madhuakula / Hacker Container
Licence: mit
Container with all the list of useful tools/commands while hacking and pentesting Kubernetes Clusters
Stars: ✭ 105
Labels
Projects that are alternatives of or similar to Hacker Container
Cloakify
CloakifyFactory - Data Exfiltration & Infiltration In Plain Sight; Convert any filetype into list of everyday strings, using Text-Based Steganography; Evade DLP/MLS Devices, Defeat Data Whitelisting Controls, Social Engineering of Analysts, Evade AV Detection
Stars: ✭ 1,136 (+981.9%)
Mutual labels: hacking, security-tools, pentesting, pentest, infosec
Dumpsterfire
"Security Incidents In A Box!" A modular, menu-driven, cross-platform tool for building customized, time-delayed, distributed security events. Easily create custom event chains for Blue- & Red Team drills and sensor / alert mapping. Red Teams can create decoy incidents, distractions, and lures to support and scale their operations. Build event sequences ("narratives") to simulate realistic scenarios and generate corresponding network and filesystem artifacts.
Stars: ✭ 775 (+638.1%)
Mutual labels: hacking, security-tools, pentesting, pentest, infosec
Crithit
Takes a single wordlist item and tests it one by one over a large collection of websites before moving onto the next. Create signatures to cross-check vulnerabilities over multiple hosts.
Stars: ✭ 182 (+73.33%)
Mutual labels: hacking, security-tools, pentesting, infosec
Awesome Shodan Queries
🔍 A collection of interesting, funny, and depressing search queries to plug into shodan.io 👩💻
Stars: ✭ 2,758 (+2526.67%)
Mutual labels: hacking, security-tools, pentesting, infosec
Spiderfoot
SpiderFoot automates OSINT for threat intelligence and mapping your attack surface.
Stars: ✭ 6,882 (+6454.29%)
Mutual labels: infosec, pentesting, pentest, security-tools
Diamorphine
LKM rootkit for Linux Kernels 2.6.x/3.x/4.x/5.x (x86/x86_64 and ARM64)
Stars: ✭ 725 (+590.48%)
Mutual labels: hacking, security-tools, pentesting, pentest
Sippts
Set of tools to audit SIP based VoIP Systems
Stars: ✭ 116 (+10.48%)
Mutual labels: hacking, security-tools, pentesting, pentest
Cameradar
Cameradar hacks its way into RTSP videosurveillance cameras
Stars: ✭ 2,775 (+2542.86%)
Mutual labels: hacking, security-tools, pentesting, infosec
Docker Security Images
🔐 Docker Container for Penetration Testing & Security
Stars: ✭ 172 (+63.81%)
Mutual labels: pentesting, pentest, infosec, container
A Red Teamer Diaries
RedTeam/Pentest notes and experiments tested on several infrastructures related to professional engagements.
Stars: ✭ 382 (+263.81%)
Mutual labels: hacking, security-tools, pentesting, tools
Security Tools
Collection of small security tools, mostly in Bash and Python. CTFs, Bug Bounty and other stuff.
Stars: ✭ 509 (+384.76%)
Mutual labels: hacking, security-tools, pentesting, infosec
Ladon
大型内网渗透扫描器&Cobalt Strike,Ladon8.9内置120个模块,包含信息收集/存活主机/端口扫描/服务识别/密码爆破/漏洞检测/漏洞利用。漏洞检测含MS17010/SMBGhost/Weblogic/ActiveMQ/Tomcat/Struts2,密码口令爆破(Mysql/Oracle/MSSQL)/FTP/SSH(Linux)/VNC/Windows(IPC/WMI/SMB/Netbios/LDAP/SmbHash/WmiHash/Winrm),远程执行命令(smbexec/wmiexe/psexec/atexec/sshexec/webshell),降权提权Runas、GetSystem,Poc/Exploit,支持Cobalt Strike 3.X-4.0
Stars: ✭ 2,911 (+2672.38%)
Mutual labels: hacking, security-tools, pentest, tools
Habu
Hacking Toolkit
Stars: ✭ 635 (+504.76%)
Mutual labels: hacking, security-tools, pentesting, pentest
Whatweb
Next generation web scanner
Stars: ✭ 3,503 (+3236.19%)
Mutual labels: hacking, security-tools, pentesting, pentest
Ios
Most usable tools for iOS penetration testing
Stars: ✭ 563 (+436.19%)
Mutual labels: security-tools, pentest, infosec, tools
Resources
A Storehouse of resources related to Bug Bounty Hunting collected from different sources. Latest guides, tools, methodology, platforms tips, and tricks curated by us.
Stars: ✭ 62 (-40.95%)
Mutual labels: hacking, security-tools, pentesting, infosec
Evillimiter
Tool that monitors, analyzes and limits the bandwidth of devices on the local network without administrative access.
Stars: ✭ 764 (+627.62%)
Mutual labels: hacking, security-tools, pentesting
Kubernetes Goat
Kubernetes Goat is "Vulnerable by Design" Kubernetes Cluster. Designed to be an intentionally vulnerable cluster environment to learn and practice Kubernetes security.
Stars: ✭ 868 (+726.67%)
Mutual labels: hacking, pentesting, container
Xattacker
X Attacker Tool ☣ Website Vulnerability Scanner & Auto Exploiter
Stars: ✭ 897 (+754.29%)
Mutual labels: hacking, security-tools, pentest
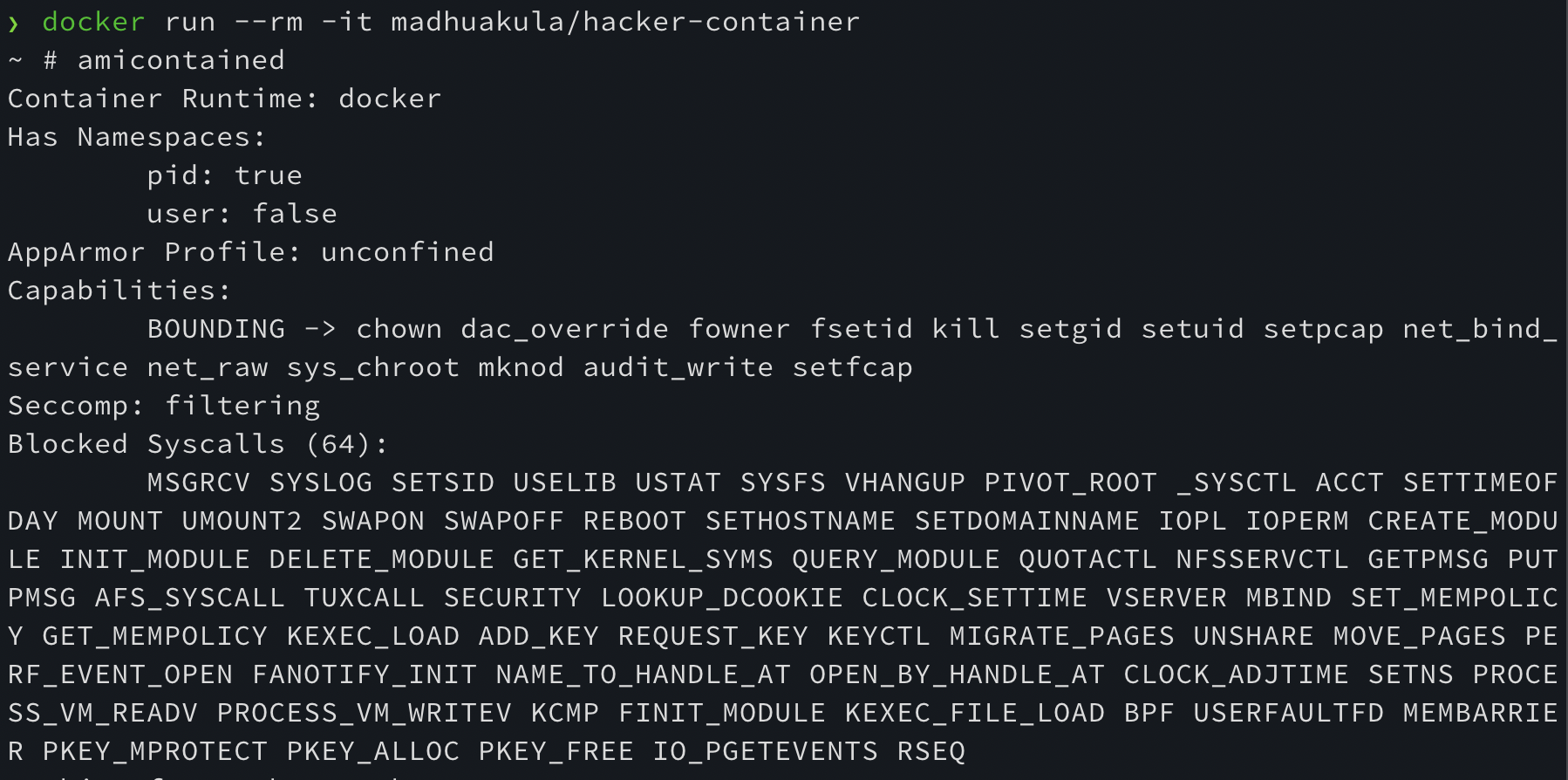
Hacker Container
Container with all the list of useful tools/commands while hacking Kubernetes Clusters. Read more about it in the blogpost https://blog.madhuakula.com/hacker-container-for-kubernetes-security-assessments-7d1522e96073
- List of the tools/commands/utilities available in container are list.todo
How to use Hacker Container
- Just run the following command to explore in the docker container environments
docker run --rm -it madhuakula/hacker-container
- To deploy as a Pod in Kubernetes cluster run the following command
kubectl run -it hacker-container --image=madhuakula/hacker-container
This container can be used in different ways in different environments, it aids your penetration testing or security assessments of container and Kubernetes cluster environments.
Hacker Container in Action
Feedback/Suggestions
Please feel free to create issue or make a pull request or tweet to me @madhuakula for improvements and suggestions
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].