ajinabraham / Droid Application Fuzz Framework
Projects that are alternatives of or similar to Droid Application Fuzz Framework
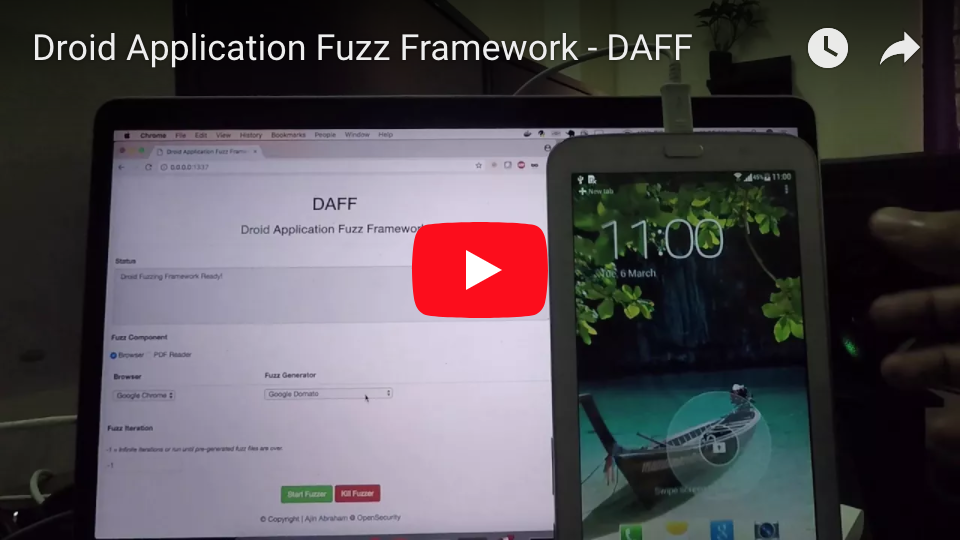
Droid Application Fuzz Framework
Droid Application Fuzz Framework (DAFF) helps you to fuzz Android Browsers and PDF Readers for memory corruption bugs in real android devices. You can use the inbuilt fuzzers or import fuzz files from your own custom fuzzers. DAFF consist of inbuilt fuzzers and crash monitor. It currently supports fuzzing the following applications:
Browsers
- Google Chrome - com.android.chrome
- Mozilla Firefox - org.mozilla.firefox
- Opera - com.opera.browser
- UC Browser - com.UCMobile.intl
PDF Viewers/Readers
- Adobe Acrobat Reader - com.adobe.reader
- Foxit PDF Reader - com.foxit.mobile.pdf.lite
- Google PDF Viewer - com.google.android.apps.pdfviewer
- WPS Office + PDF - cn.wps.moffice_eng
- Polaris Office - com.infraware.office.link (WIP)
Fuzz Generators
DAFF has three fuzzer modes:
- Google Domato - Uses slightly modified version of Google Domato for generating fuzz files.
- Dumb Fuzzer - As the the name suggests, a dumb fuzzer. (Only for PDF)
-
Pregenerated Files (3rd Party Fuzzer) - To use your private or custom fuzzer generated files. Place html samples in
generators/html/htmlsand pdf samples ingenerators/pdf/pdfs
Usage for Dummies
Android Device
- Install the supported Browsers and PDF readers in Android Device.
- Enable USB Debugging in the Android Device.
- Connect the Android Device to the same WiFi Network where the Computer is connected.
- Connect the Android Device to Computer using USB cable and Always allow the Computer for USB Debuging.
Computer
- Install Python 2.7
git clone https://github.com/ajinabraham/Droid-Application-Fuzz-Framework.gitpip install -r requirements.txt- In
settings.pyset theDEVICE_IDas the Android Device ID. You can find this withadb devicescommand. - Also set
FUZZ_IPas the local IP of the computer. Useifconfig/ipconfigcommand. - Set the path to adb binary in
ADB_BINARYifadbis not in yourPATH. - Run the Web GUI
python daff_server.py - Access the Fuzzer Web Interface at
http://0.0.0.0:1337 - Select the Application, Select the Fuzz Generator and Start Fuzzing!
DAFF in Action
Extra Tip
After installing the apps in Android Device, use them at least once. Allow popups, configure first time screens etc.
Please Note
I am just open sourcing a private project for the benefit of community. I don't have time to actively maintain this project. If you have found bugs, fix them and send pull requests. That's how open source should work! I have done my best to make the documentation clear and simple for all types of users. Please check Google or Stack Overflow if you are stuck.