secretlint / Secretlint
Programming Languages
Projects that are alternatives of or similar to Secretlint
Secretlint 
Secretlint is that Pluggable linting tool to prevent committing credential.
Features
- Scanner: Found credentials in a project and report these
- Project Friendly: Easy to set up your project and integrate CI services
- Pre-Commit Hook: Prevent committing credential files
- Pluggable: Allow creating custom rule and flexible configuration
- Documentation: Describe the reason that rule detect it as secret
Quick Start
You can try to use Secretlint on your project at one command.
If you already have installed Docker:
docker run -v `pwd`:`pwd` -w `pwd` --rm -it secretlint/secretlint secretlint "**/*"
If you already have installed Node.js:
npx @secretlint/quick-start "**/*"
After running,
If you got empty result and exit status is 0, your project is secure.
Otherwise, you got some error report, your project includes credential as raw data.
You want to get continuous security, Please see following installation guide and setup pre-commit hook and CI.
Installation
Using Docker
Prerequisites: Require Docker
Use our Docker container to get an environment with Node.js and secretlint and running as fast as you can download them.
You can check all files under the current directory with secretlint by following command:
docker run -v `pwd`:`pwd` -w `pwd` --rm -it secretlint/secretlint secretlint "**/*"
secretlint/secretlint docker container work without configuration by design.
Built-in rules:
For more details, please see secretlint's Dockerfile.
Using Node.js
Prerequisites: Require Node.js 10+.
Secretlint is written by JavaScript. You can install Secretlint using npm:
npm install secretlint @secretlint/secretlint-rule-preset-recommend --save-dev
You should then set up a configuration file:
npx secretlint --init
Finally, you can run Secretlint on any file or directory like this:
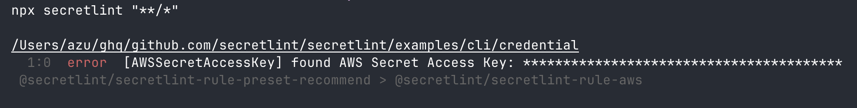
npx secretlint "**/*"
📝 Secretlint support glob pattern and glob pattern should be wrapped by a double quote.
It is also possible to install Secretlint globally using npm install --global. But, We do not recommended it, some rules may be broken in globally.
Usage
secretlint --help show Usage.
Secretlint CLI that scan secret/credential data.
Usage
$ secretlint [file|glob*]
Note
supported glob syntax is based on microglob
https://github.com/micromatch/micromatch#matching-features
Options
--init setup config file. Create .secretlintrc.json file from your package.json
--format [String] formatter name. Default: "stylish". Available Formatter: checkstyle, compact, jslint-xml, json, junit, pretty-error, stylish, table, tap, unix
--output [path:String] output file path that is written of reported result.
--no-color disable ANSI-color of output.
--no-terminalLink disable terminalLink of output.
--secretlintrc [path:String] path to .secretlintrc config file. Default: .secretlintrc.*
--secretlintignore [path:String] path to .secretlintignore file. Default: .secretlintignore
Options for Developer
--profile Enable performance profile.
--secretlintrcJSON [String] a JSON string of .secretlintrc. use JSON string instead of rc file.
Experimental Options
--locale [String] locale tag for translating message. Default: en
Examples
$ secretlint ./README.md
# glob pattern should be wrapped with double quote
$ secretlint "**/*"
$ secretlint "source/**/*.ini"
Configuration
Secretlint has a configuration file .secretlintrc.{json,yml,js}.
After running secretlint --init, you'll have a .secretlintrc.json file in your directory.
In it, you'll see some rules configured like this:
{
"rules": [
{
"id": "@secretlint/secretlint-rule-preset-recommend"
}
]
}
The id property is the name of secretlint rule package.
Secretlint does not have built-in rule.
You want to add some rule and You should install the package and add the rule to .secretlintrc file.
Each rule has same configuration pattern:
-
options: Option definition for the rule. For more details, see each rule documentation -
disabled: Ifdisabledistrue, disable the rule -
allowMessageIds:allowMessageIdsis an array of message id that you want to suppress error report- message id is defined in each rule and please see the rule documentation
Example: options
For example, @secretlint/secretlint-rule-example has allows in options.
This allows option define text pattern that you want to ignore.
{
"rules": [
{
"id": "@secretlint/secretlint-rule-example",
"options": {
"allows": [
"/dummy_secret/i"
]
}
}
]
}
Example: allowMessageIds
For example, you have got following error report by run secretlint:
$ secretlint "**/*"
SECRET.txt
1:8 error [EXAMPLE_MESSAGE] found secret: SECRET @secretlint/secretlint-rule-example
✖ 1 problem (1 error, 0 warnings)
This error's message id is EXAMPLE_MESSAGE in @secretlint/secretlint-rule-example.
If you want to ignore this error, please use allowMessageIds.
{
"rules": [
{
"id": "@secretlint/secretlint-rule-example",
"allowMessageIds": ["EXAMPLE_MESSAGE"]
}
]
}
Rule Packages
Secretlint rules has been implemented as separated modules.
- @secretlint/secretlint-rule-npm
- @secretlint/secretlint-rule-aws
- @secretlint/secretlint-rule-gcp
- @secretlint/secretlint-rule-privatekey
- @secretlint/secretlint-rule-basicauth
- @secretlint/secretlint-rule-slack
- @secretlint/secretlint-rule-sendgrid
- @secretlint/secretlint-rule-secp256k1-privatekey
- @secretlint/secretlint-rule-no-k8s-kind-secret
- @secretlint/secretlint-rule-pattern
- @secretlint/secretlint-rule-no-homedir
Also, Secretlint provide rule preset that includes recommened rule set.
-
@secretlint/secretlint-rule-preset-recommend
- Recommended rule set
Custom Rules
You can create own secretlint rule.
You want to get a secretlint rule for suitable your project and you can create it! A secretlint rule is a just npm package.
If you want to know creating secretlint rule, please see docs/secretlint-rule.md.
Integrations
Pre-commit Hook per project
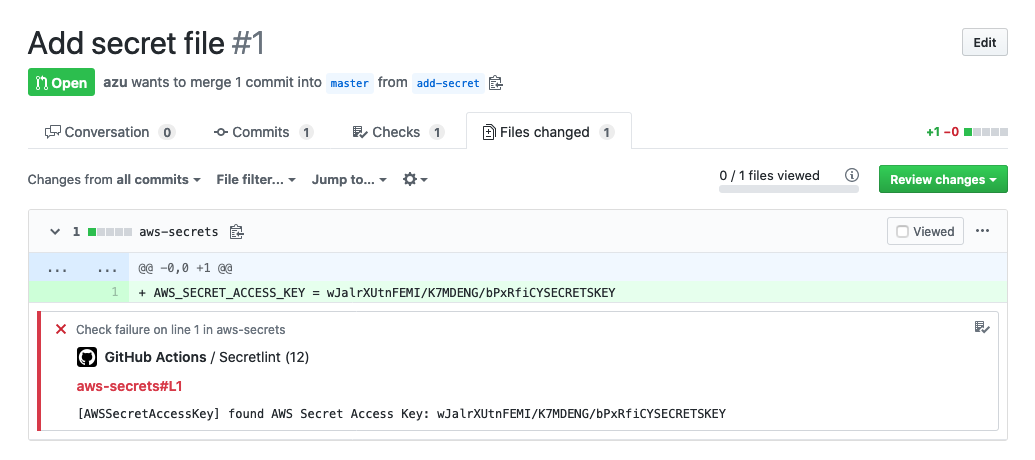
You can use Secretlint with some pre-commit tool. This can prevent to commit secret data by linting with Secretlint.
Applying secretlint to the project and improve security on team developing.
Husky + lint-staged
Use Case: If you want to introduce secretlint to Node.js project, this combination is useful.
Install Husky and lint-staged:
npm install husky lint-staged --save-dev
Edit package.json:
{
// ...
"husky": {
"hooks": {
"pre-commit": "lint-staged"
}
},
"lint-staged": {
"*": [
"secretlint"
]
}
}
This means that check each staged file by Secretlint before commit.
pre-commit
Use Case: You have a project that is developing with Docker. Easy to integrate to secretlint.
Install pre-commit
# macOS. see also https://pre-commit.com/#install
brew install pre-commit
Create .pre-commit-config.yaml:
- repo: local
hooks:
- id: secretlint
name: secretlint
language: docker_image
entry: secretlint/secretlint:latest secretlint
Example setup repository:
Bash Script
Alternately you can save this script as .git/hooks/pre-commit and give it execute permission(chmod +x .git/hooks/pre-commit):
#!/bin/sh
FILES=$(git diff --cached --name-only --diff-filter=ACMR | sed 's| |\\ |g')
[ -z "$FILES" ] && exit 0
# Secretlint all selected files
echo "$FILES" | xargs ./node_modules/.bin/secretlint
# If you using docker
# echo "$FILES" | xargs docker run -v `pwd`:`pwd` -w `pwd` --rm secretlint/secretlint secretlint
RET=$?
if [ $RET -eq 0 ] ;then
exit 0
else
exit 1
fi
Pre-commit Hook globally
Use Case: If you want to check any project by secretlint, you can use global git hooks.
Git 2.9+ supports core.hooksPath.
It allow to integrate secretlint globally.
We have created example git hooks project using secretlint + Docker.
-
secretlint/git-hooks
- Requirement: Docker
You can set up by following steps:
# clone this repository
git clone https://github.com/secretlint/git-hooks git-hooks
cd git-hooks
# integrate secretlint to git hook globally
git config --global core.hooksPath $(pwd)/hooks
After setup of core.hooksPath, secretlint check any file before you commit it.
For more details, see secretlint/git-hooks project.
Node.js version also can be used for global git hook. If you interesting in it, please see @azu/git-hooks.
CI
GitHub Actions
If you already set secretlint Using Node.js, you can run secretlint with your configuration on GitHub Actions.
Put .github/workflows/secretlint.yml in your repository.
name: Secretlint
on: [push, pull_request]
env:
CI: true
jobs:
test:
name: "Secretlint"
runs-on: ubuntu-18.04
strategy:
matrix:
node-version: [12]
steps:
- name: checkout
uses: actions/[email protected]
- name: setup Node ${{ matrix.node-version }}
uses: actions/[email protected]
with:
node-version: ${{ matrix.node-version }}
- name: Install
run: npm install
- name: Lint with Secretlint
run: npx secretlint "**/*"
This configuration also integrate Pull Request review comment via actions/setup-node.
- Example Repository: https://github.com/azu/secretlint-github-actions-example
- Example Pull Request: https://github.com/azu/secretlint-github-actions-example/pull/1/files
Semantic Versioning Policy
Secretlint project follow Semantic Versioning without secretlint-rule-preset-canary. However, secretlint is not different with most semver project.
- Patch release (intended to not break your lint build)
- A bug fix to the CLI or core (including formatters).
- Improvements to documentation.
- Non-user-facing changes such as refactoring.
- Re-releasing after a failed release (i.e., publishing a release that doesn't work for anyone).
- Minor release (might break your lint build)
- A new option.
- An existing rule is deprecated.
- A new CLI capability is created.
- New public API are added (new classes, new methods, new arguments to existing methods, etc.).
- It might break TypeScript definitions
- A new formatter is created.
- Major release (break your lint build)
- A new option to an existing rule that results in secretlint reporting more errors by default.
- An existing formatter is removed.
- Add new default rule to rule preset.
- Part of the public API is removed or changed in an incompatible way.
Motivation
-
git-secrets is useful, but it is hard to setup per project.
- It main use-case is globally installation
- Secretlint want to install for a project and customize setting per project.
-
repo-security-scanner, Gitleaks and truffleHog is good scan tools
- Secretlint need to flexible customize that include ignoring definitions, custom rules.
-
detect-secrets is similar tools, but it adopts opt-out approach
- Secretlint adopt opt-in approach
- We also need to custom rules by user
Philosophy
- Reduce false-positive of linting
- Integration to developing workflow
- Empower Users to Contribute
Opt-in instead of Opt-out
Secretlint adopt opt-in approach.
In our experience, linting tools that report various errors by default is difficult to use. Opt-in approach help to introduce Secretlint increasing.
It will help to reduce false-positive by configuration.
Rule as Documentation
We think a rule as a documentation. So, Each rule should have reasonable documentation.
We need to describe why this file is error. A rule that has not documentation, It is just a opinionated.
Describe the reason of error and then it will lead to reduce false-positive error.
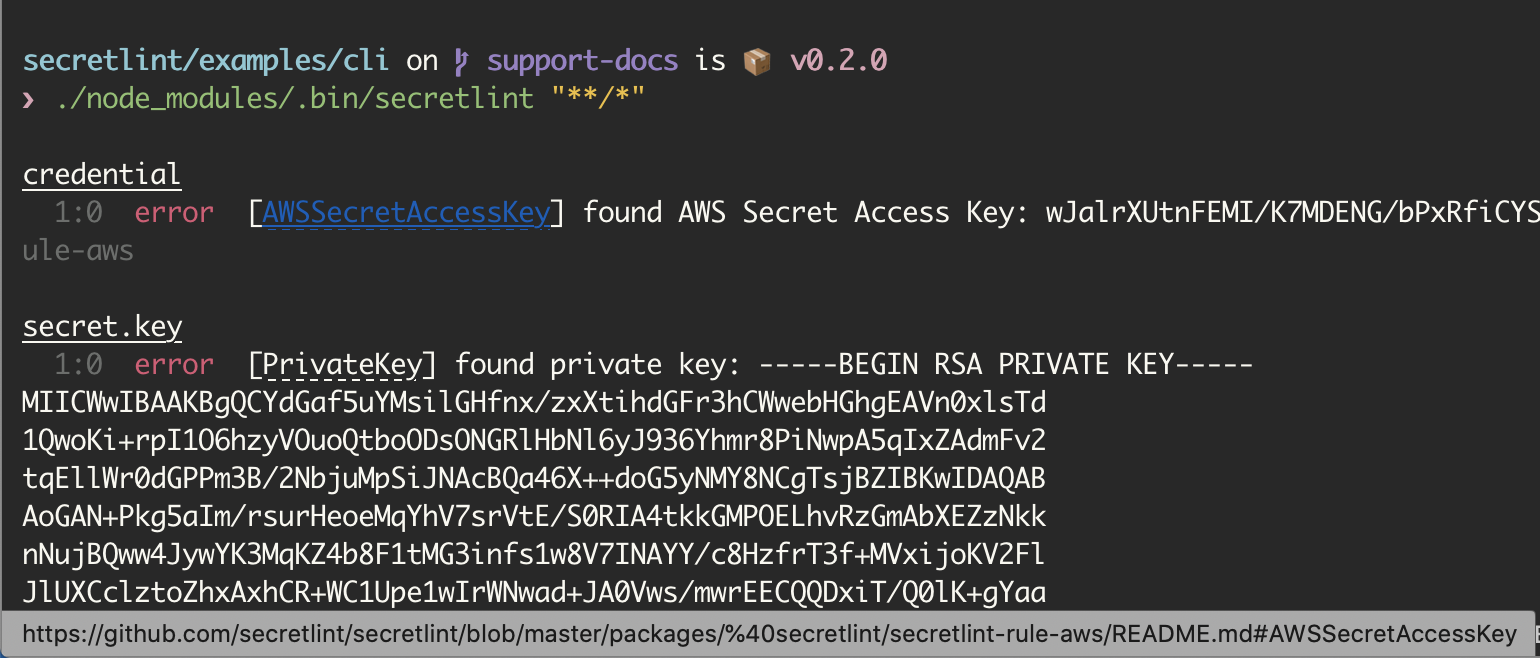
Also, Secretlint CLI support hyperlink in Terminal. It means that you can jump to rule documentation from lint error message directly.
Example on iTerm 2: Cmd + Click error's messageId and open AWSSecretAccessKey on your browser.
If you want to know support terminal, please see Hyperlinks in Terminal Emulators.
Also, Welcome to Contribution about secretlint documentation!
Why Node.js?
- Package Manager
- Require package manager to realize flexible pluggable system
- Node.js has npm and yarn as package manager
- Package manager help to install custom plugin/rule by user
- Exist Reference Implementation
- Node.js already has pluggable linting tools like ESLint, textlint, stylelint etc
- So Node.js user familiar with pluggable linting tools
- Previously, I created textlint as same approach, so I familiar with Node.js
- Users
- JavaScript is Popular language
- It means that empower Users to Contribute
- Users can create own rule by own hand
Of course, secretlint also support Docker.
Changelog
See Releases page.
Contributing
Pull requests and stars are always welcome.
For bugs and feature requests, please create an issue.
See also, CONTRIBUTING.md and CODE_OF_CONDUCT.md
Author
License
MIT © azu