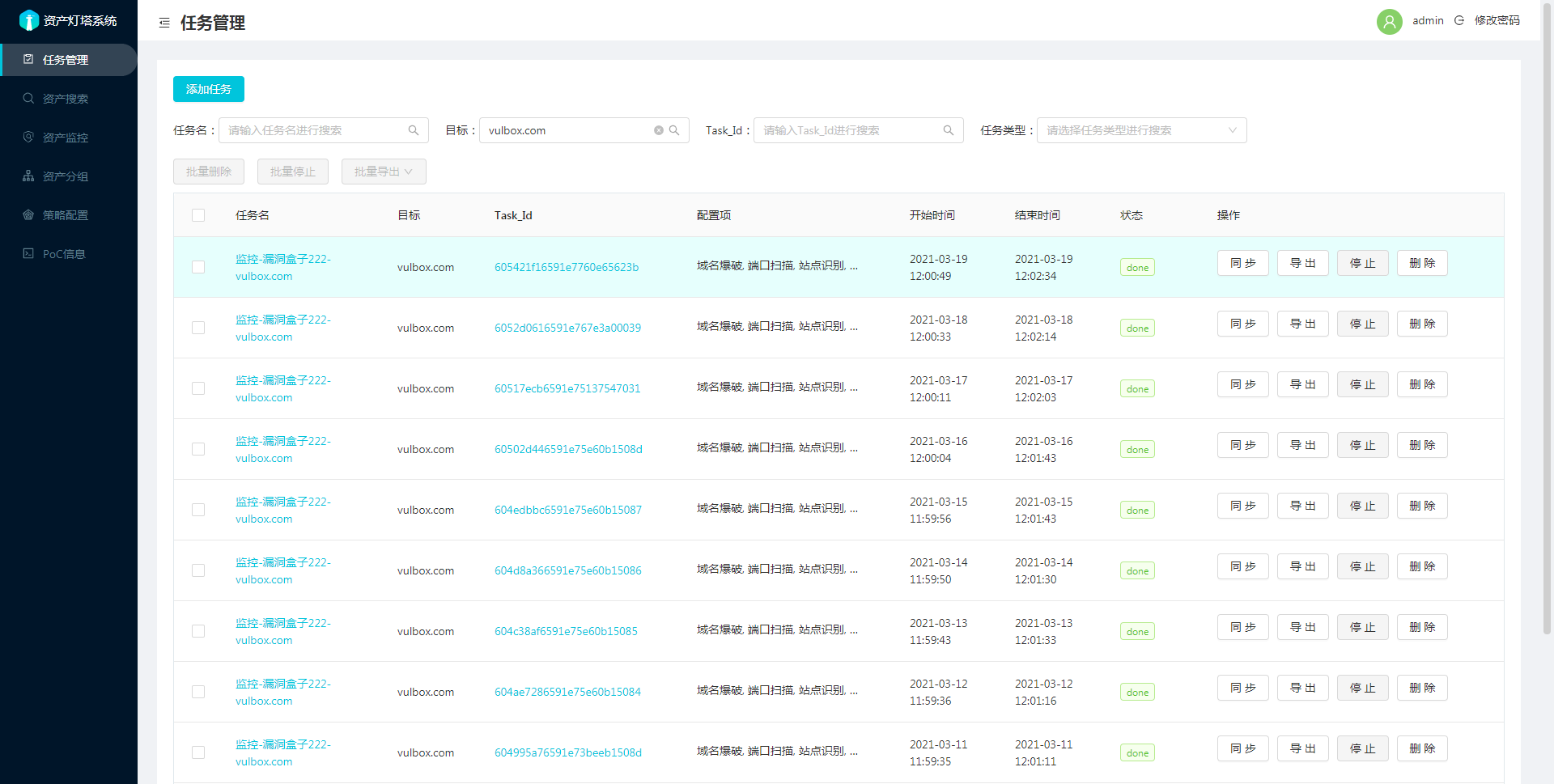
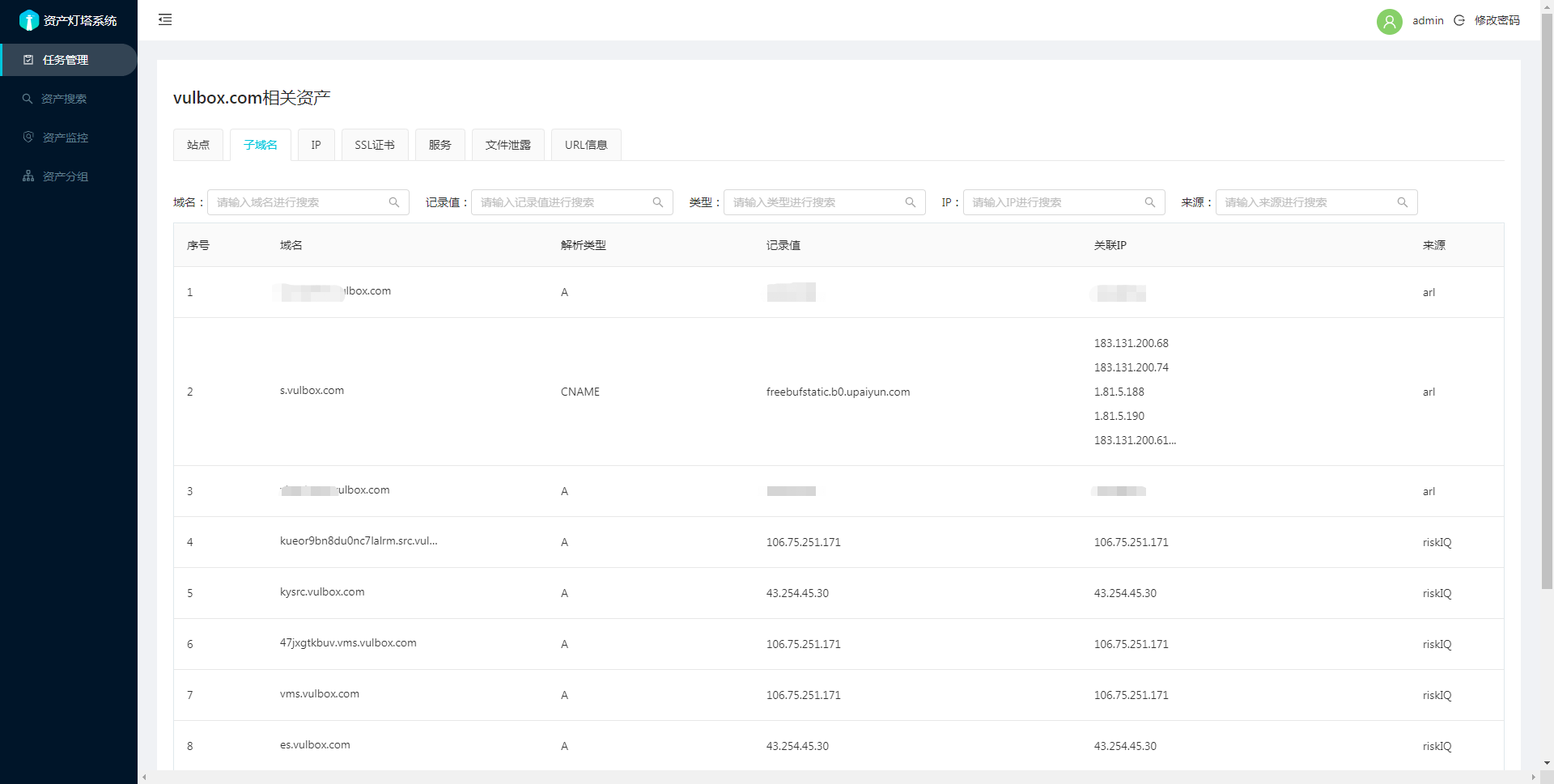
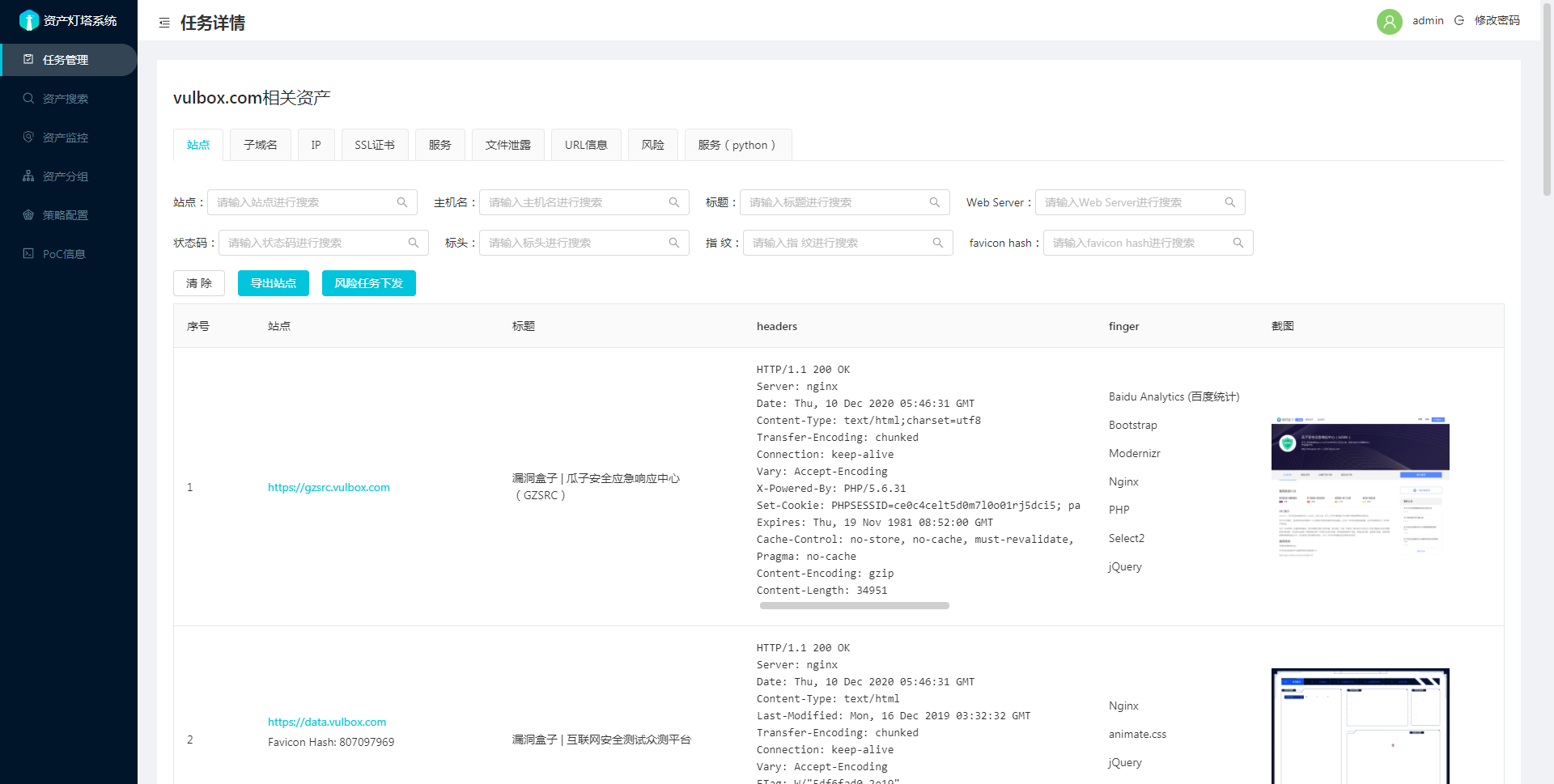
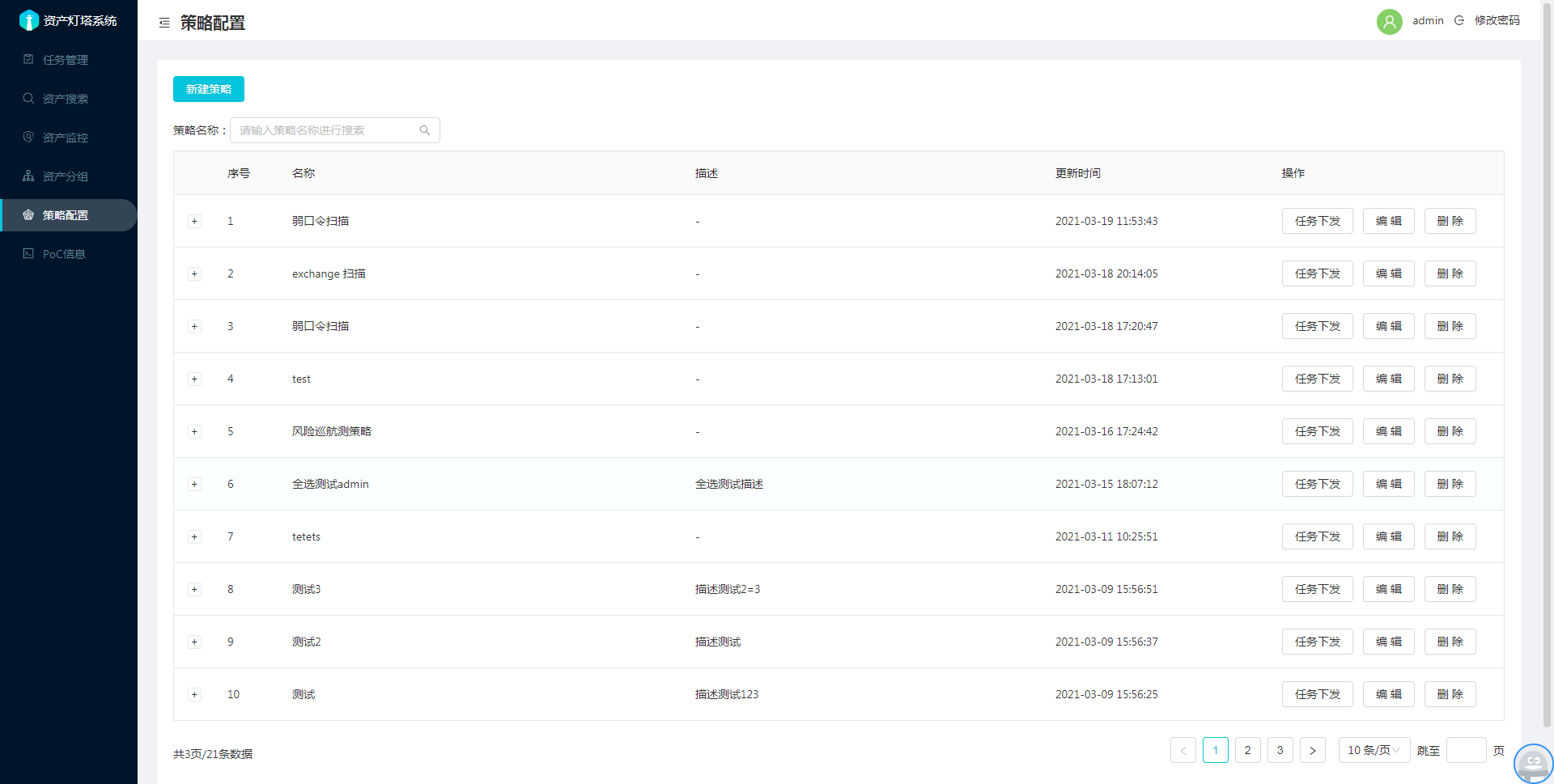
截图
登录页面,默认端口5003 (https), 默认用户名密码admin/arlpass
资产监控页面
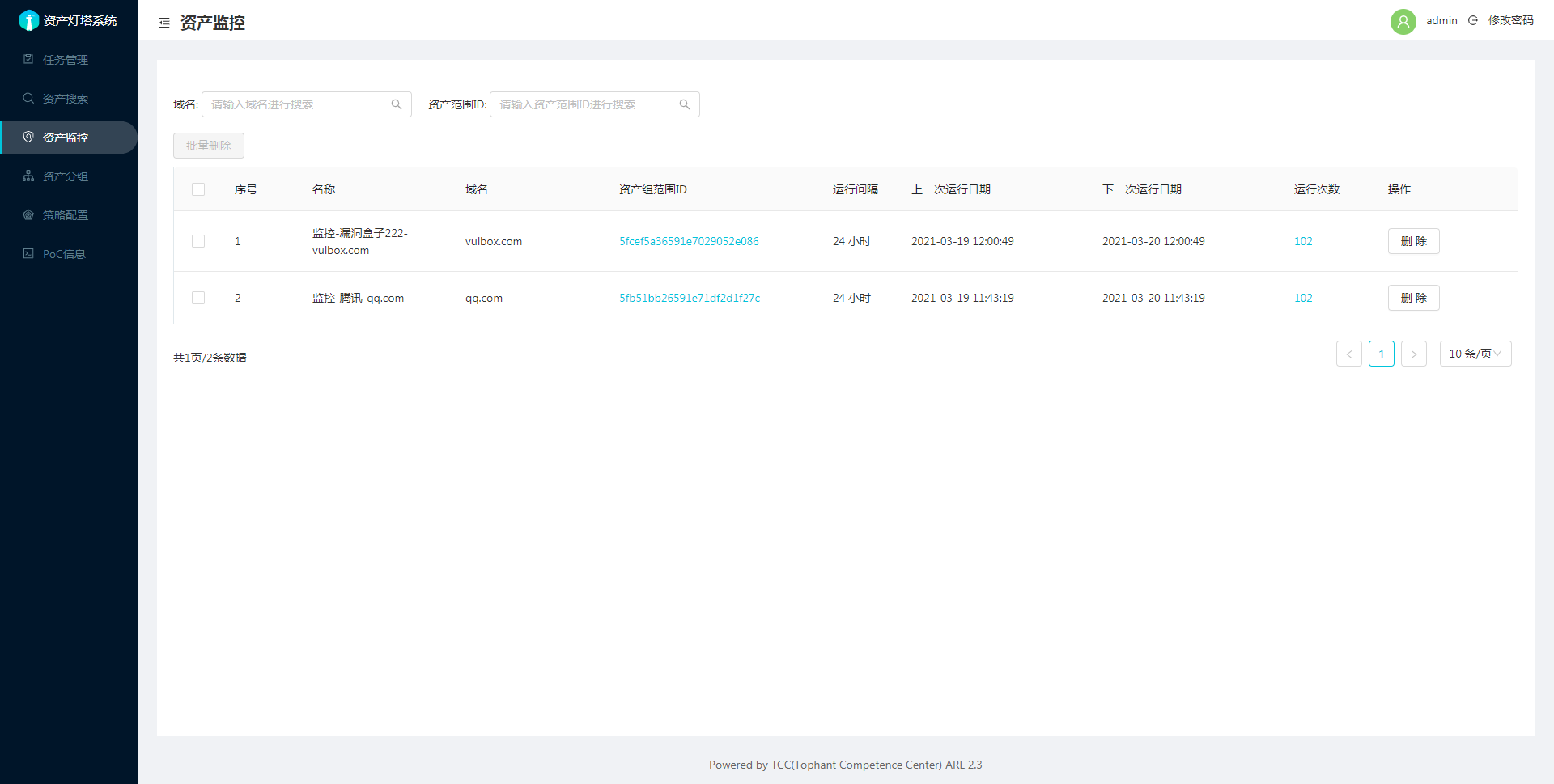 详细说明可以参考:资产分组和监控功能使用说明
详细说明可以参考:资产分组和监控功能使用说明
筛选站点进行任务下发
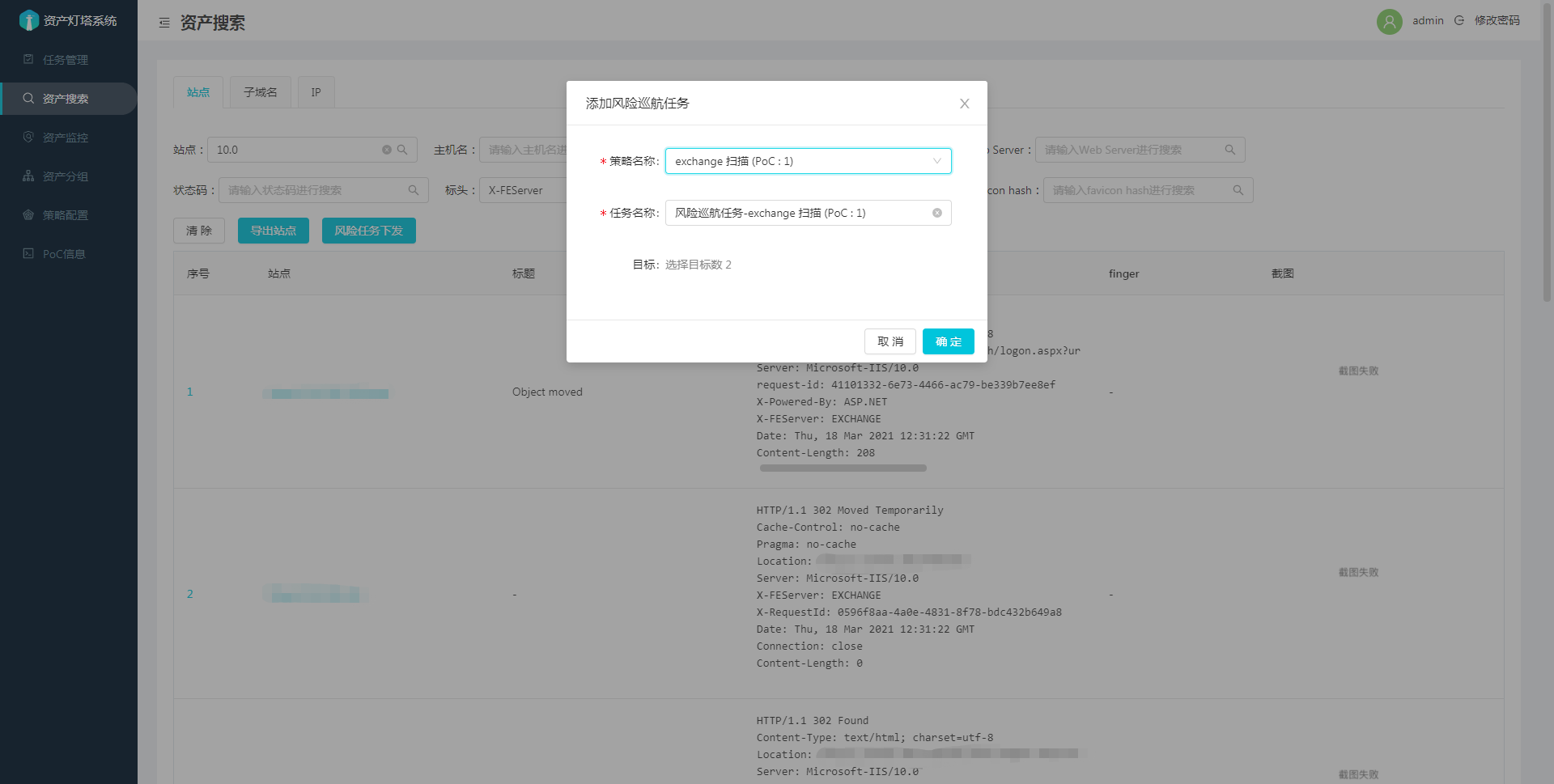 详细说明可以参考: 2.3-新添加功能详细说明
详细说明可以参考: 2.3-新添加功能详细说明
任务选项说明
| 编号 | 选项 | 说明 |
|---|---|---|
| 1 | 任务名称 | 任务名称 |
| 2 | 任务目标 | 任务目标,支持IP,IP段和域名。可一次性下发多个目标 |
| 3 | 域名爆破类型 | 对域名爆破字典大小, 大字典:常用2万字典大小。测试:少数几个字典,常用于测试功能是否正常 |
| 4 | 端口扫描类型 | ALL:全部端口,TOP1000:常用top 1000端口,TOP100:常用top 100端口,测试:少数几个端口 |
| 5 | 域名爆破 | 是否开启域名爆破 |
| 6 | DNS字典智能生成 | 根据已有的域名生成字典进行爆破 |
| 7 | Riskiq 调用 | 利用RiskIQ API进行查询域名 |
| 8 | ARL 历史查询 | 对arl历史任务结果进行查询用于本次任务 |
| 9 | 端口扫描 | 是否开启端口扫描,不开启站点会默认探测80,443 |
| 10 | 服务识别 | 是否进行服务识别,有可能会被防火墙拦截导致结果为空 |
| 11 | 操作系统识别 | 是否进行操作系统识别,有可能会被防火墙拦截导致结果为空 |
| 12 | Fofa IP查询 | 利用Fofa API进行查询域名 |
| 13 | SSL 证书获取 | 对端口进行SSL 证书获取 |
| 14 | 站点识别 | 对站点进行指纹识别 |
| 15 | 搜索引擎调用 | 利用搜索引擎结果爬取对应的URL |
| 16 | 站点爬虫 | 利用静态爬虫对站点进行爬取对应的URL |
| 17 | 站点截图 | 对站点首页进行截图 |
| 18 | 文件泄露 | 对站点进行文件泄露检测,会被WAF拦截 |
配置参数说明
Docker环境配置文件路径 docker/config-docker.yaml
| 配置 | 说明 |
|---|---|
| CELERY.BROKER_URL | rabbitmq连接信息 |
| MONGO | mongo 连接信息 |
| RISKIQ | riskiq API 配置信息 |
| GEOIP | GEOIP 数据库路径信息 |
| FOFA | FOFA API 配置信息 |
| ARL.AUTH | 是否开启认证,不开启有安全风险 |
| ARL.API_KEY | arl后端API调用key,如果设置了请注意保密 |
| ARL.BLACK_IPS | 为了防止SSRF,屏蔽的IP地址或者IP段 |
| ARL.PORT_TOP_10 | 自定义端口,对应前端端口测试选项 |
| ARL.DOMAIN_DICT | 域名爆破字典,对应前端大字典选项 |
| ARL.FILE_LEAK_DICT | 文件泄漏字典 |
忘记密码重置
当忘记了登录密码,可以执行下面的命令,然后使用 admin/admin123 就可以登录了。
docker exec -ti arl_mongodb mongo -u admin -p admin
use arl
db.user.drop()
db.user.insert({ username: 'admin', password: hex_md5('[email protected]#'+'admin123') })
本地安装
下载安装phantomjs,要添加到环境变量
http://phantomjs.org/download.html
yum install epel-release
yum install mongodb-server mongodb rabbitmq-server supervisor
yum install wqy-microhei-fonts fontconfig
或者
sudo apt-get install mongodb-server rabbitmq-server supervisor
sudo apt-get install xfonts-wqy libfontconfig
安装 Nmap
Ubuntu
apt remove nmap
apt remove ndiff
apt install alien
wget https://nmap.org/dist/nmap-7.80-1.x86_64.rpm
alien -i nmap-7.80-1.x86_64.rpm
CentOS
rpm -vhU https://nmap.org/dist/nmap-7.80-1.x86_64.rpm
配置RabbitMQ
rabbitmqctl add_user arl arlpassword
rabbitmqctl add_vhost arlv2host
rabbitmqctl set_user_tags arl arltag
rabbitmqctl set_permissions -p arlv2host arl ".*" ".*" ".*"
本地编译Docker镜像 并启动
docker build -t arl_worker:v2 -f docker/worker/Dockerfile .
cd docker
pip install docker-compose
docker-compose up -d
配置GeoIP 数据库
由于官方政策更新请前往maxmind 注册下载GeoLite2-City.tar.gz,GeoLite2-ASN.tar.gz 解压。
在config.yaml中配置好相关路径
FAQ
请访问如下链接FAQ
写在最后
目前ARL仅仅只是完成了对资产的部分维度的发现和收集,自动发现过程中难免出现覆盖度不全、不精准、不合理等缺陷的地方还请反馈至我们。
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].