0xrawsec / Whids
Programming Languages
Projects that are alternatives of or similar to Whids
What
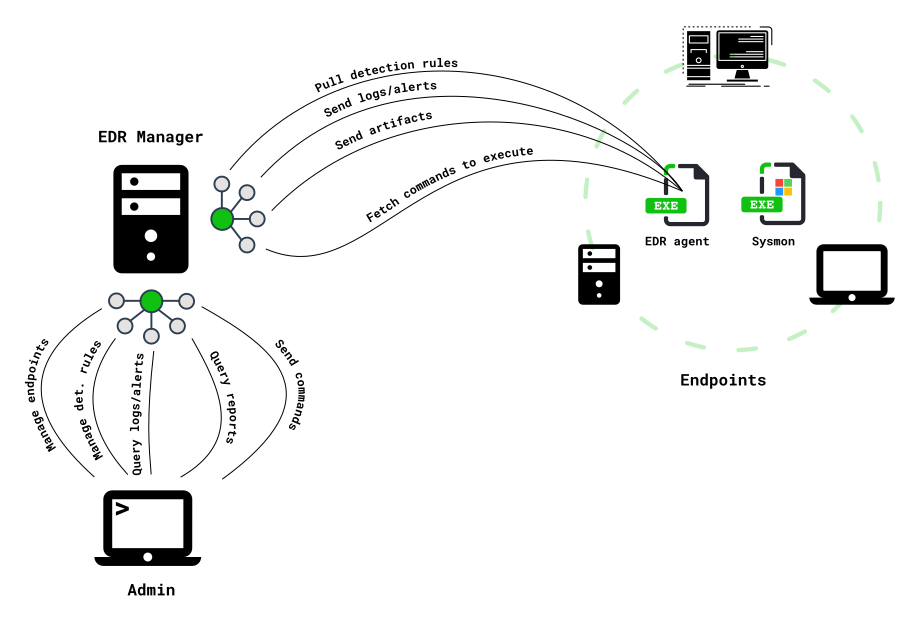
EDR with artifact collection driven by detection. The detection engine is built on top of a previous project Gene specially designed to match Windows events against user defined rules.
What do you mean by "artifact collection driven by detection" ?
It means that an alert can directly triggers some artifact collection (file, registry, process memory). This way you are sure you collected the artifacts as soon as you could (near real time).
All this work has been done on my free time in the hope it would help the IT security community, I hope you will enjoy it. Unless I get some founding to further develop this project, I will continue doing so. I will make all I can to fix the issues in time and provide updates. Feel free to open issues to improve that project and keep it alive.
Why
- Provide an Open Source EDR to the community
- Make transparency on the detection rules to make analysts understand why a rule triggered
- Offer powerful detection primitives though a flexible rule engine
- Optimize Incident Response processes by drastically reducing the time between detection and artifact collection
How
NB: the EDR can be ran standalone (without being connected to an EDR manager)
Strengths
- Open Source
- Relies on Sysmon for all the heavy lifting (kernel component)
- Very powerful but also customizable detection engine
- Built by an Incident Responder for all Incident Responders to make their job easier
- Low footprint (no process injection)
- Can co-exist with any antivirus product (advised to run it along with MS Defender)
- Designed for high thoughput. It can easily enrich and analyse 4M events a day per endpoint without performance impact. Good luck to achieve that with a SIEM.
- Easily integrable with other tools (Splunk, ELK, MISP ...)
- Integrated with ATT&CK framework
Weaknesses
- Only works on Windows
- Detection limited to what is available in the Windows event logs channels (already a lot in there)
- No process instrumentation (it is also a strength as it depends on the point of view)
- No GUI yet (will develop one if requested by the community)
- No support for ETW
- Tell me if you notice others ...
Installation
Requirements
- Install Sysmon
-
Configure Sysmon
- You can find optimized Sysmon configurations here
- Logging any ProcessCreate and ProcessTerminate is mandatory
- Take note of the path to your Sysmon binary because you will need it later on
NB: event filtering can be done at 100% with Gene rules so do not bother creating a complicated Sysmon configuration.
Pre-Installation Recommendations
In order to get the most of WHIDS you might want to improve your logging policy.
- Enable Powershell Module Logging
- Audit Service Creation: gpedit.msc ->
Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\System Audit Policies\System\Audit Security System Extension-> Enable - Enable File System Audit. Sysmon only provides FileCreate events when new files are created, so if you want/need to log other kind of accesses (Read, Write, ...) you need to enable FS Auditing.
- gpedit.msc ->
Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\System Audit Policies\Object Access\Audit File System-> Enable - Right Click Any Folder -> Properties -> Security -> Advanced -> Auditing -> Add
-
Select a principal(put here the name of the user/group you want the audit for). Put group Everyone if you want to log access from any user. -
Apply this tois used to select the scope of this audit policy starting from the folder you have selected -
Basic permissionsselect the kinds of accesses you want the logs to be generated for - Validate
-
- File System auditing logs will appear in the
Securitylog channel
- gpedit.msc ->
- If you want an antivirus to run on your endpoints, keep Microsoft Defender, first because it is a good AV but also because it logs alerts in a dedicated log channel
Microsoft-Windows-Windows Defender/Operationalmonitored by the EDR.
EDR Endpoint agent (Whids.exe)
This section covers the installation of the agent on the endpoint.
- Download and extract the latest WHIDS release https://github.com/0xrawsec/whids/releases
- Run
manage.batas administrator - Launch installation by selecting the appropriate option
- Verify that files have been created at the installation directory
- Edit configuration file by selecting the appropriate option in
manage.bator using your prefered text editor - Skip this if running with a connection to a manager, because rules will be updated automatically. If there is nothing in the rules directory the tool will be useless, so make sure there are some gene rules in there. Some rules are packaged with WHIDS and you will be prompted to choose if you want to install those or not. If you want the last up to date rules, you can get those here (take the compiled ones)
- Start the services from appropriate option in
manage.bator just reboot (preferred option otherwise some enrichment fields will be incomplete leading to false alerts) - If you configured a manager do not forget to run it in order to receive alerts and dumps
NB: At installation time the Sysmon service will be made dependant of WHIDS service so that we are sure the EDR runs before Sysmon starts generating some events.
EDR Manager
The EDR manager can be installed on several platforms, pre-built binaries are provided for Windows, Linux and Darwin.
- Create TLS certificate if needed for HTTPS connections
- Create a configuration file (there is a command line argument to generate a basic config)
- Run the binary
Configuration Examples
Please visit doc/configuration.md
Further Documentation
Known Issues
- Does not work properly when ran from a network share mapped as a network drive (this case prevent whids to identify itself and thus generate some noise). Example: if
\\vbox\testis mounted asZ:drive, runningZ:\whids.exewon't work while running\\vbox\test\whids.exeactually would.
Changelog
v1.7
- New Administrative HTTP API with following features:
- Manage endpoints (list, create, delete)
- Get basic statistics about the manager
- Execute commands on endpoints and get results
- Can drop files prior to execution, to execute binaries/scripts not present on endpoint. Dropped files are deleted after command was ran.
- Can retrieve files (post command execution), to retrieve results of the command
- Collect files from endpoints for forensic purposes
- Contain / Uncontain endpoints by restricting any network traffic except communication to the manager.
- Query endpoints logs
- Query endpoints alerts
- Pivot on a timestamp and retrieve logs/alerts around that time pivot
- Access endpoint report
- Scoring (relative to each environment) allowing to sort endpoints and spot the ones behaving differently from the others.
- Alerts / TTPs observed on a given time frame
- Manage rules (list, create, update, save, delete)
- Integration with Sysmon v12 and v13
- Integrate ClipboardData events
- Put the content of the clipboard data inside the event to allow creating rule on the content of the clipboard
- Integrate ProcessTampering events
- Enrich event with a diffing score between .text section on disk and in memory
- Integrate ClipboardData events
- Implemented certificate pinning on client to enhance security of the communiaction channel between endpoints and management server
- Log filtering capabilities, allowing one to collect contextual events. Log filtering is achieved by creating Gene filtering rules (c.f. Gene Documentation).
- Configuration files in TOML format for better readability
- Better protection of the installation directory