What is Phishious?
Phishious is an open-source Secure Email Gateway (SEG) evaluation toolkit designed for red-teamers and developed by the team at CanIPhish. Phishious provides the ability to see how various Secure Email Gateway technologies behave when presented with phishing material.
📬 Secure Email Gateways Supported
🧐 Why use Phishious?
We're not joking when we say that Phishious is a world first in Secure Email Gateway evaluation. There is currently no other tool available (free or paid) that provides you the ability to scan your phish against an array of Secure Email Gateways. The closest utility is VirusTotal, however this specifically focuses on Malware detection and not Spam/Phish detection.
Through use of Phishious, you'll be able to freely test your phishing material against the world's most popular Secure Email Gateways. This is an invaluable capability as it provides you an indication of how successful your phishing campaign may be.
🔩 How does Phishious work?
Phishious exploits a common misconfiguration where many organisations broadcast overly sensitive information in email bounce responses and non-delivery reports. The sensitive information typically comes in the form of original untampered inbound message headers.
By feeding this information into Phishious, it can extract the relevant information and detect when an email is likely to end up in a targets junk folder or be completely blocked by the SEG. When we scale this across many targets, we're able to aggregate this information to provide a holistic view on how various SEGs behave when delivered certain phishing material.
To better understand email bounce attacks and the resulting issues, please read the following Blog Post, watch this BSides Canberra presentation or watch the below introduction video on youtube.
💡 Requirements
Windows 10 Endpoint, Windows Server 2012+ or any Linux system capable of running .NET Core 5.0 (see https://dotnet.microsoft.com/download/dotnet/5.0)
⛏️ Setup
Phishious is a .NET Core 5.0 MVC Web Application. Accordingly it can be run on Windows using IIS or Linux using Apache as the Web Server. However the simplest way to use Phishious is to clone the project and then Debug it using your favourite IDE (e.g. Visual Studio, Visual Studio Code, Rider, etc.).
🏁 How to use Phishious (Automatic)
The automated scan adds an orchestration layer whereby Phishious automatically sends emails, ingests bounce responses and analyses mail headers with only a few clicks. The main exercise on you as the user is to identify vulnerable mail receivers.
Phase 1: Identification of Vulnerable Mail Receivers
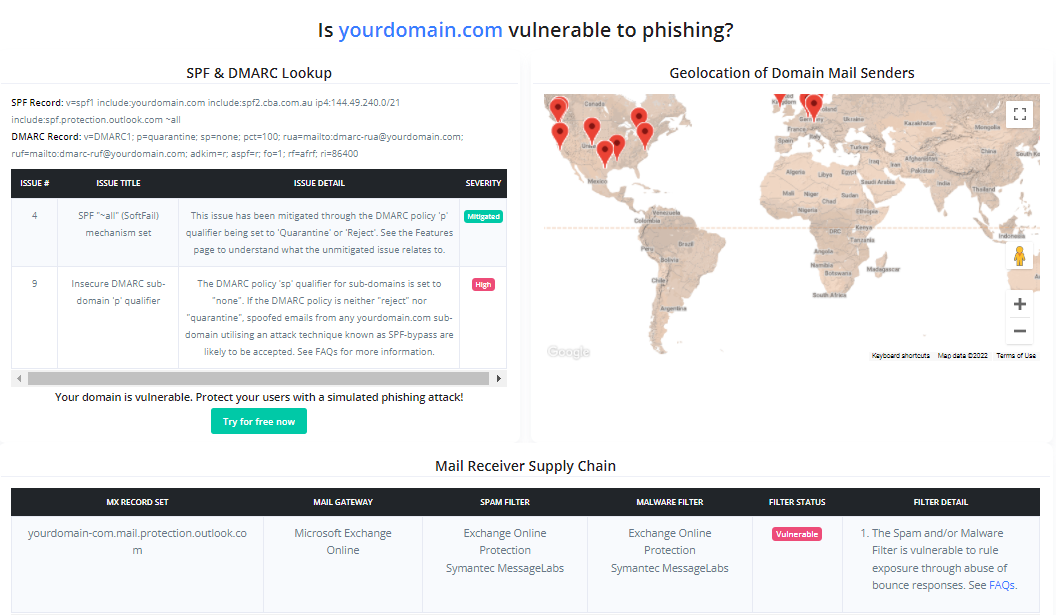
As Phishious is designed to abuse public infrastructure, you need to identify a variety of targets who use differing mail security technologies (e.g. Target 1 uses Sophos PureMessage, Target 2 uses Cisco IronPort, etc.). Identification of Vulnerable Mail Receivers can be found through manual analysis (e.g. CanIPhish Supply Chain Analysis) or programmatic means (e.g. CanIPhish Supply Chain API).
Reference: The accompanying image is of a CanIPhish Supply Chain Scan which shows a vulnerable 'Mail Receiver Supply Chain'.
Phase 2: Phishious Settings
Target Settings. Input target domains seperated by a space, line or comma. Follow this up by inputing a non-existent address into the local part address
SMTP Settings. Input the SMTP server settings you plan on using.
Note: If using Gmail then use a throwaway Gmail address with "Less secure app access" enabled. This setting can be toggled by clicking here - https://myaccount.google.com/lesssecureapps. Setup a Filter so any inbound email is never sent to spam (configured under Settings Cog > See All Settings > Filters and Blocked Addresses > Create a new filter). Finally for Gmail, the username and password are your gmail email address and password.
Storage Scan Settings. Input the location where the email bounce responses will land. At current, both Gmail and Amazon S3 are supported as storage destinations.
Note: For use of Amazon S3, you will likely need to setup some form of forwarding capability to forward bounce responses to this location (e.g. Amazon SES Mail Receiver with S3 as the destination).
Email Priming Settings. Input your sending email address, display name and a non-malicious subject and email body. Email priming is used to baseline normal behaviour of the respective Secure Email Gateway technologies, so we can analyse the delta from this when we deliver our malicious mail.
Once all settings have been provided, click 'Save Settings' followed by 'Prime Filters'. Wait up to a minute for Priming to complete.
Phase 3: Filter Detonation
Time to email malicious content to those same targets emailed during Priming.
Step 1. Input your sending email address, display name and a malicious subject and email body.
Step 2. Click 'Detonate Filters'. Wait up to a minute for Detonation to complete.
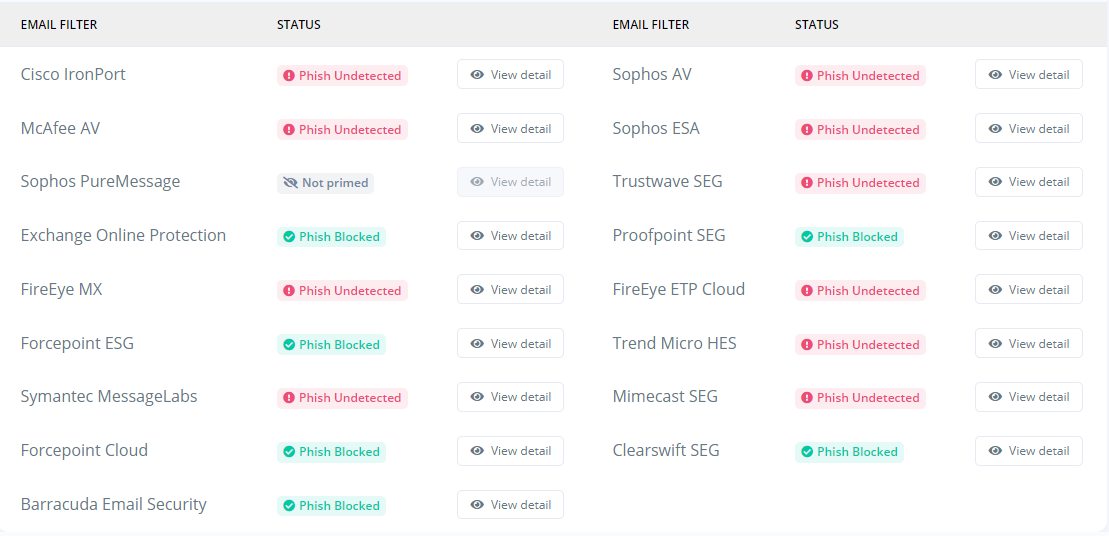
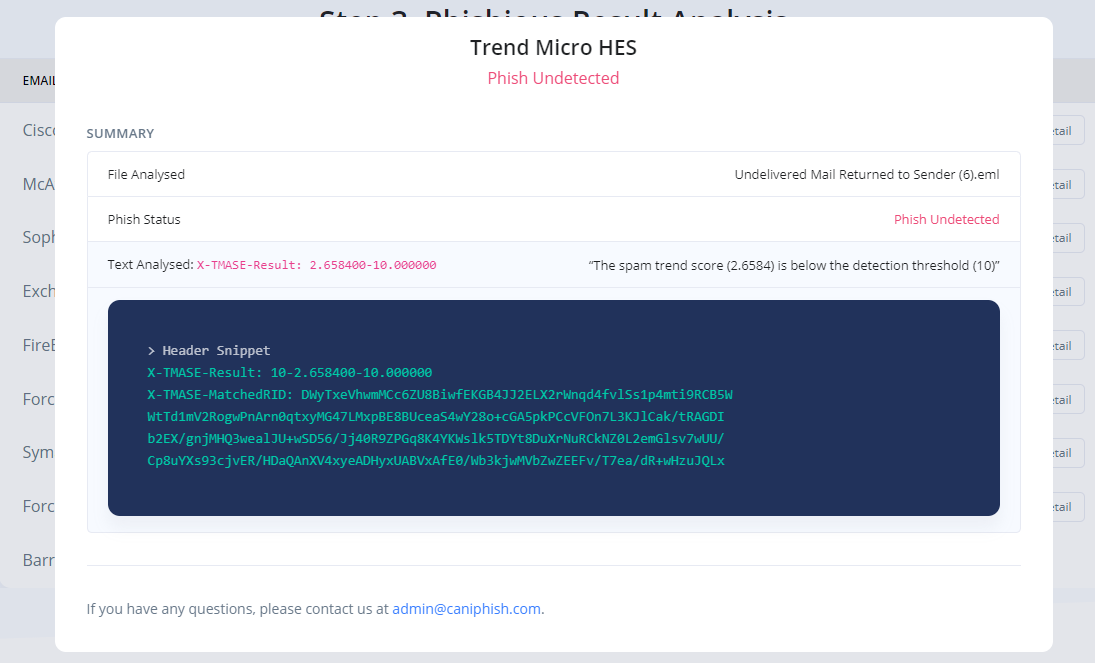
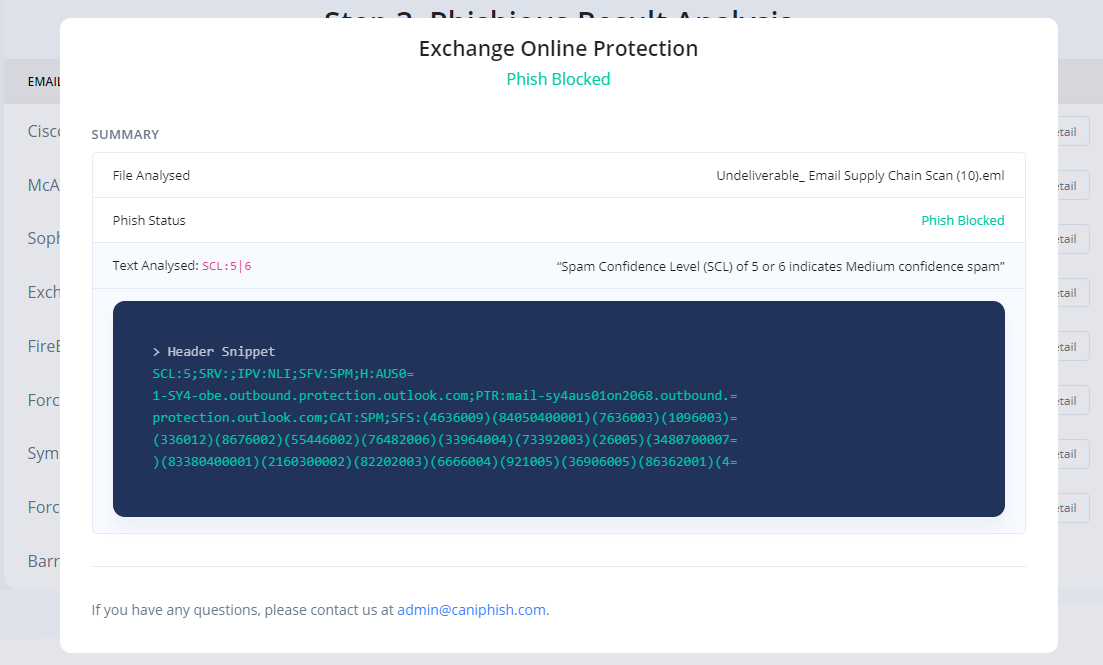
Phase 4: Results Analysis
Analyse the results to determine whether your phishing material was blocked or remained undetected. Click 'View Detail' to gain insight into what text was analysed within the Email Headers and how this impacted the overall Phishious assessment.
Reference: The accompanying images show the detailed view of two seperate SEG technologies. This view shows how Phishious analysed Email Headers to provide two seperate results from a single Phishing Email.
🏁 How to use Phishious (Manual)
Phase 1: Identification of Vulnerable Mail Receivers
As Phishious is designed to abuse public infrastructure, you need to identify a variety of targets who use differing mail security technologies (e.g. Target 1 uses Sophos PureMessage, Target 2 uses Cisco IronPort, etc.). Identification of Vulnerable Mail Receivers can be found through manual analysis (e.g. CanIPhish Supply Chain Analysis) or programmatic means (e.g. CanIPhish Supply Chain API).
Reference: The accompanying image is of a CanIPhish Supply Chain Scan which shows a vulnerable 'Mail Receiver Supply Chain'.
Phase 2: Filter Priming
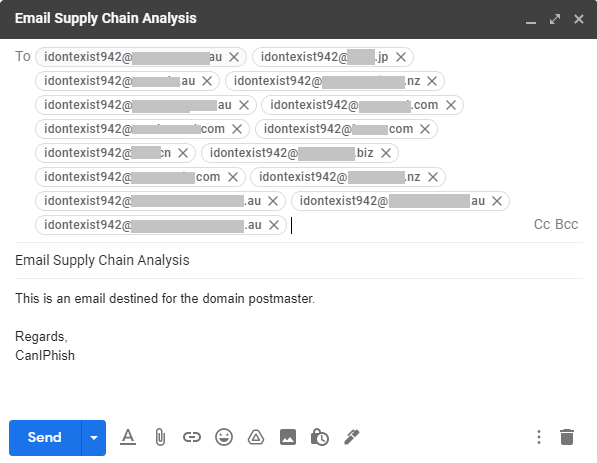
Step 1. Email non-malicious content to a non-existent address at various target domains where a bounce attack vulnerability exists and a known Secure Email Gateway (SEG) is in-use.
Note: At this stage, only Amazon SES and Gmail have been tested for the receipt of bounce responses. Do not use Exchange Online.
Reference: The accompanying image is of an email (within Gmail) directed towards non-existent addresses at 15 targets. Each target was uniquely identified and selected for their differing Secure Email Gateway technologies.
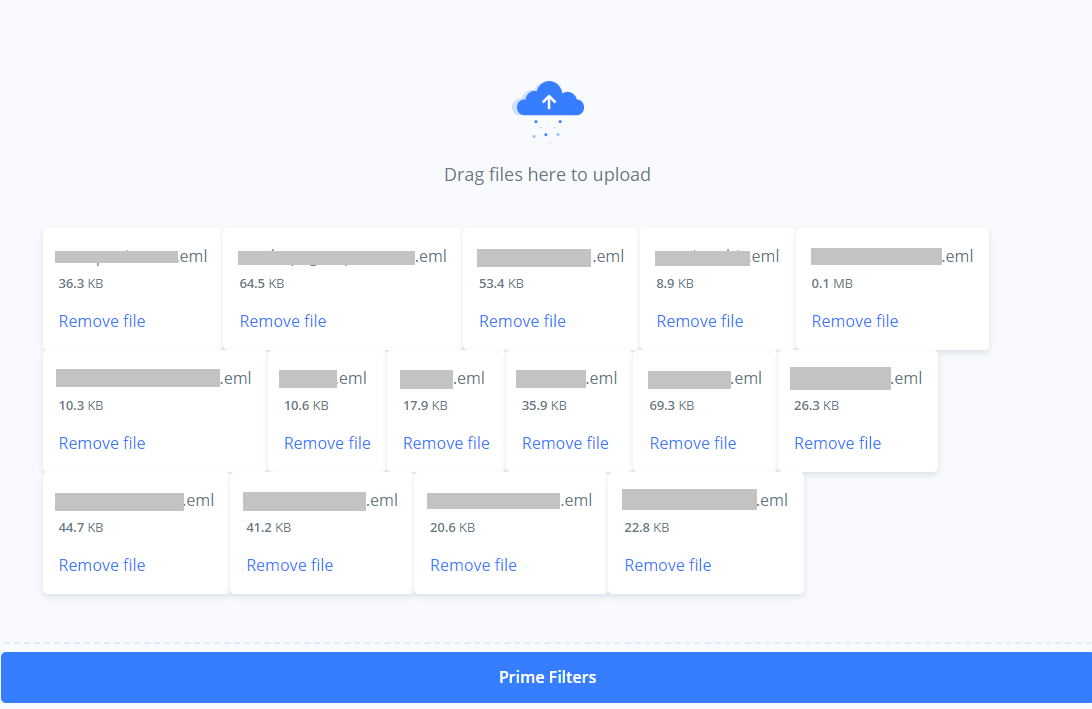
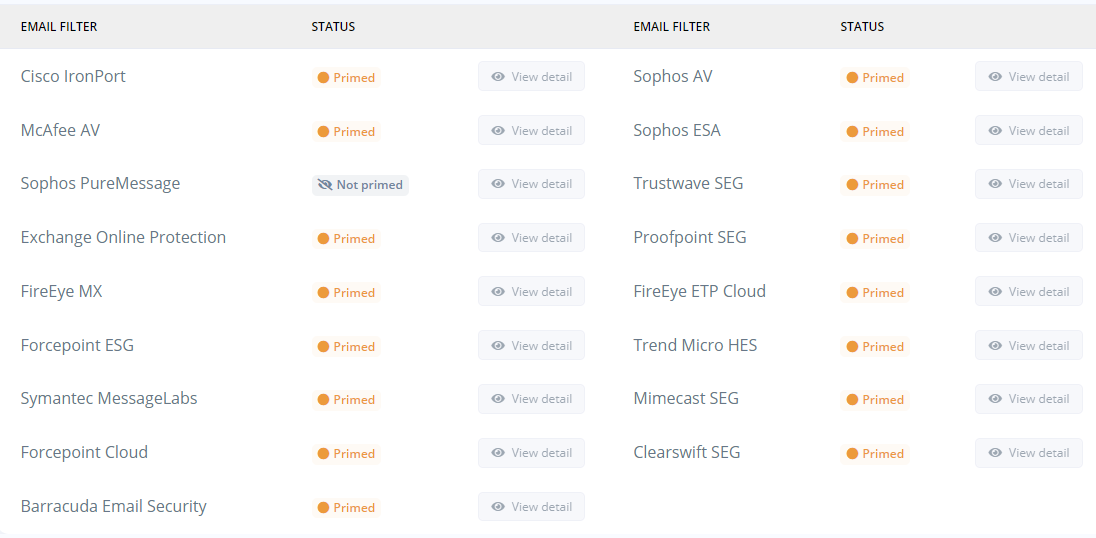
Step 2. Wait 180 seconds. Download all received bounce responses and then upload them to Phishious for Filter Priming. Upon Priming, you will see the status of all Secure Email Gateway technologies identified. For filter detonation (Phase 3), only these technologies will be targeted.
Reference: The accompanying images show the email bounce responses being uploaded to Phishious and then the observed result of Filter Priming.
Phase 3: Filter Detonation
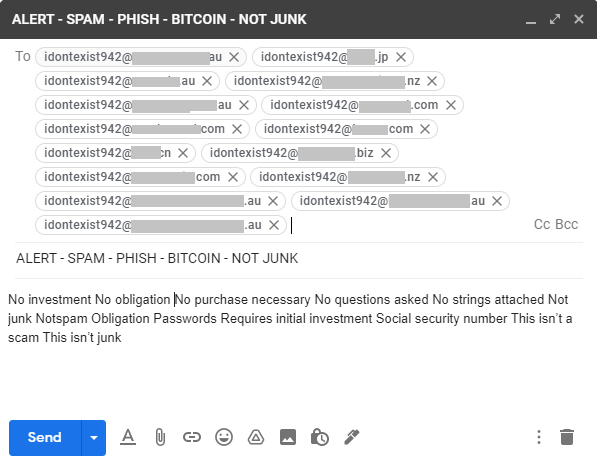
Step 1. Email malicious content to a non-existent address at the same target domains emailed in Phase 2.
Note: At this stage, only Amazon SES and Gmail have been tested for the receipt of bounce responses. Do not use Exchange Online.
Reference: The accompanying image is of an email (within Gmail) directed towards the same non-existent addresses at targeted in Phase 2. Each target was uniquely identified and selected for their differing Secure Email Gateway technologies.
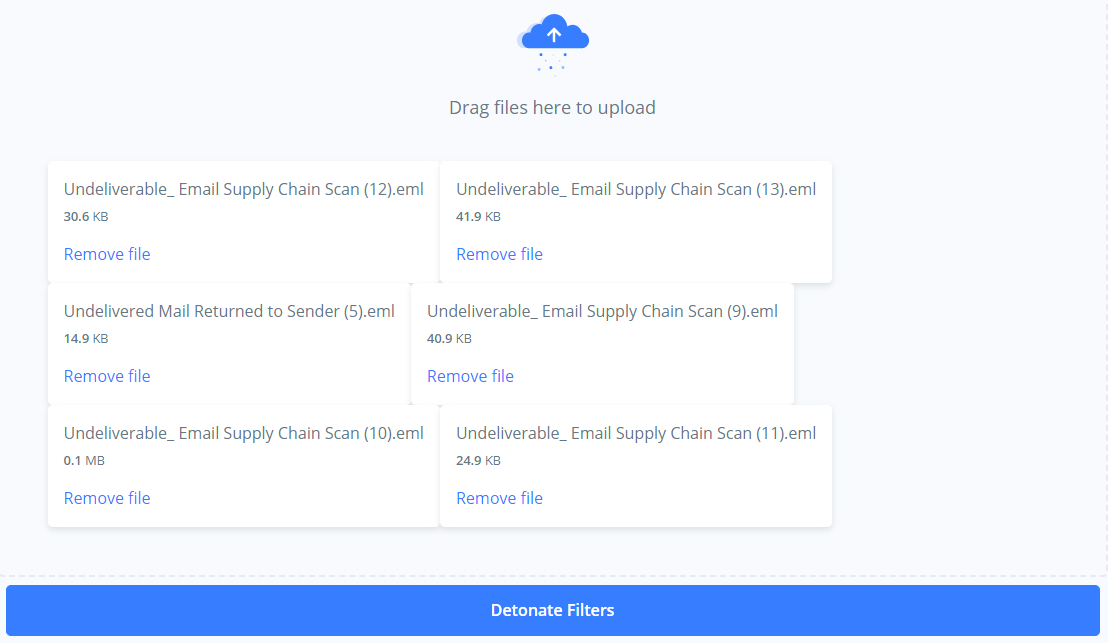
Step 2. Wait 180 seconds. Download all received bounce responses and then upload them to Phishious for Filter Detonation. Upon Detonation, you will see the status of all Secure Email Gateway technologies identified and whether the phish was blocked or remained undetected.
Reference: The accompanying images show the email bounce responses being uploaded to Phishious and then the observed result of Filter Detonation.
Phase 4: Results Analysis
Analyse the results to determine whether your phishing material was blocked or remained undetected. Click 'View Detail' to gain insight into what text was analysed within the Email Headers and how this impacted the overall Phishious assessment.
Reference: The accompanying images show the detailed view of two seperate SEG technologies. This view shows how Phishious analysed Email Headers to provide two seperate results from a single Phishing Email.


Example Outputs
📜 Documentation
Documentation is always a work-in-progress and can be found on the CanIPhish website or here on GitHub. Find something missing? Let us know by filing an issue! Interested in seeing how phishing emails look and feel? Take a look at our interactive phishing email simulator.
❕ Issues
Find a bug? Want more features? Find something missing in the documentation? Let us know! Please don't hesitate to file an issue and we'll get right on it.
📝 License
Phishious - Open-Source Secure Email Gateway Evaluation Toolkit
The MIT License (MIT)
Copyright (c) 2021 - 2021 CanIPhish Pty Ltd
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software ("Phishious Community Edition") and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
⚖️ Disclaimer
This tool should be used on applications/networks that you have permission to use. Any misuse or damage caused will be solely the users’ responsibility.