atc-project / Atc React
Programming Languages
Projects that are alternatives of or similar to Atc React
RE&CT
The project represents the following:
- A framework — knowledge base of actionable Incident Response techniques
- A community-driven collection of Security Incident Response Playbooks
- A data source of the Atomic Threat Coverage framework
The RE&CT Framework
The RE&CT Framework is designed for accumulating, describing and classification actionable Incident Response techniques.
RE&CT's philosophy is based on the MITRE's ATT&CK framework.
The columns represent Response Stages.
The cells repsresent Response Actions.
(Image generated by RE&CT Navigator)
The main use cases:
- Prioritization of Incident Response capabilities development, including skills development, technical measures acquisition/deployment, internal procedures development, etc
- Gap analysis — determine "coverage" of existing Incident Response capabilities
The main resources:
- RE&CT Navigator (modified ATT&CK Navigator) for visualization and observing the big picture
- Automatically generated RE&CT website is the best place for getting details about existing analytics
- Automatically generated Atlassian Confluence knowledge base - exporting functionality demonstration
Actionable Analytics
The ATC RE&CT project inherits the "Actionable Analytics" paradigm from the ATC project, which means that the analytics are:
-
human-readable (
.md) for sharing/using in operations -
machine-readable (
.yml) for automatic processing/integrations - executable by Incident Response Platform (TheHive Case Templates only, at the moment)
Simply saying, the analytics are stored in .yml files, that are automatically converted to .md documents (with jinja) and .json TheHive Case Templates.
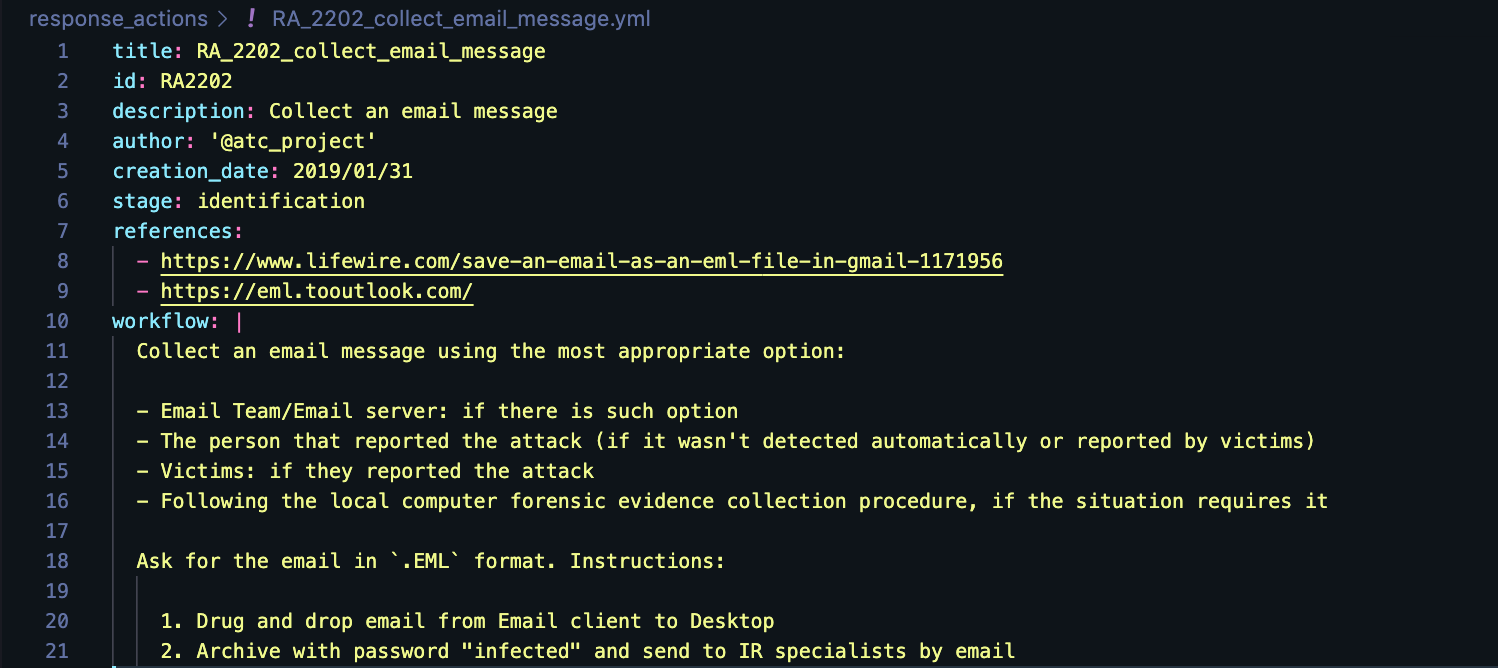
Response Action
Response Action is a description of a specific atomic procedure/task that has to be executed during the Incident Response. It is an initial entity that is used to construct Response Playbooks.
Here is an example of Response Action:
- Automatically created Markdown file
- Automatically created mkdocs web page
- Automatically created Confluence page
Each Response Action mapped to a specific Response Stage.
The first digit of the Response Action ID reflects a Stage it belongs to:
- 1: Preparation
- 2: Identification
- 3: Containment
- 4: Eradication
- 5: Recovery
- 6: Lessons Learned
The second digit of the Response Action ID reflects a Category it belongs to:
- 0: General
- 1: Network
- 2: Email
- 3: File
- 4: Process
- 5: Configuration
- 6: Identity
This way, using Response Action ID, you can see the Stage and Category it belongs to.
For example, RA2202: Collect an email message is related to Stage 2 (Identification) and Category 2 (Email).
The categorization aims to improve Incident Response process maturity assessment and roadmap development.
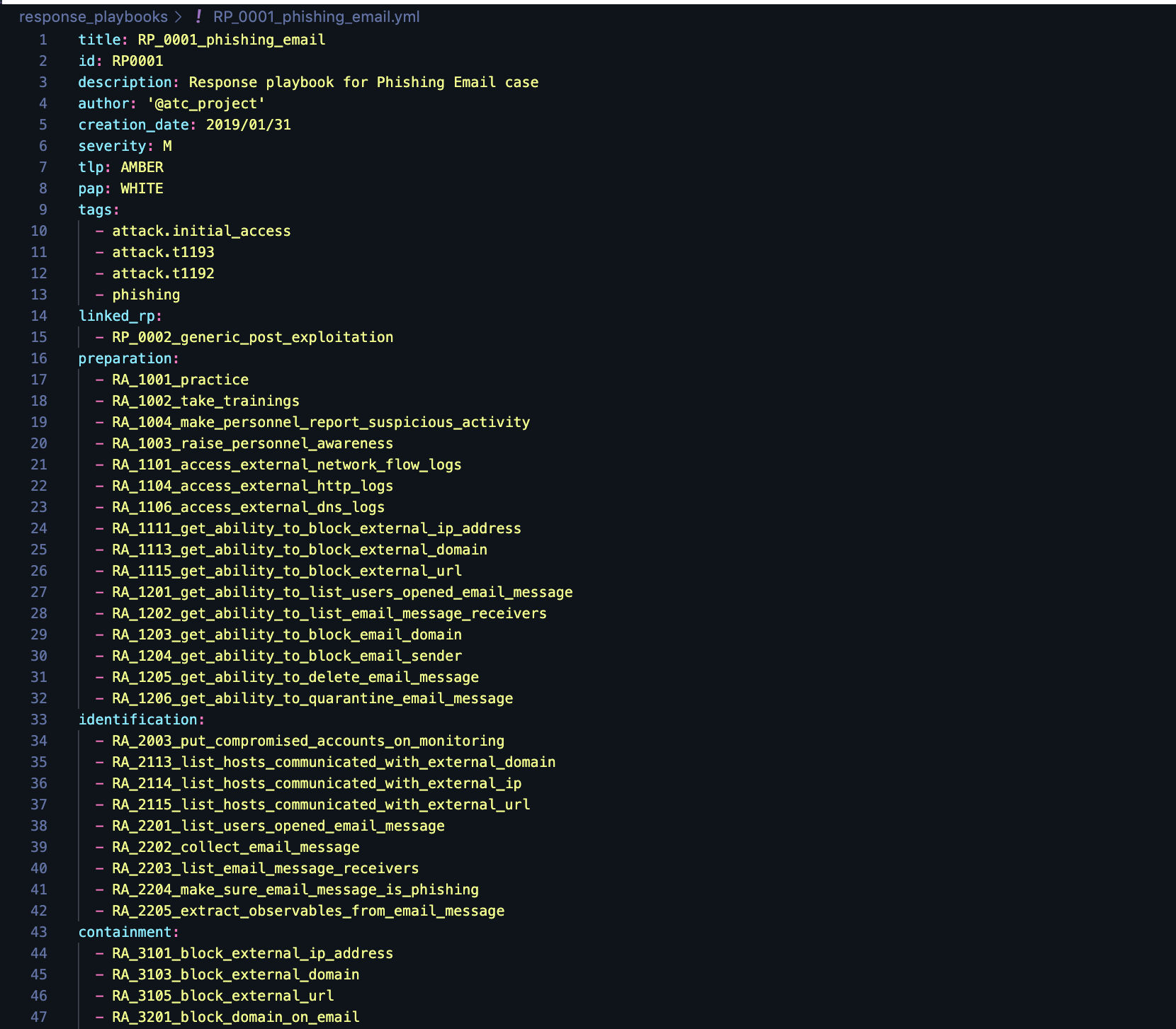
Response Playbook
Response Playbook is an Incident Response plan, that represents a complete list of procedures/tasks (Response Actions) that has to be executed to respond to a specific threat with optional mapping to the MITRE's ATT&CK or Misinfosec's AMITT frameworks.
Here is an example of Response Playbook:
- Automatically created Markdown file
- Automatically created mkdocs web page
- Automatically created Confluence page
Response Playbook could include a description of the workflow, specific conditions/requirements, details on the order of Response Actions execution, or any other relevant information.
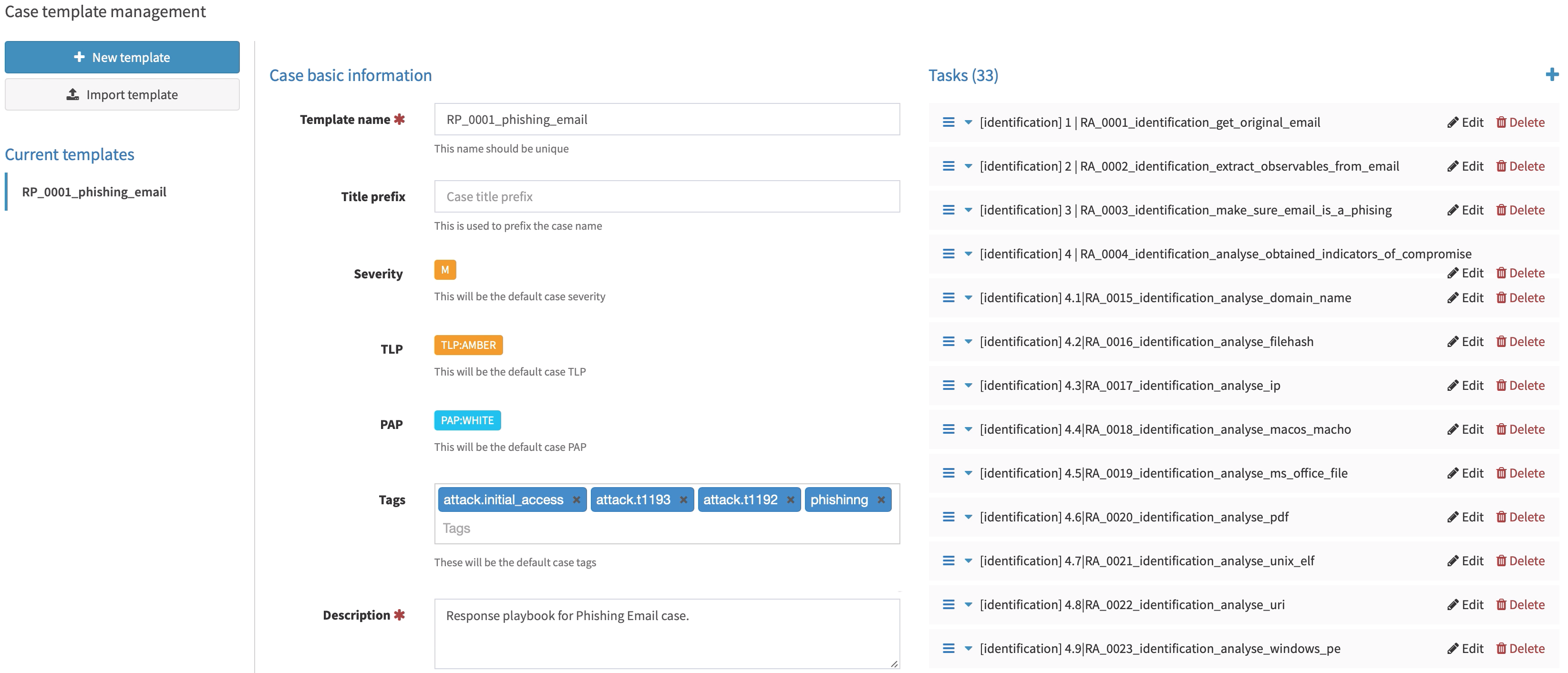
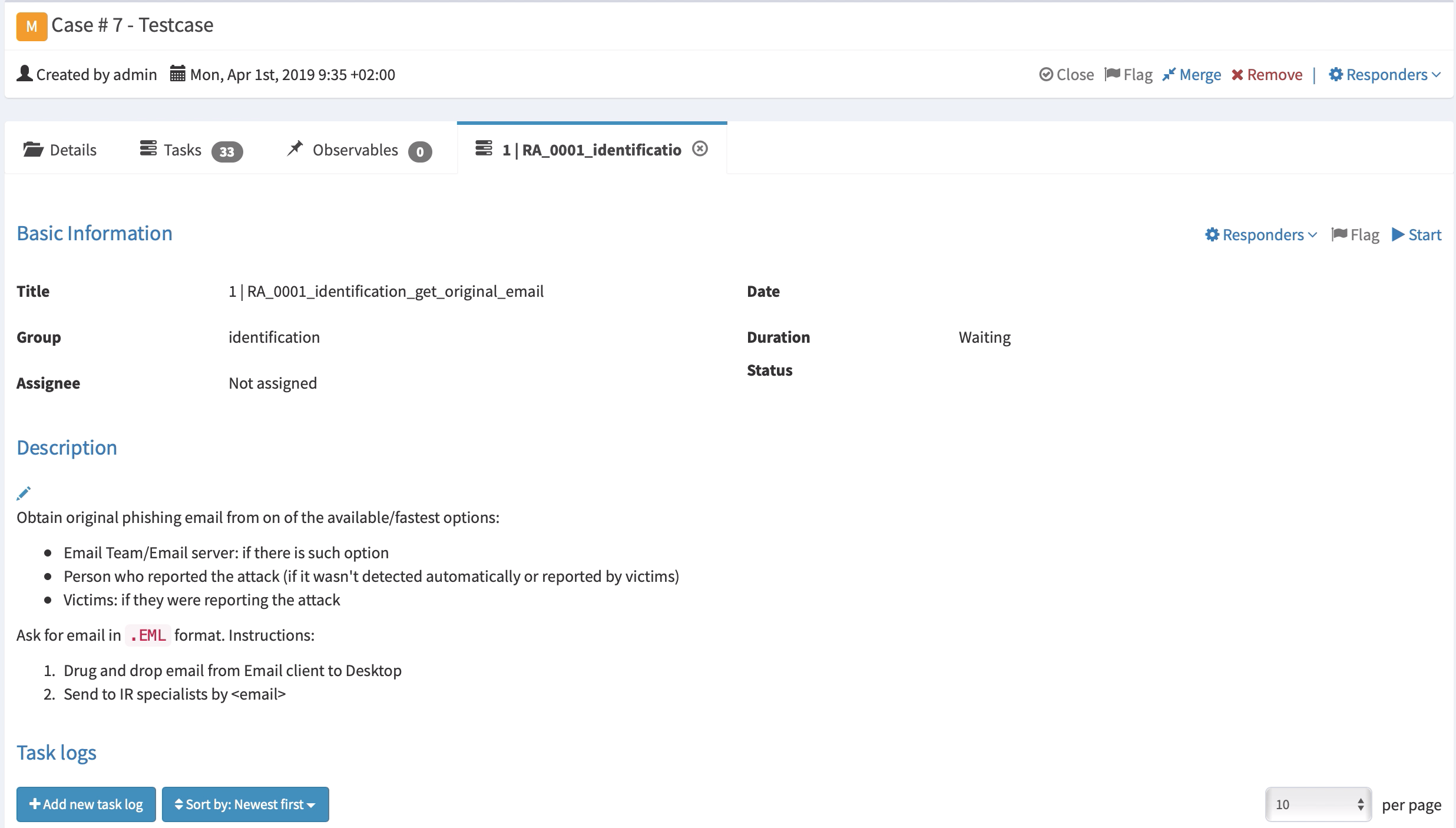
TheHive Case Templates
TheHive Case Templates are built on top of the Response Playbooks. Each task in a Case Template is a Response Action (with full description).
Here is the example of an imported TheHive Case Template:
TheHive Case Templates could be found in docs/thehive_templates directory and could be imported to TheHive via its web interface.
Data source of the ATC framework
ATC RE&CT project plays a role of data source for the Atomic Threat Coverage framework, that uses it to generate Markdown and Confluence knowledge bases, ATT&CK Navigator profiles, Elasticsearch indexes and other analytics.
Originally analytics related to Incident Response were part of the ATC, but we decided to move it into a separate project to make it easier to maintain and provide an option for integration with other projects in this area.
Usage
-
Make sure you are compliant with the requirements
-
Create configuration file by copying configuration file template
scripts/config.default.ymltoconfig.yml(root of the project). Modify it, following the guideline in the configuration file template. -
Modify existing
.ymlfiles, or develop your own analytics using the templates of Response Actions or Response Playbooks. They should be stored in the directories according to their type. -
When
.ymlfiles are ready, convert them to.mddocuments, import them into Confluence, generate TheHive templates and RE&CT Navigator layer using the following commands:python3 main.py --markdown --auto --init python3 main.py --confluence --auto --init python3 main.py --thehive python3 main.py -NAVYou will find the outcome in the
docsdirectory and Confluence pages (according to the configuration). At the moment, RE&CT Navigator profile could be opened only in the customized application. -
Generate your own (private) website with your analytics, using mkdocs:
python3 main.py -MK # automatic mkdocs config (navigation) generation python3 -m mkdocs buildThe website will be stored in the
sitedirectory. You can preview it with the following command:python3 -m mkdocs serve
Requirements
- Python 3.7
-
PyYAML, mkdocs, jinja2 and stix2 (optionally) Python libraries. They could be installed with the following command:
python3 -m pip install -r requirements.txt
Contacts
Contributors
- Timur Zinniatullin, @zinint
- Daniil Svetlov, @Mr_4nders0n
- Andreas Hunkeler, @Karneades
- Patrick Abraham, @pjabes
Would you like to become one? You are very welcome! Our CONTRIBUTING guideline is a good starting point.
Roadmap
The roadmap and related discussions could be found in the project issues by labes:
License
See the LICENSE file.