liuyx / Inline Hook
Licence: other
simple inline-hook framework works for x86, x64, arm and thumb
Stars: ✭ 102
Projects that are alternatives of or similar to Inline Hook
Pwnshop
Exploit Development, Reverse Engineering & Cryptography
Stars: ✭ 167 (+63.73%)
Mutual labels: arm, x86, x64
opcodesDB
x86-64 | ARM (AArch32/AArch64/THUMB) full instruction set.
Stars: ✭ 49 (-51.96%)
Mutual labels: arm, x64, x86
Capstone.NET
.NET Core and .NET Framework binding for the Capstone Disassembly Framework
Stars: ✭ 108 (+5.88%)
Mutual labels: arm, x64, x86
Reverse-Engineering
A FREE comprehensive reverse engineering tutorial covering x86, x64, 32-bit ARM & 64-bit ARM architectures.
Stars: ✭ 7,234 (+6992.16%)
Mutual labels: arm, x64, x86
fdtd3d
fdtd3d is an open source 1D, 2D, 3D FDTD electromagnetics solver with MPI, OpenMP and CUDA support for x86, arm, arm64 architectures
Stars: ✭ 77 (-24.51%)
Mutual labels: arm, x64, x86
Reverse Engineering Tutorial
A FREE comprehensive reverse engineering tutorial covering x86, x64, 32-bit ARM & 64-bit ARM architectures.
Stars: ✭ 5,763 (+5550%)
Mutual labels: arm, x86, x64
Box86
Box86 - Linux Userspace x86 Emulator with a twist, targeted at ARM Linux devices
Stars: ✭ 1,219 (+1095.1%)
Mutual labels: arm, x86
Bddisasm
bddisasm is a fast, lightweight, x86/x64 instruction decoder. The project also features a fast, basic, x86/x64 instruction emulator, designed specifically to detect shellcode-like behavior.
Stars: ✭ 540 (+429.41%)
Mutual labels: x86, x64
Arm now
arm_now is a qemu powered tool that allows instant setup of virtual machines on arm cpu, mips, powerpc, nios2, x86 and more, for reverse, exploit, fuzzing and programming purpose.
Stars: ✭ 719 (+604.9%)
Mutual labels: arm, x86
Fasmg Ebc
An EFI Byte Code (EBC) assembler, based on fasmg
Stars: ✭ 17 (-83.33%)
Mutual labels: arm, x64
Unicorn
Unicorn CPU emulator framework (ARM, AArch64, M68K, Mips, Sparc, PowerPC, RiscV, X86)
Stars: ✭ 4,934 (+4737.25%)
Mutual labels: arm, x86
Rappel
A linux-based assembly REPL for x86, amd64, armv7, and armv8
Stars: ✭ 818 (+701.96%)
Mutual labels: x86, x64
Barf Project
BARF : A multiplatform open source Binary Analysis and Reverse engineering Framework
Stars: ✭ 1,280 (+1154.9%)
Mutual labels: arm, x86
Capstone
Capstone disassembly/disassembler framework: Core (Arm, Arm64, BPF, EVM, M68K, M680X, MOS65xx, Mips, PPC, RISCV, Sparc, SystemZ, TMS320C64x, Web Assembly, X86, X86_64, XCore) + bindings.
Stars: ✭ 5,374 (+5168.63%)
Mutual labels: arm, x86
Renode
Renode - Antmicro's virtual development framework for complex embedded systems
Stars: ✭ 525 (+414.71%)
Mutual labels: arm, x86
Steed
[INACTIVE] Rust's standard library, free of C dependencies, for Linux systems
Stars: ✭ 520 (+409.8%)
Mutual labels: arm, x86
Keypatch
Multi-architecture assembler for IDA Pro. Powered by Keystone Engine.
Stars: ✭ 939 (+820.59%)
Mutual labels: arm, x86
It's a simple inline-hook framework works for intel(32bit,64bit) and arm(only works for arm32 and thumb) just now, and it's based on new c++11 feature.
How to build:
the framework based on cmake 2.8, all you have to do is:
cmake .
make
How to use:
The usage of the this framework is very easy,example(main.cpp) shows below:
#include "../hooker/HookerFactory.h"
#include <iostream>
#include <cstring>
#include <future>
#include <cstdio>
#include <random>
#include <memory>
void print(const char *s) {
std::cout << s << std::endl;
}
int (*old_strcmp)(const char *, const char *);
int my_strcmp(const char *s1, const char *s2) {
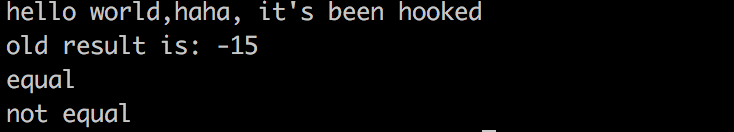
std::cout << s1 << " " << s2 << ",haha, it's been hooked" << std::endl;
if (old_strcmp) {
std::cout << "old result is: " << old_strcmp(s1, s2) << std::endl;
}
return 0;
}
int main() {
const char *s1 = "hello";
const char *s2 = "world";
using namespace hooker;
std::unique_ptr<HookerFactory> factory = HookerFactory::getInstance();
const Hooker& hooker = factory->getHooker();
hooker.hook(reinterpret_cast<void*>(strcmp), reinterpret_cast<void*>(my_strcmp), reinterpret_cast<void**>(&old_strcmp));
if (strcmp(s1,s2) == 0) {
print("equal");
} else {
print("not equal");
}
hooker.unhook(reinterpret_cast<void*>(strcmp), reinterpret_cast<void*>(old_strcmp));
if (strcmp(s1,s2) == 0) {
print("equal");
} else {
print("not equal");
}
return 0;
}
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].