VDOO-Connected-Trust / Ghidra Pyi Generator
Programming Languages
Labels
Projects that are alternatives of or similar to Ghidra Pyi Generator
Ghidra .pyi Generator
The Ghidra .pyi Generator generates .pyi type stubs
for the entire Ghidra API.
Those stub files can later be used in PyCharm to enhance the development experience.
You can either use the stubs released here, or follow the instructions below to generate them yourself.
To use the stubs in PyCharm, follow the instructions in Install, uninstall, and upgrade interpreter paths.
Using The Stubs
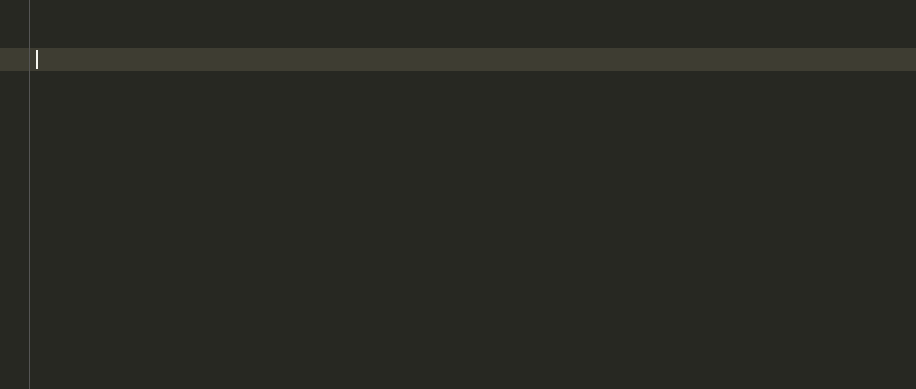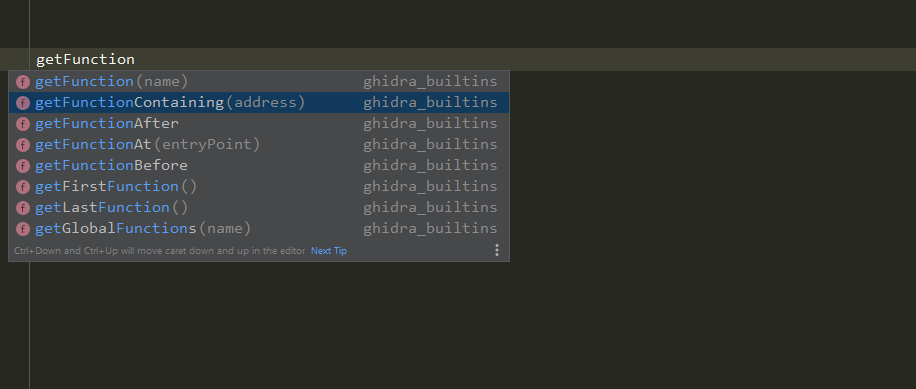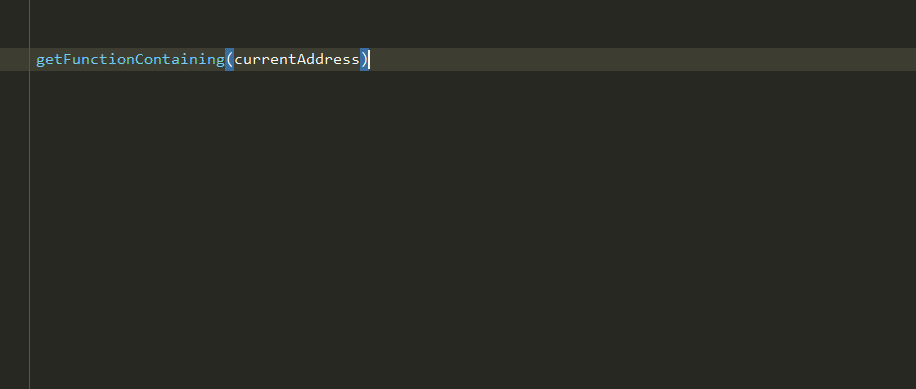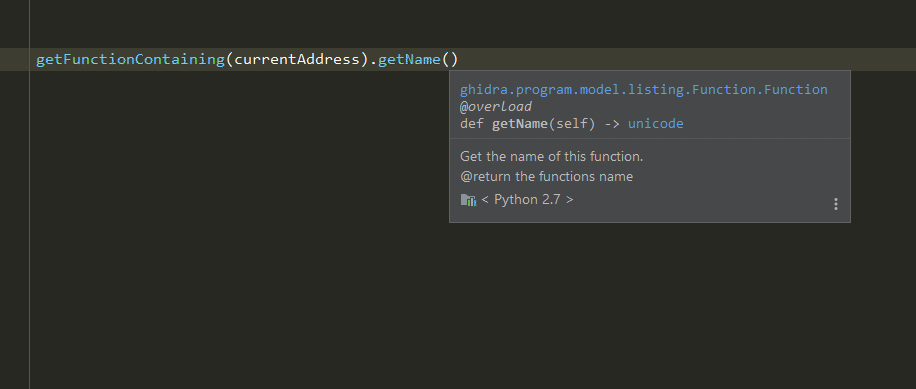
Once installed, all you need to do is import the Ghidra modules as usual, and PyCharm will do the rest.
import ghidra
To get support for the Ghidra builtins, you need to import them as well. The type hints for those exist in
the generated ghidra_builtins.pyi stub. Since it is not a real Python module, importing it at runtime will fail.
But the .pyi gives PyCharm all the information it needs to help you.
try:
from ghidra_builtins import *
except:
pass
Once done, just code & enjoy.
Dependencies
Ghidra Docs
To properly extract all types from Ghidra, make sure to extract the API documentation.
- Open the Ghidra CodeBrowser
- Go to
Help -> Ghidra API Help - Wait for Ghidra to extract the docs
Python Packages
The script depends on both the attr and typing packages.
# Create a virtualenv for Ghidra packages.
# It is important to use Python2.7 for this venv!
# If you want, you can skip this step and use your default Python installation.
mkvirtualenv -p python2.7 ghidra
# Create Jython's site-pacakges directory.
jython_site_packages=~/.local/lib/jython2.7/site-packages
mkdir -p $jython_site_packages
# Create a PTH file to point Jython to Python's site-packages directories.
# Again, this has to be Python2.7.
# Outside a virtualenv, use
python2.7 -c "import site; print(site.getusersitepackages()); print(site.getsitepackages()[-1])" > $jython_site_packages/python.pth
# If using virtualenv, use the following instead
python2.7 -c "from distutils.sysconfig import get_python_lib; print(get_python_lib())" > $jython_site_packages/python.pth
# Use pip to install packages for Ghidra
pip install attrs typing
Creating the .pyi files
GUI
- Add this directory to the
Script Directoriesin the Ghidra Script Manager - Refresh the script list
- Run
generate_ghidra_pyi.py(will be located underIDE Helpers) - When a directory-selection dialog appears, choose the directory you'd like to save the
.pyifiles in.
CLI
$GHIDRA_ROOT/support/analyzeHeadless /tmp tmp -scriptPath $(pwd) -preScript generate_ghidra_pyi.py ./
Python Package
generate_ghidra_pyi.py generates a setup.py inside the directory that was selected.
This allows using pip install to install a PEP 561 stub package that is recognized by PyCharm and other tools as containing type information for the ghidra module.