fkie-cad / Cwe_checker
Labels
Projects that are alternatives of or similar to Cwe checker
cwe_checker
NOTE: We recently changed our default analysis backend from BAP to the newer Ghidra backend. The switch causes some changes in both the command line interface and the docker image interface. Be sure to update your scripts accordingly! Alternatively, the stable version still uses the old interface.
What is cwe_checker?
cwe_checker is a suite of checks to detect common bug classes such as use of dangerous functions and simple integer overflows. These bug classes are formally known as Common Weakness Enumerations (CWEs). Its main goal is to aid analysts to quickly find vulnerable code paths.
Its main focus are ELF binaries that are commonly found on Linux and Unix operating systems. The cwe_checker uses Ghidra to disassemble binaries into one common intermediate representation and implements its own analyses on this IR. Hence, the analyses can be run on all CPU architectures that Ghidra can disassemble, which makes the cwe_checker a valuable tool for firmware analysis.
The following arguments should convince you to give cwe_checker a try:
- it is very easy to set up, just build the Docker container!
- it analyzes ELF binaries of several CPU architectures including x86, ARM, MIPS, and PPC
- it is extensible due to its plugin-based architecture
- it is configureable, e.g. apply analyses to new APIs
- view results annotated in Ghidra
- cwe_checker can be integrated as a plugin into FACT
Installation
Using the docker image
The simplest way is to pull the latest Docker image from dockerhub:
-
docker pull fkiecad/cwe_checker:latestyields an image based on the current master branch. -
docker pull fkiecad/cwe_checker:stableyields an image based on the latest stable release version.
If you want to build the docker image yourself, just run docker build -t cwe_checker .
Local installation
The following dependencies must be installed in order to build and install the cwe_checker locally:
Run make all GHIDRA_PATH=path/to/ghidra_folder (with the correct path to the local Ghidra installation inserted) to compile and install the cwe_checker.
Usage
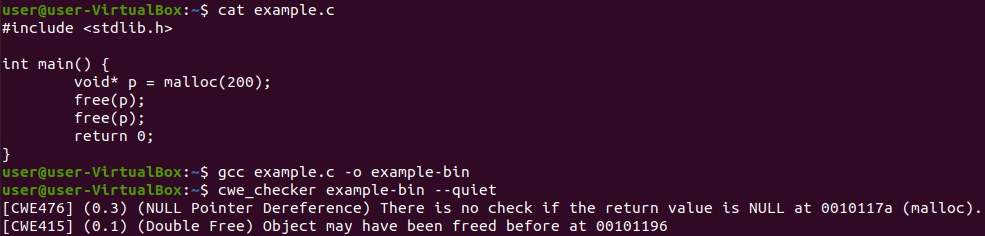
The cwe_checker takes a binary as input, runs several checks based on static analysis on the binary and then outputs a list of CWE warnings that have been found during the analysis.
If you use the official docker image, just run
docker run --rm -v /PATH/TO/BINARY:/input fkiecad/cwe_checker /input
If you installed the cwe_checker locally, run
cwe_checker BINARY
You can adjust the behavior of most checks via a configuration file located at src/config.json.
If you modify it, add the command line flag --config=src/config.json to tell the cwe_checker to use the modified file.
For information about other available command line flags you can pass the --help flag to the cwe_checker.
If you use the stable version, you can also look at the online documentation for more information.
Documentation and Tests
The test binaries for our test suite can be built with make compile_test_files (needs Docker to be installed!). The test suite can then be run with make test.
Source code documentation can be built with make documentation. For the stable version, the documentation can be found here.
Implemented Checks
So far the following analyses are implemented:
- CWE-190: Integer Overflow or Wraparound
- CWE-215: Information Exposure Through Debug Information
- CWE-243: Creation of chroot Jail Without Changing Working Directory
- CWE-332: Insufficient Entropy in PRNG
- CWE-367: Time-of-check Time-of-use (TOCTOU) Race Condition
- CWE-415: Double Free
- CWE-416: Use After Free
- CWE-426: Untrusted Search Path
- CWE-467: Use of sizeof() on a Pointer Type
- CWE-476: NULL Pointer Dereference
- CWE-560: Use of umask() with chmod-style Argument
- CWE-676: Use of Potentially Dangerous Function
- CWE-782: Exposed IOCTL with Insufficient Access Control
Please note that some of the above analyses only are partially implemented at the moment. Furthermore, false positives are to be expected due to shortcuts and the nature of static analysis as well as over-approximation.
Integration into other tools
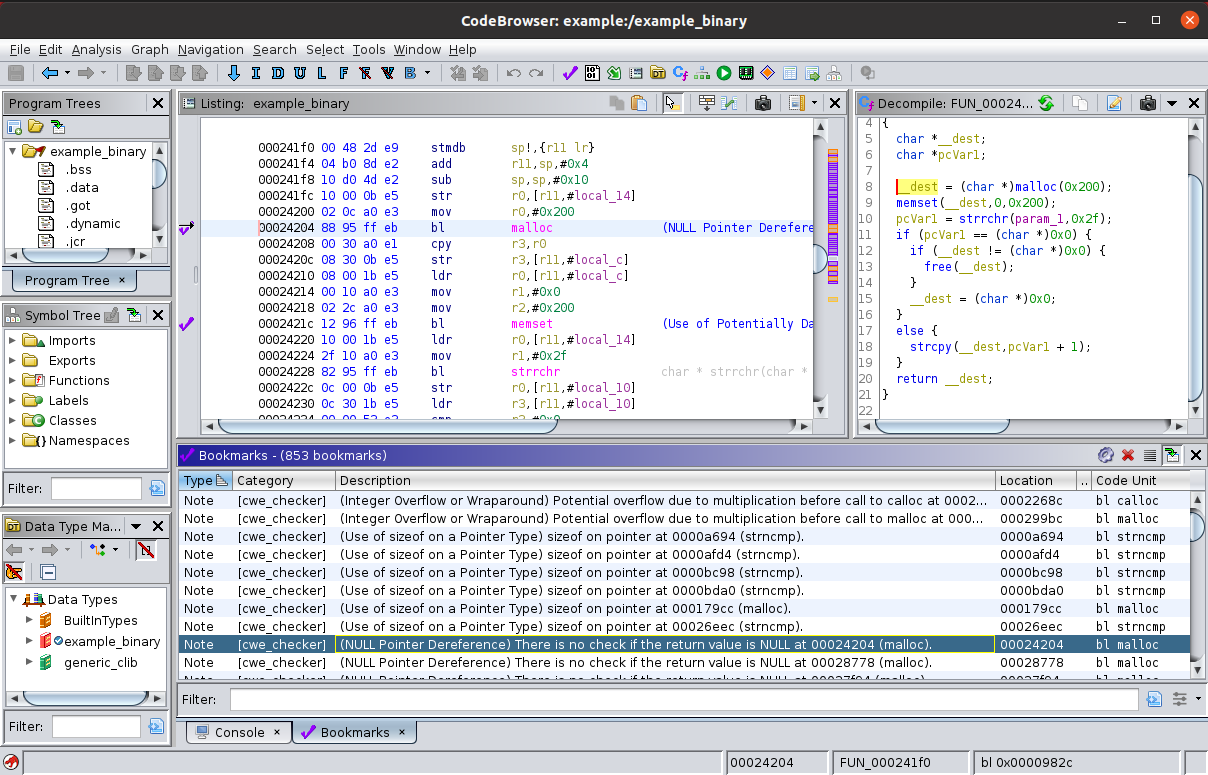
cwe_checker comes with a script for Ghidra,
which parses the output of the cwe_checker and annotates the found CWEs in the disassembler for easier manual analysis.
The script is located at ghidra_plugin/cwe_checker_ghidra_plugin.py, usage instructions are contained in the file.
How does cwe_checker work internally?
Building the documentation using cargo doc --open --document-private-items will give you more information about the internal structure of the cwe_checker.
However, the best documentation is still the source code itself.
If you have questions, be sure to ask them on our discussions page!
We are constantly striving to improve extensibility and documentation and your questions will help us to achieve that!
To get a quick/initial overview of its internals you can also look at the slides of conference presentations on the cwe_checker in the doc folder. We presented cwe_checker at the following conferences so far:
Contribute
Contributions are always welcome. Just fork it and open a pull request!
Acknowledgements
This project is partly financed by German Federal Office for Information Security (BSI).
A special thanks goes out to the BAP community (especially the official gitter) for answering questions and discussing solutions.
License
Copyright (C) 2018 - Fraunhofer FKIE ([email protected])
This library is free software; you can redistribute it and/or
modify it under the terms of the GNU Library General Public
License as published by the Free Software Foundation; either
version 3 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
Library General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.