maliceio / Malice
Labels
Projects that are alternatives of or similar to Malice
malice
Malice's mission is to be a free open source version of VirusTotal that anyone can use at any scale from an independent researcher to a fortune 500 company.
Try It Out
DEMO: demo.malice.io
-
username:
malice -
password:
ecilam
Requirements
Hardware
- ~16GB disk space
- ~4GB RAM
Software
Getting Started (OSX)
Install
$ brew install maliceio/tap/malice
Usage: malice [OPTIONS] COMMAND [arg...]
Open Source Malware Analysis Framework
Version: 0.3.11
Author:
blacktop - <https://github.com/blacktop>
Options:
--debug, -D Enable debug mode [$MALICE_DEBUG]
--help, -h show help
--version, -v print the version
Commands:
scan Scan a file
watch Watch a folder
lookup Look up a file hash
elk Start an ELK docker container
plugin List, Install or Remove Plugins
help Shows a list of commands or help for one command
Run 'malice COMMAND --help' for more information on a command.
Scan some malware
$ malice scan evil.malware
NOTE: On the first run malice will download all of it's default plugins which can take a while to complete.
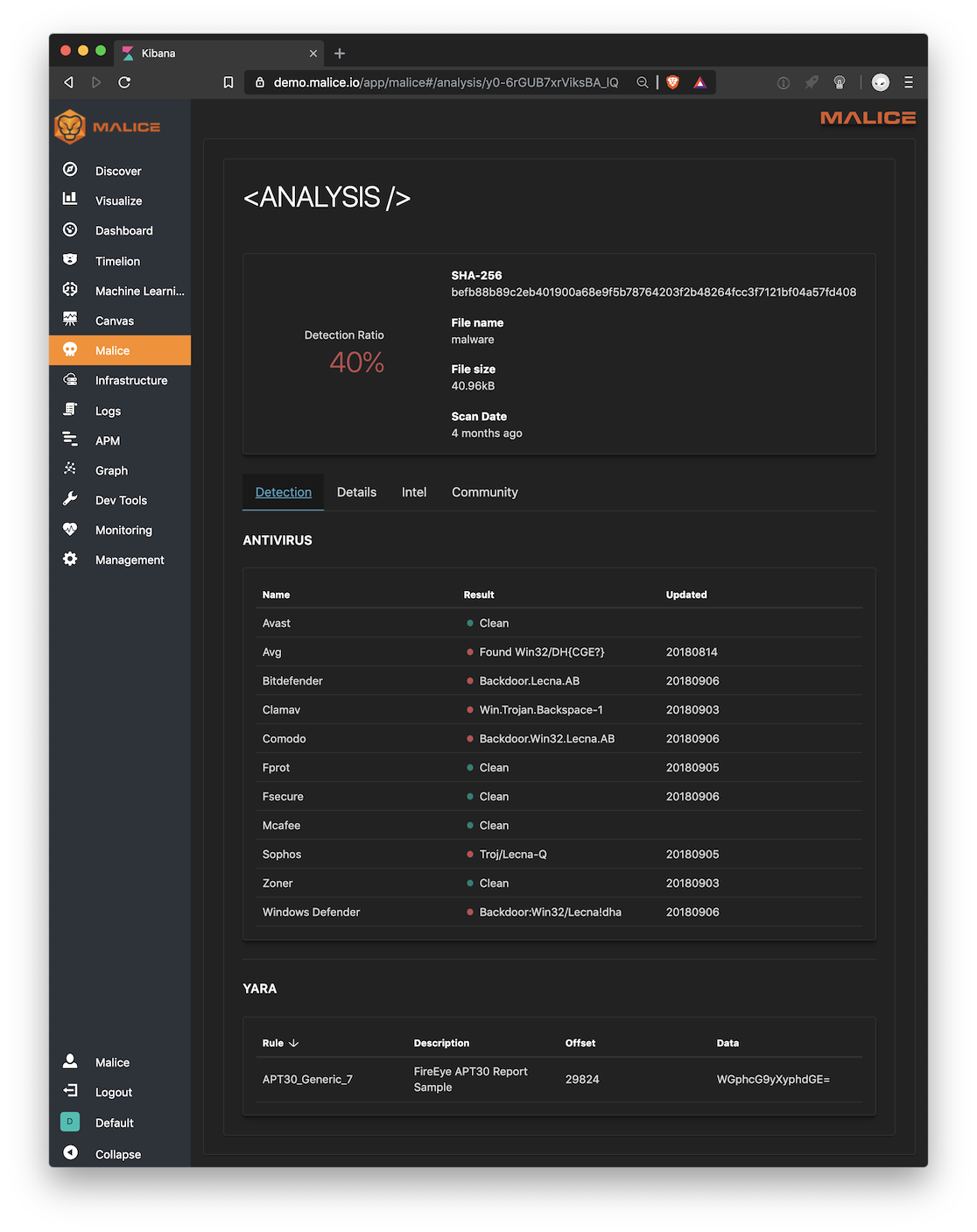
Malice will output the results as a markdown table that can be piped or copied into a results.md that will look great on Github see here
Start Malice's Web UI
$ malice elk
You can open the Kibana UI and look at the scan results here: http://localhost (assuming you are using Docker for Mac)
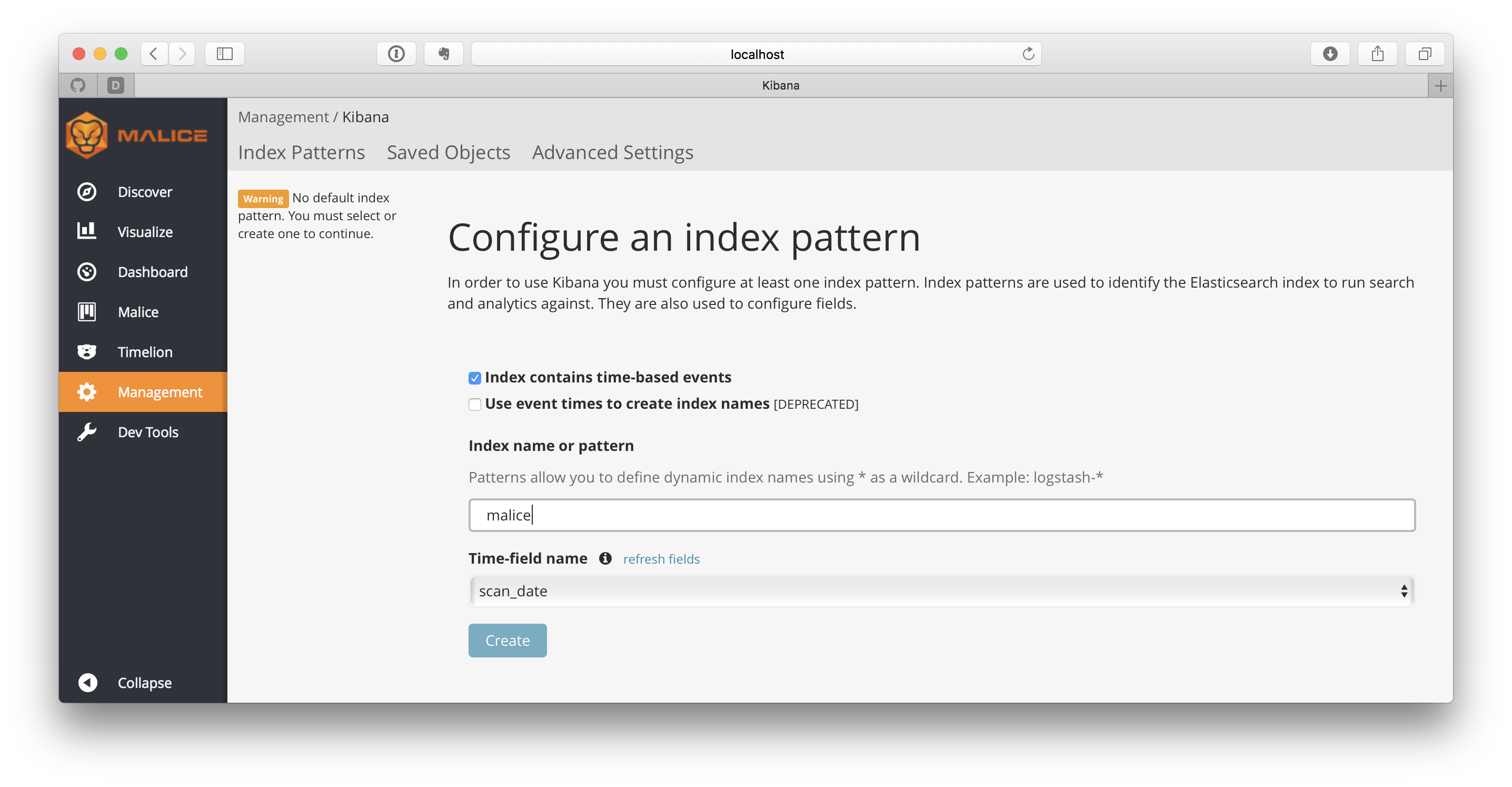
-
Type in malice as the
Index name or patternand click Create. -
Now click on the
Malice Taband behold!!!
Getting Started (Docker in Docker)
Install/Update all Plugins
docker run --rm -v /var/run/docker.sock:/var/run/docker.sock malice/engine plugin update --all
Scan a file
docker run --rm -v /var/run/docker.sock:/var/run/docker.sock \
-v `pwd`:/malice/samples \
--network="host" \
-e MALICE_VT_API=$MALICE_VT_API \
malice/engine scan SAMPLE
Documentation
Known Issues ⚠️
If you are having issues with malice connecting/writting to elasticsearch please see the following:
I have noticed when running the new 5.0+ version of malice/elasticsearch on a linux host you need to increase the memory map areas with the following command
sudo sysctl -w vm.max_map_count=262144
Elasticsearch requires a LOT of RAM to run smoothly. You can lower it to 2GB by running the following (before running a scan):
$ docker run -d \
-p 9200:9200 \
--name malice-elastic \
-e ES_JAVA_OPTS="-Xms2g -Xmx2g" \
malice/elasticsearch
See here for more details on Known Issues/FAQs ⚠️
Issues
Find a bug? Want more features? Find something missing in the documentation? Let me know! Please don't hesitate to file an issue
CHANGELOG
See CHANGELOG.md
License
Apache License (Version 2.0)
Copyright (c) 2013 - 2018 blacktop Joshua Maine