ascr0b / Pcwt
Stars: ✭ 46
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Pcwt
Asnlookup
Leverage ASN to look up IP addresses (IPv4 & IPv6) owned by a specific organization for reconnaissance purposes, then run port scanning on it.
Stars: ✭ 163 (+254.35%)
Mutual labels: pentest, nmap, bugbounty
Findsploit
Find exploits in local and online databases instantly
Stars: ✭ 1,160 (+2421.74%)
Mutual labels: pentest, nmap, bugbounty
Project Black
Pentest/BugBounty progress control with scanning modules
Stars: ✭ 257 (+458.7%)
Mutual labels: pentest, bugbounty
Findom Xss
A fast DOM based XSS vulnerability scanner with simplicity.
Stars: ✭ 310 (+573.91%)
Mutual labels: pentest, bugbounty
Pentesting
Misc. Public Reports of Penetration Testing and Security Audits.
Stars: ✭ 24 (-47.83%)
Mutual labels: bugbounty, pentest
Lazyrecon
An automated approach to performing recon for bug bounty hunting and penetration testing.
Stars: ✭ 282 (+513.04%)
Mutual labels: pentest, bugbounty
Reconky-Automated Bash Script
Reconky is an great Content Discovery bash script for bug bounty hunters which automate lot of task and organized in the well mannered form which help them to look forward.
Stars: ✭ 167 (+263.04%)
Mutual labels: nmap, bugbounty
Dictionary Of Pentesting
Dictionary collection project such as Pentesing, Fuzzing, Bruteforce and BugBounty. 渗透测试、SRC漏洞挖掘、爆破、Fuzzing等字典收集项目。
Stars: ✭ 492 (+969.57%)
Mutual labels: pentest, bugbounty
Offensive Docker
Offensive Docker is an image with the more used offensive tools to create an environment easily and quickly to launch assessment to the targets.
Stars: ✭ 328 (+613.04%)
Mutual labels: pentest, bugbounty
Payloadsallthethings
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
Stars: ✭ 32,909 (+71441.3%)
Mutual labels: pentest, bugbounty
leaky-paths
A collection of special paths linked to major web CVEs, known misconfigurations, juicy APIs ..etc. It could be used as a part of web content discovery, to scan passively for high-quality endpoints and quick-wins.
Stars: ✭ 507 (+1002.17%)
Mutual labels: bugbounty, pentest
HolyTips
A Collection of Notes, Checklists, Writeups on Bug Bounty Hunting and Web Application Security.
Stars: ✭ 1,210 (+2530.43%)
Mutual labels: bugbounty, pentest
YAPS
Yet Another PHP Shell - The most complete PHP reverse shell
Stars: ✭ 35 (-23.91%)
Mutual labels: bugbounty, pentest
CVE-2021-44228-PoC-log4j-bypass-words
🐱💻 ✂️ 🤬 CVE-2021-44228 - LOG4J Java exploit - WAF bypass tricks
Stars: ✭ 760 (+1552.17%)
Mutual labels: bugbounty, pentest
Dorknet
Selenium powered Python script to automate searching for vulnerable web apps.
Stars: ✭ 256 (+456.52%)
Mutual labels: web-app, pentest
Xspear
Powerfull XSS Scanning and Parameter analysis tool&gem
Stars: ✭ 583 (+1167.39%)
Mutual labels: pentest, bugbounty
project-black
Pentest/BugBounty progress control with scanning modules
Stars: ✭ 279 (+506.52%)
Mutual labels: bugbounty, pentest
spellbook
Framework for rapid development and reusable of security tools
Stars: ✭ 67 (+45.65%)
Mutual labels: bugbounty, pentest
PCWT
A web application that makes it easy to run your pentest and bug bounty projects.
Description
The app provides a convenient web interface for working with various types of files that are used during the pentest, automate port scan and subdomain search.
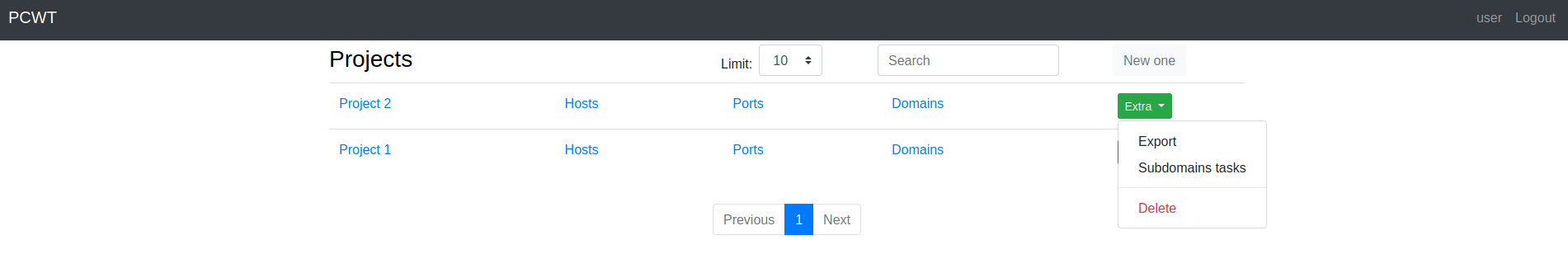
Main page
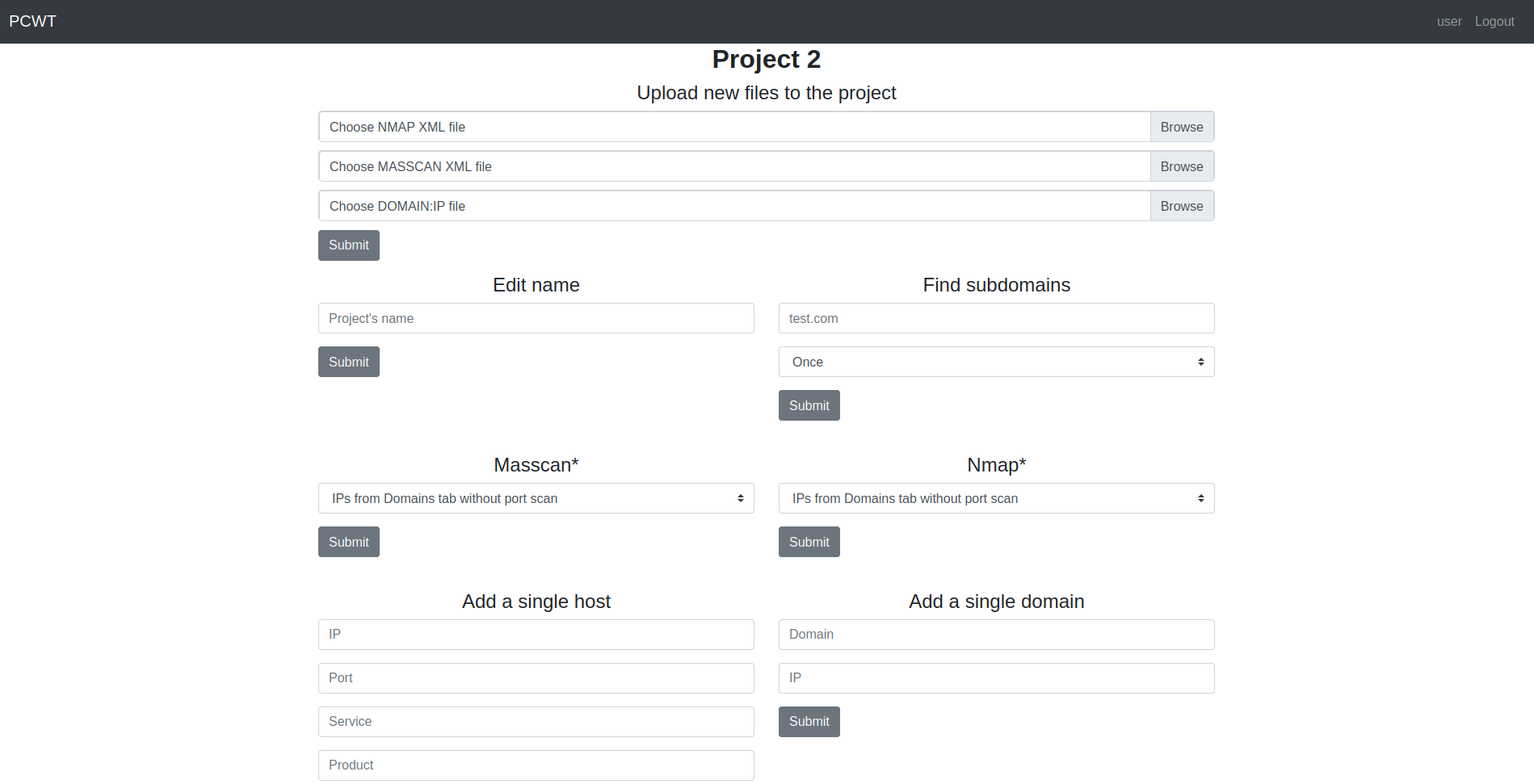
Project settings
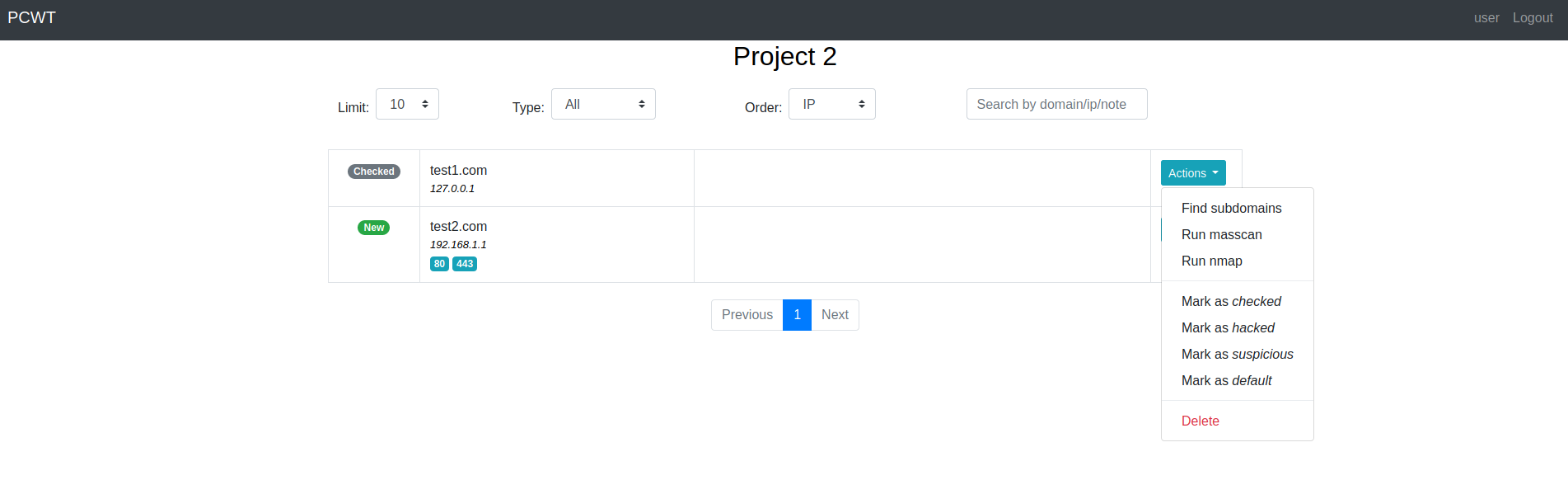
Domains dashboard
Port scan
You can scan ports using nmap or masscan. The nmap is started with the following arguments:
nmap --top-ports 10000 -sV -Pn --min-rate 300 --max-retries 2 [ip]
The masscan is started with the following arguments:
masscan -p 1-65535 --rate 2000
Subdomain search
Amass and findomain are used to find subdomains.
Features
- Leave notes to host, port or domain.
- Mark host or domain with tags.
- Search by any field related with host, port or domain (tags and notes are included). Regexp is available.
- Different types of sorting ara available on almost all dashboards.
- Run port scan for all hosts, hosts without port scan or custom list.
- Create tasks for subdomains search (every 2 hours, every 5 hours, every day or every week). You can also disable and enable them on demand using
Subdomain tasksdashboard. - Different types of export are available.
- Notifications about the start and end of the scan, as well as about new found domains can be sent to Telegram. Update the
config.pywith your chat id and token.
Install from sources
NOTE 1: Change the paths for amass, findomain, nmap and masscan in config.py before running commands.
NOTE 2: The app must be started as root if you want masscan to work.
apt install python3 python-venv python3-pip
git clone https://github.com/ascr0b/PCWT
cd PCWT
python3 -m venv env
source env/bin/activate
pip3 install -r requirements.txt
flask init-db
flask crontab add
export FLASK_APP=app
flask run
The app is available at http://127.0.0.1:5000
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].