Rewind
Immediate Virus Infection Counter Measures
The Idea
Users that have opened a weaponized document are often aware that something is wrong with that document. In many cases they notice suspicious activity or aspects like
- a command line window pops up for a fraction of a second
- no contents show up after clicking "Enable Content"
- a ransom note appears on the desktop
- another program gets started without their interaction (e.g. browser window)
- the attached document doesn't open at all (.docx.exe extensions)
We can use these moments of realization to prevent further damage caused by malicious code by providing an emergency button that users can press when they believe that sh++ just hit the fan.
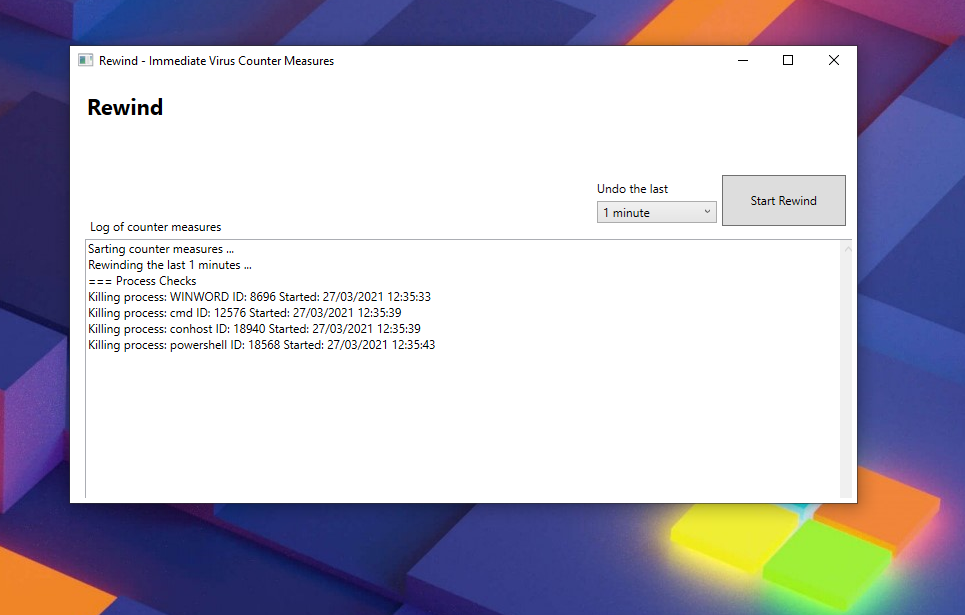
Rewind tries to kill or undo changes that occured recently by ending all recently spawned processes and removing all recently created files of certain types, as well as removing recently modified registry keys used for persistence (e.g. RUN key entries) regardless of their actual values.
This generic appreach doesn't recognize a specific type of threat but radically removes every process, file or registry key created within a very short time frame after a potential infection.
The Effect
During an infection the following things happen:
- new processes spawn
- executed code downloads further stages
- files are written to (temporary) folders on disk
- registry values are written to persist the threat
By providing the user with a panic button, we can try to interfere and try to stop some of the malicious activity before it is able to cause more damage in form of:
- disk encryption (Ransomware)
- propagation (Worms)
- dump and steal credentials (Credential Stealer)
- load further stages (Beacons)
The Side Effects
There are obvious side effects of these counter measures. Since it kills all processes accessible within the user context, removes files and registry keys, it could lead to the following situation:
- programs started within the selected time frame get killed (work is lost)
- legitimate files written to disk get removed
- program installations executed within the selected time frame may be broken
BUT:
- Since the time frame is rather short, we limit the effect of the measures to the most recent moments. It is unlikely that someone notices the suspicious activity and then starts to work on a Word document of Excel spreadsheet before pressing the panic button.
- We limit the file actions to certain file types often used by second stages or dropped by malicious documents.
- We limit the counter measures on the Registry to certain keys that are frequently used for persistence
The Limitation
All activity by Rewind is limited to the user's context. It is unable to kill important systems processes spawned within the targeted time frame.
It is therefore unable to kill processes that used local privilege escalation vulnerabilities to spawn processes in a privileged context.
Features
- Kills all processes started within the last X minutes and accessible from the current user context
Not yet implemented in the POC
- Removes all files written to disk within the last X minutes if extension is in the predefined blacklist (.exe, .dll, .ps1,.vbs, .hta, .bat, .js)
- Removes values from certain registry keys used for persitence if modified within the last X minutes
Screenshots
Further Ideas
- I would combine it with a "ping" (webhook, email, ticket etc.) to a local SOC or MDR provider, so that users can actively point out suspicious activity on their desktops to the analysts and they can search for threats on that endpoint within the indicated time frame (why not include the end user in the threat hunting activity?)