GoogleCloudPlatform / Gke Istio Vpn Demo
Programming Languages
Projects that are alternatives of or similar to Gke Istio Vpn Demo
Istio on Kubernetes Engine and Compute Engine
Table of Contents
- Introduction
- Architecture
- Prerequisites
- Creating a project
- Deployment
- Validation
- Tear Down
- Troubleshooting
- Relevant Material
Introduction
Istio is part of a new category of products known as "service mesh" software designed to manage the complexity of service resilience in a microservice infrastructure. It defines itself as a service management framework built to keep business logic separate from the logic to keep your services up and running. In other words, it provides a layer on top of the network that will automatically route traffic to the appropriate services, handle circuit breaker logic, enforce access and load balancing policies, and generate telemetry data to gain insight into the network and allow for quick diagnosis of issues.
Istio makes it easy to create a network of deployed services with load balancing, service-to-service authentication and monitoring without any changes in service code.
Core features of Istio include:
- Traffic management - Istio simplifies configuration of service-level properties like circuit breakers, timeouts, and retries making the network more robust.
- Security - Istio, using with Kubernetes (or infrastructure) network policies, provides the ability to secure pod-to-pod or service-to-service communication at the network and application layers.
- Platform support - Istio is platform-independent and currently supports service deployment on Kubernetes, services registered with Consul and services running on individual virtual machines.
- Integration and customization - Istio, has a policy enforcement component which can be extended and customized to integrate with existing solutions for ACLs, logging, monitoring, quotas and auditing.
For more information on Istio, please refer to the Istio documentation.
Istio on GKE
When you create or update the cluster with Istio on GKE, following components are installed:
- Pilot, which is responsible for service discovery and for configuring the Envoy sidecar proxies in an Istio service mesh.
- Istio-Policy and Istio-Telemetry, which enforce usage policies and gather telemetry data.
- The Istio Ingress gateway, which provides an ingress point for traffic from outside the cluster.
- The Istio Egress gateway, which allow Istio features like monitoring and routing rules to be applied to traffic exiting the mesh.
- Citadel, which automates key and certificate management for Istio.
- Galley, which provides configuration management services for Istio.
For more information on how to install Istio, please refer to the Installing Istio on GKE.
This repository contains demonstration code for Istio's mesh expansion feature between resources in two Google Cloud Platform (GCP) projects connected via VPN. The feature allows for a non-Kubernetes service running outside of the Istio infrastructure on Kubernetes Engine to be integrated into and managed by the Istio service mesh.
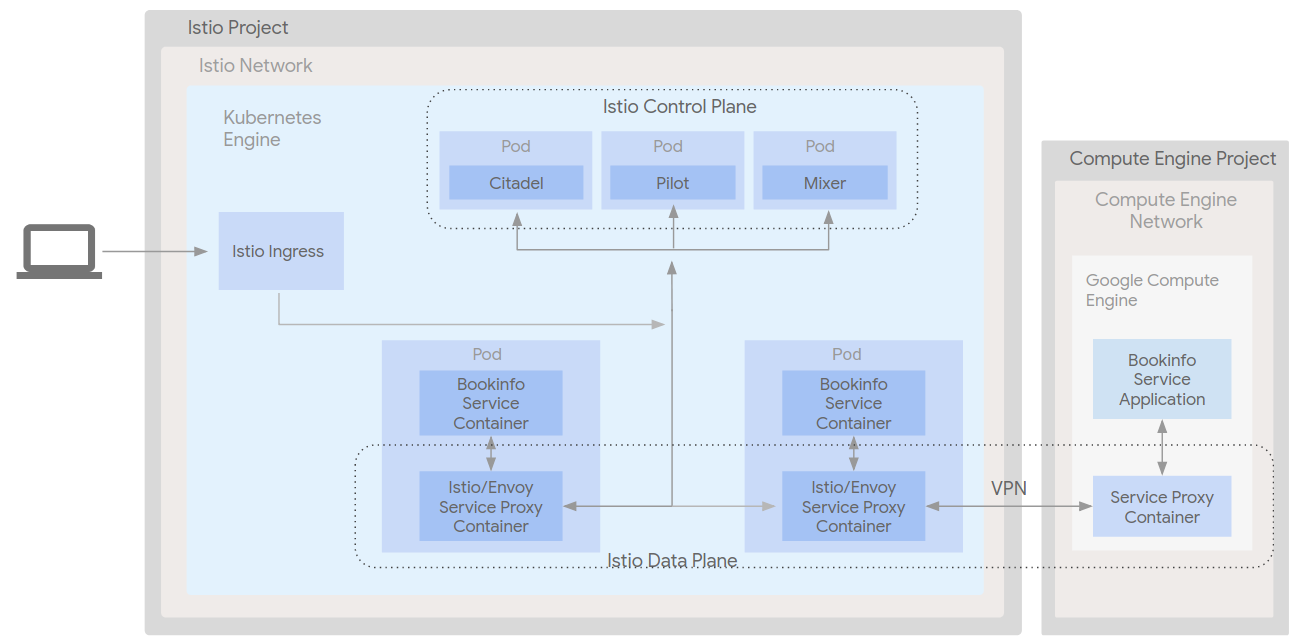
Architecture
This demonstration will create a number of resources.
- A single (GKE) cluster with IP aliasing turned on in a custom network in project A
- A Google Compute Engine (GCE) instance in a custom network project B
- A VPN bridging the two networks containing the GKE cluster and the GCE instance
- The Istio service mesh installed in the GKE cluster
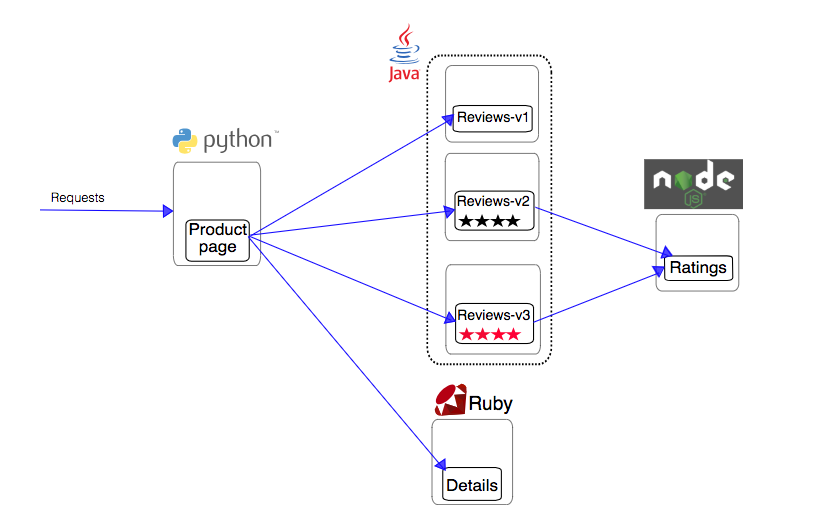
- The BookInfo application installed in the Istio service mesh
- A firewall rule allowing full SSH access to the GCE instance from any IP address
- A firewall rule allowing full access to the MySQL database from the GKE cluster
Application architecture
Infrastructure architecture
Prerequisites
Run Demo in a Google Cloud Shell
Click the button below to run the demo in a Google Cloud Shell.
Use the --recursive argument to download dependencies provided via a git submodule.
git submodule update --init --recursive
All the tools for the demo are installed. When using Cloud Shell execute the following command in order to setup gcloud cli. When executing this command please setup your region and zone.
gcloud init
Tools
In order to use the code in this demo you will need to have have access to a bash-compatible shell with the following tools installed:
- Terraform >= 0.12.3
- Google Cloud SDK version >= 253.0.0
- kubectl matching the latest GKE version
- Two GCP projects with billing enabled
Install Cloud SDK
The Google Cloud SDK is used to interact with your GCP resources. Installation instructions for multiple platforms are available online.
Install kubectl CLI
The kubectl CLI is used to interteract with both Kubernetes Engine and kubernetes in general. Installation instructions for multiple platforms are available online.
Install Terraform
Terraform is used to automate the manipulation of cloud infrastructure. Its installation instructions are also available online.
Creating a project
In order to complete this demo, two projects need to exist, one for the GKE cluster and a second for the GCE instance, which will be connected via a VPN.
To create projects:
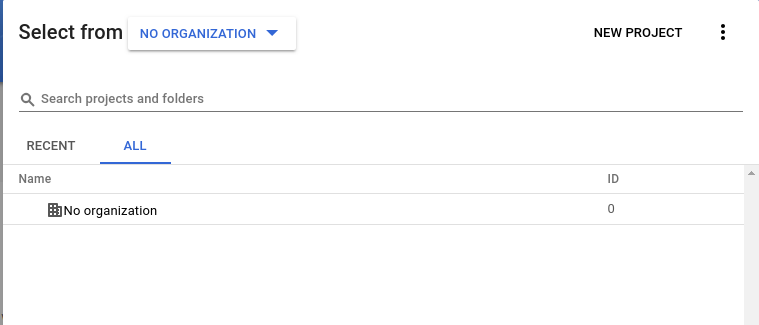
- Log in to the GCP Console
- Click on
Select a projectin the top navigating bar - Click on
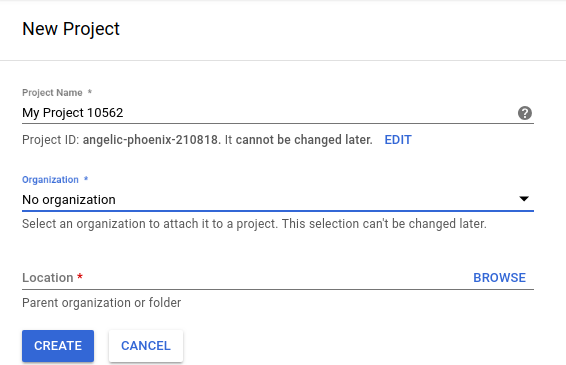
New Projectin on the top right of the window:
- Enter a project name, and note the project id below it.
(in this case, the project id is
angelic-phoenix-210818):
- Enable billing by clicking on the three lines in the top left corner select
Billingand enable it:
If necessary, repeat for a second project.
Deployment
Use git to clone this project to your local machine:
git clone --recursive https://github.com/GoogleCloudPlatform/gke-istio-vpn-demo
Note that the --recursive argument is required to download dependencies provided via a git submodule.
When downloading is complete, change your current working directory to the new project:
cd gke-istio-vpn-demo
Continue with the instructions below, running all commands from this directory.
Open the scripts/istio.env file and set:
-
ISTIO_PROJECTto the ID of the project you want to use for Istio infrastructure -
GCE_PROJECTto the ID of the project you want to use for GCE - Any variables you wish to customize
Note that the ID of the project is not always the same as the name. Also, please note that when setting ISTIO_PROJECT and GCE_PROJECT they should be uncommented. Failure to do so will result in an error in the following step.
Once configuration is complete the demo cluster and app can be deployed.:
make create
This make target calls the scripts/create.sh script which will use Terraform to automatically build out necessary infrastructure, including a Kubernetes cluster, and will then use kubectl to deploy application components and other resource to the cluster.
Noteworthy Aspects of the Deployment:
- The GKE cluster uses IP aliasing, without this feature, the demo would not work. IP Aliasing is a feature by which services and pods can have their IP addresses set to values within a specific CIDR block, which allows them to be known in advance of a deployment, and callable by other resources. This also ensures that the IP addresses will not conflict with other GCP resources and provides an additional mechanism for firewall traffic control (e.g. rules on the pod may differ from those on the underlying host).
For more information on IP Aliasing see: https://cloud.google.com/kubernetes-engine/docs/how-to/alias-ips
-
The GKE cluster's IP CIDR blocks are defined in the
istio.envfile and can be changed in the event that other values are needed (e.g. if they conflict with other IP address space). -
Firewall and Routing rules are created at deployment time to facilitate the necessary communication without exposing ports and services unnecessarily.
-
The VPN configuration (endpoints, firewalls and routing rules) are defined in the included terraform configuration,
terraform/main.tf. For more information on VPNs see: https://cloud.google.com/vpn/docs/how-to
Validation
To validate that everything is working correctly, first open your browser to the URL provided at the end of the installation script. You'll see a URL for the BookInfo web site. After taking a look, run:
make validate
This will change the rating between 1 and 5 stars for Reviewer1.
Refresh the page in your browser; the first rating should reflect the number of stars passed to the validate script. Behind the scenes, the validate script is directly editing the database on the GCE VM that was integrated into the mesh, proving that the BookInfo application is using the database on the VM as the source of the rating data.
Tear Down
To shutdown the demo run:
make teardown
This will destroy all the resources created by Terraform including everything deployed to the Kubernetes cluster.
Troubleshooting
Problem: Functions in gke-istio-shared are not available: gke-istio-shared/verify-functions.sh
Solution: If you are running this manually, you may be missing your git submodule. To fix this, run:
git submodule update --init
Problem: The Book Reviews section is returning an error stating that the ratings service is not available.
Solution: Istio may still be configuring the mesh. Wait for a minute so while refreshing the page.
Problem: The install script fails with a Permission denied when running Terraform.
Solution: The credentials that Terraform is using do not provide the necessary permissions to create resources in the selected projects. Ensure that the account listed in gcloud config list has necessary permissions to create resources. If it does, regenerate the application default credentials using gcloud auth application-default login.
Problem: Loss of GKE cluster network connectivity after 24 hours
Solution: Remove the GCE instance and rerun all steps involving the GCE setup
Problem: The install script times out while waiting for the internal load balancers to finish provisioning.
Solution: Likely the cause is a transient platform issue. Rerun the script as it is idempotent up to this point and should not run into any issues with infrastructure that already exists.
Problem: The install script gives an error like:
ERROR: (gcloud.services.enable) User [{your-email address}] does not have permission to access service compute.googleapis.com:enable] (or it may not exist): Project '{your-project-name}' not found or permission denied.
Solution: Enter the project Id and not the project name into scripts/istio.env
Relevant Material
- https://github.com/istio/community
- https://istio.io/docs/guides/bookinfo.html
- https://cloud.google.com/kubernetes-engine/docs/tutorials/istio-on-gke
- https://cloud.google.com/compute/docs/tutorials/istio-on-compute-engine
- https://istio.io/docs/setup/kubernetes/mesh-expansion.html
- https://istio.io/docs/guides/integrating-vms.html
This is not an officially supported Google product