APKLeaks
Scanning APK file for URIs, endpoints & secrets.
Installation
It's fairly simple to install APKLeaks:
from PyPi
$ pip3 install apkleaksfrom Source
Clone repository and install requirements:
$ git clone https://github.com/dwisiswant0/apkleaks
$ cd apkleaks/
$ pip3 install -r requirements.txtfrom Docker
Pull the Docker image by running:
$ docker pull dwisiswant0/apkleaks:latestDependencies
APKLeaks using jadx disassembler to decompile APK file. If it doesn't exist in your environment, it'll ask you to download.
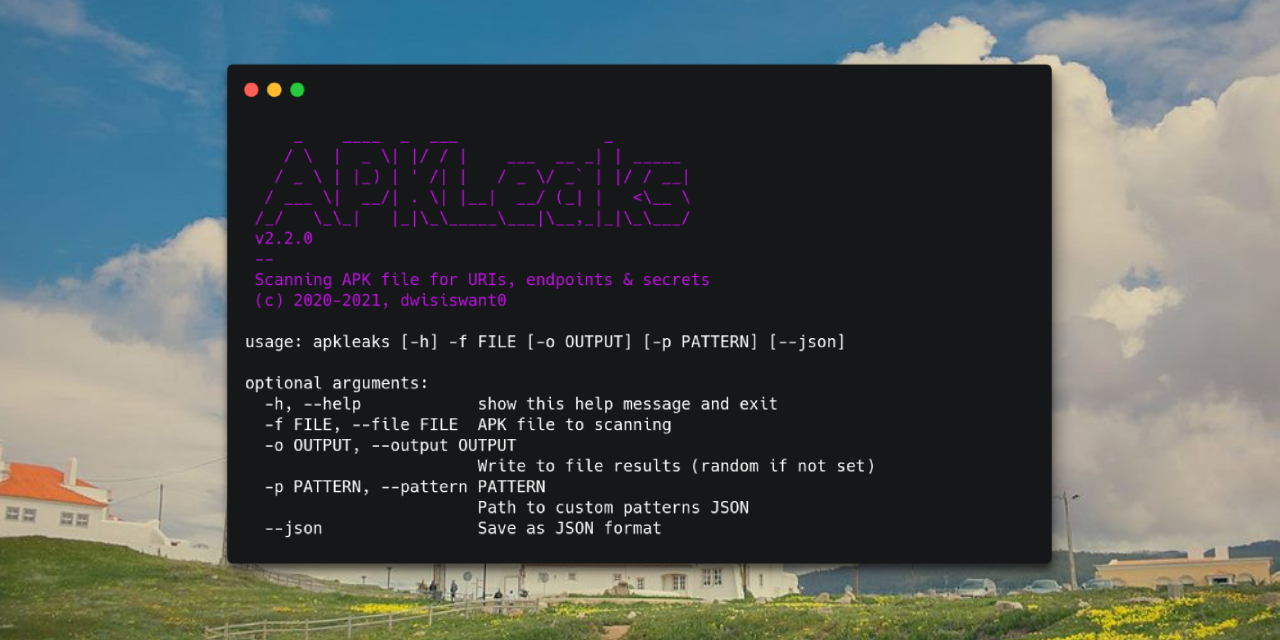
Usage
Simply,
$ apkleaks -f ~/path/to/file.apk
# from Source
$ python3 apkleaks.py -f ~/path/to/file.apk
# or with Docker
$ docker run -it --rm -v /tmp:/tmp dwisiswant0/apkleaks:latest -f /tmp/file.apkOptions
Here are all the options it supports.
| Argument | Description | Example |
|---|---|---|
| -f, --file | APK file to scanning | apkleaks -f file.apk |
| -o, --output | Write to file results (random if not set) | apkleaks -f file.apk -o results.txt |
| -p, --pattern | Path to custom patterns JSON | apkleaks -f file.apk -p custom-rules.json |
| -a, --args | Disassembler arguments | apkleaks -f file.apk --args="--deobf --log-level DEBUG" |
| --json | Save as JSON format | apkleaks -f file.apk -o results.json --json |
Output
In general, if you don't provide -o argument, then it will generate results file automatically.
NOTE: By default it will also save the results in text format, use --json argument if you want JSON output format.
Pattern
Custom patterns can be added with the following argument to provide sensitive search rules in the JSON file format: --pattern /path/to/custom-rules.json. If not set, it'll use default patterns from regexes.json file.
Example patterns file:
// custom-rules.json
{
"Amazon AWS Access Key ID": "AKIA[0-9A-Z]{16}",
...
}$ apkleaks -f /path/to/file.apk -p rules.json -o ~/Documents/apkleaks-results.txt
Arguments (disassembler)
We give user complete discretion to pass the disassembler arguments. For example, if you want to activate threads in jadx decompilation process, you can add it with -a/--args argument, example: --args="--threads-count 5".
$ apkleaks -f /path/to/file.apk -a "--deobf --log-level DEBUG"
NOTE: Please pay attention to the default disassembler arguments we use to prevent collisions.
License
apkleaks is distributed under Apache 2.
Acknowledments
Since this tool includes some contributions, and I'm not an asshole, I'll publically thank the following users for their helps and resources:
- @ndelphit - for his inspiring
apkurlgrep, that's why this tool was made. - @dxa4481 and y'all who contribute to
truffleHogRegexes. - @GerbenJavado & @Bankde - for awesome pattern to discover URLs, endpoints & their parameters from
LinkFinder. - @tomnomnom - a
gfpatterns. - @pxb1988 - for awesome APK dissambler
dex2jar. - @subho007 for standalone APK parser.
SHA2048#4361(Discord user) that help me porting code to Python3.- @Ry0taK because he had reported an OS command injection bug.
- @dee__see - for curated potentially sensitive tokens,
NotKeyHacks. - All contributors.