abhisharma404 / Vault
Licence: mit
swiss army knife for hackers
Stars: ✭ 346
Programming Languages
python
139335 projects - #7 most used programming language
Labels
Projects that are alternatives of or similar to Vault
Raccoon
A high performance offensive security tool for reconnaissance and vulnerability scanning
Stars: ✭ 2,312 (+568.21%)
Mutual labels: osint, hacking, pentesting, scanner, hacking-tool, information-gathering, offensive-security, fuzzing
Vajra
Vajra is a highly customizable target and scope based automated web hacking framework to automate boring recon tasks and same scans for multiple target during web applications penetration testing.
Stars: ✭ 269 (-22.25%)
Mutual labels: osint, hacking, pentesting, scanner, information-gathering
Pentesting Bible
Learn ethical hacking.Learn about reconnaissance,windows/linux hacking,attacking web technologies,and pen testing wireless networks.Resources for learning malware analysis and reverse engineering.
Stars: ✭ 8,981 (+2495.66%)
Mutual labels: osint, hacking, pentesting, hacking-tool, information-gathering
Dirsearch
Web path scanner
Stars: ✭ 7,246 (+1994.22%)
Mutual labels: hacking, pentesting, scanner, hacking-tool, fuzzing
Nosqlmap
Automated NoSQL database enumeration and web application exploitation tool.
Stars: ✭ 1,928 (+457.23%)
Mutual labels: hacking, scanner, hacking-tool, offensive-security
Scilla
🏴☠️ Information Gathering tool 🏴☠️ DNS / Subdomains / Ports / Directories enumeration
Stars: ✭ 116 (-66.47%)
Mutual labels: hacking, pentesting, hacking-tool, information-gathering
Crithit
Takes a single wordlist item and tests it one by one over a large collection of websites before moving onto the next. Create signatures to cross-check vulnerabilities over multiple hosts.
Stars: ✭ 182 (-47.4%)
Mutual labels: hacking, pentesting, hacking-tool, offensive-security
Evillimiter
Tool that monitors, analyzes and limits the bandwidth of devices on the local network without administrative access.
Stars: ✭ 764 (+120.81%)
Mutual labels: networking, hacking, pentesting, hacking-tool
Hosthunter
HostHunter a recon tool for discovering hostnames using OSINT techniques.
Stars: ✭ 427 (+23.41%)
Mutual labels: osint, hacking, pentesting, hacking-tool
Vulnx
vulnx 🕷️ is an intelligent bot auto shell injector that detect vulnerabilities in multiple types of cms { `wordpress , joomla , drupal , prestashop .. `}
Stars: ✭ 1,009 (+191.62%)
Mutual labels: crawler, hacking, hacking-tool, information-gathering
Deadtrap
An OSINT tool to gather information about the real owner of a phone number
Stars: ✭ 73 (-78.9%)
Mutual labels: osint, hacking, scanner, information-gathering
Osmedeus
Fully automated offensive security framework for reconnaissance and vulnerability scanning
Stars: ✭ 3,391 (+880.06%)
Mutual labels: osint, hacking, hacking-tool, information-gathering
Filesensor
Dynamic file detection tool based on crawler 基于爬虫的动态敏感文件探测工具
Stars: ✭ 227 (-34.39%)
Mutual labels: crawler, scrapy, pentesting, fuzzing
Sandmap
Nmap on steroids. Simple CLI with the ability to run pure Nmap engine, 31 modules with 459 scan profiles.
Stars: ✭ 1,180 (+241.04%)
Mutual labels: hacking, hacking-tool, information-gathering, port-scanner
Reconnoitre
A security tool for multithreaded information gathering and service enumeration whilst building directory structures to store results, along with writing out recommendations for further testing.
Stars: ✭ 1,824 (+427.17%)
Mutual labels: hacking, scanner, hacking-tool, offensive-security
Vhostscan
A virtual host scanner that performs reverse lookups, can be used with pivot tools, detect catch-all scenarios, work around wildcards, aliases and dynamic default pages.
Stars: ✭ 767 (+121.68%)
Mutual labels: hacking, scanner, hacking-tool, offensive-security
Reconspider
🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
Stars: ✭ 621 (+79.48%)
Mutual labels: osint, hacking, scanner, information-gathering
Oscp Prep
my oscp prep collection
Stars: ✭ 105 (-69.65%)
Mutual labels: osint, hacking, pentesting, scanner
Rengine
reNgine is an automated reconnaissance framework for web applications with a focus on highly configurable streamlined recon process via Engines, recon data correlation and organization, continuous monitoring, backed by a database, and simple yet intuitive User Interface. reNgine makes it easy for penetration testers to gather reconnaissance with…
Stars: ✭ 3,439 (+893.93%)
Mutual labels: osint, scanner, information-gathering, pentesting
Red hawk
All in one tool for Information Gathering, Vulnerability Scanning and Crawling. A must have tool for all penetration testers
Stars: ✭ 1,898 (+448.55%)
Mutual labels: crawler, scanner, information-gathering
VAULT
Swiss army knife for hackers
Table of contents
Getting Started
Steps to setup :
git clone <your-fork-url>cd vaultsudo apt-get install python3-pipsudo pip3 install virtualenvvirtualenv venvsource venv/bin/activatepip3 install -r requirements.txt
Starting Vault :
cd vault/srcpython3 vault.py
Features
-
Scan website for the following vulnerabilities
- [x] XSS
- [x] LFI
- [ ] RFI
- [ ] SQLi
-
Scanner
- [x] Port scanning : ACK, FIN, NULL, XMAS
- [x] IP scanning : Ping Sweep, ARP
- [x] SSL vulnerability scan
- [x] OS scan
- [x] Hash scanner : MD5, SHA1, SHA224, SHA256, SHA512
-
Others
- Information Gathering
- [x] Clickjacking
- [x] jQuery version checking
- [x] Insecure cookie flags
- [x] Testing HTTP methods
- [x] Insecure headers
- [x] Header/banner grabbing
- Finder
- [x] Find comments in source code
- [x] Find e-mails in source code
- [ ] Session fixation through cookie injection
- [x] Brute force login through authorization headers
- [x] URL Fuzzer
- [x] WHOIS Lookup
- [x] Google Dork
- [ ] Error handler checker
- [x] Admin panel finder
- [x] Open redirect vulnerability
- [x] CMS Detection
- [x] Detect Honeypots
- [ ] Detect DDoS attack
- [ ] Detect De-authentication attack
- [ ] Detect ARP spoof attack
-
Crawling
- [x] Crawl a website and collect all the links
- [x] Crawl and scrape the website for images
-
Attacks
- [x] DDoS Attack
- [x] ARP Spoofer
- [ ] DNS Spoofer
- [x] De-authentication attack
- [ ] Network disassociation attack
- [X] Ping of death
- [x] MAC Flood attack
-
Utilities
- [ ] Generate customized backdoor
- [ ] Data monitoring
- [X] Keylogger
- [ ] SSH Tunelling
- [ ] Generate sitemap
- [x] MAC address changer
- [ ] Trace route
Usage
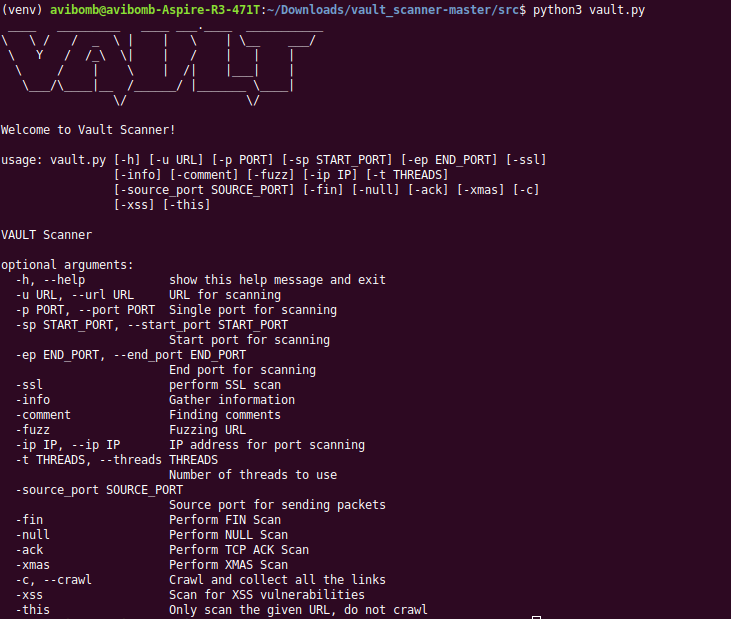
usage: vault.py [-h] [-u URL] [-p PORT] [-sp START_PORT] [-ep END_PORT] [-ssl]
[-info] [-comment] [-email] [-fuzz] [-ip IP] [-t THREADS]
[-i INTERFACE] [-source_port SOURCE_PORT] [-fin] [-null]
[-ack] [-xmas] [-os_scan] [-xss] [-this] [-ping_sweep] [-arp]
[-ip_start_range IP_START_RANGE] [-ip_end_range IP_END_RANGE]
[-lfi] [-whois] [-o OUTPUT] [-d DORK] [-ddos] [-mac_flood]
[-interval INTERVAL] [-cr] [-cri] [-all] [-exclude EXCLUDE]
[-admin] [-orv] [-keylogger] [-host HOST] [-username USERNAME]
[-password PASSWORD] [-sender SENDER]
[-destination DESTINATION] [-arp_spoof] [-jquery]
[-ping_death] [-bruteforce] [-hash] [-md5] [-sha1] [-sha224]
[-sha256] [-sha512] [-dir DIR] [-detect_cms] [-change_mac]
[-mac MAC] [-honey] [-target_bssid TARGET_BSSID] [-deauth]
VAULT
optional arguments:
-h, --help show this help message and exit
-u URL, --url URL URL for scanning
-p PORT, --port PORT Single port for scanning
-sp START_PORT, --start_port START_PORT
Start port for scanning
-ep END_PORT, --end_port END_PORT
End port for scanning
-ssl perform SSL scan
-info Gather information
-comment Finding comments
-email Finding emails
-fuzz Fuzzing URL
-ip IP, --ip IP IP address for port scanning
-t THREADS, --threads THREADS
Number of threads to use
-i INTERFACE, --interface INTERFACE
Networking Interface to use
-source_port SOURCE_PORT
Source port for sending packets
-fin Perform FIN Scan
-null Perform NULL Scan
-ack Perform TCP ACK Scan
-xmas Perform XMAS Scan
-os_scan Perform OS Scan
-xss Scan for XSS vulnerabilities
-this Only scan the given URL, do not crawl
-ping_sweep ICMP ECHO request
-arp ARP Scan
-ip_start_range IP_START_RANGE
Start range for scanning IP
-ip_end_range IP_END_RANGE
End range for scanning IP
-lfi Scan for LFI vulnerabilities
-whois perform a whois lookup of a given IP
-o OUTPUT, --output OUTPUT
Output all data
-d DORK, --dork DORK Perform google dorking
-ddos Perform DDoS attack
-mac_flood Perform MAC Flooding attack
-interval INTERVAL Interval time for sending packets
-cr For extracting links from a web page
-cri For extracting images from a Web page
-all Run all scans
-exclude EXCLUDE Scans to exclude
-admin Find admin panel on a given domain
-orv Test for open redirection Vulnerability
-keylogger Capture keystrokes and send them by email
-host HOST SMTP Host to use
-username USERNAME Username to login
-password PASSWORD Password to login
-sender SENDER Email to send from
-destination DESTINATION
Email to send to
-arp_spoof ARP Spoofing
-jquery Check jQuery version and get vulnerabilities
-ping_death Perform ping of death attack
-bruteforce Perform brute force attack through
Authorizationheaders
-hash Start hash scan
-md5 Scan MD5
-sha1 Scan SHA1
-sha224 Scan SHA224
-sha256 Scan SHA256
-sha512 Scan SHA512
-dir DIR Directory to scan
-detect_cms Perform CMS Detection
-change_mac Chnage MAC address
-mac MAC New MAC address
-honey Detect honeypot
-target_bssid TARGET_BSSID
Target BSSID
-deauth De-authentication attack
Example Usage : python3 vault.py -u 'http://url' -info -comment -ssl -fuzz
Screenshot
Contributing
Any and all contributions, new-issues, features and tips are welcome.
Please refer to CONTRIBUTING.md for more details.
License
This project is currently a part of IIT KWoC 2018.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].