marco-lancini / Docker_offensive_elk
Programming Languages
Projects that are alternatives of or similar to Docker offensive elk
Offensive ELK: Elasticsearch for Offensive Security
Offensive ELK is a custom Elasticsearch setup, aiming to show how traditional “defensive” tools can be effectively used for offensive security data analysis, helping your team collaborate and triage scan results.
In particular, Elasticsearch offers the chance to aggregate a multitude of disparate data sources, query them with a unified interface, with the aim of extracting actionable knowledge from a huge amount of unclassified data.
A full walkthrough that led me to this setup can be found at: https://www.marcolancini.it/2018/blog-elk-for-nmap/.
Usage
- Clone this repository:
❯ git clone https://github.com/marco-lancini/docker_offensive_elk.git
- Create the
_datafolder (if not present) and ensure it is owned by your own user:
❯ cd docker_offensive_elk/
❯ mkdir ./_data/
❯ sudo chown -R <user>:<user> ./_data/
- Start the stack using docker-compose:
docker-elk ❯ docker-compose up -d
- Give Kibana a few seconds to initialize, then access the Kibana web UI running at: http://localhost:5601.
- Start ingesting your nmap results.
- During the first run, create an index.
Ingest Nmap Results
In order to be able to ingest our Nmap scans, we will have to output the results in an XML formatted report (-oX) that can be parsed by Elasticsearch.
Once done with the scans, place the reports in the ./_data/nmap/ folder and run the ingestor:
❯ docker-compose run ingestor
Starting elk_elasticsearch ... done
Processing /data/scan_192.168.1.0_24.xml file...
Sending Nmap data to Elasticsearch
Processing /data/scan_192.168.2.0_24.xml file...
Sending Nmap data to Elasticsearch
Processing /data/scan_192.168.3.0_24.xml file...
Sending Nmap data to Elasticsearch
Create an Index
-
Open Kibana in your browser (http://localhost:5601) and you should be presented with a screen similar to the one below:
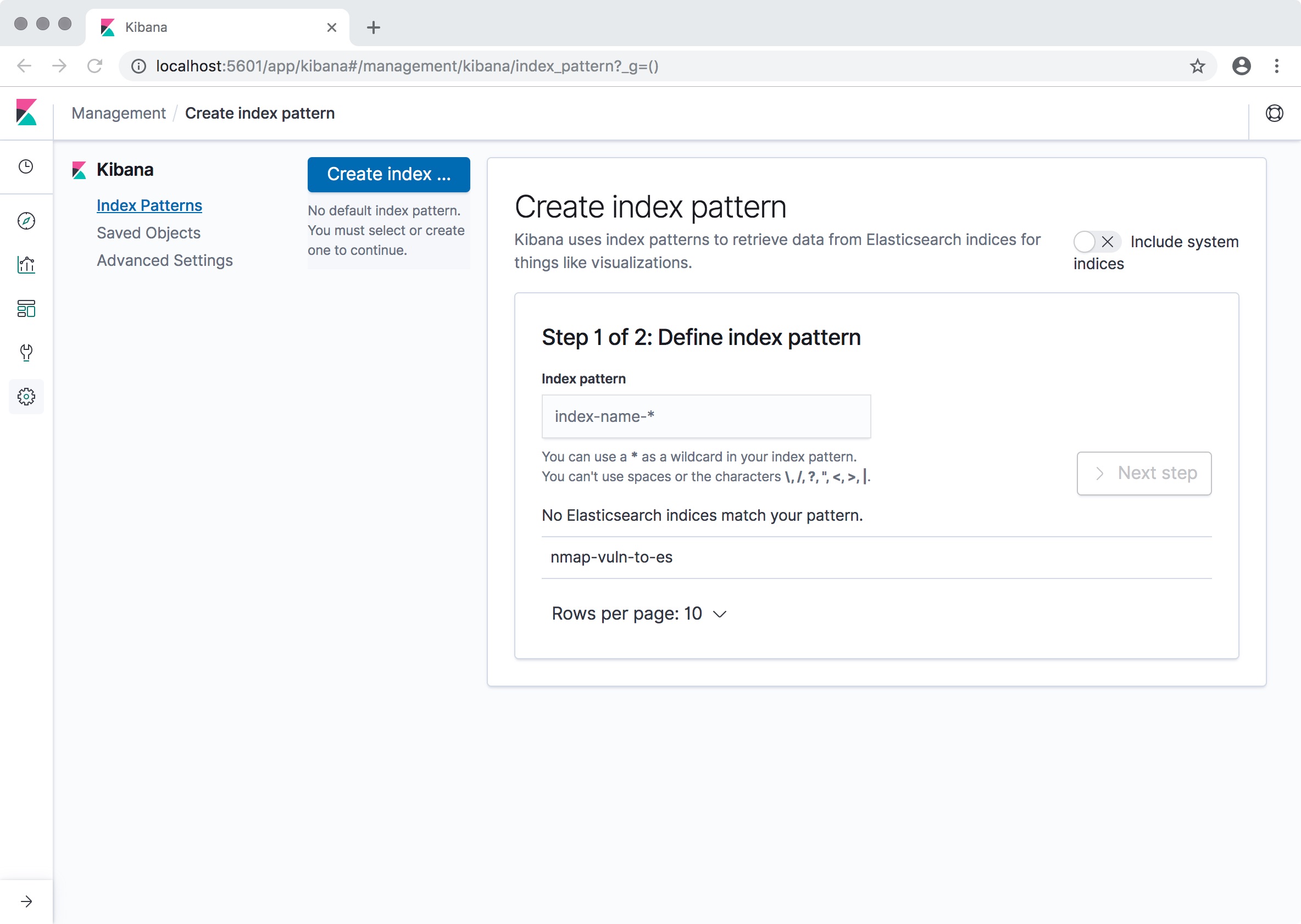
-
In the "Time Filter" field name choose "
time", then click on "Create Index Pattern":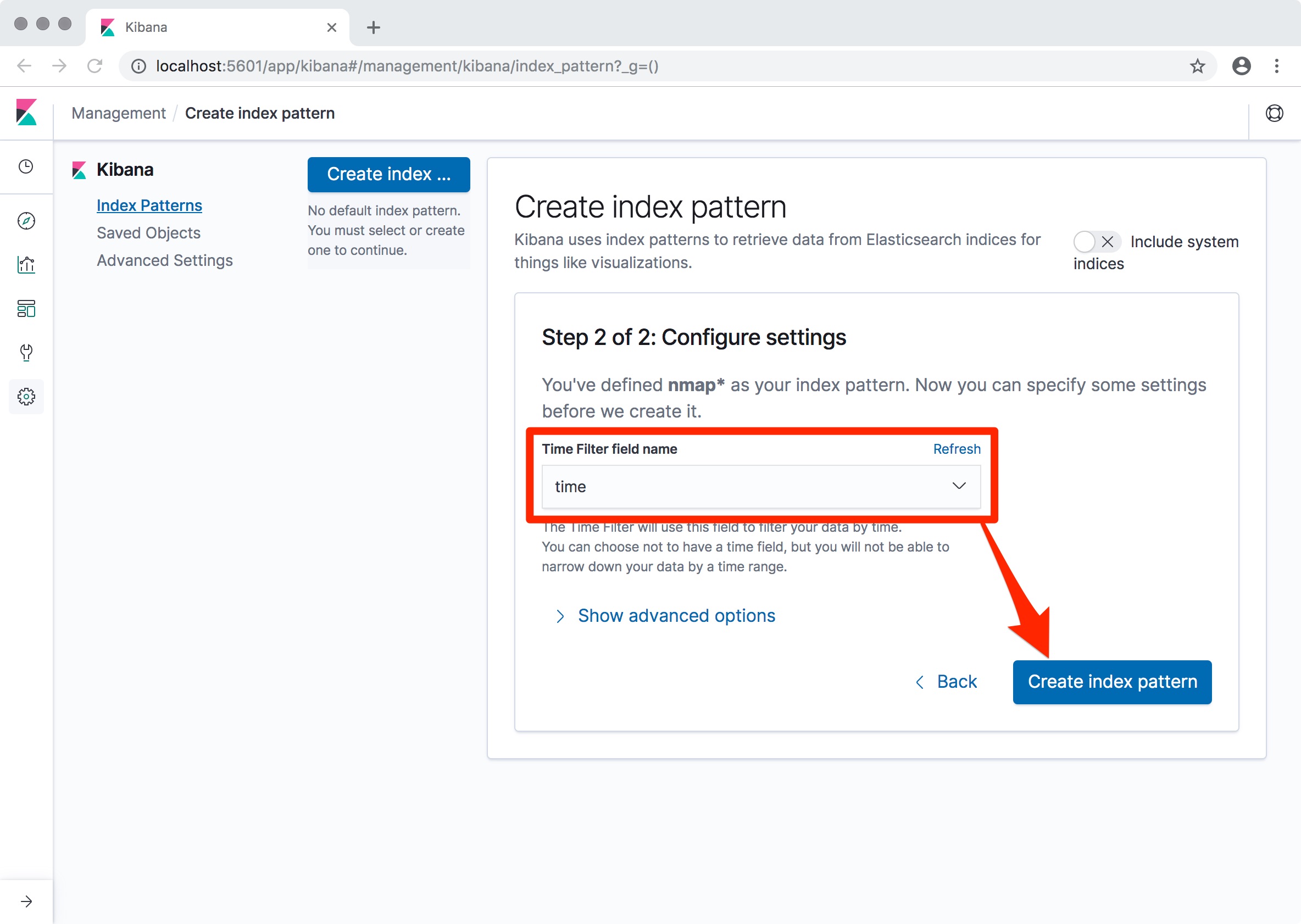
-
If everything goes well you should be presented with a page that lists every field in the
nmap*index and the field's associated core type as recorded by Elasticsearch.