OpenCSPM / Opencspm
Programming Languages
Projects that are alternatives of or similar to Opencspm
 OpenCSPM
OpenCSPM
Open Cloud Security Posture Management, OpenCSPM, is an open-source platform for gaining deeper insight into your cloud configuration and metadata to help understand and reduce risk over time.
Who is OpenCSPM for?
- Security teams running infrastructure in cloud environments looking to gain visibility into security risk across the entire account and track the resolution of those issues.
- Development and Infrastructure teams looking for a set of security best-practices to follow as they develop new systems and bake security in early and often.
- Red Teams wanting to create targeted scenarios specific to their environment with the highest impact and benefit to their Blue Team.
- Any organization looking to establish a baseline of security issues, prioritize them by risk, and track them to closure over time.
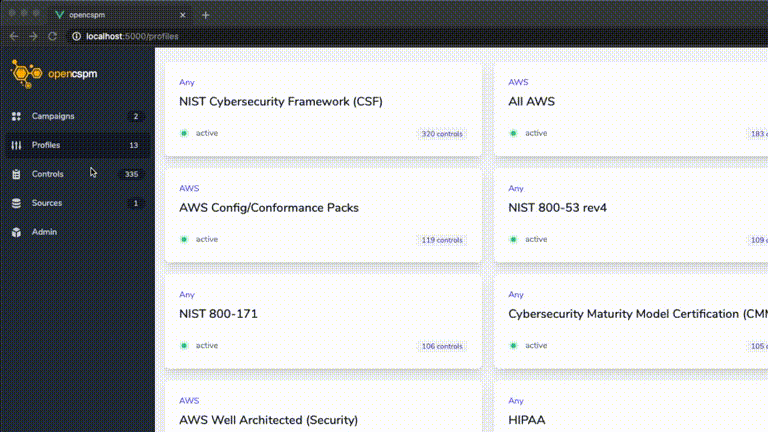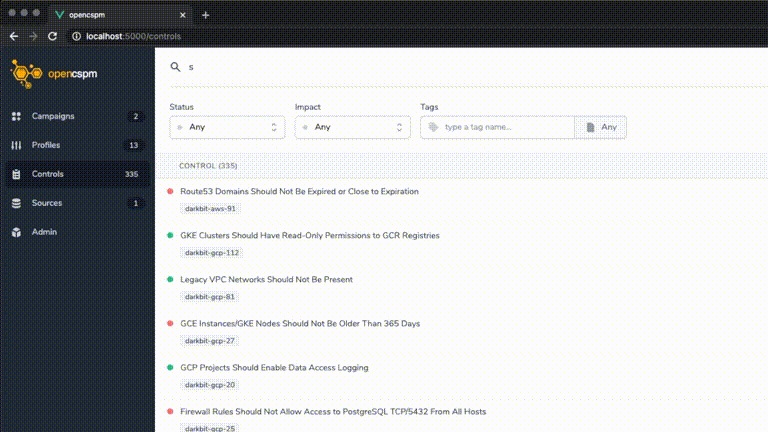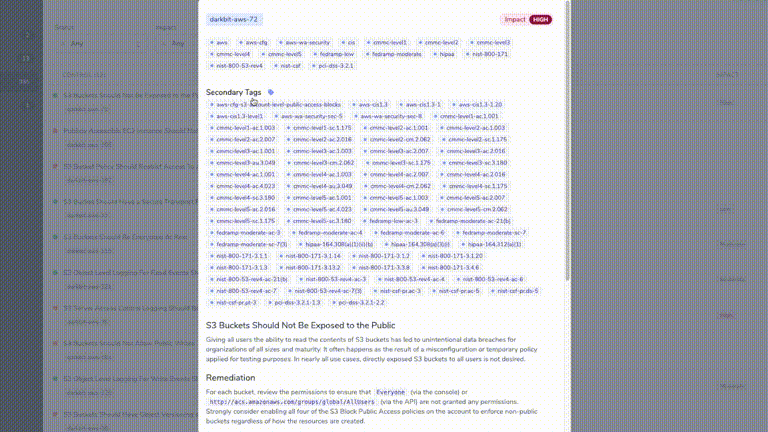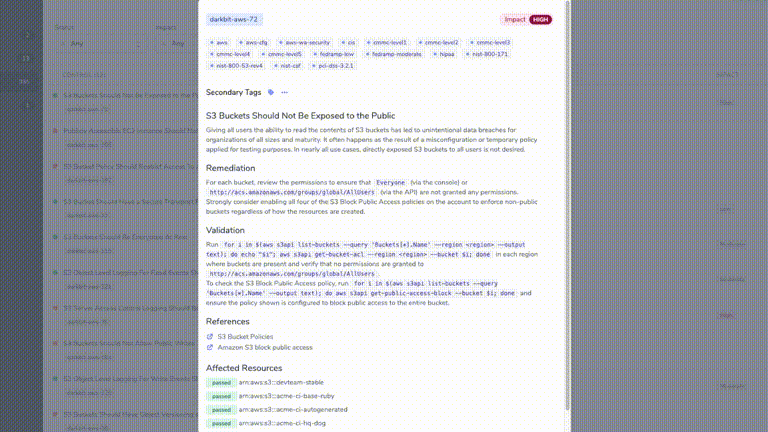
What does OpenCSPM do?
When deployed inside your environment, it can:
- collect several types of cloud configuration data on a one-time or recurring basis from your cloud account resources (VMs, Clusters, IAM, etc),
- parse and load that data into a graph database with deep linked relationships between resources to support advanced querying capabilities,
- run a customizable series of policy checks to determine conformance and record passing/failing resources on a recurring basis,
- create custom groupings of related policy checks that aid in tracking remediation efforts and reduction in risk over time,
- and provide notifications when deviations from desired baselines occur to multiple destinations.
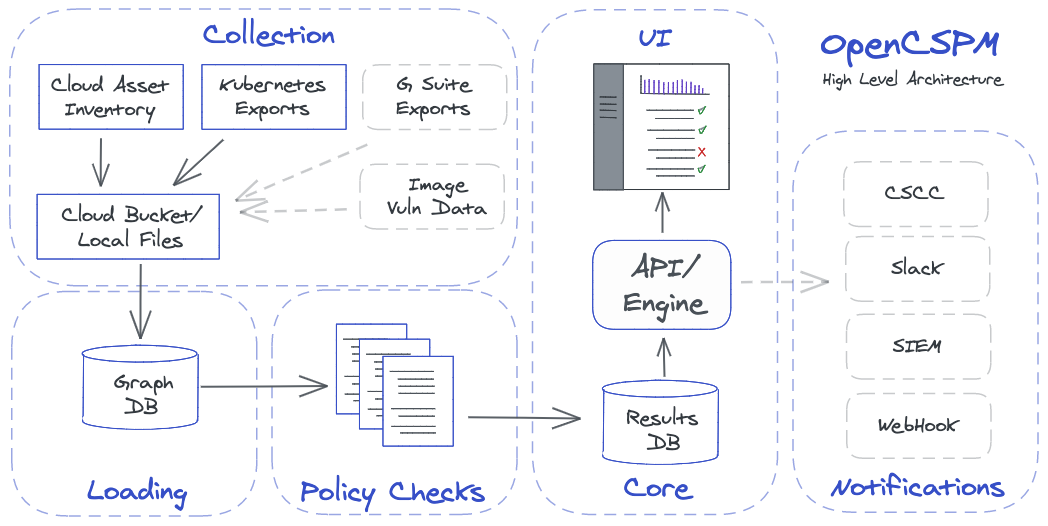
High-level Architecture
OpenCSPM has several key components that work together:
- Structured configuration and metadata is collected from the GCP Cloud Asset Inventory and Kubernetes API to a Storage Bucket or local filesystem.
- The data is parsed and loaded into a Graph Database with complex relationships intact.
- One or more customizable sets of policy checks ("control packs") are run against the parsed inventory data, and results are stored.
- The API/Engine serves up the user interface, handles tracking of campaigns, and notifications.
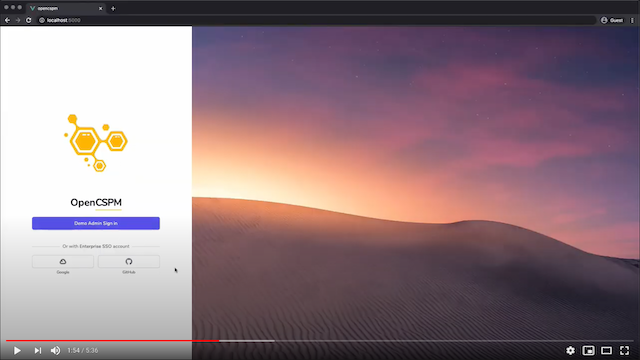
Getting Started
Ready to get going? Follow the instructions for getting started or watch the following getting started video:
Support and Community
OpenCSPM is undergoing active development and community assistance is available via the OpenCSPM Slack Channel. If you have found an issue, please file it using a GitHub issue.
Contributing
We invite you to submit requests for new features and bug reports using a Github issue. If you would like to contribute to OpenCSPM, please review our development guide.
Creators
OpenCSPM was made open-source software by Josh Larsen and Brad Geesaman, the co-founders of Darkbit. Darkbit is a cloud-native security assessment consulting firm based in the US that helps organizations understand the risks in their cloud and Kubernetes resource configurations.