actions-rs / Audit Check
Programming Languages
Projects that are alternatives of or similar to Audit Check
Rust audit-check Action
Security vulnerabilities audit
This GitHub Action is using cargo-audit to perform an audit for crates with security vulnerabilities.
Usage
Audit changes
We can utilize the GitHub Actions ability to execute workflow only if the specific files were changed and execute this Action to check the changed dependencies:
name: Security audit
on:
push:
paths:
- '**/Cargo.toml'
- '**/Cargo.lock'
jobs:
security_audit:
runs-on: ubuntu-latest
steps:
- uses: actions/[email protected]
- uses: actions-rs/[email protected]
with:
token: ${{ secrets.GITHUB_TOKEN }}
It is recommended to add the paths: section into the workflow file,
as it would effectively speed up the CI pipeline, since the audit process
will not be performed if no dependencies were changed.
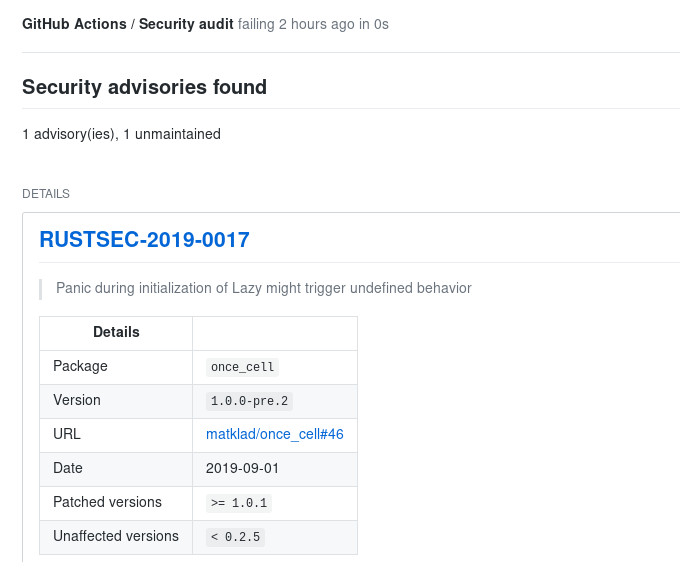
In case of any security advisories found, status check
created by this Action will be marked as "failed".
Note that informational advisories are not affecting the check status.
Limitations
Due to token permissions,
this Action WILL NOT be able to create Checks for Pull Requests from the forked repositories,
see actions-rs/clippy-check#2 for details.
As a fallback this Action will output all found advisories to the stdout.
It is expected that this behavior will be fixed later by GitHub.
Scheduled audit
Another option is to use schedule event
and execute this Action periodically against the HEAD of repository default branch.
name: Security audit
on:
schedule:
- cron: '0 0 * * *'
jobs:
audit:
runs-on: ubuntu-latest
steps:
- uses: actions/[email protected]
- uses: actions-rs/[email protected]
with:
token: ${{ secrets.GITHUB_TOKEN }}
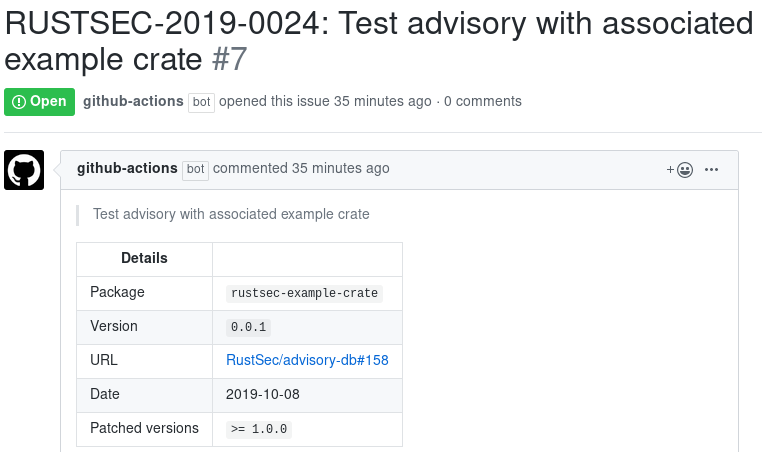
With this example Action will be executed periodically at midnight of each day
and check if there any new advisories appear for crate dependencies.
For each new advisory (including informal) an issue will be created:
Inputs
| Name | Required | Description | Type | Default |
|---|---|---|---|---|
token |
✓ |
GitHub token, usually a ${{ secrets.GITHUB_TOKEN }}
|
string |