hashicorp / Terraform Google Vault
Labels
Projects that are alternatives of or similar to Terraform Google Vault
Vault for Google Cloud Platform (GCP)
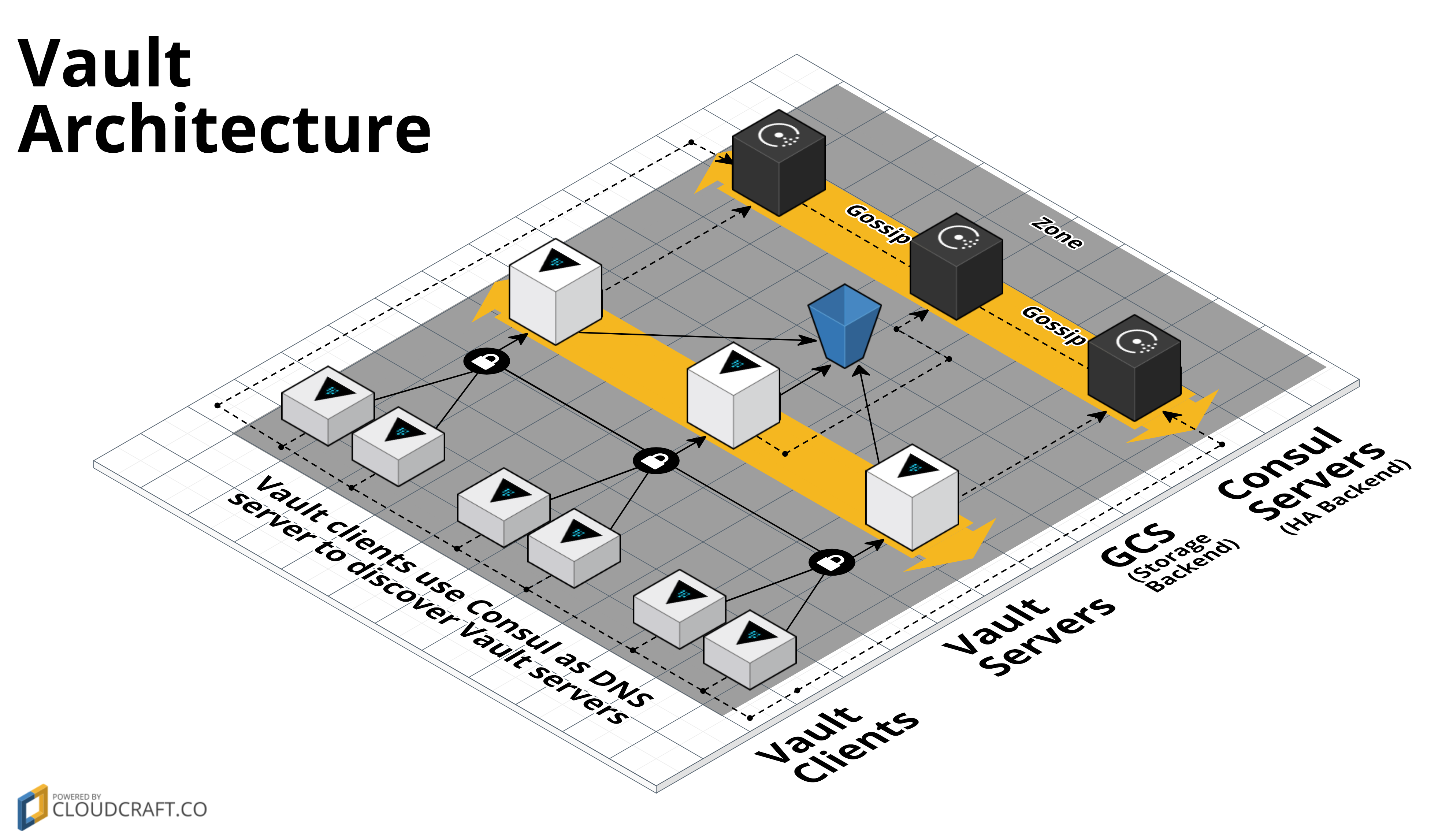
This repo contains a Terraform Module for how to deploy a Vault cluster on GCP using Terraform. Vault is an open source tool for managing secrets. This Module uses GCS as a storage backend and a Consul server cluster as a high availability backend:
This Module includes the following submodules:
-
install-vault: This module can be used to install Vault. It can be used in a Packer template to create a Vault Google Image.
-
run-vault: This module can be used to configure and run Vault. It can be used in a Startup Script to fire up Vault while the server is booting.
-
install-nginx: This module can be used to install Nginx. It can be used in a Packer template to create a Vault Google Image. This module is only necessary when using a Load Balancer which requires a Health Checker.
-
run-nginx: This module can be used to configure and run nginx. It can be used in a Startup Script to launch nginx while the server is booting.
-
vault-cluster: Terraform code to deploy a cluster of Vault servers using a Managed Instance Group.
-
vault-lb-fr: Configures a Regional External Load Balancer in front of Vault if you need to access it from the public Internet.
-
private-tls-cert: Generate a private TLS certificate for use with a private Vault cluster.
-
update-certificate-store: Add a trusted, CA public key to an OS's certificate store. This allows you to establish TLS connections to services that use this TLS certs signed by this CA without getting x509 certificate errors.
What's a Terraform Module?
A Terraform Module refers to a self-contained packages of Terraform configurations that are managed as a group. This repo is a Terraform Module and contains many "submodules" which can be composed together to create useful infrastructure patterns.
Who maintains this Module?
This Module is maintained by Gruntwork. If you're looking for help or commercial support, send an email to [email protected]. Gruntwork can help with:
- Setup, customization, and support for this Terraform Module.
- Commercially supported Modules for other types of infrastructure, such as VPCs, Docker clusters, databases, and continuous integration.
- Modules that meet compliance requirements, such as HIPAA.
- Consulting & Training on AWS, Google Cloud, Terraform, and DevOps.
How do you use this Module?
This Module adheres to Terraform Module Conventions and has the following folder structure:
- modules: This folder contains the reusable code for this Terraform Module, broken down into one or more submodules.
- examples: This folder contains examples of how to use the submodules.
- test: Automated tests for the submodules and examples.
Click on each of the submodules above for more details.
To deploy Vault with this Terraform Module, you will need to deploy two separate clusters: one to run Consul servers (which Vault uses as a high availability backend) and one to run Vault servers.
To deploy the Consul server cluster, use the Consul GCP Module.
To deploy the Vault cluster:
-
Create a Google Image that has Vault installed (using the install-vault module) and the Consul agent installed (using the install-consul module). Here is an example Packer template. Google Cloud does not allow the creation of public Images so you must create this Image on your own to proceed!
-
Deploy that Image across a Managed Instance Group using the Terraform vault-cluster-module.
1 TODO ACCESSING THE CLUSTER THROUGH SSH
-
Execute the run-consul script with the
--clientflag during boot on each Instance to have the Consul agent connect to the Consul server cluster. -
Execute the run-vault script during boot on each Instance to create the Vault cluster.
-
If you only need to access Vault from inside your GCP account (recommended), run the install-dnsmasq module on each server, and that server will be able to reach Vault using the Consul Server cluster as the DNS resolver (e.g. using an address like
vault.service.consul). See the vault-cluster-private example for working sample code. -
If you need to access Vault from the public Internet, deploy the vault-lb-fr module and have all requests to Vault go through the Load Balancer. See the vault-cluster-public example for working sample code.
-
Head over to the How do you use the Vault cluster? guide to learn how to initialize, unseal, and use Vault.
Quick Start
See the root-example for the fastest way to try out this Module.
How do I contribute to this Module?
Contributions are very welcome! Check out the Contribution Guidelines for instructions.
How is this Module versioned?
This Terraform Module follows the principles of Semantic Versioning. You can find each new release, along with the changelog, in the Releases Page.
During initial development, the major version will be 0 (e.g., 0.x.y), which indicates the code does not yet have a
stable API. Once we hit 1.0.0, we will make every effort to maintain a backwards compatible API and use the MAJOR,
MINOR, and PATCH versions on each release to indicate any incompatibilities.
License
This code is released under the Apache 2.0 License. Please see LICENSE and NOTICE for more details.
Copyright © 2017 Gruntwork, Inc.