blackploit / Hash Identifier
Software to identify the different types of hashes used to encrypt data and especially passwords
Stars: ✭ 198
Programming Languages
python
139335 projects - #7 most used programming language
Labels
Projects that are alternatives of or similar to Hash Identifier
Multihash
Self describing hashes - for future proofing
Stars: ✭ 656 (+231.31%)
Mutual labels: hash-functions
Nabhash
An extremely fast Non-crypto-safe AES Based Hash algorithm for Big Data
Stars: ✭ 62 (-68.69%)
Mutual labels: hash-functions
Plibsys
Highly portable C system library: threads and synchronization primitives, sockets (TCP, UDP, SCTP), IPv4 and IPv6, IPC, hash functions (MD5, SHA-1, SHA-2, SHA-3, GOST), binary trees (RB, AVL) and more. Native code performance.
Stars: ✭ 402 (+103.03%)
Mutual labels: hash-functions
Xxhash
Extremely fast non-cryptographic hash algorithm
Stars: ✭ 5,783 (+2820.71%)
Mutual labels: hash-functions
Bitcoin Cryptography Library
Nayuki's implementation of cryptographic primitives used in Bitcoin.
Stars: ✭ 81 (-59.09%)
Mutual labels: hash-functions
Zero Allocation Hashing
Zero-allocation hashing for Java
Stars: ✭ 561 (+183.33%)
Mutual labels: hash-functions
Swift Crypto
Open-source implementation of a substantial portion of the API of Apple CryptoKit suitable for use on Linux platforms.
Stars: ✭ 1,005 (+407.58%)
Mutual labels: hash-functions
Upash
🔒Unified API for password hashing algorithms
Stars: ✭ 484 (+144.44%)
Mutual labels: hash-functions
Cdsa
A library of generic intrusive data structures and algorithms in ANSI C
Stars: ✭ 549 (+177.27%)
Mutual labels: hash-functions
Streebog
GOST R 34.11-2012: RFC-6986 cryptographic hash function
Stars: ✭ 24 (-87.88%)
Mutual labels: hash-functions
Scala Hashing
Fast non-cryptographic hash functions for Scala
Stars: ✭ 66 (-66.67%)
Mutual labels: hash-functions
FastHashes
A .NET implementation of several non-cryptographic hashes.
Stars: ✭ 24 (-87.88%)
Mutual labels: hash-functions
Highwayhash
Native Go version of HighwayHash with optimized assembly implementations on Intel and ARM. Able to process over 10 GB/sec on a single core on Intel CPUs - https://en.wikipedia.org/wiki/HighwayHash
Stars: ✭ 670 (+238.38%)
Mutual labels: hash-functions
Mum Hash
Hashing functions and PRNGs based on them
Stars: ✭ 117 (-40.91%)
Mutual labels: hash-functions
Meow hash
Official version of the Meow hash, an extremely fast level 3 hash
Stars: ✭ 1,204 (+508.08%)
Mutual labels: hash-functions
Java Crypto Utils
Java Cryptographic, Encoding and Hash Utilities
Stars: ✭ 15 (-92.42%)
Mutual labels: hash-functions
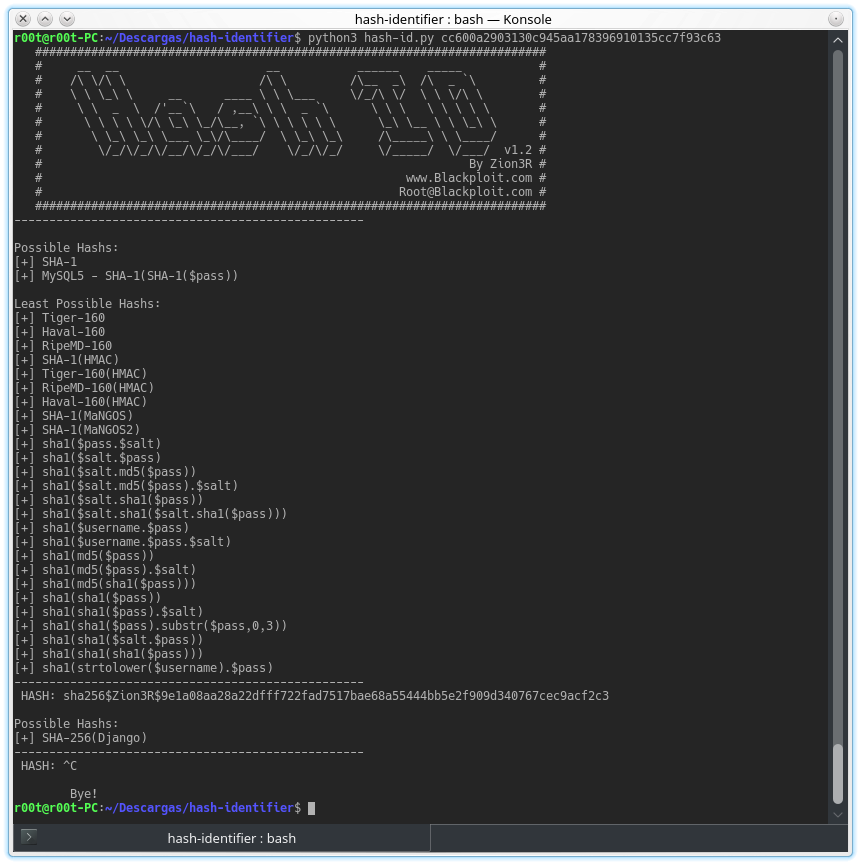
hash-identifier
Software to identify the different types of hashes used to encrypt data and especially passwords.
Encryption formats supported:
- ADLER-32
- CRC-32
- CRC-32B
- CRC-16
- CRC-16-CCITT
- DES(Unix)
- FCS-16
- GHash-32-3
- GHash-32-5
- GOST R 34.11-94
- Haval-160
- Haval-192 110080 ,Haval-224 114080 ,Haval-256
- Lineage II C4
- Domain Cached Credentials
- XOR-32
- MD5(Half)
- MD5(Middle)
- MySQL
- MD5(phpBB3)
- MD5(Unix)
- MD5(Wordpress)
- MD5(APR)
- Haval-128
- MD2
- MD4
- MD5
- MD5(HMAC(Wordpress))
- NTLM
- RAdmin v2.x
- RipeMD-128
- SNEFRU-128
- Tiger-128
- MySQL5 - SHA-1(SHA-1($pass))
- MySQL 160bit - SHA-1(SHA-1($pass))
- RipeMD-160
- SHA-1
- SHA-1(MaNGOS)
- Tiger-160
- Tiger-192
- md5($pass.$salt) - Joomla
- SHA-1(Django)
- SHA-224
- RipeMD-256
- SNEFRU-256
- md5($pass.$salt) - Joomla
- SAM - (LM_hash:NT_hash)
- SHA-256(Django)
- RipeMD-320
- SHA-384
- SHA-256
- SHA-384(Django)
- SHA-512
- Whirlpool
- And more…
Encryption algorithms that can not be differentiated unless they have been decrypted, so the efficiency of the software also depends on the user's criteria.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].