seemoo-lab / Openhaystack
Programming Languages
Projects that are alternatives of or similar to Openhaystack
 OpenHaystack
OpenHaystack
OpenHaystack is a framework for tracking personal Bluetooth devices via Apple's massive Find My network. Use it to create your own tracking tags that you can append to physical objects (keyrings, backpacks, ...) or integrate it into other Bluetooth-capable devices such as notebooks.
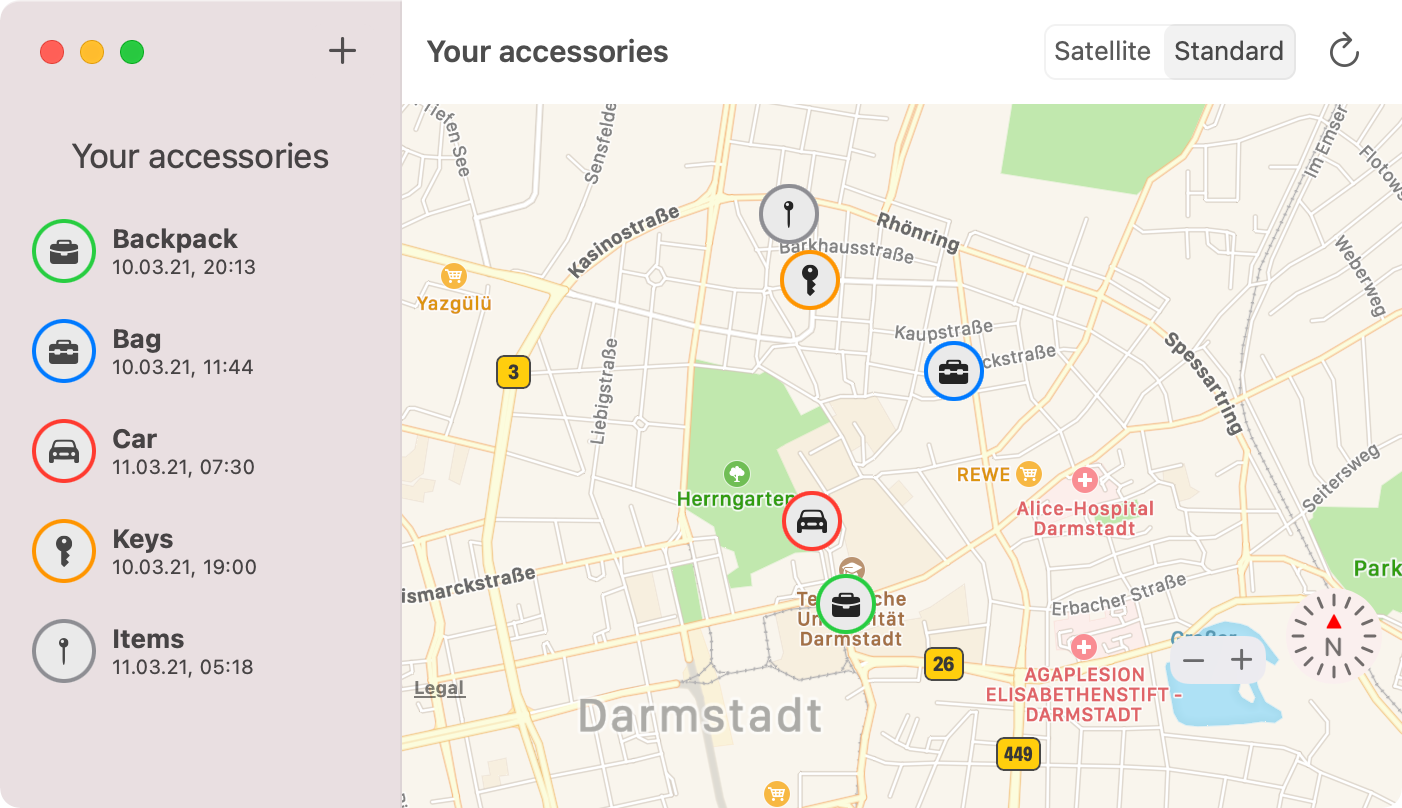
Table of contents
- What is OpenHaystack?
- How to use OpenHaystack?
- How does Apple's Find My network work?
- How to track other Bluetooth devices?
- Authors
- References
- License
What is OpenHaystack?
OpenHaystack is an application that allows you to create your own accessories that are tracked by Apple's Find My network. All you need is a Mac and a other Bluetooth-capable device. By using the app, you can track your accessories anywhere on earth without cellular coverage. Nearby iPhones will discover your accessories and upload their location to Apple's servers when they have a network connection.
History
OpenHaystack is the result of reverse-engineering and security analysis work of Apple's Find My network (or offline finding). We at the Secure Mobile Networking Lab of TU Darmstadt started analyzing offline finding after its initial announcement in June 2019. We identified how Apple devices can be found by iPhones devices, even when they are offline through this work. The whole system is a clever combination of Bluetooth advertisements, public-key cryptography, and a central database of encrypted location reports. We disclosed a specification of the closed parts of offline finding and conducted a comprehensive security and privacy analysis. We found two distinct vulnerabilities. The most severe one, which allowed a malicious application to access location data, has meanwhile been fixed by Apple (CVE-2020-9986). For more information about the security analysis, please read our paper. Since its release, we received quite a bit of press and media coverage.
Disclaimer
OpenHaystack is experimental software. The code is untested and incomplete. For example, OpenHaystack accessories using our firmware broadcast a fixed public key and, therefore, are trackable by other devices in proximity (this might change in a future release). OpenHaystack is not affiliated with or endorsed by Apple Inc.
How to use OpenHaystack?
OpenHaystack consists of two components. First, we provide a macOS application that can display the last reported location of your personal Bluetooth devices. Second, the firmware image enables Bluetooth devices to broadcast beacons that make them discoverable by iPhones.
System requirements
OpenHaystack requires macOS 11 (Big Sur).
Installation
The OpenHaystack application requires a custom plugin for Apple Mail. It is used to download location reports from Apple's servers via a private API (technical explanation: the plugin inherits Apple Mail's entitlements required to use this API). Therefore, the installation procedure is slightly different and requires you to temporarily disable Gatekeeper. Our plugin does not access any other private data such as emails (see source code).
- Download a precompiled binary release from our GitHub page.
Alternative: build the application from source via Xcode. - Open OpenHaystack. This will ask you to install the Mail plugin in
~/Library/Mail/Bundle. - Open a terminal and run
sudo spctl --master-disable, which will disable Gatekeeper and allow our Apple Mail plugin to run. - Open Apple Mail. Go to Preferences → General → Manage Plug-Ins... and activate the checkbox next to OpenHaystackMail.mailbundle.
- Allow access and restart Mail.
- Open a terminal and enter
sudo spctl --master-enable, which will enable Gatekeeper again.
Usage
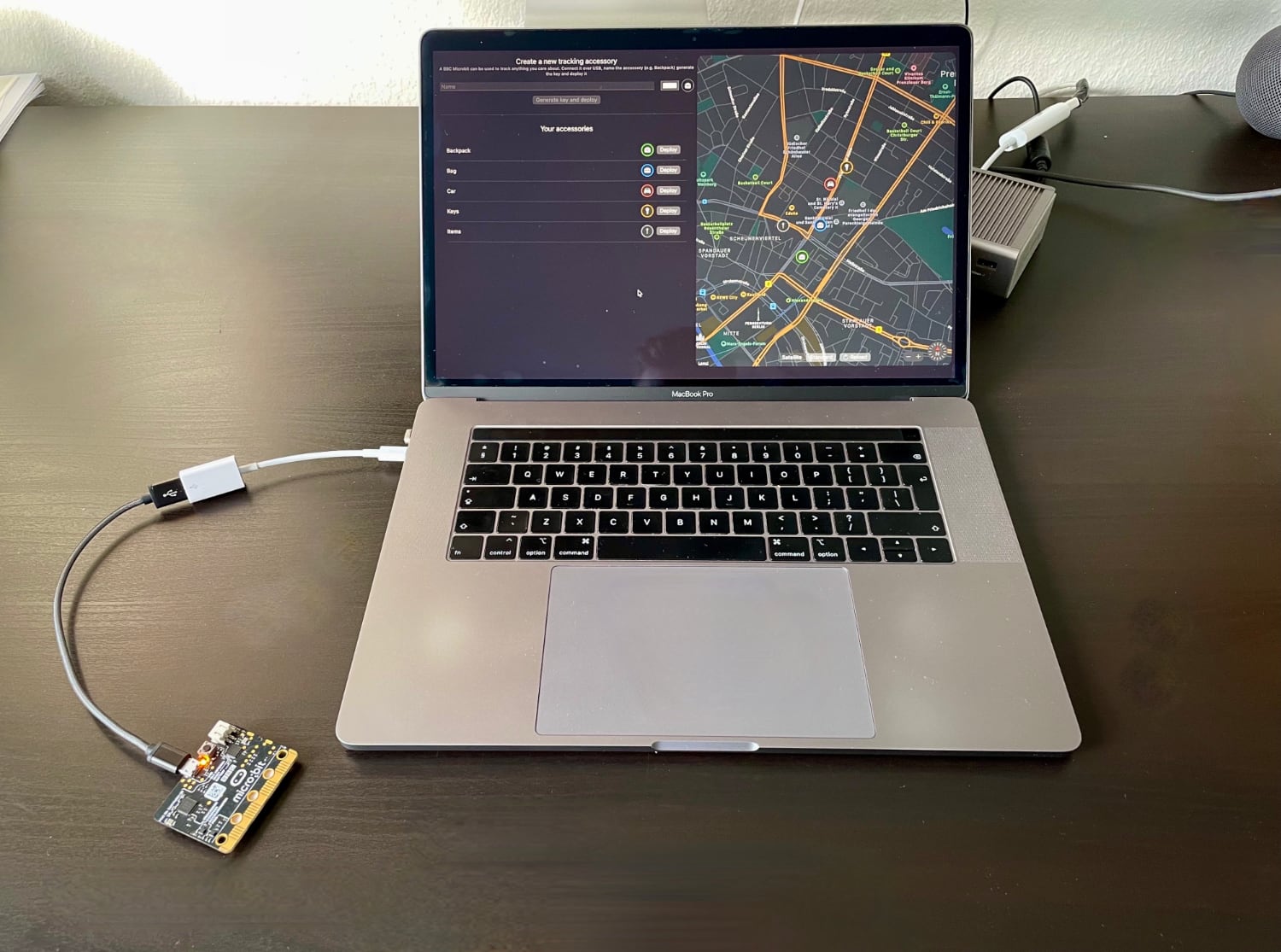
Adding a new accessory. To create a new accessory, you just need to enter a name for it and optionally select a suitable icon and a color. The app then generates a new key pair that is used to encrypt and decrypt the location reports. The private key is stored in your Mac's keychain.
Deploy to device. Connect a supported device via USB to your Mac and hit the Deploy button next to the accessory's name and choose the corresponding. Instead of using OpenHaystack's integrated deployment, you may also copy the public key used for advertising (right click on accessory) and deploy it manually.
Display devices' locations. It can take up to 30 minutes until you will see the first location report on the map on the right side. The map will always show all your items' most recent locations. You can click on every item to check when the last update was received. By clicking the reload button, you can update the location reports.
How does Apple's Find My network work?
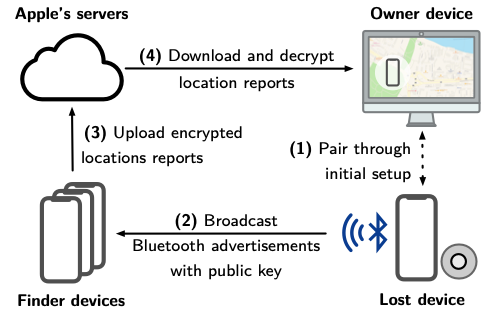
We briefly explain Apple's offline finding system (aka PETS paper and Apple's accessory specification for more details. We provide a schematic overview (from our paper) and explain how we integrate the different steps in OpenHaystack below.
Pairing (1)
To use Apple's Find My network, we generate a public-private key pair on an elliptic curve (P-224). The private key remains on the Mac securely stored in the keychain, and the public key is deployed on the accessory, e.g., an attached micro:bit.
Losing (2)
In short, the accessories broadcast the public key as Bluetooth Low Energy (BLE) advertisements (see firmware). Nearby iPhones will not be able to distinguish our accessories from a genuine Apple device or certified accessory.
Finding (3)
When a nearby iPhone receives a BLE advertisement, the iPhone fetches its current location via GPS, encrypts it using public key from the advertisement, and uploads the encrypted report to Apple's server. All iPhones on iOS 13 or newer do this by default. OpenHaystack is not involved in this step.
Searching (4)
Apple does not know which encrypted locations belong to which Apple account or device. Therefore, every Apple user can download any location report as long as they know the corresponding public key. This is not a security issue: all reports are end-to-end encrypted and cannot be decrypted unless one knows the corresponding private key (stored in the keychain). We leverage this feature to download the reports from Apple that have been created for our OpenHaystack accessories. We use our private keys to decrypt the location reports and show the most recent one on the map.
Apple protects their database against arbitrary access by requiring an authenticated Apple user to download location reports. We use our Apple Mail plugin, which runs with elevated privileges, to access the required authentication information. The OpenHaystack app communicates with the plugin while downloading reports. This is why you need to keep Mail open while using OpenHaystack.
How to track other Bluetooth devices?
In principle, any Bluetooth device can be turned into an OpenHaystack accessory that is trackable via Apple's Find My network. Currently, we provide a convenient deployment method of our OpenHaystack firmwares for a small number of embedded devices (see table below). We also support Linux devices via our generic HCI script. Feel free to port OpenHaystack to other devices that support Bluetooth Low Energy based on the our paper. Please share your results with us!
| Platform | Tested on | Deploy via app | Comment |
|---|---|---|---|
| Nordic nRF51 | BBC micro:bit v1 | ✓ | Only supports nRF51288 at this time (see issue #6). |
| Espressif ESP32 | SP32-WROOM, ESP32-WROVER | ✓ | Deployment can take up to 3 minutes. Requires Python 3. Thanks @fhessel. |
| Linux HCI | Raspberry Pi 4 w/ Raspbian | Should support any Linux machine. |
Authors
References
- Alexander Heinrich, Milan Stute, Tim Kornhuber, Matthias Hollick. Who Can Find My Devices? Security and Privacy of Apple's Crowd-Sourced Bluetooth Location Tracking System. Proceedings on Privacy Enhancing Technologies (PoPETs), 2021. 📄 Preprint.
- Tim Kornhuber. Analysis of Apple's Crowd-Sourced Location Tracking System. Technical University of Darmstadt, Master's thesis, 2020.
- Apple Inc. Find My Network Accessory Specification – Developer Preview – Release R3. 2020. 📄 Download.
License
OpenHaystack is licensed under the GNU Affero General Public License v3.0.