anouarbensaad / Vulnx
Programming Languages
Labels
Projects that are alternatives of or similar to Vulnx

VulnX
Vulnx 🕷️ is An Intelligent Bot Auto Shell Injector that detects vulnerabilities in multiple types of Cms
https://github.com/anouarbensaad/vulnx/archive/master.zip
VulnX Wiki • How To Use • Compatibility • Library •
Vulnx is An Intelligent Bot Auto Shell Injector that detects vulnerabilities in multiple types of Cms, fast cms detection,informations gathering and vulnerabilitie Scanning of the target like subdomains, ipaddresses, country, org, timezone, region, ans and more ...
Instead of injecting each and every shell manually like all the other tools do, VulnX analyses the target website checking the presence of a vulnerabilitie if so the shell will be Injected.searching urls with dorks Tool.
🕷️ Features
- Detects cms (wordpress, joomla, prestashop, drupal, opencart, magento, lokomedia)
- Target informations gatherings
- Target Subdomains gathering
- Multi-threading on demand
- Checks for vulnerabilities
- Auto shell injector
- Exploit dork searcher
-
Ports ScanHigh Level -
Dns-Servers Dump - Input multiple target to scan.
- Dorks Listing by Name& by ExploitName.
- Export multiple target from Dorks into a logfile.
🕷️ DNS-Map-Results
To do this,run a scan with the --dns flag and -d for subdomains.
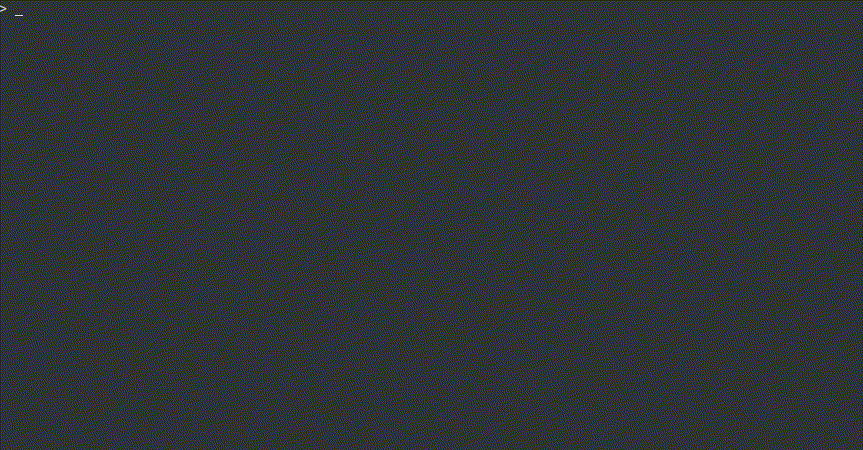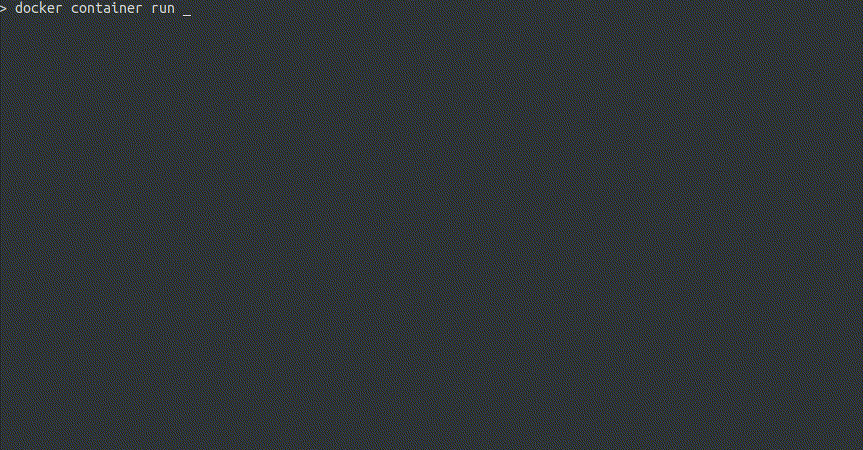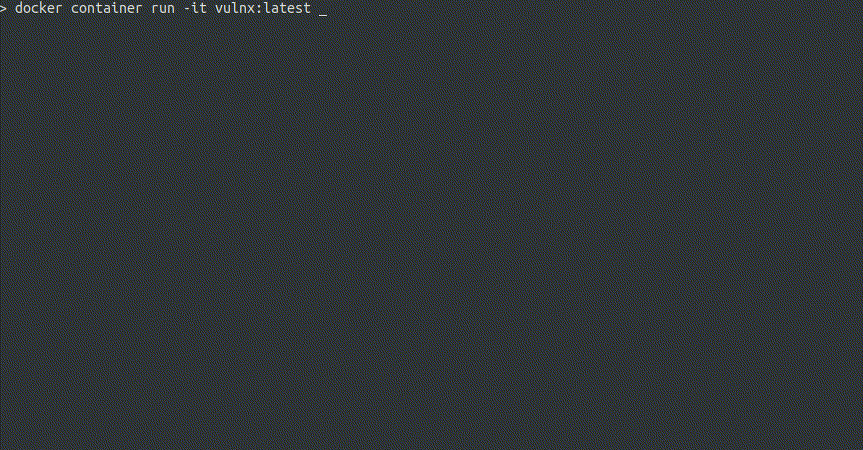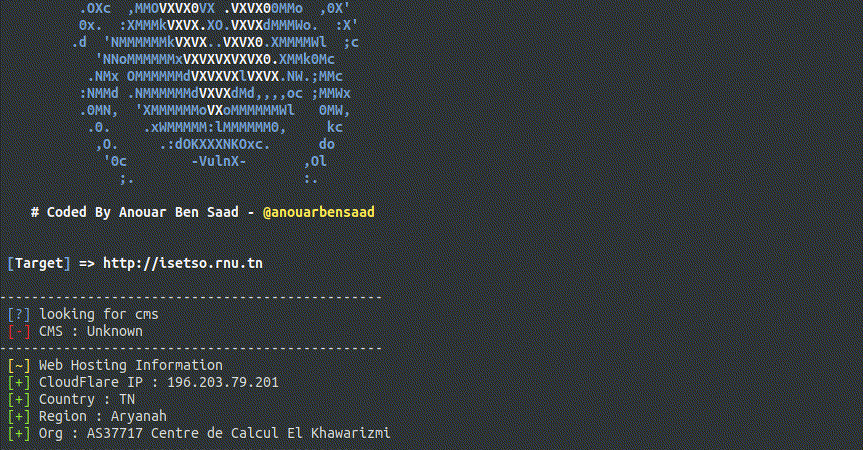
To generate a map of isetso.rnu.tn, you can run the command
vulnx -u isetso.rnu.tn --dns -d --output $PATHin a new terminal.
$PATH : Where the graphs results will be stored.
Let's generates an image displaying target Subdomains,MX & DNS data.
🕷️ Exploits
Joomla
- [x] Com Jce
- [x] Com Jwallpapers
- [x] Com Jdownloads
- [x] Com Jdownloads2
- [x] Com Weblinks
- [x] Com Fabrik
- [x] Com Fabrik2
- [x] Com Jdownloads Index
- [x] Com Foxcontact
- [x] Com Blog
- [x] Com Users
- [x] Com Ads Manager
- [x] Com Sexycontactform
- [x] Com Media
- [x] Mod_simplefileupload
- [x] Com Facileforms
- [x] Com Facileforms
- [x] Com extplorer
Wordpress
- [x] Simple Ads Manager
- [x] InBoundio Marketing
- [x] WPshop eCommerce
- [x] Synoptic
- [x] Showbiz Pro
- [x] Job Manager
- [x] Formcraft
- [x] PowerZoom
- [x] Download Manager
- [x] CherryFramework
- [x] Catpro
- [x] Blaze SlideShow
- [x] Wysija-Newsletters
Drupal
- [ ] Add Admin
- [ ] Drupal BruteForcer
- [ ] Drupal Geddon2
PrestaShop
- [x] attributewizardpro
- [x] columnadverts
- [ ] soopamobile
- [x] pk_flexmenu
- [x] pk_vertflexmenu
- [x] nvn_export_orders
- [x] megamenu
- [x] tdpsthemeoptionpanel
- [ ] psmodthemeoptionpanel
- [x] masseditproduct
- [ ] blocktestimonial
- [x] soopabanners
- [x] Vtermslideshow
- [x] simpleslideshow
- [x] productpageadverts
- [x] homepageadvertise
- [ ] homepageadvertise2
- [x] jro_homepageadvertise
- [x] advancedslider
- [x] cartabandonmentpro
- [x] cartabandonmentproOld
- [x] videostab
- [x] wg24themeadministration
- [x] fieldvmegamenu
- [x] wdoptionpanel
Opencart
🕷️ VulnxMode
NEW
vulnx now have an interactive mode.
URLSET
DORKSET
🕷️ Available command line options
usage: vulnx [options]
-u --url url target
-D --dorks search webs with dorks
-o --output specify output directory
-t --timeout http requests timeout
-c --cms-info search cms info[themes,plugins,user,version..]
-e --exploit searching vulnerability & run exploits
-w --web-info web informations gathering
-d --domain-info subdomains informations gathering
-l, --dork-list list names of dorks exploits
-n, --number-page number page of search engine(Google)
-p, --ports ports to scan
-i, --input specify domains to scan from an input file
--threads number of threads
--dns dns informations gathering
🕷️ Docker
VulnX in DOCKER !!.
$ git clone https://github.com/anouarbensaad/VulnX.git
$ cd VulnX
$ docker build -t vulnx ./docker/
$ docker run -it --name vulnx vulnx:latest -u http://example.com
run vulnx container in interactive mode
to view logfiles mount it in a volume like so:
$ docker run -it --name vulnx -v "$PWD/logs:/VulnX/logs" vulnx:latest -u http://example.com
change the mounting directory..
VOLUME [ "$PATH" ]
🕷️ Install vulnx on Ubuntu
$ git clone https://github.com/anouarbensaad/vulnx.git
$ cd VulnX
$ chmod +x install.sh
$ ./install.sh
Now run vulnx
🕷️ Install vulnx on Termux
$ pkg update
$ pkg install -y git
$ git clone http://github.com/anouarbensaad/vulnx
$ cd vulnx
$ chmod +x install.sh
$ ./install.sh
🕷️ Install vulnx in Windows
- click here to download vulnx
- download and install python3
- unzip vulnx-master.zip in c:/
- open the command prompt cmd.
> cd c:/vulnx-master
> python vulnx.py
example command with options : settimeout=3 , cms-gathering = all , -d subdomains-gathering , run --exploits
vulnx -u http://example.com --timeout 3 -c all -d -w --exploit
example command for searching dorks : -D or --dorks , -l --list-dorks
vulnx --list-dorks
return table of exploits name.
vulnx -D blaze
return urls found with blaze dork
🕷️ Versions
⚠️ Warning!
I Am Not Responsible of any Illegal Use
🕷️ Contribution & License
You can contribute in following ways:
- Report bugs & add issues
- Search for new vulnerability
- Develop plugins
- Searching Exploits
- Give suggestions (Ideas) to make it better
Do you want to have a conversation in private? email me : [email protected]
VulnX is licensed under GPL-3.0 License