0Kee-Team / Watchad
Programming Languages
Labels
Projects that are alternatives of or similar to Watchad
WatchAD
AD Security Intrusion Detection System
English Document | 中文文档
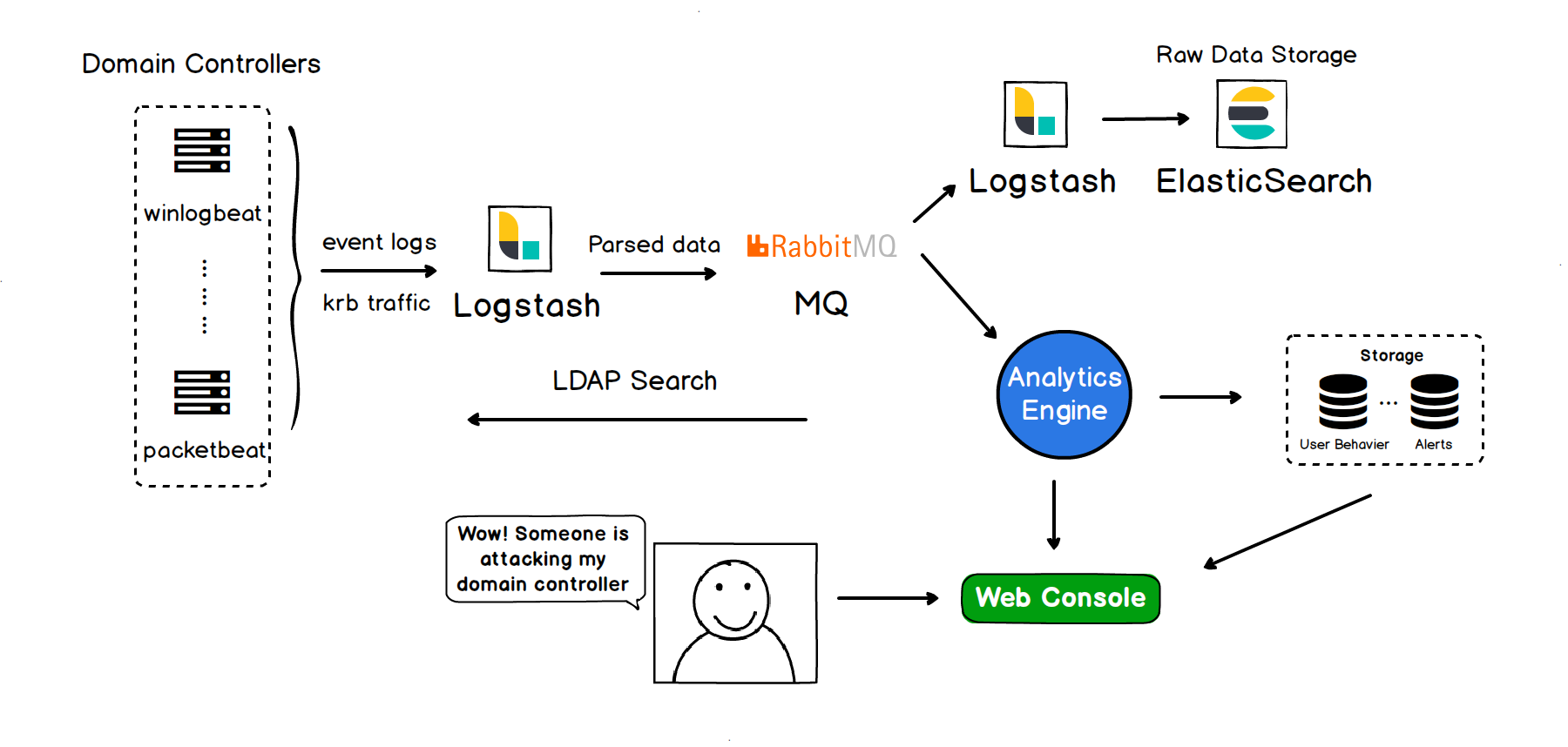
After Collecting event logs and kerberos traffic on all domain controllers, WatchAD can detect a variety of known or unknown threats through features matching, Kerberos protocol analysis, historical behaviors, sensitive operations, honeypot accounts and so on.The WatchAD rules cover the many common AD attacks.
The WatchAD has been running well on the Qihoo 360 intranet for more than six months and has found several threat activities.
In order to support the open-source community and promote the improvement of the project, we decided to open source part of the system that based on the event log detections.
The following are currently supported detections:
- Discovery: Reconnaissance using Directory Services queries, Reconnaissance using PsLoggedOn, Honeypot accounts Activity.
- Credential Dumping: Kerberoasting [NT], AS-REP Roasting, Remotely dump the password of DC.
- Lateral Movement: Brute Force , Suspicious remotely logon using credentials, Remote execution targeting to DC、Abnormal windows file share name, Encryption downgrade activity [NT], Abnormal Kerberos ticket request [NT].
- Privilege Escalation: Abnormal modification of ACL, Detection of MS17-010 attacks, Creation of new Group Policy, NTLM Relay Activity, Sensitive permission of resource-based constraint delegation granted, Attacking printer services with SpoolSample, Privilege escalation with MS14-068 Attacks [NT], Suspicious Kerberos Constraint Delegation activity [NT]
- Persistence: Modification of AdminSDHolder, DCShadow Attack Detection, Modification of the DSRM password, Sensitive permission of Group Policy delegation granted, Sensitive permission of Kerberos constraint delegated granted, Modification of sensitive groups, Creation of new System Service on DC, Creation of new Scheduled Task on DC, Modification of SIDHistory, Skeleton Key active detection, Skeleton Key passive detection [NT], Kerberos Golden Ticket Activity [NT].
- Defense Evasion: Malicous clearance of event logs, Event log service shut down
[NT] represent "based on Network traffic". Up to now, these part is not in this open-source plan. We will continue to open source based on the feedback.
Our talk "Evaded Microsoft ATA? But You Are Completely Exposed By Event Logs" about detecting AD attacks based on event log is shown at the DEF CON 27 @ Blue Team Village.
Installation
WatchAD is a completely detection system with lots of components. Please refer to the installation tutorial to install. To set up a honeypot account, please refer to the honeypot account tutorial。
Architecture:
This project WatchAD only contains part of the code, which associated with the detection engine. In order to format the display you can put alarm data into your platform, or use the Web platform we developed -- WatchAD-Web, which is a simple platform tailored to WatchAD for some common operations. If you have more needs for interface design or operation experience, please customize the development according to WatchAD's alarm data.
Custom detection module
WatchAD supports the development of custom detection modules, please refer to our development tutorial。
If you don't need some module,You can delete the module's .py file directly and restart the detection engine.
Do not delete files in the "record" directory, which is not involved in threat detections and just record for key activities of entities.
// TODO
- English code comment
- Compatible with ElasticSearch 6.X
- Reduce false positives
- Kerberoasting: the detection based on event log was replaced by kerberos traffic analysis. We are considering add it back.
- Pass-the-Hash(PtH): There are some false positives, optimizing
- Pass-the-Ticket(PtT): There are some false positives, optimizing
- Silver-Ticket: There are some false positives, optimizing
- Fake account information:There are some false positives, optimizing
- Compromised account detection based on historical behaviors
- Detections Based on Kerberos traffic open source
- NTLM protocol traffic Analysis
If you find other attack methods that can be added to WatchAD detection, please submit a issue to let us know, or submit a PR to become a contributor to this project.
If you find that a detection module has many false positives (more than 10 per day), please submit a issue to tell us or submit a PR after fixing.
Follow me
Github: @9ian1i Twitter: @9ian1i
Contact us
We come from 360 0KEE Team, if you have security tools or security system development experience , have passionate about security construction, please post your resume to: zhanglu-it#360.cn, renyan-it #360.cn, zhusiyu1#360.cn.
Reference
- Active Directory Kill Chain Attack & Defense
- Active Directory Security
- Windows Security Log Events
- harmj0y's blog
- event log doc
- Understanding SDDL Syntax
- Escalating privileges with ACLs in Active Directory
- Abusing Exchange: One API call away from Domain Admin
- 3gstudent's blog
- Penetration Testing Lab Blog
- Attack Defense & Detection
- INSIDER THREAT SECURITY BLOG
- How to use the UserAccountControl flags to manipulate user account properties
- Advanced Threat Analytics documentation