stuxnet999 / Memlabs
Programming Languages
Projects that are alternatives of or similar to Memlabs
Table of contents
- About MemLabs
- Motivation
- Structure of Repository
- Tools and Frameworks
- Flag Submission
- Resources
- Feedback & suggestions
- Usage
- Author
About MemLabs 🔍
MemLabs is an educational, introductory set of CTF-styled challenges which is aimed to encourage students, security researchers and also CTF players to get started with the field of Memory Forensics.
Motivation 🎯
The main goal of creating this repository was to provide a reliable platform where individuals can learn, practice and enhance their skills in the field of memory forensics. As of the CTF-style, well, what better & interesting way to learn security than by playing CTFs?
I also believe these labs can be used by anyone to help others become good with the essentials and fundamentals of memory forensics.
Structure of repository
| Directory | Challenge Name | Level Of Difficulty |
|---|---|---|
| Lab 0 | Never Too Late Mister | Sample challenge |
| Lab 1 | Beginner's Luck | Easy |
| Lab 2 | A New World | Easy |
| Lab 3 | The Evil's Den | Easy - Medium |
| Lab 4 | Obsession | Medium |
| Lab 5 | Black Tuesday | Medium - Hard |
| Lab 6 | The Reckoning | Hard |
To aid first-timers to understand how to approach CTF challenges & usage of volatility, please refer Lab 0 which comes with a elaborate walkthrough & I hope it will be a great way to start MemLabs!
All the memory dumps are that of a Windows system.
Note: The level of difficulty specified may not be fully accurate as it depends on the individual. I've tried my best to categorize them after receiving feedback from beginners to the field.
Tools and frameworks 🛠
I'd suggest everyone use The Volatility Framework for analysing the memory images.
Please execute the setup.sh file to install all the required dependencies in your system.
Note: Windows users can download the executable file from here.
As these labs are quite introductory, there is no need for installing more tools. However, if the user wishes, they can install many other forensic tools.
The preferred OS would be Linux. However, you can also use Windows (WSL) or macOS.
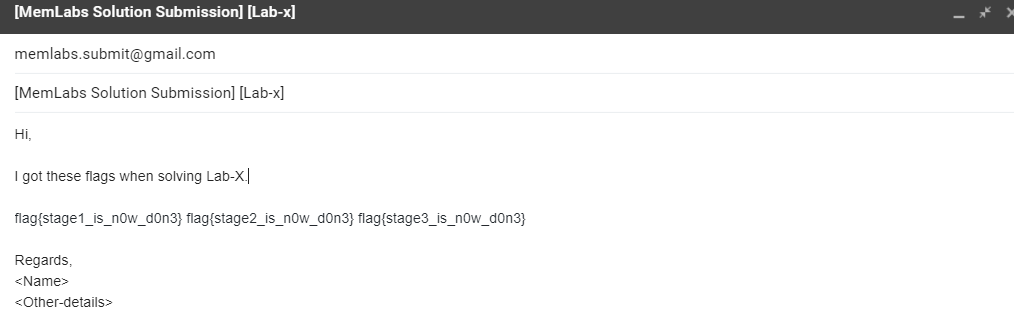
Flag submission 🚩
Please mail the flags of each lab to [email protected]
Please have a look at the following example to better understand how to submit the solution.
Suppose you find 3 flags in a particular lab,
- flag{stage1_is_n0w_d0n3}
- flag{stage2_is_n0w_d0n3}
- flag{stage3_is_n0w_d0n3}
Concatenate all the flags like this: flag{stage1_is_n0w_d0n3} flag{stage2_is_n0w_d0n3} flag{stage3_is_n0w_d0n3}
Note: Place the flags in the right order. The content inside the flags indicates their place. The flags must be space-separated.
All the labs will follow the same flag format unless specified otherwise.
Email format
Please follow the following guidelines when sending the solution. Below is a sample:
Email Subject: [MemLabs Solution Submission] [Lab-x]
x indicates the Lab number. Ex: 1,2,3 etc..
Email your solution to [email protected]
If the solution is correct, then the participant will receive a confirmation mail.
Feedback & suggestions
I'd love the community's feedback regarding these labs. Any suggestions or improvements are always welcome. Please email it to me or contact my via Twitter: @_abhiramkumar.
Resources 🚀
This section contains resources which I've composed myself and some others which I have used when I learnt memory forensics. I hope this resources will help everyone in not only solving these labs but also in exploring more areas in memory forensics.
- Basics of Memory Forensics
- Volatility Windows Command Reference
- Sans DFIR Memory Forensics cheat sheet
If you're interested to play more CTFs or want to try more challenges,
If you are interested in knowing how to write plugins for Volatility framework,
- https://stuxnet999.github.io/volatility/2020/07/04/Writing-Plugins-Volatility.html
- https://stuxnet999.github.io/volatility/2020/08/08/Writing-Plugins-Volatility-Part2.html
Usage
MemLabs is completely free to anyone to use. If you wish to use MemLabs in your workshops, classes or use the labs anywhere else, it is my humble request to you to use the original links to the labs and please mention my name as well. For any other queries, please contact me.
Author 👤
P. Abhiram Kumar
Digital Forensics, Team bi0s
- Mail: [email protected]
- Twitter: @_abhiramkumar
- Personal Blog: stuxnet999.github.io