enemy-submarine / Pidrila
Licence: gpl-2.0
Python Interactive Deepweb-oriented Rapid Intelligent Link Analyzer
Stars: ✭ 125
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Pidrila
Whatweb
Next generation web scanner
Stars: ✭ 3,503 (+2702.4%)
Mutual labels: hacking, pentesting, penetration-testing, scanner, pentest, appsec
Dirsearch
Web path scanner
Stars: ✭ 7,246 (+5696.8%)
Mutual labels: hacking, pentesting, penetration-testing, scanner, appsec, bug-bounty
Dumpall
一款信息泄漏利用工具,适用于.git/.svn源代码泄漏和.DS_Store泄漏
Stars: ✭ 250 (+100%)
Mutual labels: hacking, pentesting, scanner, bug-bounty
Vajra
Vajra is a highly customizable target and scope based automated web hacking framework to automate boring recon tasks and same scans for multiple target during web applications penetration testing.
Stars: ✭ 269 (+115.2%)
Mutual labels: hacking, pentesting, scanner, bug-bounty
Penetration Testing Study Notes
Penetration Testing notes, resources and scripts
Stars: ✭ 461 (+268.8%)
Mutual labels: hacking, pentesting, penetration-testing, pentest
tugarecon
Pentest: Subdomains enumeration tool for penetration testers.
Stars: ✭ 142 (+13.6%)
Mutual labels: scanner, penetration-testing, bug-bounty, pentest
aquatone
A Tool for Domain Flyovers
Stars: ✭ 43 (-65.6%)
Mutual labels: penetration-testing, bug-bounty, pentest, appsec
Sifter
Sifter aims to be a fully loaded Op Centre for Pentesters
Stars: ✭ 403 (+222.4%)
Mutual labels: pentesting, penetration-testing, scanner, pentest
Security Tools
Collection of small security tools, mostly in Bash and Python. CTFs, Bug Bounty and other stuff.
Stars: ✭ 509 (+307.2%)
Mutual labels: hacking, pentesting, scanner, bug-bounty
Habu
Hacking Toolkit
Stars: ✭ 635 (+408%)
Mutual labels: hacking, pentesting, penetration-testing, pentest
Keye
Keye is a reconnaissance tool that was written in Python with SQLite3 integrated. After adding a single URL, or a list of URLs, it will make a request to these URLs and try to detect changes based on their response's body length.
Stars: ✭ 101 (-19.2%)
Mutual labels: hacking, penetration-testing, pentest, bug-bounty
Capsulecorp Pentest
Vagrant VirtualBox environment for conducting an internal network penetration test
Stars: ✭ 214 (+71.2%)
Mutual labels: hacking, pentesting, penetration-testing, pentest
Rengine
reNgine is an automated reconnaissance framework for web applications with a focus on highly configurable streamlined recon process via Engines, recon data correlation and organization, continuous monitoring, backed by a database, and simple yet intuitive User Interface. reNgine makes it easy for penetration testers to gather reconnaissance with…
Stars: ✭ 3,439 (+2651.2%)
Mutual labels: scanner, penetration-testing, bug-bounty, pentesting
Offensive Docker
Offensive Docker is an image with the more used offensive tools to create an environment easily and quickly to launch assessment to the targets.
Stars: ✭ 328 (+162.4%)
Mutual labels: hacking, pentesting, pentest, bug-bounty
Thc Archive
All releases of the security research group (a.k.a. hackers) The Hacker's Choice
Stars: ✭ 474 (+279.2%)
Mutual labels: hacking, pentesting, penetration-testing, pentest
Oscp Prep
my oscp prep collection
Stars: ✭ 105 (-16%)
Mutual labels: hacking, pentesting, penetration-testing, scanner
Sublert
Sublert is a security and reconnaissance tool which leverages certificate transparency to automatically monitor new subdomains deployed by specific organizations and issued TLS/SSL certificate.
Stars: ✭ 699 (+459.2%)
Mutual labels: hacking, penetration-testing, pentest, bug-bounty
Reconftw
reconFTW is a tool designed to perform automated recon on a target domain by running the best set of tools to perform scanning and finding out vulnerabilities
Stars: ✭ 974 (+679.2%)
Mutual labels: hacking, scanner, pentest
Active Directory Exploitation Cheat Sheet
A cheat sheet that contains common enumeration and attack methods for Windows Active Directory.
Stars: ✭ 870 (+596%)
Mutual labels: hacking, pentesting, penetration-testing
PIDRILA
Current Release: v0.1.0 (2020.11.08)
Overview
PIDRILA: Python Interactive Deepweb-oriented Rapid Intelligent Link Analyzer is really fast async web path scanner prototype developed by BrightSearch team for all ethical netstalkers.
Installation & Usage
git clone https://github.com/enemy-submarine/pidrila.git
cd pidrila
python3 pidrila.py -u <URL>
Options
Usage: pidrila.py [OPTIONS]
Options:
-U, --user-agent TEXT User-Agent
-t, --timeout INTEGER Request timeout [default: 30]
-A, --auth TEXT Basic HTTP auth, i.e. login:password
-M, --max-connections-per-host INTEGER
How many simultaneous connections should we
open (per each host) [default: 16]
-m, --max-connections INTEGER How many simultaneous connections should we
open [default: 128]
-p, --proxy TEXT Proxy address, like socks5h://127.0.0.1:9050
-p, --pathlist FILENAME Path list
-L, --url-list FILENAME Target URL list
-u, --url TEXT Target URL, option is mutually exclusive
with url_list [required]
-l, --logs DIRECTORY Destination directory for the logs
--http-method [head|get] HTTP method: GET or HEAD [default: get]
--help Show this message and exit.
Features
- Asynchronous
- Can simultaneously scan unlimited number of sites
- Keep-alive support
- HTTP and SOCKS proxy support
- User agent randomization
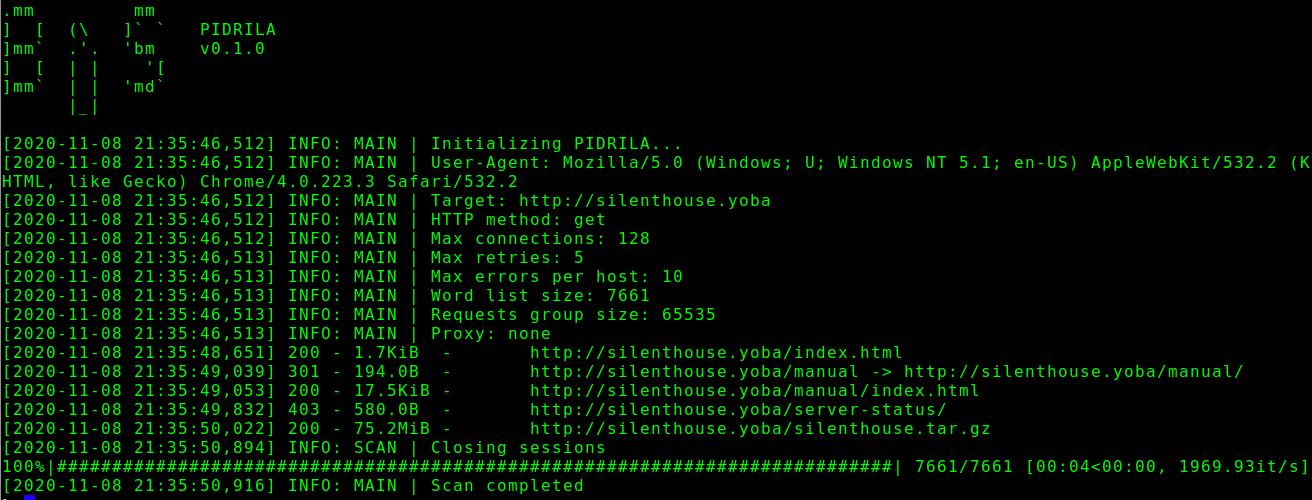
Screenshot
Usage examples
Scan single clearweb site
python3 ./pidrila.py -u http://silenthouse.yoba -M 128
Scan single onion site
python3 ./pidrila.py -u http://zqktlwi4fecvo6ro.onion -m 16 -M 16 --proxy=socks5h://127.0.0.1:9050
Fast batch scan with custom User-Agent
python3 ./pidrila.py -m 2048 -L darkweb_sites_list.txt --user-agent "Pantusha/2.0 (4.2BSD)"
License
License: GNU General Public License, version 2
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].