splunk / Attack_range
Projects that are alternatives of or similar to Attack range
Splunk Attack Range ⚔️
Purpose 🛡
The Attack Range is a detection development platform, which solves three main challenges in detection engineering. First, the user is able to build quickly a small lab infrastructure as close as possible to a production environment. Second, the Attack Range performs attack simulation using different engines such as Atomic Red Team or Caldera in order to generate real attack data. Third, it integrates seamlessly into any Continuous Integration / Continuous Delivery (CI/CD) pipeline to automate the detection rule testing process.
Demo 📺
A short demo (< 6 min) which shows the basic functions of the attack range. It builds a testing enviroment using terraform, walks through the data collected by Splunk. Then attacks it using MITRE ATT&CK Technique T1003 and finally showcases how Splunk Security Content searches are used to detect the attack.
Building 👷♂️
Attack Range can be built in three different ways:
- cloud with terraform plus AWS or Azure.
- locally with vagrant and virtualbox
- serverless with terraform and AWS services
Installation 🏗
AWS and Ubuntu 18.04
source <(curl -s 'https://raw.githubusercontent.com/splunk/attack_range/develop/scripts/ubuntu_deploy.sh')aws configurepython attack_range.py configure
AWS and MacOS
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/splunk/attack_range/develop/scripts/macos_deploy_aws.sh)" && cd attack_range && source venv/bin/activateaws configurepython attack_range.py configure
Azure and MacOS
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/splunk/attack_range/develop/scripts/macos_deploy_azure.sh)" && cd attack_range && source venv/bin/activateaz loginpython attack_range.py configure
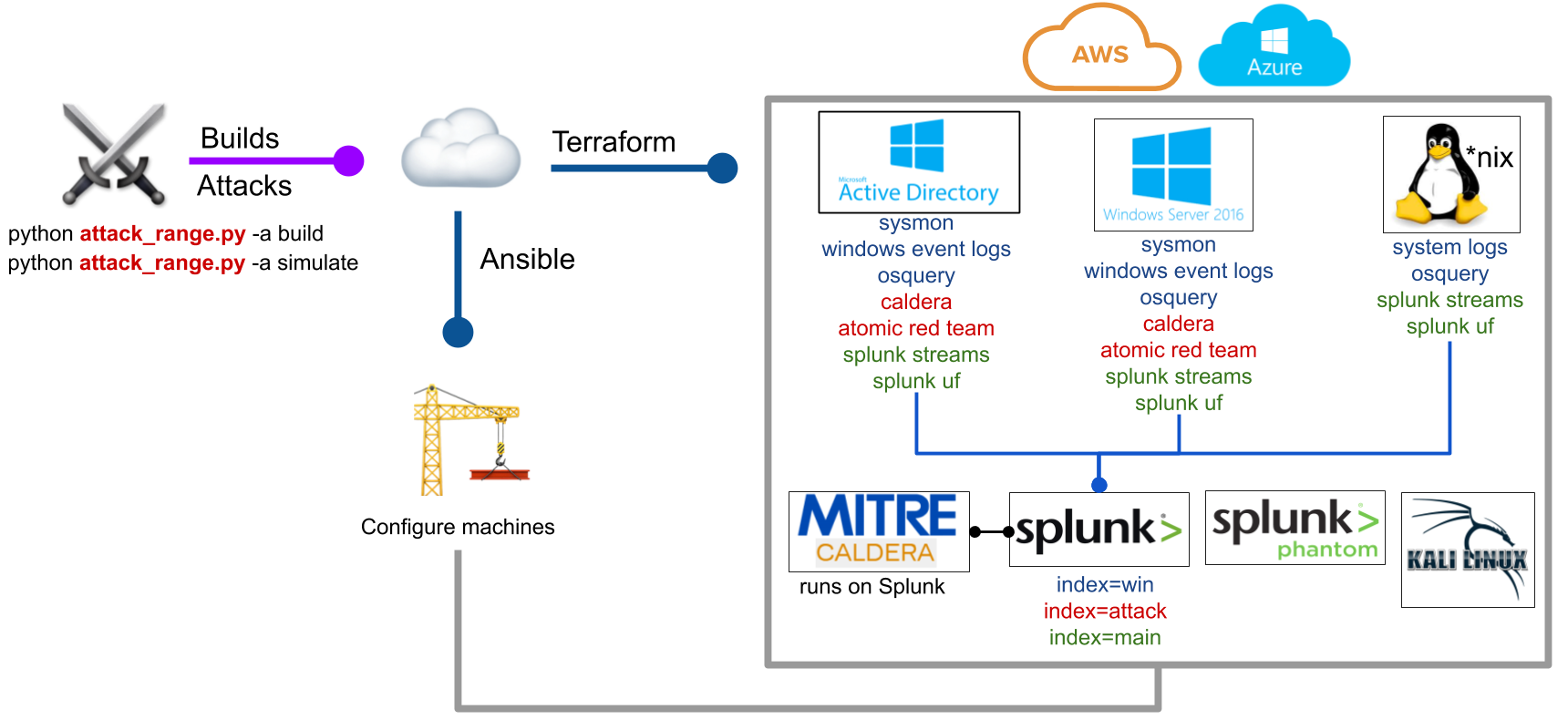
Architecture 🏯
The virtualized deployment of Attack Range consists of:
- Windows Domain Controller
- Windows Server
- Windows Workstation
- A Kali Machine
- Splunk Server
- Phantom Server
- Zeek Sensor
Which can be added/removed/configured using attack_range.conf. More machines such as Phantom, Linux server, Linux client, MacOS clients are currently under development.
An approximate cost estimate for running attack_range on AWS can be found here.
Logging
The following log sources are collected from the machines:
- Windows Event Logs (
index = win) - Sysmon Logs (
index = win) - Powershell Logs (
index = win) - Network Logs with Splunk Stream (
index = main) - Attack Simulation Logs from Atomic Red Team and Caldera (
index = attack)
Running 🏃♀️
Attack Range supports different actions:
- Configuring Attack Range
- Build Attack Range
- Perform Attack Simulation
- Test with Attack Range
- Destroy Attack Range
- Stop Attack Range
- Resume Attack Range
- Dump Log Data from Attack Range
Configure Attack Range
python attack_range.py configure
Build Attack Range
python attack_range.py build
Show Attack Range Infrastructure
python attack_range.py show
Perform Attack Simulation
python attack_range.py simulate -st T1003.001 -t ar-win-dc-default-username-33048
Test with Attack Range
python attack_range.py test -tf tests/T1003_001.yml
Destroy Attack Range
python attack_range.py destroy
Stop Attack Range
python attack_range.py stop
Resume Attack Range
python attack_range.py resume
Dump Log Data from Attack Range
python attack_range.py dump -dn data_dump
Replay Dumps into Attack Range Splunk Server
- Replay previously saved dumps from Attack Range
python attack_range.py replay -dn data_dump [--dump NAME_OF_DUMP]
- default will dump all enabled dumps described in
attack_data/dumps.yml - with optional argument
--dumpyou can specify which dump to replay
python attack_range.py replay -dn data_dump --dump windows_sec_events
Features 💍
-
- Indexing of Microsoft Event Logs, PowerShell Logs, Sysmon Logs, DNS Logs, ...
- Preconfigured with multiple TAs for field extractions
- Out of the box Splunk detections with Enterprise Security Content Update (ESCU) App
- Preinstalled Machine Learning Toolkit (MLTK)
- pre-indexed BOTS datasets
- Splunk UI available through port 8000 with user admin
- ssh connection over configured ssh key
-
- Splunk Enterprise Security is a premium security solution requiring a paid license.
- Enable or disable Splunk Enterprise Security in attack_range.conf
- Purchase a license, download it and store it in the apps folder to use it.
-
- Splunk Phantom is a Security Orchestration and Automation platform
- For a free development license (100 actions per day) register here
- Enable or disable Splunk Phantom in attack_range.conf
-
Windows Domain Controller & Window Server & Windows 10 Client
- Can be enabled, disabled and configured over attack_range.conf
- Collecting of Microsoft Event Logs, PowerShell Logs, Sysmon Logs, DNS Logs, ...
- Sysmon log collection with customizable Sysmon configuration
- RDP connection over port 3389 with user Administrator
-
- Attack Simulation with Atomic Red Team
- Will be automatically installed on target during first execution of simulate
- Atomic Red Team already uses the new Mitre sub-techniques
-
- Adversary Emulation with Caldera
- Installed on the Splunk Server and available over port 8888 with user admin
- Preinstalled Caldera agents on windows machines
-
- Preconfigured Kali Linux machine for penetration testing
- ssh connection over configured ssh key
Support 📞
Please use the GitHub issue tracker to submit bugs or request features.
If you have questions or need support, you can:
- Join the #security-research room in the Splunk Slack channel
- Post a question to Splunk Answers
- If you are a Splunk Enterprise customer with a valid support entitlement contract and have a Splunk-related question, you can also open a support case on the https://www.splunk.com/ support portal
Contributing 🥰
We welcome feedback and contributions from the community! Please see our contribution guidelines for more information on how to get involved.
Author
Contributors
- Bhavin Patel
- Rod Soto
- Russ Nolen
- Phil Royer
- Joseph Zadeh
- Rico Valdez
- Dimitris Lambrou
- Dave Herrald
- Ignacio Bermudez Corrales
- Peter Gael
- Josef Kuepker
- Shannon Davis