secrary / Idenlib
Programming Languages
Projects that are alternatives of or similar to Idenlib
idenLib - Library Function Identification
When analyzing malware or 3rd party software, it's challenging to identify statically linked libraries and to understand what a function from the library is doing.
idenLib.exe is a tool for generating library signatures from .lib/.obj/.exe files.
idenLib.dp32/idenLib.dp64 is a x32dbg/x64dbg plugin to identify library functions.
idenLib.py is an IDA Pro plugin to identify library functions.
Any feedback is greatly appreciated: @_qaz_qaz
How does idenLib.exe generate signatures?
- Parses input file(
.lib/.objfile) to get a list of function addresses and function names. - Gets the last opcode from each instruction
-
Compresses the signature with zstd
-
Saves the signature under the
SymExdirectory, if the input filename iszlib.lib, the output will bezlib.lib.sigorzlib.lib.sig64, ifzlib.lib.sig(64)already exists under theSymExdirectory from a previous execution or from the previous version of the library, the next execution will append different signatures. If you executeidenLib.exeseveral times with different version of the.libfile, the.sig/sig64file will include all unique function signatures.
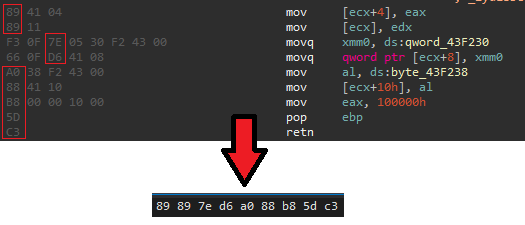
Inside of a signature (it's compressed):

Usage:
- Generate library signatures:
idenLib.exe /path/to/fileoridenLib.exe /path/to/directory - Generate
mainfunction signature:idenLib.exe /path/to/pe -getmain
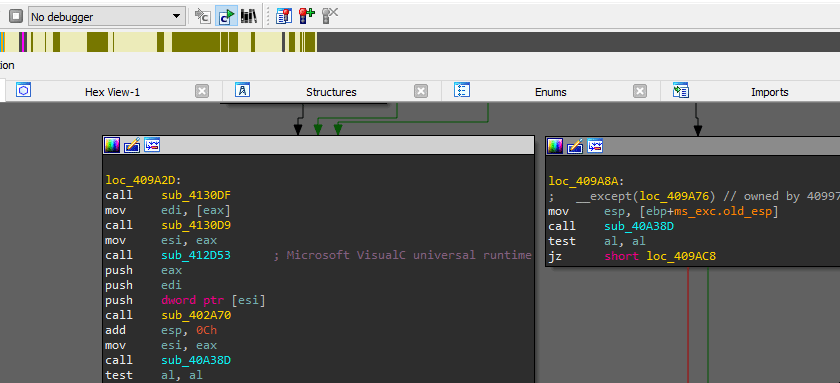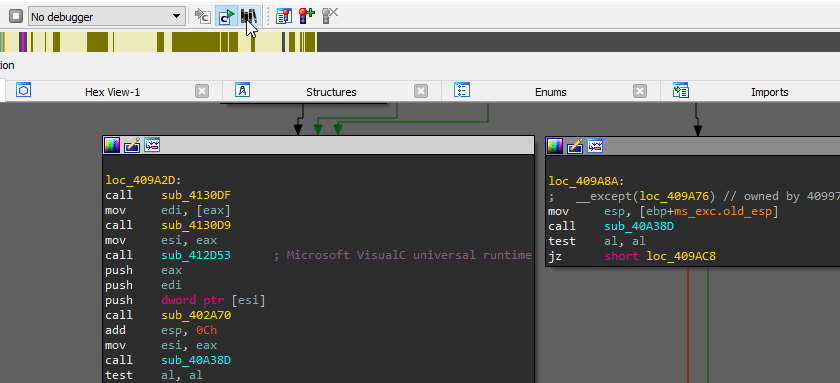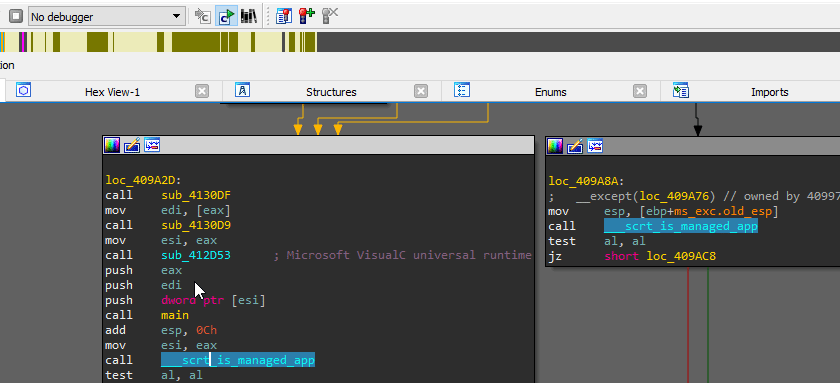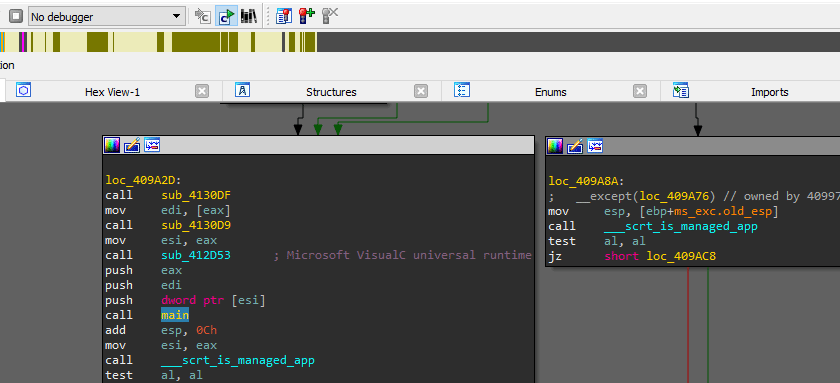
Generating library signatures
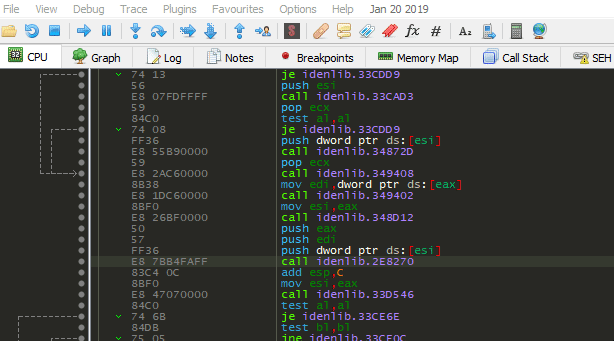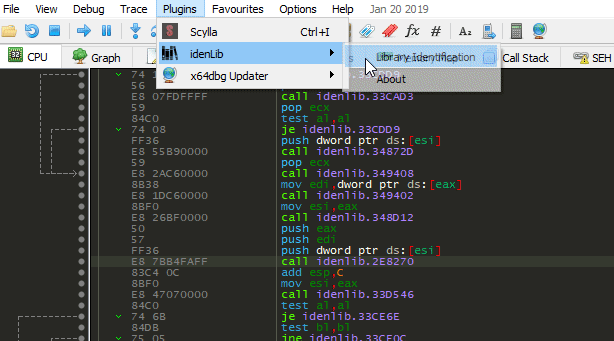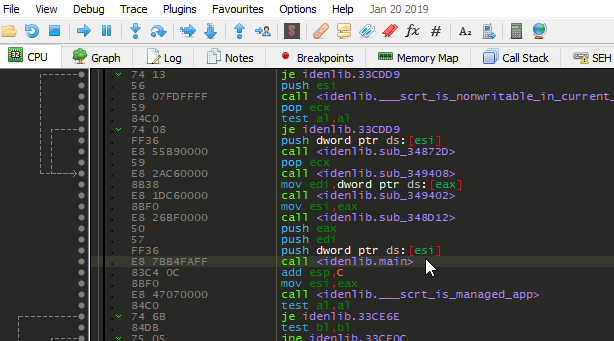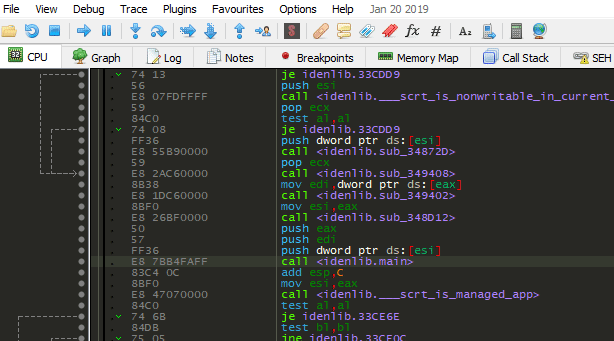
x32dbg/x64dbg, IDA Pro plugin usage:
- Copy
SymExdirectory underx32dbg/x64dbg/IDA Pro's main directory - Apply signatures:
Generating main function signature:
If you want to generate a signature for main function compiled using MSVC 14 you need to create a hello world application with the corresponding compiler and use the application as input for idenLib
main function signature files are EntryPointSignatures.sig and EntryPointSignatures.sig64
Notes Regarding to main Function Signatures
-
idenLibuses theDIA APIsto browse debug information stored in a PDB file. To runidenLibwith-getmainparameter you will need to ensure that the msdia140.dll (found inMicrosoft Visual Studio\2017\Community\DIA SDK\bin) is registered as a COM component, by invoking regsvr32.exe on the dll.
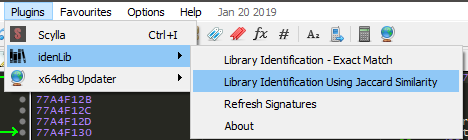
Applying Signatures
There are two ways to apply signatures, exact match and using Jaccard index
Useful links:
- Detailed information about
C Run-Time Libraries (CRT)
Third-party
-
Zydis (MIT License)
-
Zstandard (BSD License)
-
Icon by freepik