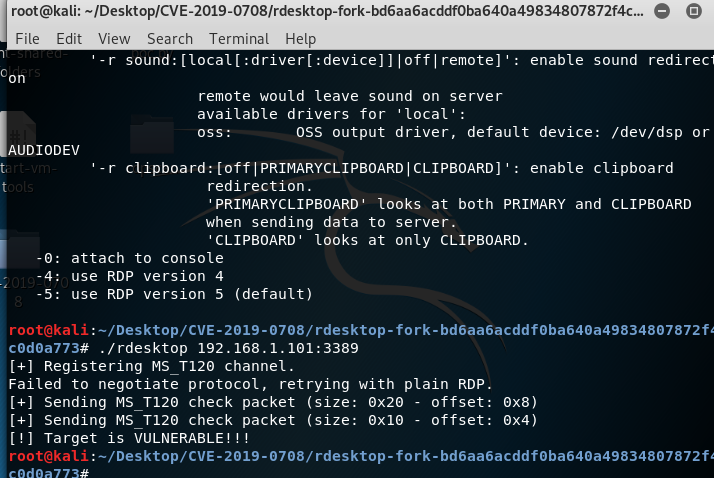
Ladon大型内网渗透扫描器&Cobalt Strike,Ladon8.9内置120个模块,包含信息收集/存活主机/端口扫描/服务识别/密码爆破/漏洞检测/漏洞利用。漏洞检测含MS17010/SMBGhost/Weblogic/ActiveMQ/Tomcat/Struts2,密码口令爆破(Mysql/Oracle/MSSQL)/FTP/SSH(Linux)/VNC/Windows(IPC/WMI/SMB/Netbios/LDAP/SmbHash/WmiHash/Winrm),远程执行命令(smbexec/wmiexe/psexec/atexec/sshexec/webshell),降权提权Runas、GetSystem,Poc/Exploit,支持Cobalt Strike 3.X-4.0
Stars: ✭ 2,911 (+731.71%)
Mutual labels: hacking, exploit, pentest, poc
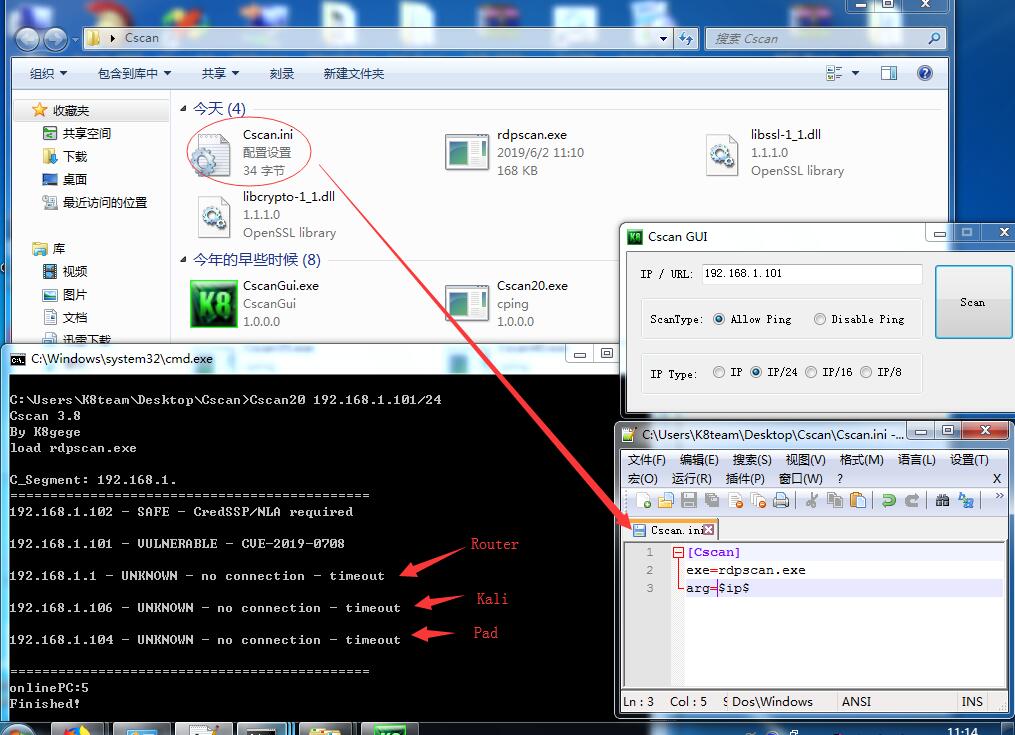
K8cscanK8Cscan大型内网渗透自定义插件化扫描神器,包含信息收集、网络资产、漏洞扫描、密码爆破、漏洞利用,程序采用多线程批量扫描大型内网多个IP段C段主机,目前插件包含: C段旁注扫描、子域名扫描、Ftp密码爆破、Mysql密码爆破、Oracle密码爆破、MSSQL密码爆破、Windows/Linux系统密码爆破、存活主机扫描、端口扫描、Web信息探测、操作系统版本探测、Cisco思科设备扫描等,支持调用任意外部程序或脚本,支持Cobalt Strike联动
Stars: ✭ 693 (+98%)
Mutual labels: hacking, exploit, pentest, poc
K8toolsK8工具合集(内网渗透/提权工具/远程溢出/漏洞利用/扫描工具/密码破解/免杀工具/Exploit/APT/0day/Shellcode/Payload/priviledge/BypassUAC/OverFlow/WebShell/PenTest) Web GetShell Exploit(Struts2/Zimbra/Weblogic/Tomcat/Apache/Jboss/DotNetNuke/zabbix)
Stars: ✭ 4,173 (+1092.29%)
Mutual labels: hacking, exploit, pentest, poc
PowerladonLadon Network Penetration Scanner for PowerShell, vulnerability / exploit / detection / MS17010/SmbGhost,Brute-Force SMB/IPC/WMI/NBT/SSH/FTP/MSSQL/MYSQL/ORACLE/VNC
Stars: ✭ 39 (-88.86%)
Mutual labels: hacking, exploit, pentest, poc
Pwn jenkinsNotes about attacking Jenkins servers
Stars: ✭ 841 (+140.29%)
Mutual labels: hacking, exploit, pentest
PentestingMisc. Public Reports of Penetration Testing and Security Audits.
Stars: ✭ 24 (-93.14%)
Mutual labels: exploit, poc, pentest
Thc ArchiveAll releases of the security research group (a.k.a. hackers) The Hacker's Choice
Stars: ✭ 474 (+35.43%)
Mutual labels: hacking, exploit, pentest
XattackerX Attacker Tool ☣ Website Vulnerability Scanner & Auto Exploiter
Stars: ✭ 897 (+156.29%)
Mutual labels: hacking, exploit, pentest
Pythempentest framework
Stars: ✭ 1,060 (+202.86%)
Mutual labels: hacking, exploit, pentest
Cve 2019 0708 ToolA social experiment
Stars: ✭ 87 (-75.14%)
Mutual labels: hacking, exploit, poc
Cve 2019 0604cve-2019-0604 SharePoint RCE exploit
Stars: ✭ 91 (-74%)
Mutual labels: hacking, exploit, pentest
MS17010EXPLadon Moudle MS17010 Exploit for PowerShell
Stars: ✭ 40 (-88.57%)
Mutual labels: exploit, pentest
YAPSYet Another PHP Shell - The most complete PHP reverse shell
Stars: ✭ 35 (-90%)
Mutual labels: exploit, pentest
Exploit-DevelopmentExploit Development - Weaponized Exploit and Proof of Concepts (PoC)
Stars: ✭ 84 (-76%)
Mutual labels: exploit, poc
CVE-2021-33766ProxyToken (CVE-2021-33766) : An Authentication Bypass in Microsoft Exchange Server POC exploit
Stars: ✭ 37 (-89.43%)
Mutual labels: exploit, poc
Offensive DockerOffensive Docker is an image with the more used offensive tools to create an environment easily and quickly to launch assessment to the targets.
Stars: ✭ 328 (-6.29%)
Mutual labels: hacking, pentest
Jenkins Rce😈 Jenkins RCE PoC. From unauthenticated user to remote code execution, it's a hacker's dream!
Stars: ✭ 262 (-25.14%)
Mutual labels: hacking, exploit
Commodity Injection SignaturesCommodity Injection Signatures, Malicious Inputs, XSS, HTTP Header Injection, XXE, RCE, Javascript, XSLT
Stars: ✭ 267 (-23.71%)
Mutual labels: exploit, poc