ghidraninja / Ghidra_scripts
Licence: gpl-3.0
Scripts for the Ghidra software reverse engineering suite.
Projects that are alternatives of or similar to Ghidra scripts
YobiYara Based Detection Engine for web browsers
Stars: ✭ 39 (-94.67%)
Mutual labels: yara
StoqAn open source framework for enterprise level automated analysis.
Stars: ✭ 352 (-51.91%)
Mutual labels: yara
MultiscannerModular file scanning/analysis framework
Stars: ✭ 494 (-32.51%)
Mutual labels: yara
HamburglarHamburglar -- collect useful information from urls, directories, and files
Stars: ✭ 321 (-56.15%)
Mutual labels: yara
StrelkaReal-time, container-based file scanning at enterprise scale
Stars: ✭ 387 (-47.13%)
Mutual labels: yara
yarasploitYaraSploit is a collection of Yara rules generated from Metasploit framework shellcodes.
Stars: ✭ 31 (-95.77%)
Mutual labels: yara
Mitigating Web ShellsGuidance for mitigation web shells. #nsacyber
Stars: ✭ 698 (-4.64%)
Mutual labels: yara
Icewater16,432 Free Yara rules created by
Stars: ✭ 324 (-55.74%)
Mutual labels: yara
YaraThe pattern matching swiss knife
Stars: ✭ 5,209 (+611.61%)
Mutual labels: yara
Freki🐺 Malware analysis platform
Stars: ✭ 285 (-61.07%)
Mutual labels: yara
Python IocextractDefanged Indicator of Compromise (IOC) Extractor.
Stars: ✭ 300 (-59.02%)
Mutual labels: yara
ThreatingestorExtract and aggregate threat intelligence.
Stars: ✭ 439 (-40.03%)
Mutual labels: yara
MqueryYARA malware query accelerator (web frontend)
Stars: ✭ 264 (-63.93%)
Mutual labels: yara
freki🐺 Malware analysis platform
Stars: ✭ 327 (-55.33%)
Mutual labels: yara
Yara PythonThe Python interface for YARA
Stars: ✭ 368 (-49.73%)
Mutual labels: yara
ManalyzeA static analyzer for PE executables.
Stars: ✭ 701 (-4.23%)
Mutual labels: yara
Die EngineDIE engine
Stars: ✭ 648 (-11.48%)
Mutual labels: yara
PeframePEframe is a open source tool to perform static analysis on Portable Executable malware and malicious MS Office documents.
Stars: ✭ 472 (-35.52%)
Mutual labels: yara
ghidra_scripts
Scripts for the Ghidra software reverse engineering suite.
Installation
In the Ghidra Script Manager click the "Script Directories" icon in the toolbar and add the checked out repository as a path. Scripts from this collection will appear in the "Ghidra Ninja" category.
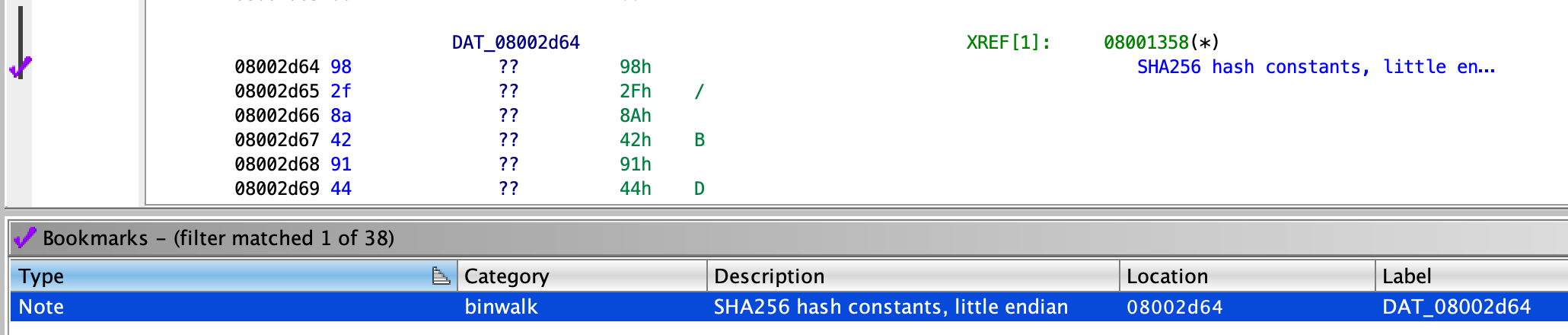
binwalk.py
Runs binwalk on the current program and bookmarks the findings. Requires binwalk to be in $PATH.
yara.py
Automatically find crypto constants in the loaded program - allows to very quickly identify crypto code.
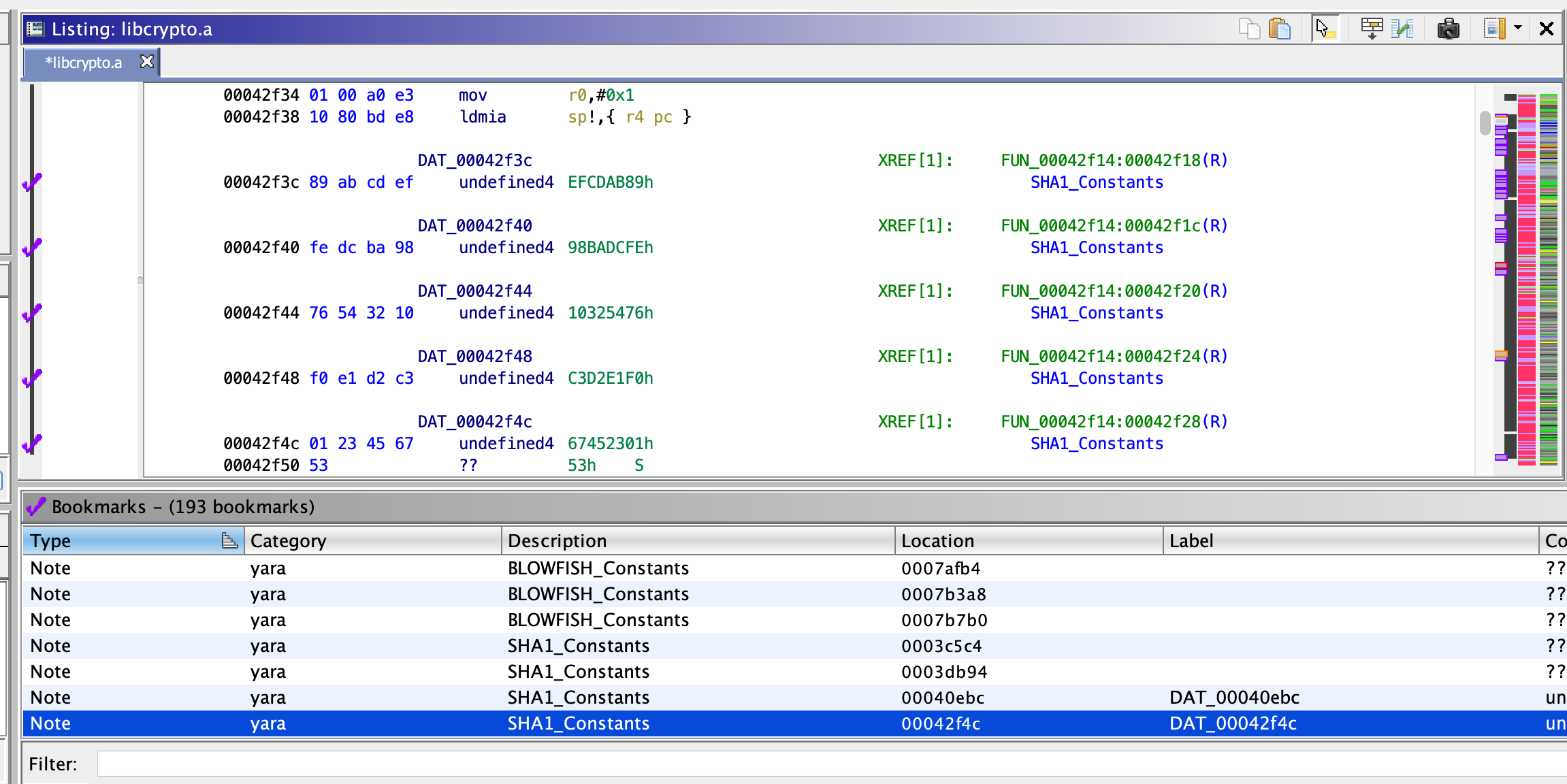
Runs yara with the patterns found in yara-crypto.yar on the current program. The Yara rules are licensed under GPLv2. In addition @phoul's SHA256 rule was added.
Requires yara to be in $PATH.
export_gameboy_rom.py
Exports working ROMs from ROMs imported using Gekkio's GhidraBoy.
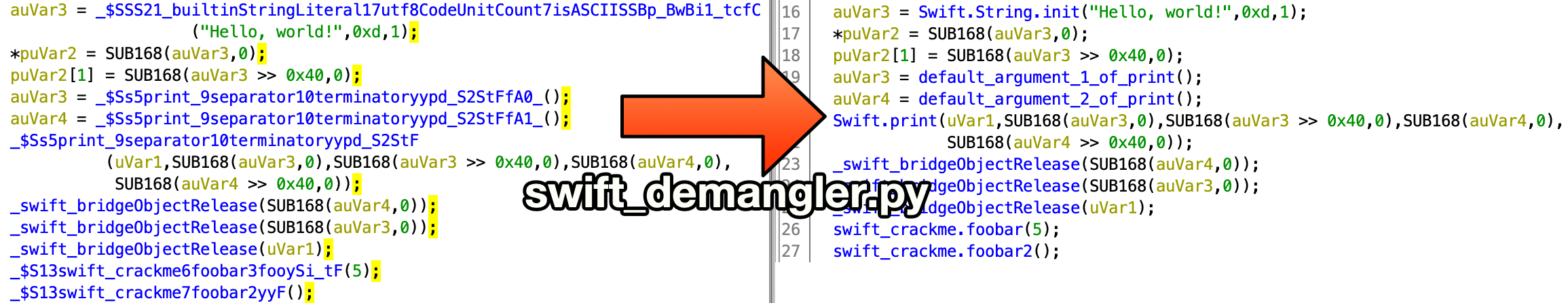
swift_demangler.py
Automatically demangle swift function names. For more complex functions it adds the full demangled name into the function comment. Requires swift to be in $PATH.
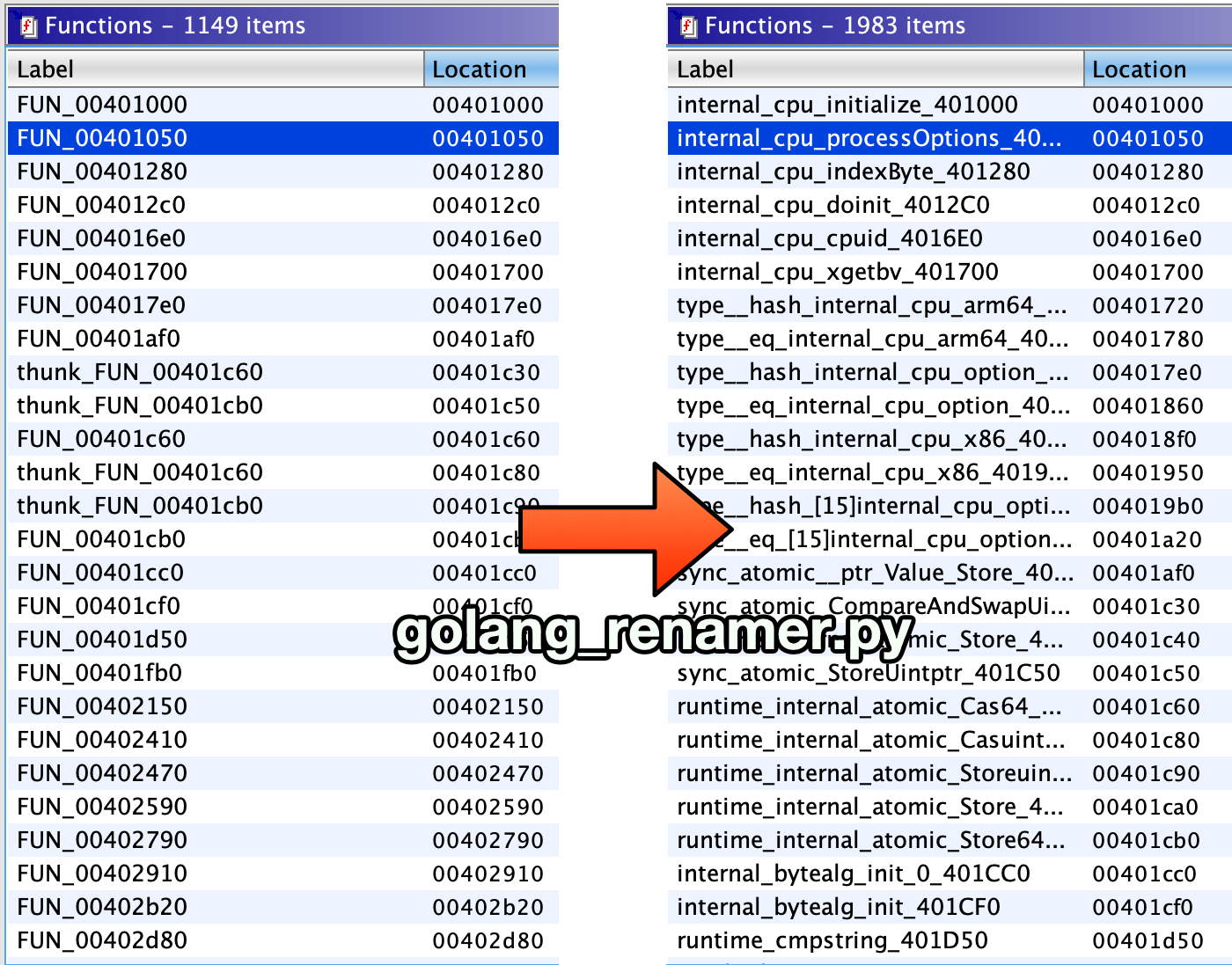
golang_renamer.py
Restores function names from a stripped Go binary. This script was contributed by QwErTy (QwErTyReverse on Telegram) and is a port of George Zaytsev's go_renamer.py.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at
[email protected].




