sgabe / Winaflpet
Programming Languages
Labels
Projects that are alternatives of or similar to Winaflpet
WinAFL Pet
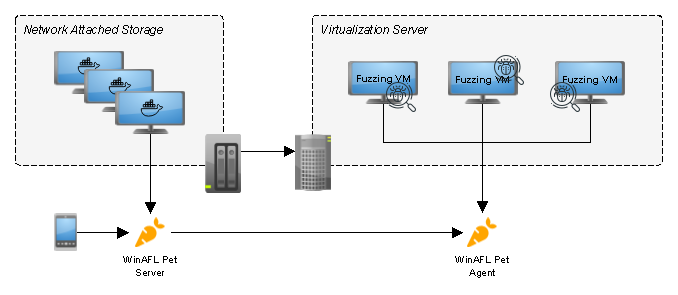
WinAFL Pet is a web user interface dedicated to WinAFL remote management via an agent running as a system service on fuzzing machines. The purpose of this project is to allow easy monitoring of fuzzing jobs running on several remote machines. Typical use case is to run the server component on a NAS or Raspberry PI and deploy agents on a virtualization server as you like. The below figure shows this typical deployment scenario.
Demo
Requirements
The following tools must be available on the fuzzing machine. It is recommended to install all the tools in a single directory (e.g. C:\Tools\...) for easier management. In general, if WinAFL runs fine manually, should be also fine when run by the agent. In fact, start fuzzing manually and continue with the agent once everything is set up correctly.
Deployment
Server
The server is written in Go using the Gin web framework and it is running in a minimal Docker image based on Alpine Linux. You could use the following command to start a container with persistent data storage:
> docker run -p 127.0.0.1:4141:4141 \
-v /path/to/winaflpet/data:/opt/winaflpet/data \
sgabe/winaflpet
Agent
The agent is also written in Go and designed for minimal footprint. Currently it uses the Windows Credential Vault to store an automatically generated API key. A service account with Log on as a service permission is necessary to retrieve the API key from the vault. See the FAQ for more information. Note down the key as it will be necessary to create a new agent on the management interface.
> winaflpet-agent.exe --service install
Username of service account: fuzzy\gabor
Password of service account: ********
Secret key of service account: <API_KEY>
> winaflpet-agent.exe --service start
Usage
Currently the default user is admin with the hostname or Docker container ID as password. Do not forget to change the default password after logging in. Follow the below steps to start fuzzing:
- Go to the Agents page and create a new agent using the previously generated secret key.
- Go to the Jobs page and create a new job associated with the agent created in the previous step.
-
Start a fuzzing instance by clicking on the
icon.
- Be patient until the start request completes (and WinAFL finishes the dry-run).
-
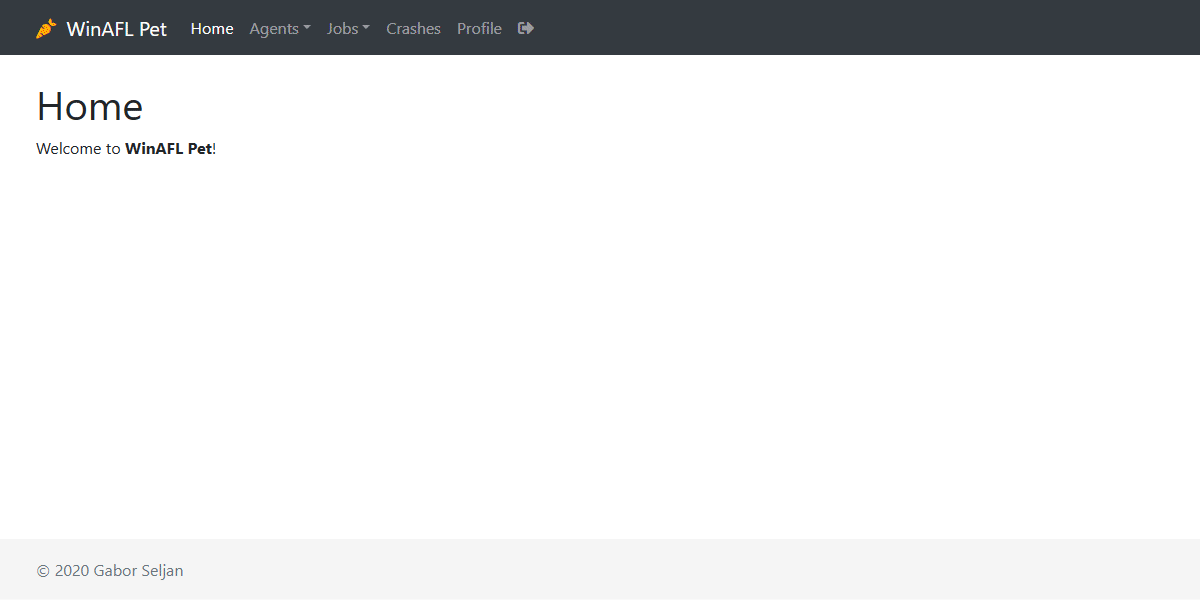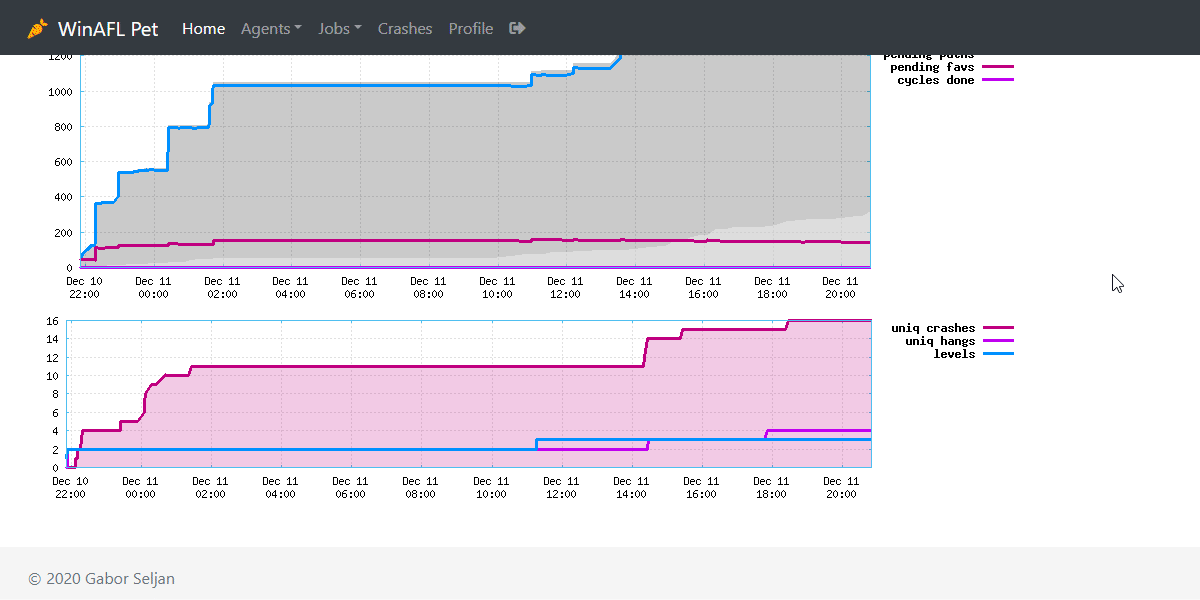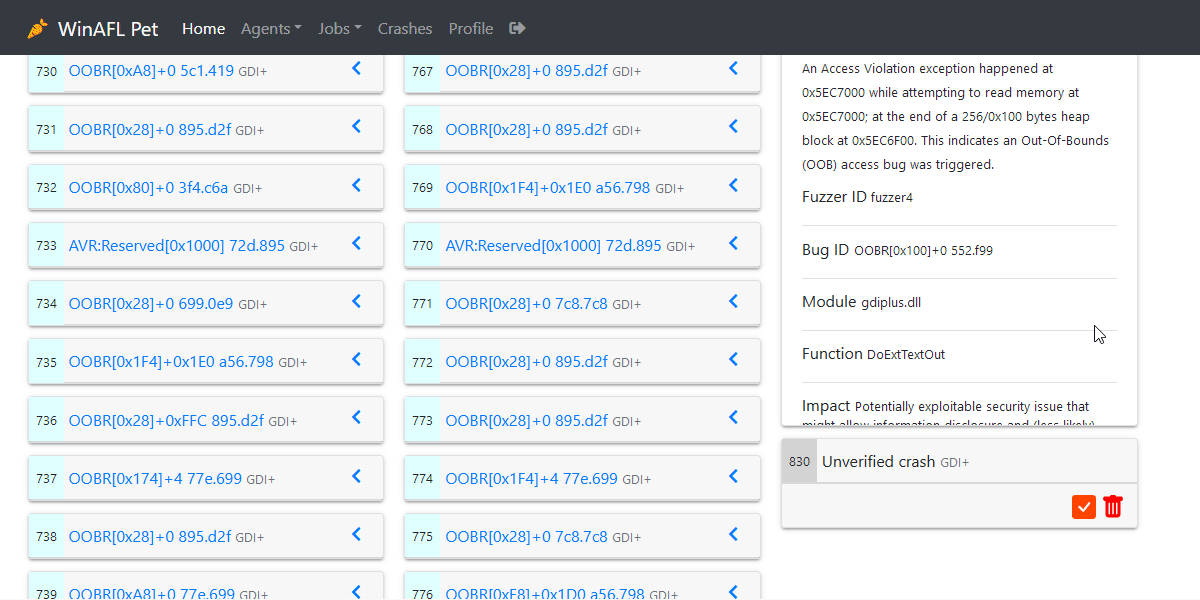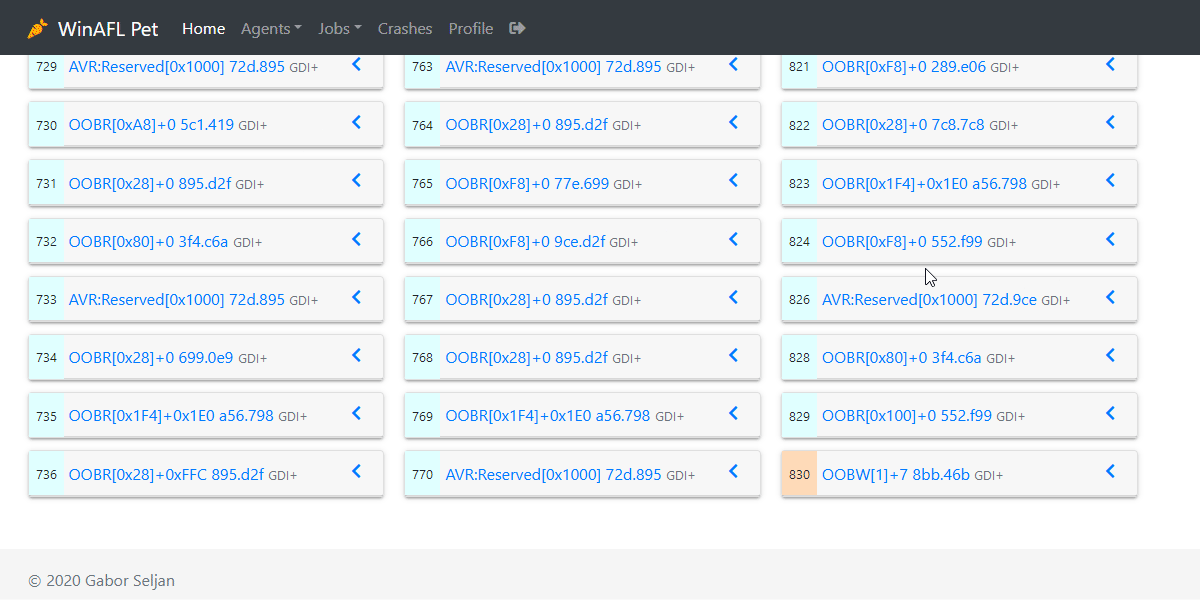
View statistics by clicking on the
icon.
-
Check running instances by clicking on the
icon.
-
Collect crash data by clicking on the
icon.
- Go to the Crashes page to verify new crashes by clicking on the
icon.
- Go to the Jobs page and stop all fuzzing instances by clicking on the
icon.
Environment variables
Some of the configuration options are exposed via environment variables to be used in the container. This allows you to customize WinAFL Pet without creating or modifying configuration files. The below table summarizes the available environment variables and their default settings.
| Variable | Default |
|---|---|
WINAFLPET_DATA |
data |
WINAFLPET_HOST |
127.0.0.1 |
WINAFLPET_PORT |
4141 |
WINAFLPET_LOG |
winaflpet.log |
Building WinAFL Pet
You can build the server in a Docker container on Linux:
make server
Or the service binary for the agent on Windows:
make agent
FAQ
How do I configure a user account to have Logon as a service permission?
Perform the following to edit the Local Security Policy of the computer where you want to fuzz:
- Open the Local Security Policy.
- Expand Local Policies and click on User Rights Assignment.
- In the right pane, double-click Log on as a service.
- Click on the Add User or Group... button to add the new user.
- In the Select Users or Groups dialogue, find the user you wish to enter and click OK.
- Click OK in the Log on as a service Properties to save changes.
Ensure that the user which you have added above is not listed in the Deny log on as a service policy in the Local Security Policy.