jessfraz / Aws Fargate Action
A GitHub action to deploy to AWS Fargate on push to the master branch.
Stars: ✭ 116
Labels
Projects that are alternatives of or similar to Aws Fargate Action
Spinnaker Terraform
A set of terraform scripts to create an environment from scratch with a Bastion Host, Jenkins, and Spinnaker
Stars: ✭ 106 (-8.62%)
Mutual labels: hcl
Terraform Aws Ecr
Terraform Module to manage Docker Container Registries on AWS ECR
Stars: ✭ 110 (-5.17%)
Mutual labels: hcl
Terraform aws scp
AWS Organizations Service Control Policies (SCPs) written in HashiCorp Terraform.
Stars: ✭ 114 (-1.72%)
Mutual labels: hcl
Terraform Google Vault
A Terraform Module for how to run Vault on Google Cloud using Terraform and Packer
Stars: ✭ 108 (-6.9%)
Mutual labels: hcl
Terraform Up And Running Code
Code samples for the book "Terraform: Up & Running" by Yevgeniy Brikman
Stars: ✭ 1,739 (+1399.14%)
Mutual labels: hcl
Kubernetes Coreos Terraform
Simple Kubernetes cluster on CoreOS in AWS using Terraform
Stars: ✭ 114 (-1.72%)
Mutual labels: hcl
Terraform Aws Vpc
An example of Terraform which brings up a VPC with Public/Private Subnets
Stars: ✭ 109 (-6.03%)
Mutual labels: hcl
Best Practices
No description, website, or topics provided.
Stars: ✭ 1,478 (+1174.14%)
Mutual labels: hcl
Terraform Aws Config
Enables AWS Config and adds managed config rules with good defaults.
Stars: ✭ 107 (-7.76%)
Mutual labels: hcl
Terraform Null Ansible
Terraform Module to run ansible playbooks
Stars: ✭ 114 (-1.72%)
Mutual labels: hcl
Terraform Aws Dynamic Subnets
Terraform module for public and private subnets provisioning in existing VPC
Stars: ✭ 106 (-8.62%)
Mutual labels: hcl
Terraform Nixos
A set of Terraform modules that are designed to deploy NixOS
Stars: ✭ 116 (+0%)
Mutual labels: hcl
Hello Lambda
🔥 An example of a Python (AWS) Lambda exposed with API Gateway, configured with Terraform.
Stars: ✭ 114 (-1.72%)
Mutual labels: hcl
Awesome Codepipeline Ci
an AWS CodePipeline, AWS CodeBuild, AWS APIGateway & AWS Lambda CI
Stars: ✭ 112 (-3.45%)
Mutual labels: hcl
AWS Fargate Action
A GitHub action to deploy to AWS Fargate on push to the master branch.
Table of Contents
Usage
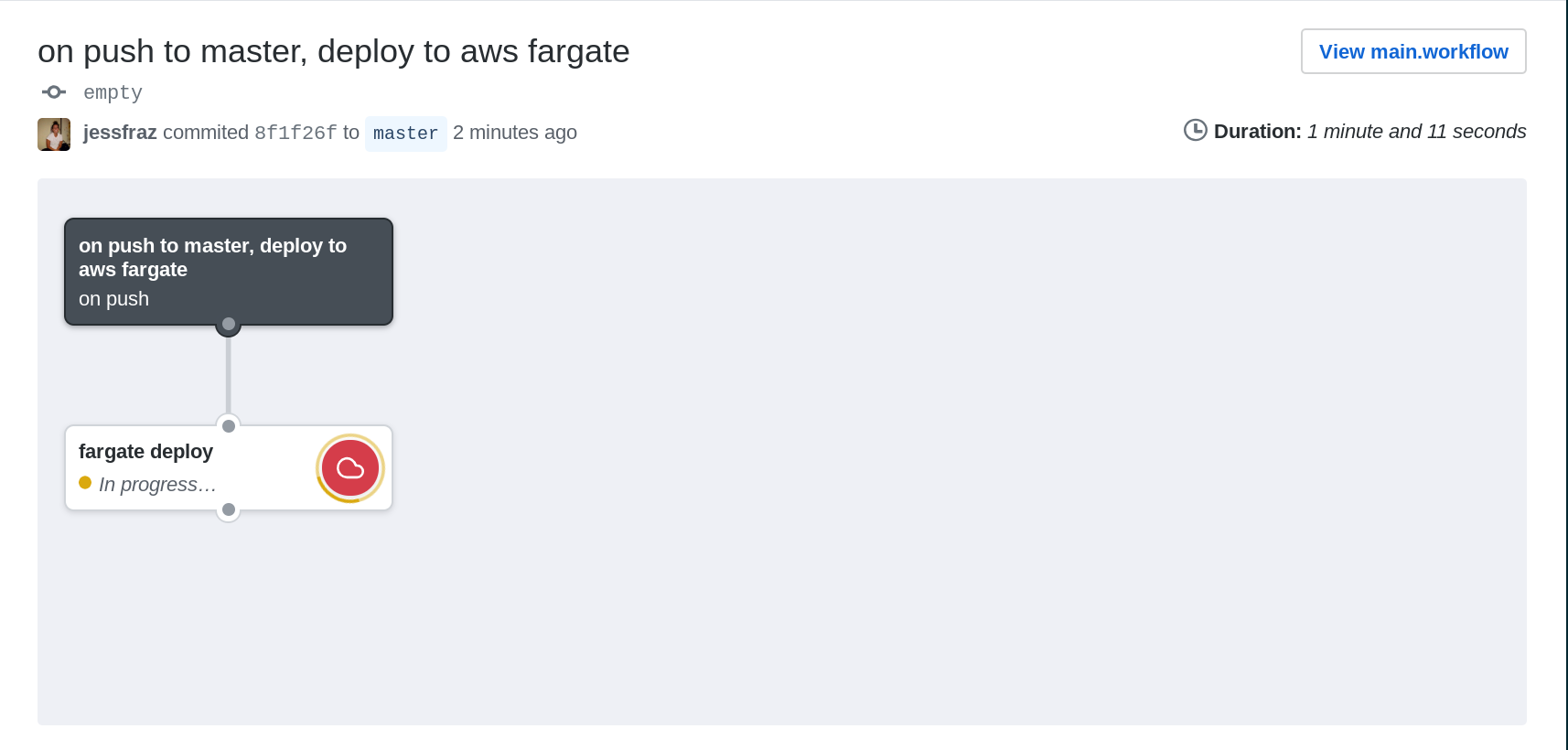
workflow "on push to master, deploy to aws fargate" {
on = "push"
resolves = ["fargate deploy"]
}
action "fargate deploy" {
uses = "jessfraz/[email protected]"
env = {
AWS_REGION = "us-west-2"
IMAGE = "r.j3ss.co/party-clippy"
PORT = "8080"
COUNT = "2"
CPU = "256"
MEMORY = "512"
BUCKET = "aws-fargate-action"
}
secrets = ["AWS_ACCESS_KEY_ID", "AWS_SECRET_ACCESS_KEY"]
}
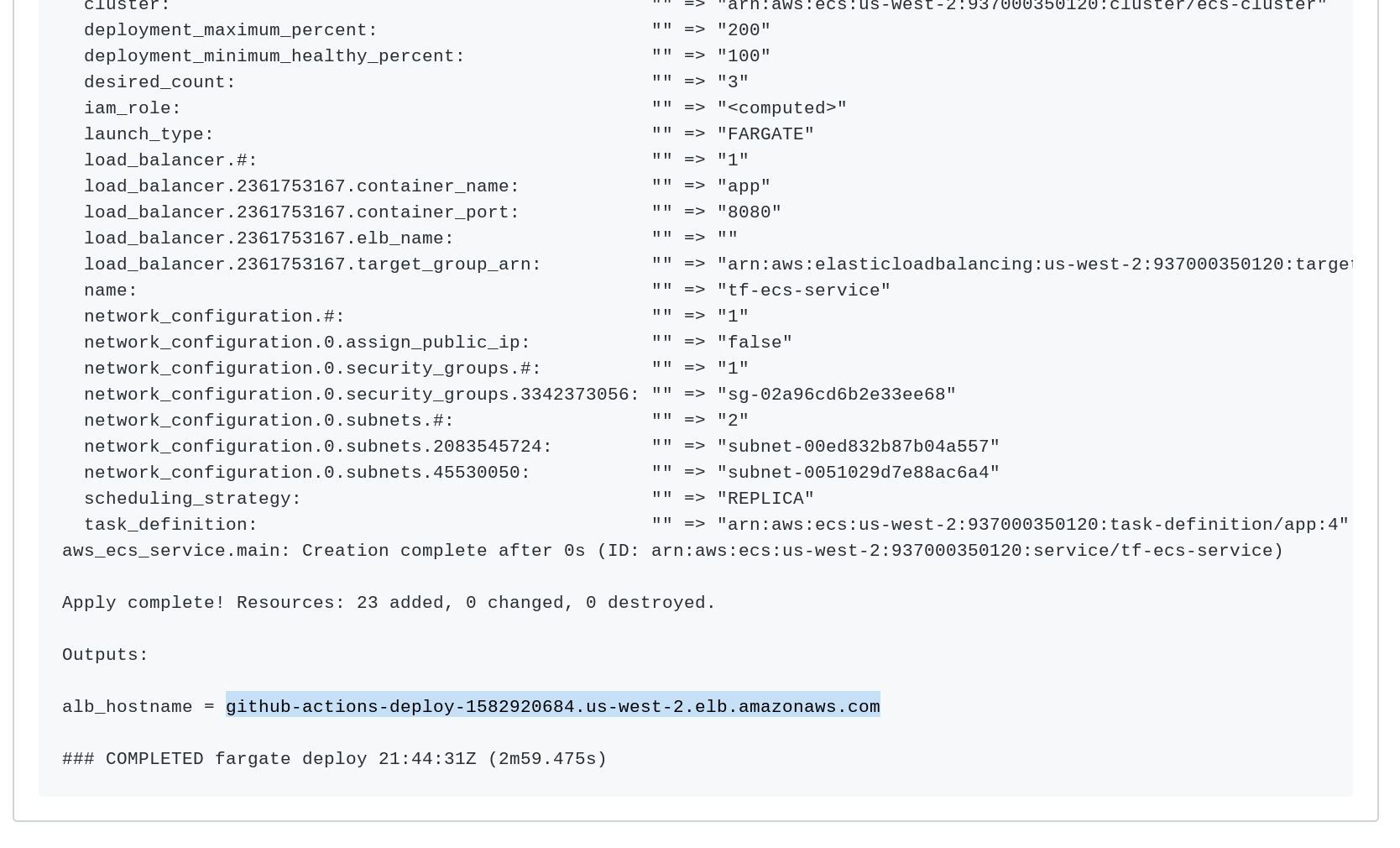
NOTE: The bucket above needs to be in the same region as
AWS_REGIONAND it needs to be created before running the action. That is the only prerequisite.
The action will run...
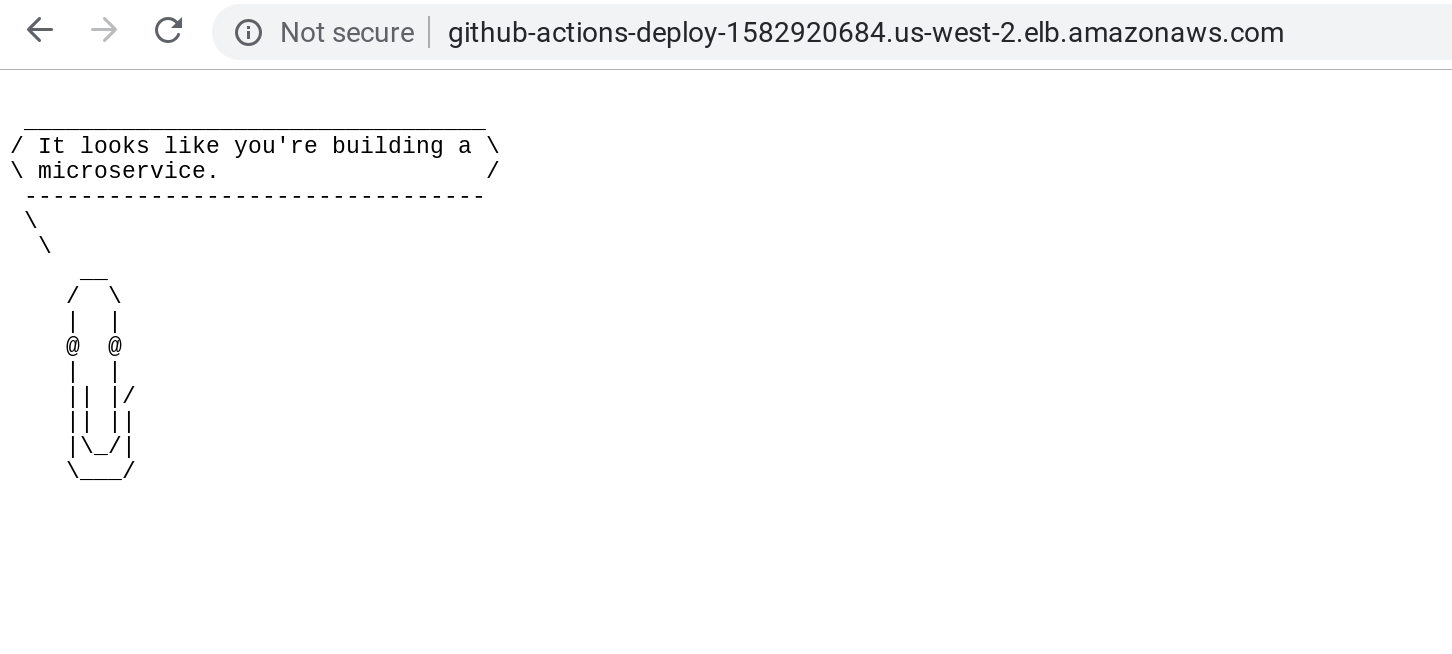
On success, it will output the URL...
Go to that in your browser...
Contributing
Running the tests
The tests use shellcheck. You don't need to install anything. They run in a container.
$ make test
Using the Makefile
$ make help
aws-apply Run terraform apply for Amazon.
aws-destroy Run terraform destroy for Amazon.
aws-plan Run terraform plan for Amazon.
shellcheck Runs the shellcheck tests on the scripts.
test Runs the tests on the repository.
update-terraform Update terraform binary locally from the docker container.
update Update terraform binary locally.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].