maiyao1988 / Elf Dump Fix
Utils use to dump android ELF from memory and do some fix including the ELF section header rebuilding
Stars: ✭ 166
Programming Languages
c
50402 projects - #5 most used programming language
Projects that are alternatives of or similar to Elf Dump Fix
Detect It Easy
Program for determining types of files for Windows, Linux and MacOS.
Stars: ✭ 2,982 (+1696.39%)
Mutual labels: elf, reverse-engineering
Vmlinux To Elf
A tool to recover a fully analyzable .ELF from a raw kernel, through extracting the kernel symbol table (kallsyms)
Stars: ✭ 317 (+90.96%)
Mutual labels: elf, reverse-engineering
Dji Firmware Tools
Tools for handling firmwares of DJI products, with focus on quadcopters.
Stars: ✭ 424 (+155.42%)
Mutual labels: elf, reverse-engineering
E9patch
A powerful static binary rewriting tool
Stars: ✭ 317 (+90.96%)
Mutual labels: elf, reverse-engineering
Xelfviewer
ELF file viewer/editor for Windows, Linux and MacOS.
Stars: ✭ 279 (+68.07%)
Mutual labels: elf, reverse-engineering
Goblin
An impish, cross-platform binary parsing crate, written in Rust
Stars: ✭ 591 (+256.02%)
Mutual labels: elf, reverse-engineering
Dithumb
Minimal ARM/Thumb linear sweep disassembler similar to objdump
Stars: ✭ 5 (-96.99%)
Mutual labels: elf, reverse-engineering
Jupiter
A Windows virtual memory editing library with support for pattern scanning.
Stars: ✭ 156 (-6.02%)
Mutual labels: reverse-engineering
Rbasefind
A firmware base address search tool.
Stars: ✭ 159 (-4.22%)
Mutual labels: reverse-engineering
Z3 and angr binary analysis workshop
Code and exercises for a workshop on z3 and angr
Stars: ✭ 154 (-7.23%)
Mutual labels: reverse-engineering
Edb Debugger
edb is a cross-platform AArch32/x86/x86-64 debugger.
Stars: ✭ 2,019 (+1116.27%)
Mutual labels: reverse-engineering
Pikachu Volleyball P2p Online
Pikachu Volleyball peer-to-peer online via WebRTC data channels
Stars: ✭ 160 (-3.61%)
Mutual labels: reverse-engineering
Gymnasticon
Make obsolete and/or proprietary exercise bikes work with popular cycling training apps like Zwift, TrainerRoad, Rouvy and more.
Stars: ✭ 155 (-6.63%)
Mutual labels: reverse-engineering
Apkleaks
Scanning APK file for URIs, endpoints & secrets.
Stars: ✭ 2,707 (+1530.72%)
Mutual labels: reverse-engineering
Mixplaintext
可对 Xcode 项目工程所有的 objective-c 文件内包含的明文进行加密混淆,提高逆向分析难度。
Stars: ✭ 152 (-8.43%)
Mutual labels: reverse-engineering
Android Lkms
Android Loadable Kernel Modules - mostly used for reversing and debugging on controlled systems/emulators
Stars: ✭ 164 (-1.2%)
Mutual labels: reverse-engineering
Anno1800 Mod Loader
The one and only mod loader for Anno 1800, supports loading of unpacked RDA files, XML merging and Python mods.
Stars: ✭ 161 (-3.01%)
Mutual labels: reverse-engineering
elf-dump-fix
This resp include two utils about dumping and fixing arm elf32/elf64 from the memory.
- dump
- Run on android, can dump ELF from a process memory and fix it, Rebuild the Section Header for better IDA analysis.
- sofix
- Run on PC, can fix an ELF file dumped from memory and rebuild the Section Header for better IDA analysis.
The main target is to rebuild the Section Header of an ELF by memory dumped.Useful in breaking packed so file like UPX or something like 360 libjiagu.so
Build
-
dump
-
cd app/jni/ ndk-build - output path is app/libs/armeabi-v7a/dump
-
-
sofix
- on linux/mac, make sure clang/gcc is installed, just run ./build-fix.sh
- on windows, It can be built in mingw , but not tested.
HowToUse
- sofix
- params <src_so_path> <base_addr_in_memory_in_hex> <out_so_path>
- <src_so_path> the elf file dumped from memory.(you can use dd or IDA debugger dumping an ELF file from android process)
- <base_addr_in_memory_in_hex> the memory base for the elf file dumped from memory, if you don't know, pass 0 is ok
- <out_so_path> the output file
- example
- ./sofix dumped.so 0x6f5a4000 b.so
- params <src_so_path> <base_addr_in_memory_in_hex> <out_so_path>
- dump
- This is run on Android Phone
- make sure your phone have root access.
- push it onto /data/local/tmp and grant +x like this
- adb push app/libs/armeabi-v7a/dump /data/local/tmp/ && adb shell chmod 777 /data/local/tmp/dump
- use adb shell to enter your phone and switch to root user by su command.
- params <base_hex> <end_hex> [is-stop-process-before-dump] [is-fix-so-after-dump]
- the process id you want to dump
- <base_hex> the start address of ELF you want to dump in process memory, you can get this by
cat /proc/<pid>/maps - <end_hex> the end address of ELF you want to dump in process memory, you can get this by
cat /proc/<pid>/maps - the fixed ELF output path in your phone.
- [is-stop-process-before-dump] 0/1 should send sigal to the process before doing dump job, useful in some anti dumping app. if there is no anti dumping on your target process, 0 is ok
- [is-fix-so-after-dump] 0/1 should do the fix job and Section Header rebuilding, if you pass on, it will try to fix the ELF after dump.
- example
- if you want to dump libc.so, and your /proc/[pid]/maps like this
-
40105000-4014c000 r-xp 00000000 b3:19 717 /system/lib/libc.so 4014c000-4014d000 ---p 00000000 00:00 0 4014d000-4014f000 r--p 00047000 b3:19 717 /system/lib/libc.so 4014f000-40152000 rw-p 00049000 b3:19 717 /system/lib/libc.so 40152000-40160000 rw-p 00000000 00:00 0 - ./dump 1148 0x40105000 0x40160000 ./out.so 0 1
- dump to 40160000 not 40152000 is because the ELF .bss memory if exist should be dump too, the fix process depends on it.
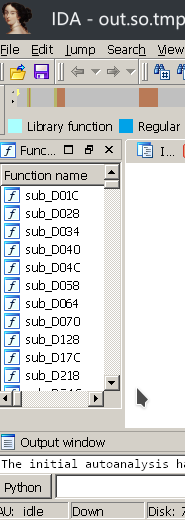
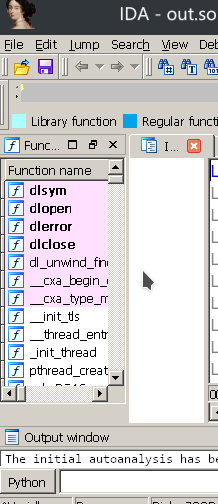
Compare between no-fix and fixed ELF
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].